SecureWorks® Counter Threat Unit™ (CTU) researchers continue to monitor activity associated with the BRONZE UNION threat group (formerly referred to as TG-3390) after investigating the group's compromise of an international industry organization's website between mid-2015 and late-2016. The group used the website to stage malware.
CTU™ researchers began tracking BRONZE UNION in 2013 and have observed the threat actors targeting organizations in the aerospace, defense, technology, and energy verticals, as well as organizations focused on international relations. Based on analysis of the group's espionage operations, targeting, and tools, CTU researchers assess BRONZE UNION is likely located in the People's Republic of China (PRC).
Use of compromised website
The threat group used the compromised website to deliver a malicious executable (named javaws.exe) to potential victims. The location of the malware on the website suggested that intended victims' systems were specifically directed to the file, likely via a strategic web compromise (SWC) on a separate website. CTU analysis determined that the file was a modified version of the legitimate Java Web Start framework software with functionality limited to downloading and executing second-stage malware. The javaws.exe file attempted to connect to 45 . 114 . 9 . 174 to retrieve the secondary payload. As of this publication, the second-stage payload has been removed and is not available for analysis. However, based on CTU researchers' understanding of the group's methods, it likely deployed one of the backdoor tools commonly leveraged by BRONZE UNION (e.g., HttpBrowser or PlugX) using DLL side-loading.
CTU researchers also identified the threat actors using the compromised website between July 22, 2015 and November 14, 2016 to temporarily stage tools that they could leverage while conducting their actions on objectives within other victims' environments. In July and September 2015, a file that appeared to be the OwaAuth web shell (named OwaAuth.dll) was retrieved from the compromised website, likely by the threat actors, and then deployed in other compromised environments (see Figure 1).
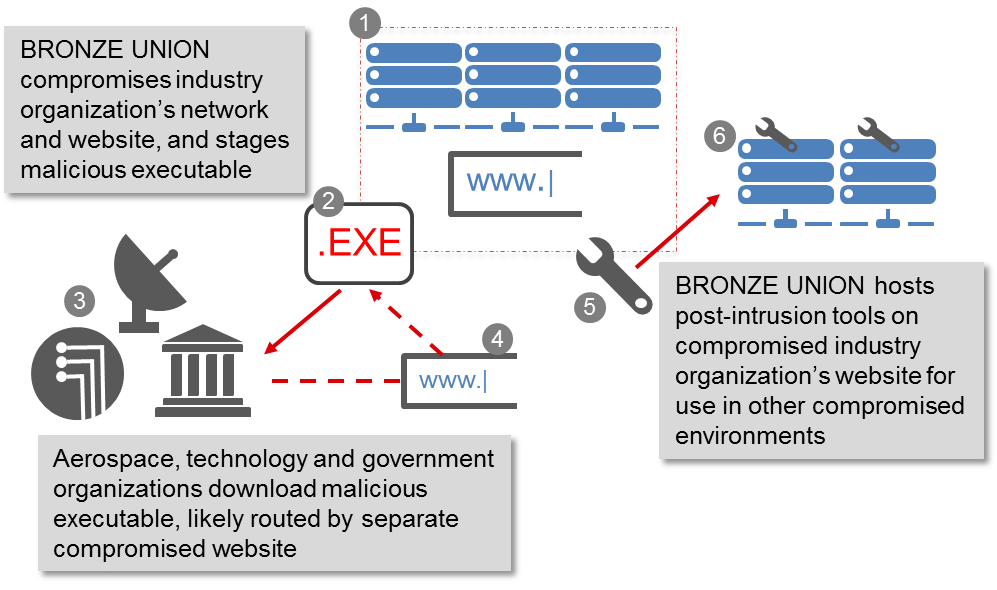
Figure 1. BRONZE UNION compromise and use of industry organization website. (Source: SecureWorks)
Affected organizations
Between late-July 2015 and mid-November 2016, CTU researchers observed the javaws.exe malware impacting aerospace organizations in the U.S. and UK, academic and media organizations in the PRC, and technology and media networks in Canada. Global organizations in the healthcare, government, and utilities verticals were also affected (see Figure 2).
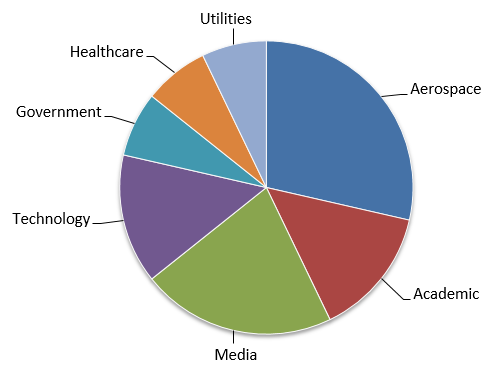
Figure 2. Organization types impacted by BRONZE UNION malware between July 22, 2015 and November 14, 2016. (Source: SecureWorks)
The targeting shifted between November 14 and 21, 2016. CTU researchers discovered that the malware hosted on the compromised website was primarily downloaded by Turkish government, financial services, and academic organizations. The frequency and consistency of the activity during this period strongly suggests that BRONZE UNION was focused on Turkish entities (see Figure 3).

Figure 3. Destination IP addresses associated with Turkish organizations accessing the malware between July 2015 and November 2016. (Source: SecureWorks)
During an eight-day period in November 2016, seventeen Turkish government IP addresses retrieved the javaws.exe file. Five Turkish banks and two Turkish academic networks were also affected (see Figure 4).
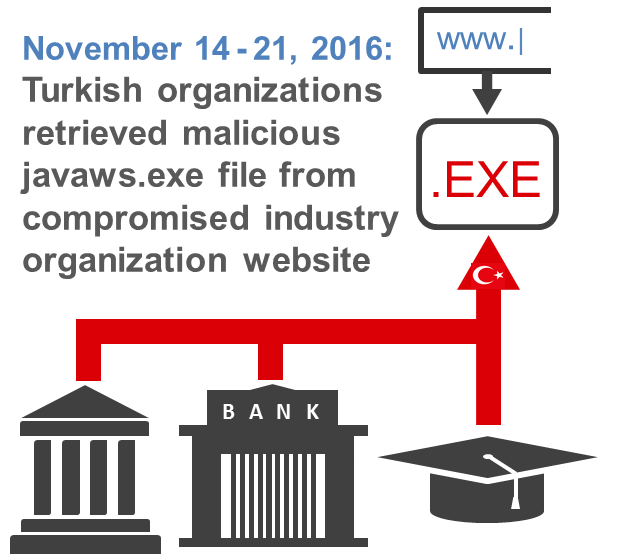
Figure 4. Targeting of Turkish entities in November 2016. (Source: SecureWorks)
BRONZE UNION's abrupt and concerted effort to compromise Turkish networks represents a notable shift in the group's targeting behavior and highlights the breadth of this threat group's intent towards organizations in Turkey. CTU researchers consider the following to be possible motives for this apparent demand for information from high profile Turkish networks:
- As a NATO member and U.S. ally that is geographically close to the Middle East and Syria, cyber threat groups are likely to view Turkey as a potential target for political and defense intelligence gathering.
- As a geographic conduit between the Middle East and Europe, Turkey is likely to be a significant priority for PRC-based businesses seeking to increase trade in these regions (dubbed the New Silk Road). Consequently, Turkish entities linked to trade and economic development topics could be targeted.
- CTU researchers have observed BRONZE UNION targeting the Uyghurs[1] in previous campaigns. Due to Turkic ethnic links, some Uyghurs have settled in Turkey and surrounding territories. Thus, Turkish government organizations, which maintain information relating to the activities of Uyghurs, would likely be of interest to the BRONZE UNION threat group.
Conclusion
BRONZE UNION is a highly capable threat group that is characterized by its use of strategic web compromises and web shells (particularly on Exchange servers), and its fast-paced operations. The range of organization types targeted in this campaign illustrates the breadth and scale of the threat group's intent and objectives. As of this publication, the group continues to use similar SWC techniques and the same javaws.exe malware used in the 2015 compromises.
Understanding a threat group's focus and methods can help potential victims detect and mitigate malicious activity. Organizations should evaluate the geopolitical conditions they operate in and identify data and systems that could be of interest to threat actors. CTU researchers recommend that organizations whose data, location, or connections could be of value to the BRONZE UNION threat group consider implementing continuous, intelligence-driven network monitoring, as well as advanced malware and endpoint threat detection tools as part of their mitigation strategy.
Threat Indicators
The threat indicators in Table 1 are associated with BRONZE UNION activity. Note that IP addresses can be reallocated. The IP address may contain malicious content, so consider the risks before accessing it in a browser.
|
Indicator |
Type |
Context |
|
javaws.exe |
Filename |
Malware used in BRONZE UNION SWC that downloads and executes a second-stage payload |
|
98c5f2a680fe9de19683120be90ea75c |
MD5 hash |
Malware used in BRONZE UNION SWC (javaws.exe) |
|
daa03d4aa72a16fff910142982b057b195018e6d |
SHA1 hash |
Malware used in BRONZE UNION SWC (javaws.exe) |
|
ec60e57419f24fabbe67451cb1055b3d2684ab2534cd55c4a88cc395f9ed1b09 |
SHA256 hash |
Malware used in BRONZE UNION SWC (javaws.exe) |
|
45 . 114 . 9 . 174 |
IP address |
Used by BRONZE UNION to host second-stage payload for SWC |
Table 1. BRONZE UNION indicators.
[1] Uyghurs are a largely Muslim ethnic group that is highly represented in the PRC's Xinjiang region. As a non-religious country, the PRC government allegedly imposes restrictions on religious expression and discriminates against Uyghurs regarding education, employment and housing opportunities. There are violent extremist Uyghur groups in the PRC, which the country's ruling Communist Party views as a significant domestic terrorist threat.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

