Cloud is instrumental to digital transformation. Companies use cloud to rapidly roll out innovative digital products and services, modernize IT environments, and support hybrid working. Consequently, cloud adoption has already reached remarkable levels and continues to grow. According to the Flexera 2021 State of the Cloud Report , 80% of organizations have a private cloud, 97% use a public cloud, and 92% leverage multiple clouds. Industry-analysis firm Gartner estimates that in 2022, organizations worldwide will spend $482 billion on public-cloud services such as software-as-a-service (SaaS), infrastructure-as-a-service (IaaS), and platform-as-a-service (PaaS). This projection implies a 21.7% year-over-year growth compared to 2021.
As more sensitive data makes its way to the cloud, privacy regulations like GDPR and CCPA weigh in, and cybercrime continues to rise, businesses are ramping up their investment in the ability to protect themselves. Gartner forecasts that worldwide security and risk management spending will exceed $150 billion in 2021, and cloud security will be the fastest growing security-market segment, expanding 41.2% year-over-year to reach $841 million.
Cloud Security is a Shared Responsibility
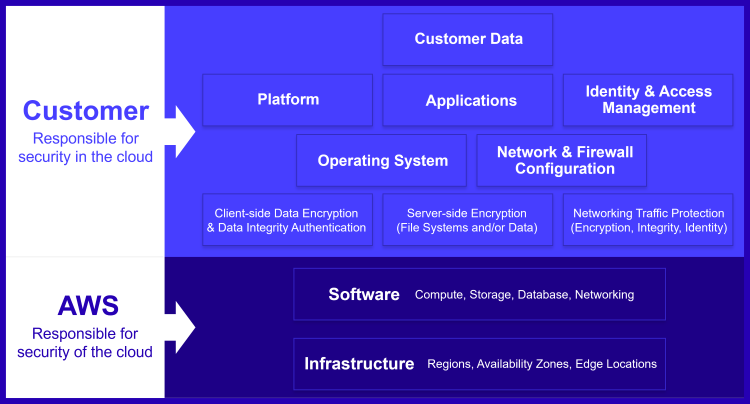
Organizations and their cloud infrastructure provider(s) share the responsibility for security and compliance by following a “shared responsibility model.” As illustrated for AWS in Figure 1 below, the infrastructure provider is responsible for security of the cloud, while the customer is responsible for security in the cloud. The infrastructure provider is on point for protecting everything from concrete to hypervisor, i.e., data center facilities and hardware, software, and network infrastructure. Customers are accountable for data and applications that run on the cloud infrastructure. So, the proverbial unsecured AWS S3 buckets that have resulted in sensitive data exposure for numerous organizations illustrate a misconfiguration problem on the customer side.
Top Cloud Security Threats
Cloud users are a prime target for malevolent hackers, and protecting complex cloud environments is no small feat for organizations. Experts at the Cloud Security Alliance have identified the following 11 critical threats to cloud computing (ranked in order of severity), referred to as the “Egregious Eleven:”
- Data breaches. Security responsibility: customer and cloud-service provider
- Misconfiguration and inadequate change control. Security responsibility: customer
- Lack of cloud security architecture and strategy. Security responsibility: customer
- . Insufficient identity, credential, access and key management. Security responsibility: customer
- Account hijacking. Security responsibility: customer and cloud-service provider
- Insider threat. Security responsibility: customer
- Insecure interfaces and APIs. Security responsibility: customer and cloud-service provider
- Weak control plane. Security responsibility: customer
- Metastructure and applistructure failures. Security responsibility: customer and cloud-service provider
- Limited cloud usage visibility. Security responsibility: customer and cloud-service provider
- Abuse and nefarious use of cloud services. Security responsibility: customer and cloud-service provider.
How to Approach Cloud Security
Building a continuous cloud-security management program for your organization is critical. As a first step, you may want to familiarize yourself with leading security frameworks (such as NIST Cyber Security Framework and related publications, ISO/IEC 27017, etc.) and best practices for cloud security (such as Center of Internet Security Benchmarks providing security-configuration guides for various cloud environments—from AWS to Azure to Google Cloud Platform to Alibaba Cloud).
The Cloud Security Alliance (CSA) publishes a Cloud Controls Matrix (CCM) that outlines fundamental security principles and controls to “guide cloud service providers (CSPs) and cloud service customers (CSCs) seeking secure implementation, assessment, and management of cloud services security risks.” CCM covers 197 controls across 17 security domains, such as Audit and Assurance, Application and Interface Security, Change Control and Configuration Management, Governance, Risk and Compliance, Infrastructure and Virtualization Security, Threat and Vulnerability Management, and others.
You can leverage cloud security consultants to examine how your enterprise processes, stores, accesses, and uses data in the cloud, then you can craft a custom data-governance protocol and other elements of the security-management program aligned to your business objectives and risk profile. Professional cloud security assessments and penetration testing would also be instrumental to helping you utilize the cloud in a compliant and secure fashion.
In the unfortunate event of a company experiencing a breach, having a cloud incident response plan in place is crucial to mitigating the impact of an attack and minimizing damage. Enduring any catastrophic enterprise event is traumatic enough, but how the enterprise reacts after such an event will often determine their fate. Moreover, the organization's response plays an influential role in the potential cost of a cyber breach.
Protect Your Cloud With Secureworks®
A secure cloud infrastructure is a requirement that every modern business must meet to remain competitive. Learn more about our cloud security products and services and leverage our expertise to create a cloud security strategy that fits your business needs.
You might also be interested in
- 5 Steps to AWS Cloud Adoption with Security in Mind
- Build a Cloud Security Management Program With Confidence
Cloud Computing Services: SaaS vs PaaS vs IaaS
There are three different types of cloud computing services:
-
Software as a Service (SaaS)
Software as a Service (SaaS) allows a software company to publish their software and let their users access the software via a web browser. Suite servers like Microsoft Office 365 or applications like Salesforce provide users with instant access to documents and files without the hassle of installing, managing, and storing applications and data on their personal devices.
Users and organizations utilize SaaS applications for additional computer space, added cloud security, ease of updating software, and the ability to synchronize data across many devices. SaaS applications help users avoid software ownership and costly, time-consuming updates and typically operate on a monthly or annual subscription-based model.
-
Platform as a Service (PaaS)
Platform as a Service (PaaS) means that an enterprise uses software and hardware provided by a Cloud Solution Provider (CSP) to build and deploy their own suite of services. For instance, Amazon Web Services (AWS) and Heroku are popular PaaS providers that act as the platform or host to many other popular software programs such as QuickBooks Online, Expedia, and Adobe. Enterprises can utilize PaaS providers to develop and launch simple cloud-based apps to cloud-enabled enterprise applications.
Businesses can store their clients' data in the platform provider's cloud service without having to invest in hardware, software, and connectivity. They can also use testing and compiling functions from PaaS to efficiently communicate and deliver new production developments with an extended national or international network. Avoid expensive investments for managing software licenses and utilize tools to inspect data and improve your cloud-based services.
-
Infrastructure as a Service (IaaS)
Infrastructure as a Service (IaaS), also referred to as utility computing, allows users to obtain access to servers, storage, and hardware through the cloud. The pay-as-you-go method allows users to pay a single monthly subscription fee based on how many gigabytes or megabytes of data they have hosted by the provider.
IaaS is the most flexible cloud computing service and allows users to customize their product mix. Direct access to outside servers requires no internal capital investment in expensive hardware. IaaS enables its organizational users to have the most control over their cloud infrastructure. Gain the cloud security your enterprise needs without upfront capital investments.
What are the Risks and Challenges of Cloud Computing?
Although cloud computing services are a great option for many businesses, there are some risks that come with the territory. Since the introduction of cloud computing, more and more companies have been steadily switching to third-party cloud computing providers. This influx of valuable data in single locations makes cloud providers a prime target for malicious activity.
As an illustration of this issue, imagine that everyone stores their savings in a personal safe at their respective homes. That means each homeowner is directly responsible for their own money. However, most people prefer to store the majority of their money in a third-party bank. Although this means that the bank will provide added security and have more secure safety regulations, it also means the bank is a prime target for professional robbers to attack.
Just like the bank scenario, businesses have to trust cloud vendors to secure their critical data. Although there are many security and government regulations in place, no data center is 100% safe from hackers and malware. Also, insider threats are becoming a prevalent concern for many cloud service providers.
CISOs should work closely with their cloud providers, treating the relationship as a partnership rather than just a hardware or software vendor. When treated as a partnership, you can vet out the details of the services that the cloud service provider is offering and you can choose the right partner for your needs.
Top Cloud Security Threats
Cloud providers are a prime target for malevolent hackers. Experts at the Cloud Security Alliance have identified the following 12 critical issues to cloud security (ranked in order of severity per survey results) referred to as the “Treacherous 12”:
- Data Breaches
- Weak Identity, Credential and Access Management
- Insecure Application Programming Interfaces (APIs)
- System and Application Vulnerabilities
- Account Hijacking
- Malicious Insiders
- Advanced Persistent Threats (APTs)
- Data Loss
- Insufficient Due Diligence
- Abuse and Nefarious Use of Cloud Services
- Denial of Service
- Shared Technology Issues
The rise of enterprise cloud computing has created tremendous opportunity not only for cloud service providers, but also for cloud security specialists. Preventing any of these twelve vulnerabilities has become an industry unto itself. Small and medium-sized businesses are ridiculed for attempting to maintain their own data servers. Thus, every business that utilizes SaaS becomes dependent upon secure PaaS and IaaS providers, and vulnerable to any of these 12 threats.
Cloud Security Solutions
A protected cloud infrastructure is now a commodity that every modern business must have to remain competitive. Learn more about our cloud security solutions and how we can create a security strategy that fits your business' needs. From cloud incident response to resources for selecting a cloud managed security services provider (MSSP), it is critical to learn how to protect your valuable data.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.