Secureworks® Counter Threat Unit™ (CTU) researchers have tracked the activities of the likely China-based BRONZE UNION (also known as Emissary Panda, APT 27, and LuckyMouse) threat group since 2013. The threat group focuses on espionage activities. CTU™ analysis of BRONZE UNION network compromises revealed broad targeting, a range of capabilities, flexible tactics, and a persistent focus:
- Since 2016, Secureworks analysts have observed BRONZE UNION targeting a variety of data from political, technology, manufacturing, and humanitarian organizations. The threat group's activities ranged from stealing data about cutting-edge weapons technologies to spying on dissidents and other civilian groups.
- In 2017 and 2018, the threat actors used an extensive arsenal of tools and intrusion methods to achieve their aims. This range creates challenges for frontline network defenders and incident responders.
- The threat actors are adept at circumventing common security controls and escalating their privileges. They often use services, tools, and credentials native to the compromised environment (also known as living off the land).
- After obtaining access to a network, the threat actors are diligent about maintaining access to high-value systems over long periods of time. They typically return to compromised networks every three months (see Figure 1) to verify their access to existing web shells, refresh their access to credentials, and in some instances revisit data of interest. The choice of a three-month maintenance schedule could be to align with the cadence that many organizations use for password changes.
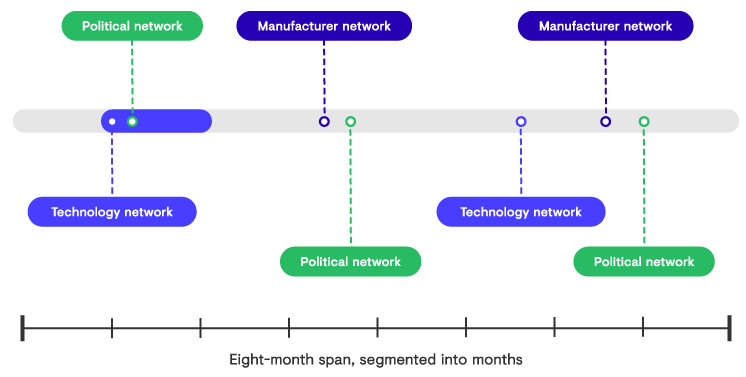
Figure 1. Timeline of BRONZE UNION intrusion maintenance across multiple network compromises. (Source: Secureworks) - The threat actors use stolen credentials to remotely access business email accounts and search for specific keywords and individuals in significant roles. BRONZE UNION has also used email access to download email attachments and data and log into victims' instant messenger services (see Figure 2).
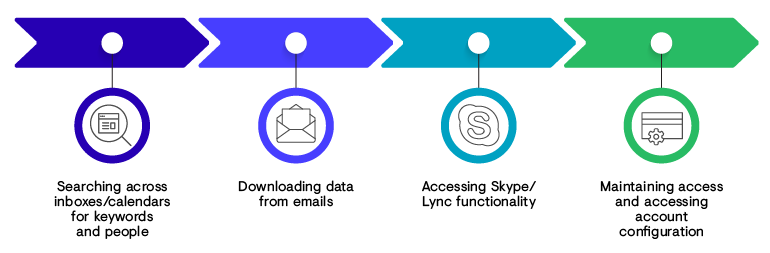
Figure 2. BRONZE UNION leverages business email account access. (Source: Secureworks)
Conclusion
BRONZE UNION is one of the most prolific and active targeted threat groups tracked by CTU researchers as of this publication. CTU analysis suggests that the threat actors use a loose set of operational processes and workflows but are familiar with a wide range of tools and methods. This flexibility enables them to overcome barriers and challenges during the intrusion process.
CTU researchers encourage organizations whose data align with BRONZE UNION's interests to implement security controls and risk management strategies that defend against the threat group's tactics, techniques, and procedures (TTPs). Due to the flexibility and change rate of BRONZE UNION's methods, CTU researchers recommend that organizations implement network and endpoint security technologies that focus on anomalous behaviors rather than relying solely on known malicious malware or attacker infrastructure.
Additional threat analysis of BRONZE UNION by Secureworks’ Counter Threat Unit (CTU) team:
27th February 2019 — A Peek into BRONZE UNION’S Toolbox
27th June 2017 — BRONZE UNION: Cyberespionage Persists Despite Disclosures
27th June 2017 — Chinese Threat Group Targeted High-Profile Turkish Organizations
05th August 2015 — Threat Group 3390 Cyberespionage
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

