A few years ago, organizations didn't need much to stop threats. If their perimeters and endpoints were secured with a firewall, IDS, next generation endpoint protection and several other security, identity and access layers, and if regular attention was paid to patching, organizations had all they needed to stop most threats.
How times have changed!
An average enterprise today has around 761 cybersecurity tools to protect an ever-expanding IT infrastructure centered on the cloud and a highly distributed IT stack. With this in mind, it shouldn't be surprising that during 2022 Secureworks® Taegis™ customers experienced 55%2 of their security incidents coming from the cloud undetected by endpoint telemetry data.
There are now thousands of attack surfaces and methods for threat actors to gain access to and compromise highly distributed networks. However, what is not changing quickly enough is overreliance and preoccupation with endpoint detection and response security. Many organizations still believe that EDR will solve their security problems.
However, as our event data clearly shows, this assumption is false. It's time to look more strategically at your IT security operations in the context of your budgets, resources and threats and start building a more strategic cybersecurity foundation that will scale to threats today and in the future.
Real-World Causes of Breaches
Statistics from the Secureworks Taegis platform customer base of over 4,500 global organizations and first-hand experience from our incident response and adversarial testing teams clearly illustrate the insufficiency of endpoint protection and endpoint detection and response security alone.
-
88%1 of Business Email Compromise (BEC) incidents happened through phishing, or the use of stolen, guessed or purchased credentials.
As these attacks do not involve endpoint malware and often occur on cloud-based resources (like Microsoft365), the data needed to detect and respond to these attacks is commonly found in the audit logs related to authentication events. Detecting suspicious login activity or events touching cloud resources, such as the creation of suspicious email forwarding rules, is not a role endpoint or endpoint telemetry data is designed to solve.
-
52%2 of incidents affecting customers started with access to an exploited vulnerability.
If your organization can automatically patch any vulnerabilities in your systems or applications, then you may be able to avoid many exploit incidents. A recent study conducted for ServiceNow by the Ponemon Institute in 2022 showed that 57% of cyberattack victims reported their breaches could have been prevented by installing an available patch and that 74% of companies cannot patch fast enough due to a lack of staff.
-
39%2 of ransomware incidents involved the abuse of credentials.
These credentials were typically acquired through on-premises systems such as VPN logins. Accurate credentials detection telemetry comes from logs from identity providers, on-premises active directory and initial detection from network monitoring logs, and less often or reliably from any endpoint controls.
Moving Beyond the Endpoint
It's easy to point a finger at an over reliance on endpoint protection and EDR, but in fact there are several other security issues that exist at most organizations today that are making their entire IT security stack inefficient at delivering the early detection and responses to threats and attacks they need.
Organizations themselves are now realizing this, as no matter how much budget they allocate on IT security, their effectiveness doesn't increase in line with spend.
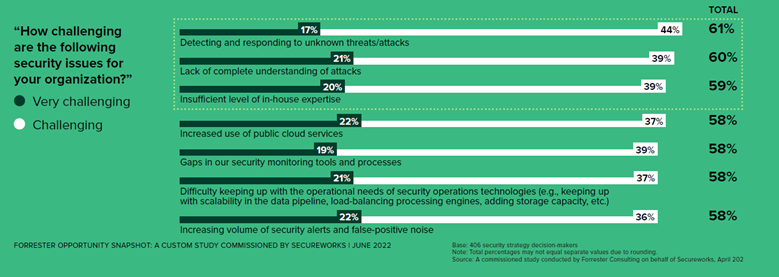
An independent survey commissioned from Forrester3 in April 2022 uncovered where organizations were focusing their security implementations, and why. The survey showed that organizations faced fundamental challenges: detection, rapid response and understanding attacks and having the right in-house resources and expertise to respond effectively to threats.
Secondary challenges were digital transformation, the secure use of public cloud services, gaps in security toolsets, and efficiently operating toolsets — especially while suffering from alert and analyst overload. For many, managing defenses and a typical IT security stack is difficult, inefficient, and worst of all ineffective in relation to security requirements and needs.
This overall insufficiency (along with that of EDR) is just another symptom of these larger cybersecurity challenges. Challenges that led us to ask in the Forrester survey, ”Just what are organizations looking for, what is on their wish list to change in this situation?”
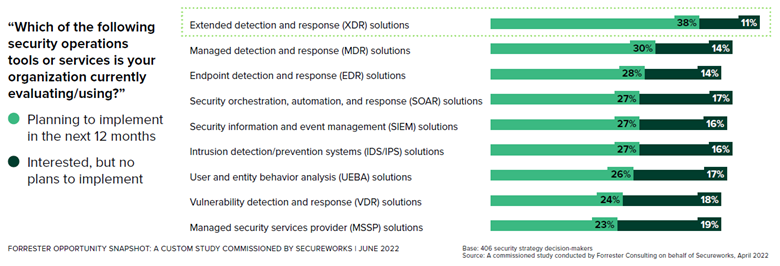
The answers were clear: most organizations are looking for help from tools or partnerships.
As the table shows, 68% of respondents are looking to implement an extended detection and response (XDR) or a managed detection and response (MDR) solution in the next 12 months.
Supplemental information also showed that organizations are currently seeking to invest in these offerings to give them full visibility across their entire IT landscape (an EDR shortcoming). And then, to work with a third-party security partner to manage their XDR solution partly, or fully, for 24/7/365 detection and response. The full Forrester report can be found here.
It's clear that moving beyond endpoint security is now a necessity. The harsh reality is cybersecurity is changing fast and there are a growing number of issues that organizations need to address urgently to run an effective SecOps department. No matter how you proceed or what vendor you choose, it's critical to realize that effectiveness and efficiency will ultimately come from a transparent partnership that steps up and clearly shows they are always in the fight with you.
To learn more about Secureworks Taegis you can talk to a security expert or read our white paper "It’s Time for Your Cybersecurity to Move Beyond the Endpoint."
1 Source: Panaseer Security Leaders Peer Report 2022
2 Source: Secureworks customer incident response data Jan-Oct 2022
3 Source: Forrester Opportunity Snapshot: Wise XDR Choices Lead To More Benefits Than Expected.
(A 2022 custom study commissioned by Secureworks)
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

