SecureWorks® Counter Threat Unit™ (CTU) researchers have observed threat actors redoubling their efforts when they hit "roadblocks" such as containment and eviction measures.
Dealing with this type of determination sets targeted threat response apart from response to malware infections. After malware deployed by an opportunistic threat is removed and systems are patched, the incident is typically contained and remediated. However, incidents involving targeted threat actors reveal why these threat actors are referred to as "persistent adversaries:" when faced with some sort of disruption (containment, eviction, etc.), the threat actors often change their tactics, techniques, and procedures (TTPs).
During one engagement, CTU™ researchers deployed Red Cloak in a client environment to assist with containment and eviction procedures regarding a targeted threat group. However, the group returned to the infrastructure, as is often the case with a persistent adversary. The threat actors realized they were being detected and began to investigate instead of running away. They started by disabling the "Cylance PROTECT" service on the system that was compromised (see Figure 1).
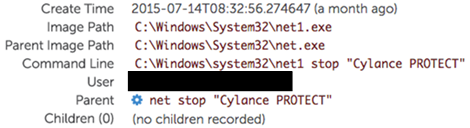
Figure 1. Adversary disables security service on compromised system. (Source: SecureWorks)
Following eviction and re-entry, CTU researchers observed the adversary collecting information by archiving the contents of the C:\Cylance folder ("temp.log" is a renamed copy of the WinRAR archive utility), apparently in an attempt to determine how they had been discovered. The threat actors used the command shown in Figure 2.
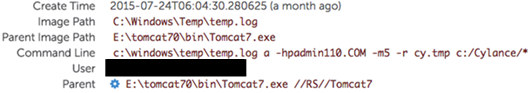
Figure 2. Adversary collecting information for exfiltration. (Source: SecureWorks)
The adversary had apparently reviewed the information collected from the Cylance product and did not find evidence to indicate that they had been detected through that source. The threat actors then returned to the infrastructure to see if they had been detected via some other means, such as the installed antivirus product. CTU researchers observed the adversary using commands on the same infrastructure, a week later, to collect information from a Kaspersky Security Center product (see Figure 3).

Figure 3. Adversary collecting information from another source. (Source: SecureWorks)
In Figure 3, the file "sprvm_5948335.log" is a renamed copy of the WinRAR archive utility, and the command archives the contents of a Kaspersky product remote installation folder.
Using Red Cloak, CTU researchers were able to detect the escalation of defensive evasion tactics employed by a targeted threat group. The threat actors seemed to have some sense that they had been detected, as CTU researchers observed them disabling security services, as well as collecting, archiving, and exfiltrating information from security tools and installed antivirus products. Targeted threat actors who have been tasked with achieving an objective will work to overcome any hurdles that stand between them and their mission.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

