Secureworks® Counter Threat Unit™ (CTU) researchers created a capture-the-flag (CTF) cyber competition for the 2020 Secureworks Threat Intelligence Summit. Three forensics and open-source intelligence (OSINT) challenges revealed the story of a threat actor compromising a fictitious 1980s rock promotion company named 8Es_Rock. Solving the technical puzzles required beginner to intermediate analysis skills.
Challenge #1: Find the high-value coupon code
“A threat actor compromised an important server at a company called 8Es_Rock. They were after a high-value coupon code. Using the following proxy logs, can you determine what that coupon code was?”
CTU™ researchers provided challenge participants with a file named access.log, which includes proxy logs from the fictitious 8Es_Rock breach. The competitors needed to analyze the web server logs to determine what actions the threat actor took and identify the high-value ‘coupon code’ the actor sought. The proxy logs contain not only the forensic data necessary for this challenge but also data that is useful for solving the other challenges in this series.
The logs show a sequence of sixteen HTTP GET events to the webserver hosted at l00t . tazerup . tk. The URIs end with an encoded string. The last log event in the sequence finishes with a character that signifies the end of Base64-encoded text (see Figure 1).
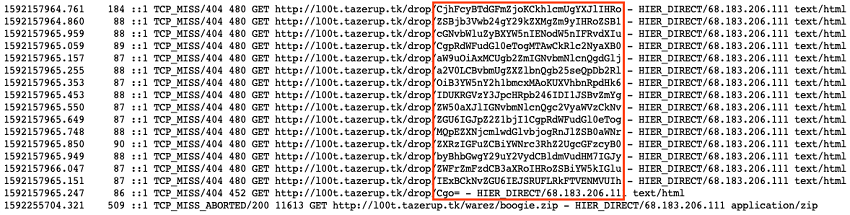
Figure 1. Challenge #1 logs contained a series of encoded text chunks. (Source: Secureworks)
Concatenating and Base64-decoding the strings reveals a message from 8Es_Rock management to their staff. The note contained coupon codes for an upcoming tour by the band Wang Chung (see Figure 2).
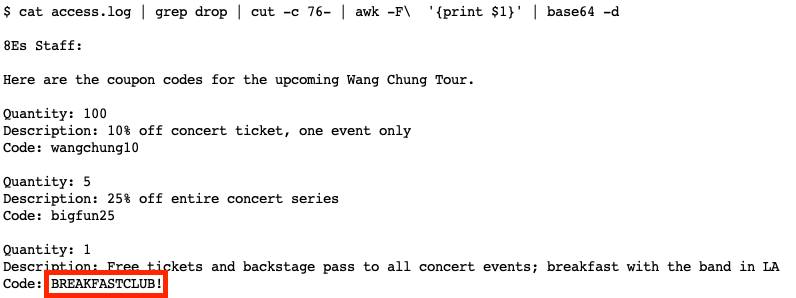
Figure 2. The Base64-decoded text reveals a note and the flag for Challenge #1. (Source: Secureworks)
Reviewing the plaintext message reveals that the “BREAKFASTCLUB!” coupon code has the highest value. CTF competitors who submitted this solution earned 25 points.
Challenge #2: Identify the threat actor’s instruction to 8Es_Rock
“The threat actor who compromised the 8Es_Rock server left an important note on the compromised host. What did they instruct 8Es_Rock to do? [This challenge may require you to solve Challenge #1.]”
The hint for this challenge is in the final line of the proxy logs from Challenge #1. That log entry shows the threat actor downloading the “boogie.zip” file from the server used to exfiltrate the coupon code. The ZIP file is in the “warez” directory. Querying the server for that file results in a 404 error. But other pieces of information provided in Challenge #1 are essential to finding this flag.
The threat actor exfiltrated the coupon code file to an external server on the tazerup . tk domain. An inspection of http: //www . tazerup . tk reveals a fan website with images related to the band Wang Chung (see Figure 3).

Figure 3. A fan site was hosted on the threat actor’s infrastructure. (Source: Secureworks)
The website appears to be a simple homage to the English new wave band. But an inspection of the source code reveals the string ‘@wangchung_r00lz’, which seems to be a social media handle (see Figure 4).
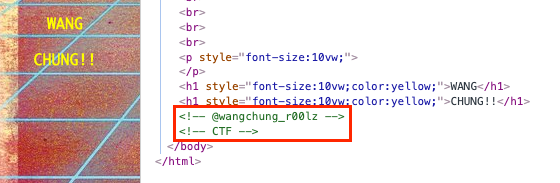
Figure 4. The social media handle @wangchung_r00lz was embedded in the fan site’s source code. (Source: Secureworks)
A quick search of popular social media sites leads to a Twitter account that uses the @wangchung_r00lz handle (see Figure 5). The account’s profile contains a link to the tazerup . tk website, and the profile’s banner contains imagery found on the website. This overlap strongly suggests that the website, the Twitter account, and the threat actor are related.
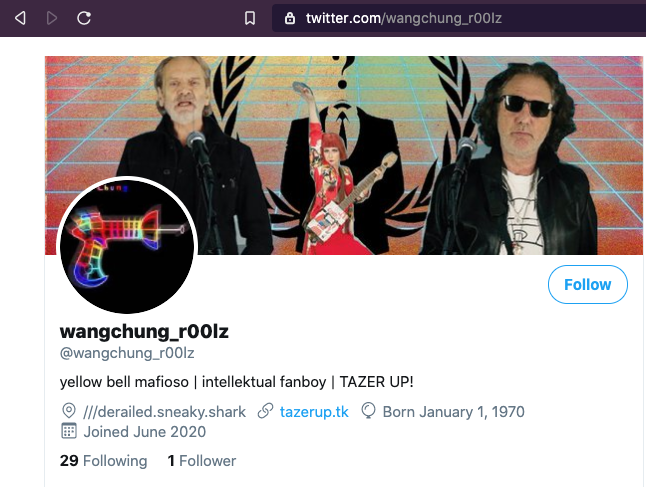
Figure 5. The @wangchung_r00lz Twitter account reveals connections between the threat actor and infrastructure used during the intrusion. (Source: Secureworks)
A study of the Twitter accounts followed by @wangchung_r00lz reveals popular OSINT and forensics sites like The Wayback Machine, Shodan, urlscan.io, archive.today, and CAPE Sandbox. The Wayback Machine and Shodan were included in the list as distractions, but the others are resources essential to solving Challenge #2 and Challenge #3.
By searching urlscan.io for tazerup . tk, CTF competitors could discover an important clue. The oldest entry in the search results is from June 25, 2020. It lists two IP addresses linked to the threat actor’s infrastructure: 68 . 183 . 206 . 111 and 68 . 183 . 199 . 125. The first IP address appeared in the proxy logs, but the second IP address is a new detail. Under the HTTP tab, the second transaction shows that this IP address hosted an image file for a development version of the threat actor’s www . tazerup . tk fan site (see Figure 6).
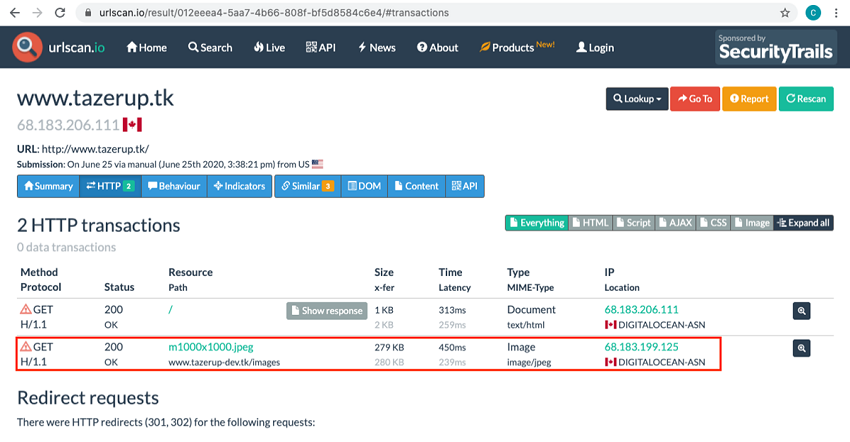
Figure 6. A urlscan.io archive entry showed a connection between the threat actor’s domain and IP address 68 . 183 . 199 . 125. (Source: Secureworks)
Searches for tazerup . tk and tazerup-dev . tk on archive.today, a free service that captures and archives public web page content, do not reveal any cached pages. However, searches for the IP addresses yield archived content. The search results for 68 . 183 . 206 . 111 are not useful, but the results for 68 . 183 . 199 . 125 can advance competitors closer to the challenge flag (see Figure 7).
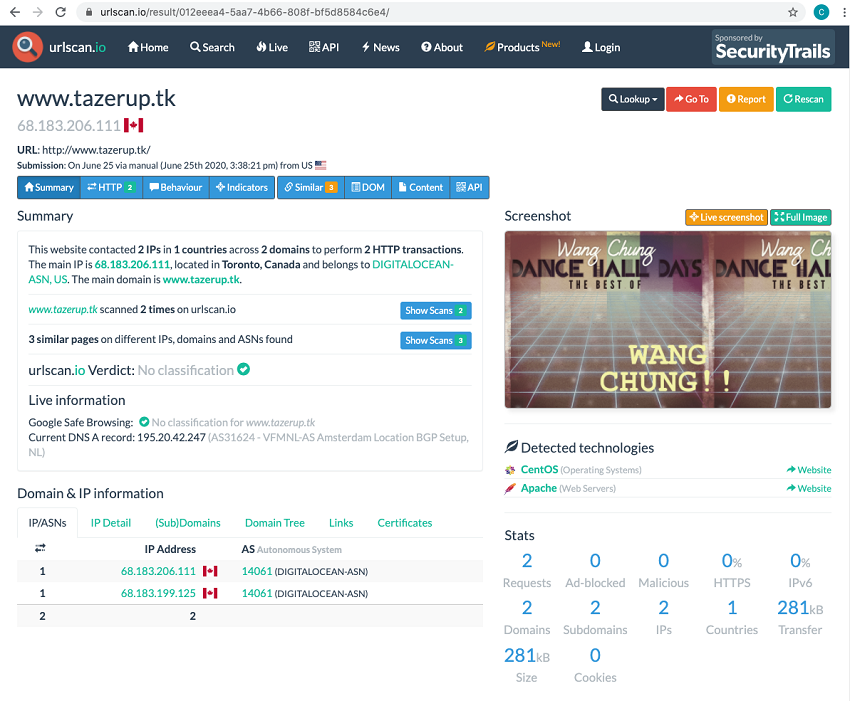
Figure 7. The archive.today service has a cached entry for http: //68 . 183 . 199 . 125. (Source: Secureworks)
The directory listing of http: //68 . 183 . 199 . 125 was cached on June 25, 2020. Also available are two files, targets.txt and /warez/boogie.exe.md5, that are essential for solving Challenge #2 and Challenge #3. The boogie.exe.md5 file contains a hash (MD5: 97a67a2ca90b44282407cec13b23aca1) for an executable named boogie.exe. This name matches the ZIP file retrieved by the threat actor, as evidenced in the proxy logs.
A quick search of CAPE Sandbox for the MD5 hash shows that a sample matching that hash was previously submitted and analyzed (see Figure 8). Files dropped by the malware during the prior payload and configuration extraction are listed under the “Dropped Files” tab in the CAPE interface (see Figure 9).
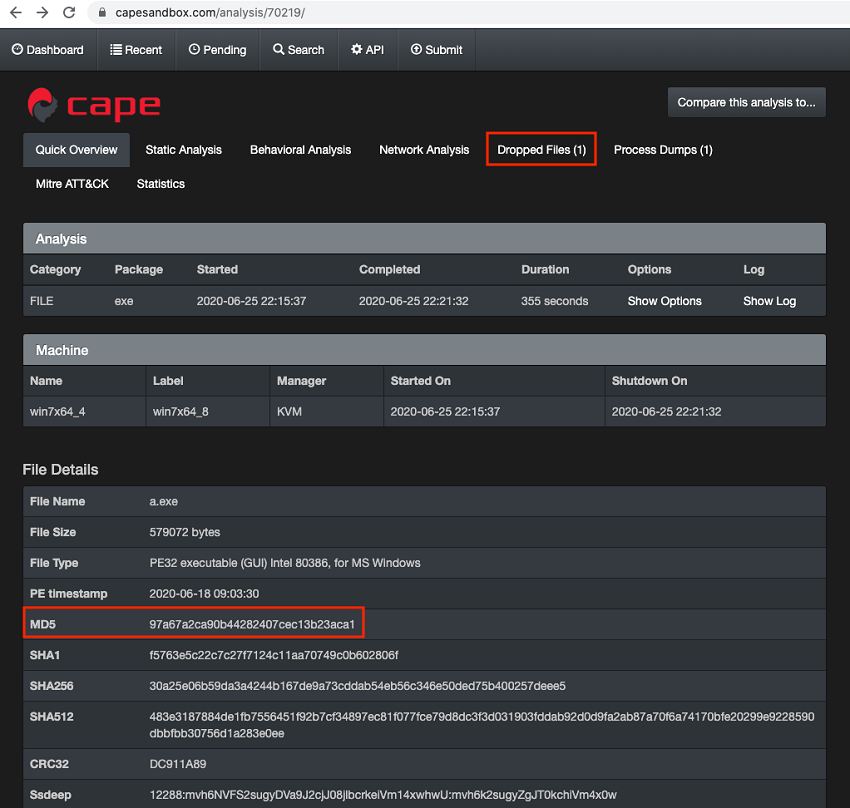
Figure 8. A sample matching the MD5 hash for boogie.exe was previously uploaded to CAPE Sandbox. (Source: Secureworks)
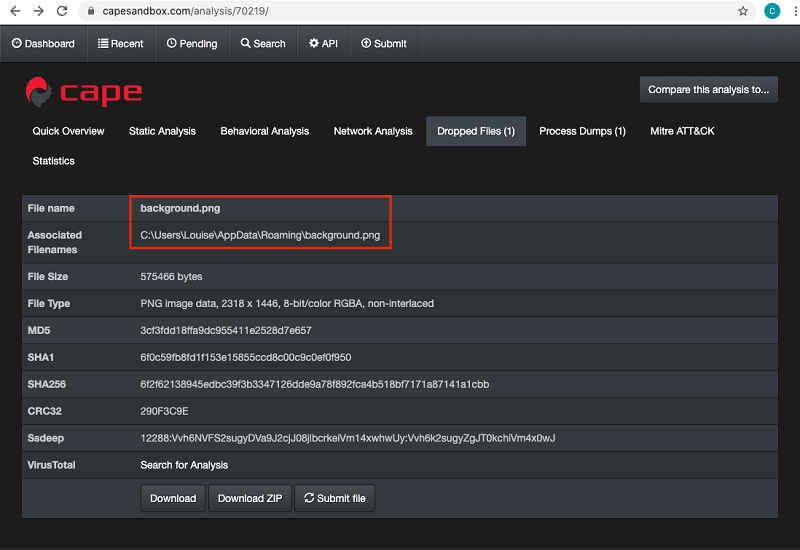
Figure 9. The malicious executable dropped the background.png file. (Source: Secureworks)
Downloading and examining the dropped background.png image file reveals the message “DANCE!” (see Figure 10). Competitors who found this instruction solved Challenge #2 and earned 50 points.

Figure 10. The dropped file contained the message “DANCE!”, which was the flag for Challenge #2. (Source: Secureworks)
Challenge #3: Determine the next target
“Seems like the 8Es_Rock threat actor wasn't done after the first breach. More targets have been identified and attacked. Can you determine the next target on their radar?”
The targets.txt file discovered on the archive.today website in Challenge #2 is the key to solving Challenge #3. The file contains an encoded list of targets (see Figure 11).

Figure 11. Encoded targets listed in the targets.txt file. (Source: Secureworks)
“Tango Down LONDON” and “Tango Down PHILADELPHIA” likely refer to previous attacks against these cities. If so, the next line could be the next target. Competitors who were familiar with the what3words geolocation service could quickly identify the next city on the list. Otherwise, the tuple required additional research. As with prior clues, there was a hint in the list of Twitter accounts followed by @wangchung_r00lz (see Figure 12).
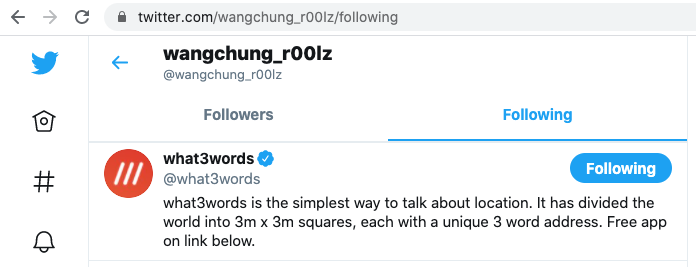
Figure 12. The threat actor’s Twitter account referenced the what3words service, which could decode the target list. (Source: Secureworks)
What3words maps the Earth using a 3x3 meter grid pattern. Each block in the grid is assigned a three-word tuple. The CTF participant could geolocate “///leaves.stacks.brass” to Providence, Rhode Island. In fact, converting all of the tuples results in a list of cities on Wang Chung’s 1984 tour. Providence was the flag for Challenge #3 and was worth 50 points.
Conclusion
The 8Es_Rock challenges were intended to weave moderately difficult forensics and open-source investigation tests into the story of a threat actor with love of Wang Chung and a transparent public social media profile. Many CTF participants solved the first challenge, and some solved the second challenge. No competitors solved the third challenge.
CTU researchers often leverage the public services that were used to solve these challenges. These services frequently provide useful insights about infrastructure and malware associated with real-world network intrusions.
Read other CTF walk-throughs or view on-demand presentations from the 2020 Threat Intelligence Summit.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

