The annual Secureworks® Threat Intelligence Summit took place on June 30, 2020. The event marked two firsts: we went virtual due to the ongoing pandemic, and we hosted a capture-the-flag (CTF) cyber competition for attendees. The competition generated substantial interest. The 161 competitors from both industry and academia represented nearly 20 percent of summit attendees. Many participants indicated that the competition was a key reason for attending the summit. When asked what could be improved about the summit, one respondent replied, “Nothing! Nice variety and fun CTF!”
Constructing the competition
Developing the five-hour cyber competition took approximately three weeks and involved substantial coordination and project management. The first step was to solicit CTF contributors.
The contributors included about a dozen members of the Secureworks Counter Threat Unit™ (CTU) research team: intel analysts, reverse engineers, infrastructure developers, technical writers, and leadership staff. Team members were eager to take a break from their routine to create some fiendish challenges. Several contributors had built or participated in competitions before, which inspired many ideas and passionate discussions about the Secureworks CTF format.
After establishing the team, we set up a chat-based communication channel and other collaboration mechanisms. A spreadsheet tracked the challenges as they were created, vetted, and entered on the CTFd platform. We also created a shared folder for the challenge files, which ranged from binaries to packet captures to memory dumps to image files. For each challenge, we documented the following details:
- Challenge question (e.g., What gaming platform is delivered at IP address 5.62.117.121?)
- Challenge answer (e.g., Minecraft)
- Category (cryptography/steganography/encoding, web exploitation, forensics, log analysis, malware/reverse engineering, open source intelligence, reconnaissance/scanning/enumeration, threat intel, trivia, or other)
- Difficulty level (easy, moderate, or hard)
- Point value (25, 50, or 100)
- Hint (penalties applied)
- Tips for solving (for internal use only)
- Names of associated challenge files in the shared folder
- Names of challenge author and peer reviewer
- Verification of quality control check
- Status of upload to the CTFd platform
- Additional comments from the author and peer reviewer
After populating the CTFd platform and checking the challenges for accuracy, the work shifted from development to execution and we were ready for the summit. We moderated the CTF progression, responded to competitors' questions, and shared progress via Twitter. There were close to 70 challenges distributed across the categories, with 3,350 possible points. The competitors solved all but five of the challenges. We announced the winners and awarded Amazon gift cards to the top ten competitors (see Figure 1).
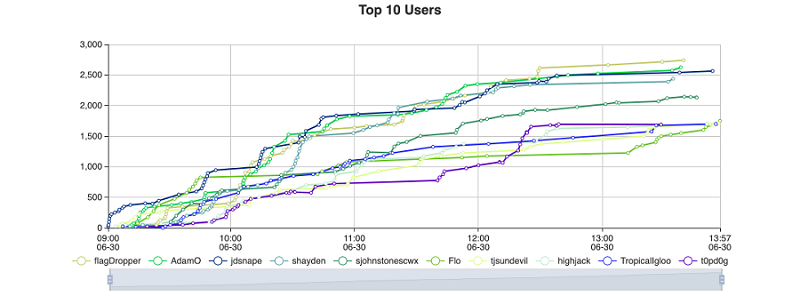
Figure 1. Final CTF scoreboard showing point totals for the top ten competitors. (Source: Secureworks)
Travel Far walk-through
In response to many requests, we will be publishing some challenge walk-throughs. The first is for the multi-part 'Travel Far' challenge, which required competitors to use a unique URL to visit a website from as many countries as possible (see Figure 2). Points were granted as the competitors achieved different country-count milestones.
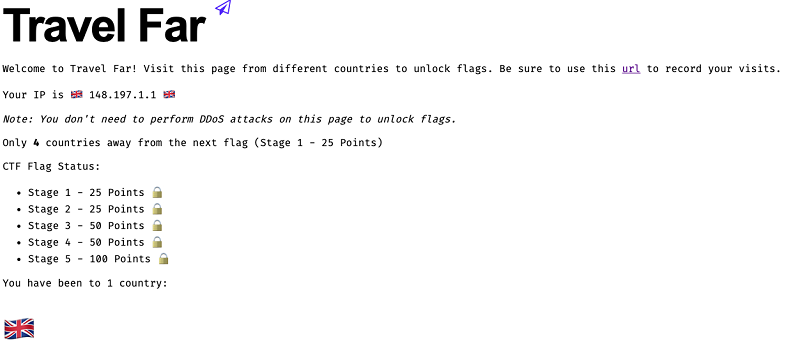
Figure 2. Screenshot of the Travel Far website. (Source: Secureworks)
Bonus challenges were hidden in the screen view of the web application. The page's source code reveals four additional challenges that were hidden using the 'display: none' CSS property (see Figure 3).
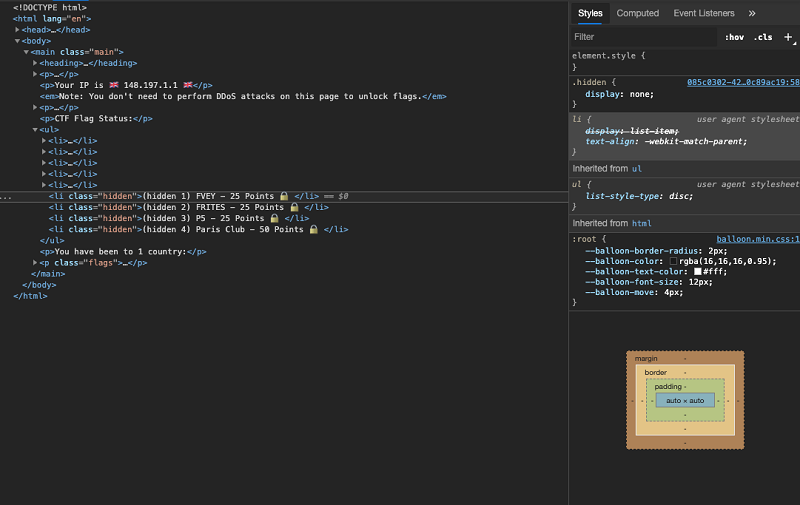
Figure 3. Partial source code view showing the hidden Travel Far challenges. (Source: Secureworks)
Each of these challenges has an associated acronym that indicates what countries must be used to unlock the challenge:
- FVEY – The Five Eyes intelligence alliance (Australia, Canada, New Zealand, the United Kingdom, and the United States)
- FRITES – The largest Mediterranean countries in Europe (France, Italy, and Spain)
- P5 – The permanent members of the United Nations Security Council (China, France, Russia, United Kingdom, and the United States)
- Paris Club – A group of officials from 22 major creditor countries that find coordinated and sustainable solutions to payment difficulties experienced by debtor countries
There was no intentional flaw in the web application that would allow countries to be incorrectly recorded. There was also no flaw added to the backend database to allow arbitrary access.
This challenge tested the competitors' understanding of location-based infrastructure and their ability to write a small script. The following solution is one of many possible methods to solve the challenge. This script uses the Node.js language, which has many packages.
In this solution, the request sent to the URL sets the 'X-Forwarded-For' header to an IP address for the targeted country. A request can then be sent from an IP address from each country in the world.
The RIPEstat Data API can generate IP addresses from each country. It queries a two-letter ISO (International Organization for Standardization) country code and returns a list of associated resources, including IPv4 ranges (see Figure 4). The Node.js 'get-ip-range' package can then generate a single IP address from one of the ranges.
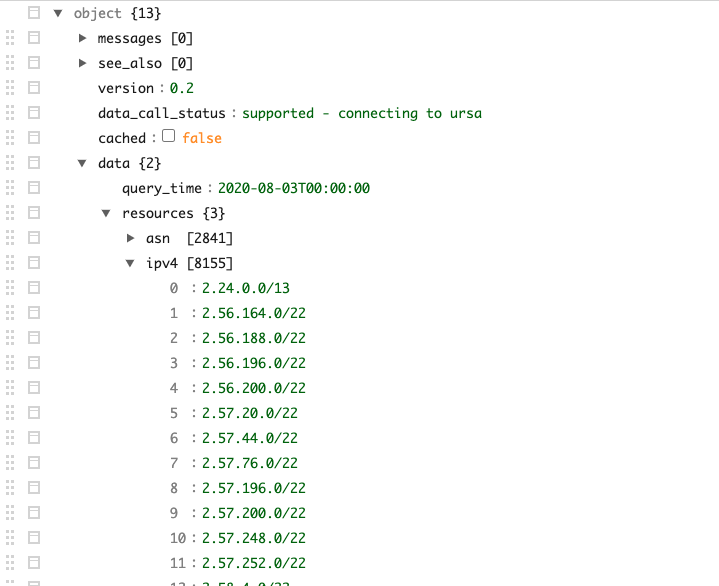
Figure 4. Sample data from the RIPEstat Data API. (Source: RIPE NCC)
Combining this information with the 'bluebird' promise library to support concurrent requests and the 'axios' promise-based HTTP client can produce a function that iterates through every country code and visits the URL from a single IP address (see Figure 5).
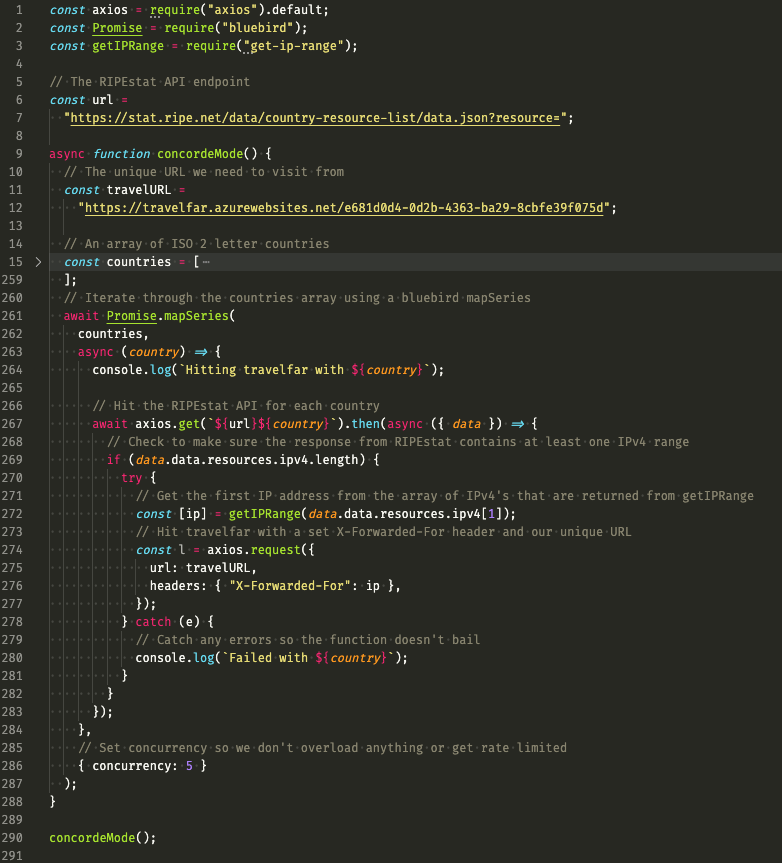
Figure 5. Possible solution for the Travel Far CTF challenge. (Source: Secureworks)
Conclusion
For this challenge, competitors were required to prototype a tactical solution to gain points. CTU researchers often use a similar approach to collect intelligence from threat actors and malware campaigns. Interpreted languages are useful in these scenarios because they do not need to be compiled and are typically platform-independent. By combining an understanding of basic internet architecture with the use of various application programming interfaces (APIs), researchers can collect and process raw data quickly and efficiently.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

