Multi-factor authentication (MFA) is an enhanced security configuration that requires a user to present more than a single form of authentication in order to access a website or service. Requiring a password in addition to a code from a text message to access a website is an example of MFA. MFA is viewed by the security industry as a secure practice that greatly increases the level of effort an attacker must expend in order to compromise a user’s account.
Secureworks identified an Office365 MFA vulnerability bypass that takes advantage of design features provided by Microsoft. The following details the vulnerable configuration as well as the steps required to successfully bypass authentication.
[On Demand Webinar]
Lessons from the Field: How Are Skilled Testers Infiltrating?
Many organizations perform regular annual or bi-annual testing to identify network vulnerabilities, gaps in their controls and satisfy industry compliance requirements. View this webinar for an opportunity to see how good guys simulate the bad guys and gain valuable insights.
Vulnerable Configuration
Microsoft Office 365 & Azure Active Directory allow for “named locations”1 where MFA is not required for authentication. Authentication attempts from these trusted IP addresses only require basic username and password, even if a user has previously configured MFA. The purpose of this configuration is to allow users quicker access from trusted locations such as a corporate office, branch office, or other restricted environment.
In order for an attacker to successfully bypass MFA, they would normally require physical access to a particular location whose IP address had been added as a “named location.” While access to a targeted company’s network would typically be prohibitive for such an attack, there is an often-overlooked consequence for this type of configuration.
If the targeted company provides wireless guest network access, although traffic may be segmented from corporate network traffic, both networks will have the same trusted public IP address.
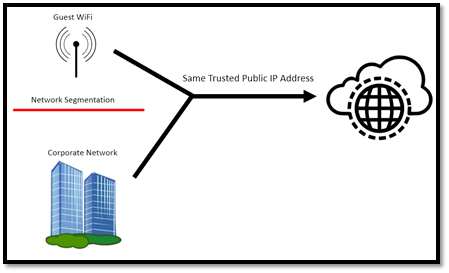
In this scenario, an attacker only needs access to the provided guest wireless connection to bypass Office365 MFA, as the public IP address seen by Microsoft is originating from a trusted location.
Proof of Concept
The following authentication attempt was made from the public internet using valid Office365 credentials. As seen below, the user account requires MFA in order to continue.
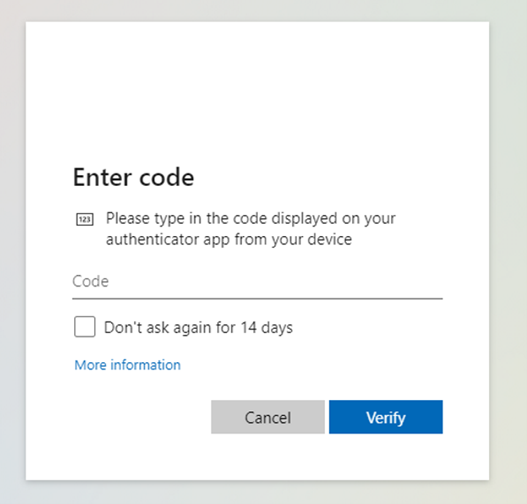
The attacker now connects to the guest wireless network and retries the authentication attempt from a trusted IP address:
Summary
Like many vulnerabilities, the mechanics of an attack are quite simple to understand. This attack scenario was discovered and exploited in the wild to bypass MFA and leverage access into a corporate environment.
When it comes to securing your organization against potential MFA hacks, taking a holistic approach to cybersecurity – that incorporates both an offensive and defensive position – is the best strategy. The Secureworks Adversary Group (SwAG) provides offensive and proactive services to help you anticipate an adversary’s possible next moves. Learn more about adversarial security testing and which assessment may meet your organization’s needs.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.