Summary
The GOLD MYSTIC threat group has operated the LockBit name-and-shame ransomware-as-a-service (RaaS) scheme since mid-2019, exploiting unauthorized access to thousands of organizations to deploy ransomware and steal data to facilitate the extortion of victims. At approximately 4:00 pm EST on February 19, 2024, the UK's National Crime Agency (NCA) and U.S. Federal Bureau of Investigation (FBI), in conjunction with international law enforcement partners, took disruptive action against the infrastructure used by the LockBit RaaS operation.
Secureworks® incident responders investigated 22 compromises featuring LockBit ransomware from July 2020 through January 2024. These investigations revealed the tactics, techniques, and procedures (TTPs) that LockBit affiliates have used in their intrusions. The complexity of operations varies from manual encryption of individual hosts to automated ransomware deployments from domain controllers. In some incidents, ransomware is not deployed at all. Instead, affiliates rely on data theft alone to extort victims. LockBit's evolution includes targeting VMware ESXi hosts to encrypt virtual machines, which can have a devastating impact on organizations that rely heavily on virtualized infrastructure. As the LockBit brand has grown in stature, copycat cybercriminals have sought to exploit the name for their own ransomware operations or other extortion threats.
Law enforcement action
During the disruptive action, law enforcement placed a seizure notice on the leak site and its mirrors, and informed affiliates via the LockBit panel that the NCA was aware of their activities. As of this publication, the website hosting an archive of victim data is still available. At 6:30 am EST on February 20, the seizure notice on the LockBit leak site was replaced with a series of tiles in the style of the original leak site. The tiles link to explanations for the various aspects of the law enforcement activity. The operation disrupted the LockBit ransomware operation by taking down its infrastructure, targeting specific individuals, seizing funds, and promising further sanctions. A version of this Threat Analysis was hidden behind one of the tiles (see Figure 1).

Figure 1. LockBit leak site after the law enforcement seizure and rebranding. (Source: Secureworks)
Background
The GOLD MYSTIC threat group began ransomware operations in 2019, adopting the LockBit name for its file-encrypting malware in 2020 and listing its first victims to the leak site in September 2020. The first iteration of LockBit did not have substantial impact, with only nine victim names posted to its leak site in the first five months of operation. In June 2021, GOLD MYSTIC launched LockBit 2.0 following six months of apparent inactivity. The threat actors claimed that this enhanced version of the ransomware was easier to use and implemented faster encryption. The number of victims named on the leak site increased significantly from that moment.
GOLD MYSTIC named over 2,350 victims across 112 countries between the LockBit leak site's inception and the end of 2023, far exceeding its closest competitor (see Figure 2) and accounting for just over one fifth of victims named across all leak sites since name-and-shame ransomware was introduced to the cybercrime ecosystem in May 2019.
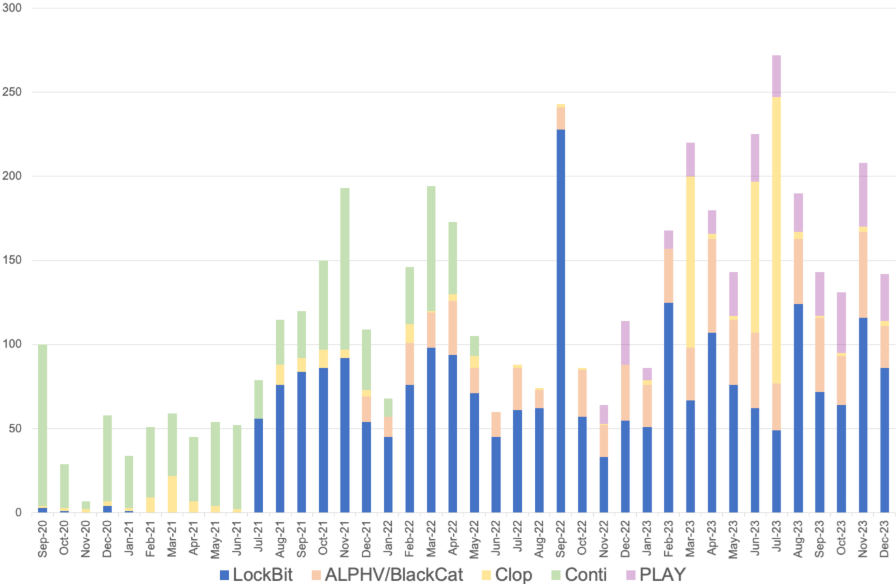
Figure 2. Number of victims posted by the top 5 name-and-shame ransomware groups from September 2020 through December 2023. (Source: Secureworks)
As of this publication, the data of over 700 past victims remains available for download from servers operated by GOLD MYSTIC on the Tor network. In February 2023, Canada's cybersecurity intelligence agency, the Communications Security Establishment (CSE), claimed that LockBit was responsible for 44% of all global ransomware attacks.
While GOLD MYSTIC did not introduce the RaaS concept, the group's devolved operating model changed the landscape and allowed LockBit to become the most prolific ransomware operation. Unlike other ransomware groups, GOLD MYSTIC ceded control to its affiliates, making them responsible for handling both negotiations and payments. While ostensibly setting certain rules of engagement, including forbidding the encryption of organizations involved with electric power generation, petroleum manufacture and distribution, and delivery of acute medical care, GOLD MYSTIC exercised little oversight over affiliates' actions or choice of victims. This approach allowed the group to scale operations significantly, incorporating dozens of affiliates over the years. However, it did introduce an element of chaos into the operation.
In December 2022, a LockBit affiliate targeted a children's hospital in Toronto. The LockBit operators subsequently apologized, issued a free decryptor, and purportedly expelled the attacker from their affiliate program. Several months later, the LockBit operators seemed unaware of a high-profile attack one of their affiliates had perpetrated against Royal Mail, originally denying the company was one of their victims before later admitting it (see Figure 3).
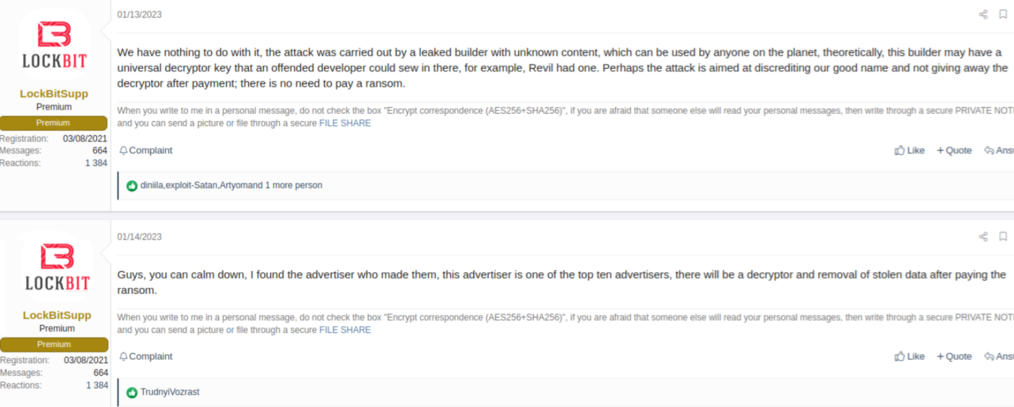
Figure 3. The LockBitSupp persona first denying the group's involvement in the attack on Royal Mail and subsequently admitting it. (Source: Secureworks)
The increase in affiliates and the prolific targeting also reportedly posed significant challenges for GOLD MYSTIC's infrastructure. Storage issues rendered many claims of data publication on the leak site false, with no information being hosted once the deadline for payment passed. Affiliates publicly complained about the lack of support they were getting through the LockBit scheme. However, the lack of published data suggests another possibility: in some cases, there may not have been data to publish. Without insight into a specific compromise, it is hard to draw conclusions about the efficacy of a ransomware deployment or data exfiltration attempt. It is likely that the impact on some named victims was minimal. The leak site lists victims that have not paid the ransom, suggesting that they may have recovered without the need for a decryption key and had little concern about the publication of stolen data.
It is clear that LockBit branding was a key component of GOLD MYSTIC's operating model. In fact, creating the impression of devastating impact by the sheer volume of attacks might have been more important than the impact to individual victims. Encouraging victims to pay is essential, and keeping LockBit in the news cycle is useful in achieving that goal. The threat actors' self-promotion and criticism of competitors may also be driven by egoism and a desire to attract affiliates in a competitive cybercrime market.
Nevertheless, LockBit RaaS affiliates have engaged in many thousands of network compromises. Secureworks' visibility into multiple LockBit intrusions provides insight into the TTPs that affiliates have used.
LockBit operations
Secureworks Counter Threat Unit™ (CTU) researchers have observed the activities of multiple LockBit RaaS affiliates since mid-2020. The range of TTPs is broad, and the ultimate success of operations varies. Some LockBit deployments inflicted irreparable harm on victims' networks, while others caused minimal impact and were quickly remediated. The same is true for data exfiltration. Given the number of affiliates, CTU™ researchers expect to observe a wide range of capabilities in LockBit intrusions.
Ransomware deployments
Secureworks incident responders have observed complex, technically advanced, and high-impact deployments of LockBit ransomware. These deployments involved methods that enabled broader reach than can be achieved by navigating to individual hosts to detonate instances of the ransomware binary.
In Incident O in mid-2023, Secureworks incident responders observed a threat actor use access to two domain controllers to automatically distribute LockBit ransomware throughout a victim's network. Although encryption events, a lack of endpoint visibility, and the absence of centralized logging significantly hindered forensic analysis, Secureworks incident responders were able to infer some of the tools the threat actor deployed in the compromise:
- Advanced Port Scanner — an off-the-shelf tool to identify open ports and determine the versions of software running on the system
- Impacket — a collection of modules written in Python that include tools for remote execution, credential dumping, Kerberos manipulation, and relay attacks
- LaZagne — a tool to collect passwords from a network
- FileZilla — a free, open-source FTP solution for transferring files
- LockBit ransomware
Multiple files containing outputs from the first three tools were found in the environment, suggesting their repeated use. After installing FileZilla, the threat actor gathered numerous files, some of which contained company billing information, into a single network folder. Although no evidence of data exfiltration was found, this activity likely constituted the staging for such activity. Given the absence of logs, it is possible that data was stolen from the network but remained undetected.
Four and a half hours after the first observed malicious activity, the threat actor deployed the ransomware from two domain controllers to multiple hosts in the environment, likely via batch scripts. The timing of the encryption of some hosts suggested automation. Just prior to detonating the LockBit ransomware, the threat actor uninstalled the Cisco Secure Endpoint solution. While evidence indicated that only the Windows version of the ransomware was deployed, a Linux executable was also discovered on the network.
Incident G in early 2022 demonstrated how LockBit ransomware operations are facilitated by the wider cybercrime ecosystem. A network administrator at an organization in the Middle East downloaded cracked software that was hosted on the Discord content delivery network (CDN). This software was bundled with the RedLine infostealer malware in a ZIP file. Bundling infostealers with cracked software is a common method of delivery and often results in the unwitting user exposing system information alongside credentials, cookies, and session tokens stored in a web browser. This data typically relates to personal use such as private webmail and social media accounts, but work credentials can be exposed when personal devices are permitted to access corporate assets. In this incident, it is likely that RedLine was opportunistically delivered and that the resulting log containing valuable credentials was subsequently bought from an underground marketplace by a LockBit affiliate.
Approximately a week after the administrator inadvertently downloaded RedLine, the affiliate exploited the stolen credentials to access the compromised organization's Citrix App server, which was protected with only single-factor authentication. As the account already had administrator privileges, there was no need to escalate privileges post-compromise. All subsequent malicious activity was conducted using this single, compromised account.
After gaining access to the Citrix App server, the threat actor moved laterally via Remote Desktop Protocol (RDP) to a Windows server, where they used the Bing search engine in Internet Explorer to conduct a search for domain temp . sh (see Figure 4). However, the security controls on the server blocked access to this domain and its contents.
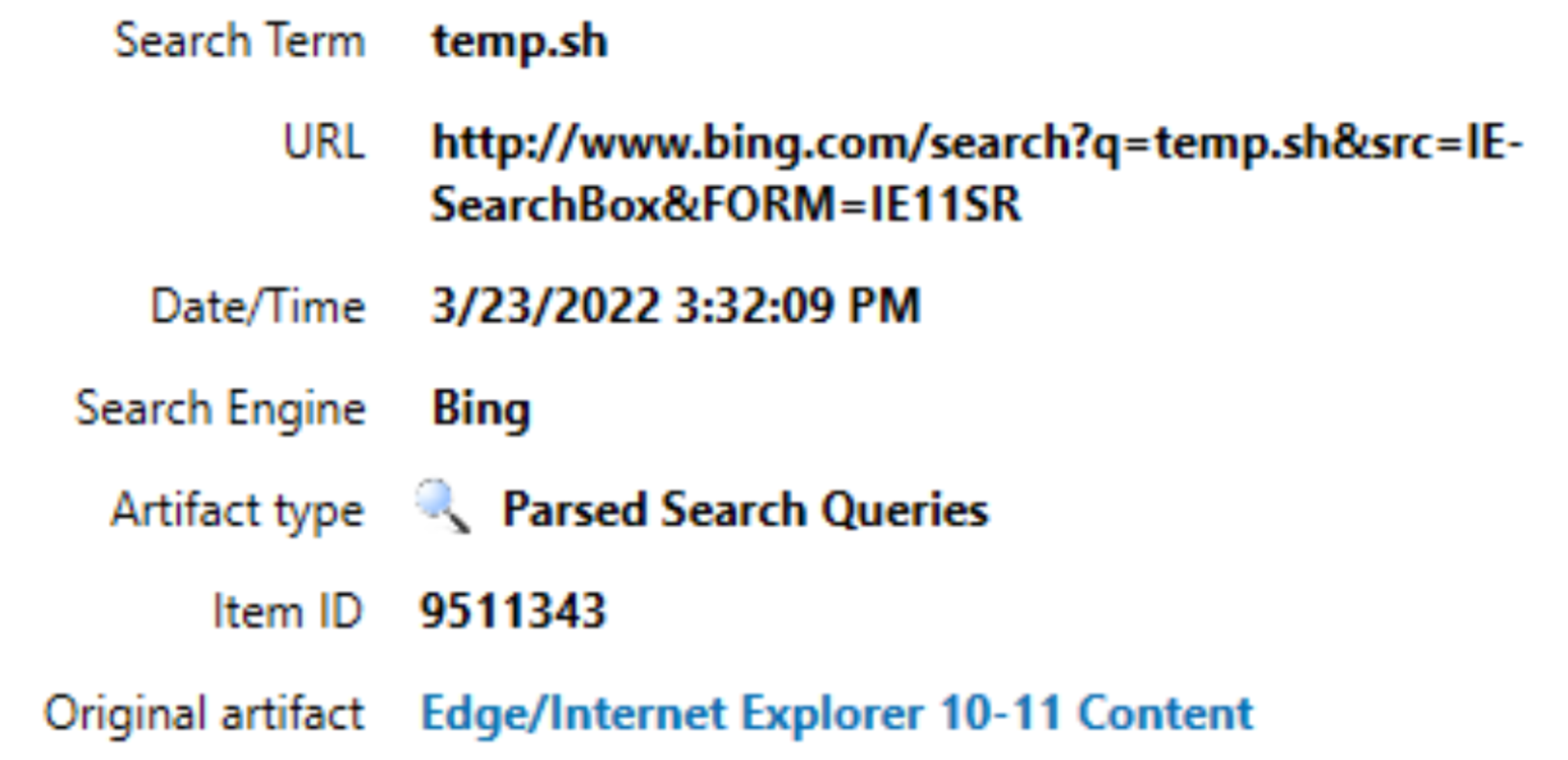
Figure 4. Search for the temp . sh folder via Internet Explorer. (Source: Secureworks)
Not to be put off, the threat actor ran the Nltest utility to enumerate domain controllers and then navigated to two of them via RDP. It is not known what activity took place on these devices, as they had been restored before Secureworks incident responders had an opportunity to analyze them. Several hours later, the threat actor moved laterally via RDP to a different server. Fewer security controls were running on this server, so the attacker was able to navigate to temp . sh and download the files hosted there to a local staging folder. These files were the tools the threat actor used to conduct their ransomware attack:
- SoftPerfect Network Scanner — an open-source network discovery tool
- Mimikatz — a credential harvesting tool
- AdFind — a tool to query Active Directory
- PsExec — a legitimate SysInternals utility used for remote execution
- CleanWipe — a legitimate Symantec tool to disable its endpoint protection solution
- StealBit — a tool developed by GOLD MYSTIC to facilitate data exfiltration in LockBit ransomware intrusions
- LockBit 2.0 — the ransomware used to encrypt devices on the victim's network
Before deploying the ransomware, the threat actor spent a day exploring multiple files on the network in search of sensitive information to exfiltrate. This research encompassed folders on approximately 40 different hosts. The data was exfiltrated over a 90-minute period, likely via the StealBit tool, prior to execution of the ransomware. The attacker used batch scripts to run PsExec, which propagated and deployed the ransomware to numerous hosts. The IP addresses of the targeted hosts were listed in a text file that the threat actor had created during the discovery phase of the intrusion.
The time from the first recorded malicious activity (one week after the infostealer obtained the administrator credentials) to the deployment of ransomware was less than two days. Despite the apparent care the threat actors took to identify the data they wanted to steal, the victim claimed it was not sensitive and was of little value. Following non-payment of the ransom, GOLD MYSTIC named the victim on the LockBit leak site and published the stolen data.
Not all LockBit affiliates use GOLD MYSTIC's custom StealBit tool to exfiltrate data, despite the group encouraging them to do so on the affiliates page of the public LockBit leak site. When investigating LockBit Incident N in mid-2023, Secureworks incident responders identified the legitimate Rclone data transfer tool on the victim's network. There was no evidence of its use, but the analysis confirmed that it was placed in the environment by the threat actor. The fact an affiliate likely chose to use Rclone as an alternative to StealBit for data exfiltration might relate to the data storage issues that GOLD MYSTIC experienced in mid-2023. StealBit purportedly automatically uploads stolen data to LockBit infrastructure in preparation for publication on the leak site.
VMware ESXi targeting
Ransomware groups have developed versions of their tooling that are compatible with VMware ESXi devices, and GOLD MYSTIC is no exception. The group launched Linux and VMware ESXi-compatible versions of LockBit in late 2021.
This evolution was a logical step. First, the increased rollout of endpoint detection and response (EDR) services on Microsoft Windows devices likely had an impact on ransomware groups' operations. The Secureworks Taegis™ XDR solution has alerted many customers to precursor activity, enabling speedy intervention and remediation that likely prevented damaging ransomware deployments. Ransomware groups identified the need to circumvent this technology to successfully encrypt networks. One solution was to spend as little time as possible on monitored hosts and navigate to areas of the network less equipped to detect malicious activity, such as virtualized environments. Second, threat actors realized that encrypting VMware ESXi devices can have a devastating impact on a victim's network. Depending on how an organization's virtualized environment is configured, encrypting a single host may take all virtual machines offline and effectively halt business operations.
Multiple Secureworks incident response engagements have involved ransomware affiliates attempting to target VMware ESXi devices with LockBit. In Incident M in early 2023, a LockBit affiliate was able to access a victim's network through their Fortinet VPN before conducting discovery on the network and encrypting a single VMware ESXi device that hosted 25 virtual machines. Files on three Windows domain controllers were also encrypted and replaced with a ransom note. In a similar compromise later that year (Incident Q), a threat actor likely abused existing VPN credentials for access before exfiltrating data and encrypting all virtual machines in the environment.
In late 2022's Incident J, another LockBit affiliate targeted an organization's virtualized environment in an extortion attempt. The malicious activity started from a device used for training purposes when a domain administrator account attempted to connect to a domain controller via RDP. The training device did not have an EDR solution running on it, so activity conducted at this endpoint went undetected. Once successfully authenticated on the domain controller, the attacker executed a network scanning tool before moving to four additional hosts via RDP. The attacker then used Mozilla Firefox to navigate from the domain controller to IP addresses associated with VMware ESXi hosts before creating a new account and adding it to the domain admin and "ESX Admin" groups. Secureworks incident responders did not observe additional activity associated with this account. The threat actor reverted to the original compromised administrator account.
While on the domain controller, the threat actor installed and executed MobaXterm. This legitimate application facilitates SSH connections and allows a user to launch remote sessions and execute Unix commands on a Windows desktop. Shortly after this tool was installed, the attacker connected to three VMware ESXi hosts via SSH over port 22. They then launched the WinSCP service, which is an open-source FTP client for Windows. However, Secureworks incident responders did not observe evidence of data staging or exfiltration. Virtual machines hosted on some of the ESXi hosts were encrypted via unknown means, and the LockBit ransom note was delivered to devices.
Ransomware failure to launch
In mid-2020, when LockBit was still a fledging operation using the first iteration of its ransomware, Secureworks incident responders investigated a compromise (Incident A) in which an attacker attempted but failed to deploy LockBit ransomware.
The threat actor was able to gain access to a Citrix server using likely compromised credentials. There was little subsequent hands-on keyboard activity and no evidence of network discovery or lateral movement. The attacker executed an unknown binary, installed the AnyPlace Control remote access software, and deployed LockBit ransomware. There was no evidence that the AnyPlace Control software was used. The execution of LockBit was successful, as the following initial automated functions began to execute. However, no files were encrypted, and it is unclear why the ransomware failed.
- Establish persistence via the registry Run key
- Prevent restoration of the host from backups and recovery states:
-
vssadmin delete shadows /all /quiet
-
wmic shadowcopy delete
-
wmic SHADOWCOPY /nointeractive
-
bcdedit /set {default} bootstatuspolicy ignoreallfailures -
bcdedit /set {default} recoveryenabled no -
wbadmin delete catalog -quiet
-
- Modify the boot configuration for the host to prevent recovery and failure notifications:
-
bcdedit /set {default} recoveryenabled No -
bcdedit /set {default} bootstatuspolicy ignoreallfailures
-
- Delete system backups:
-
wbadmin DELETE SYSTEMSTATEBACKUP
-
- Clear system, security, and application logs via wevtutil
Later in 2023, the same organization was targeted by the GOLD DUPONT threat group, which distributes the RansomExx ransomware. Although the entry point was similar — access to a Citrix server — it is unlikely the same affiliate was responsible given the significant difference in TTPs.
Data theft-only
Not all LockBit affiliates seek to encrypt systems with ransomware. While taking business operations offline provides a strong incentive for ransom payment, GOLD MYSTIC ultimately strives to monetize any access its affiliates can obtain. This approach lowers the bar to entry, allowing threat actors without significant technical skill to conduct extortion operations.
In Incident R in late 2023, Secureworks incident responders observed an affiliate gain access to a network by exploiting the 'Citrix Bleed' buffer overflow vulnerability (CVE-2023-4966) in NetScaler ADC and NetScaler Gateway. Exploiting the flaw is trivially easy and exposes session authentication tokens that can be used for access in place of credentials, even bypassing multi-factor authentication (MFA). While patching can prevent further exploitation of the vulnerability, any session tokens stolen prior to patching can still be used for access unless explicitly terminated.
The initial compromise in this intrusion occurred after the flaw was made public and exploit code was released. After gaining access via Citrix Bleed, the threat actor conducted network discovery using the SoftPerfect Network scanner and then moved laterally from the NetScaler appliance to a different host. Once on this new host, the attacker set up unattended access using the legitimate Zoho Assist remote access application, configuring the tool through the registry to ensure persistence on reboot. They then used Zoho Assist's ToolsIQ.exe component to launch a command prompt and conduct reconnaissance, including establishing a list of current users and domain controllers.
Approximately one hour later, a batch script (1.bat) was created on a different server. This simple script distributed a file (IMPORTANT_README.txt) to folders within a network share (see Figure 5).
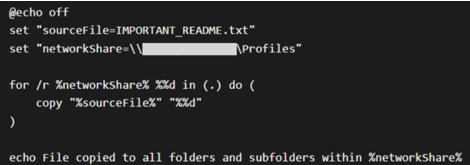
Figure 5. 1.bat script to deploy IMPORTANT_README.txt to network share folders. (Source: Secureworks)
This text file was a LockBit ransom note that included URLs to official LockBit payment portals (see Figure 6). The note did not mention encryption or demand payment for decryption keys. Instead, it implied that stolen data would be published if the victim did not pay the ransom.
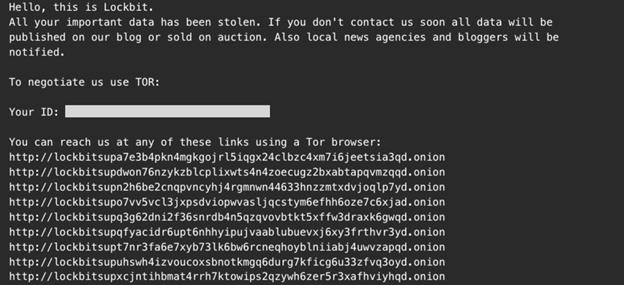
Figure 6. LockBit ransom note claiming data theft. (Source: Secureworks)
As in Incident N, the affiliate chose not to use StealBit to exfiltrate data. However, in this incident they relied on the legitimate MEGAsync service to steal and store the data for ransom.
This data theft-only intrusion highlights an important aspect of the behavior of ransomware groups in general. If an affiliate is unable to deploy ransomware, the ransomware fails, or the affiliate decides to rely on data theft alone to extort victims, the RaaS operators will not turn them away if there is an opportunity to make money. In some respects, the brand of the leak site is more important than the brand of the ransomware. In fact, in early 2023, the head of the LockBit operation, who uses the ‘LockBitSupp' underground persona, claimed that they were agnostic about the ransomware that their affiliates used as long as the affiliates used the LockBit platform to name victims and expose the stolen data (see Figure 7).
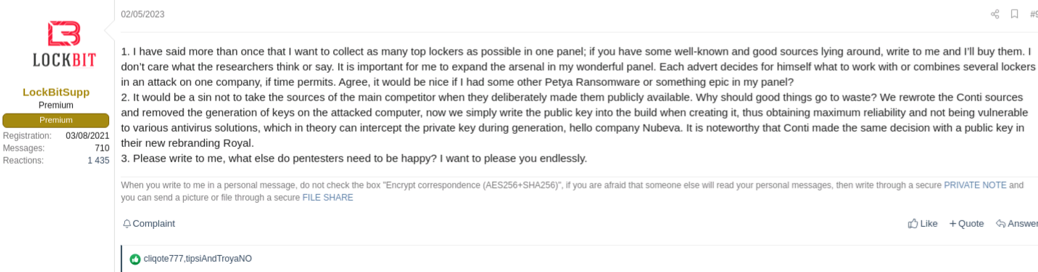
Figure 7. LockBitSupp stating they want to make multiple ransomware variants available to LockBit affiliates. (Source: Secureworks)
In late 2023, LockBitSupp also encouraged affiliates of the ALPHV (also known as BlackCat) and NoEscape RaaS schemes to use the LockBit leak site to post their victims' names and continue the extortion process (see Figure 8). The post followed law enforcement's takedown of the ALPHV infrastructure and the exit scam perpetrated by NoEscape's operators. RaaS operators, especially the LockBit operators, do not seem to care how or why victims are added to their leak sites if there is potential for financial gain.
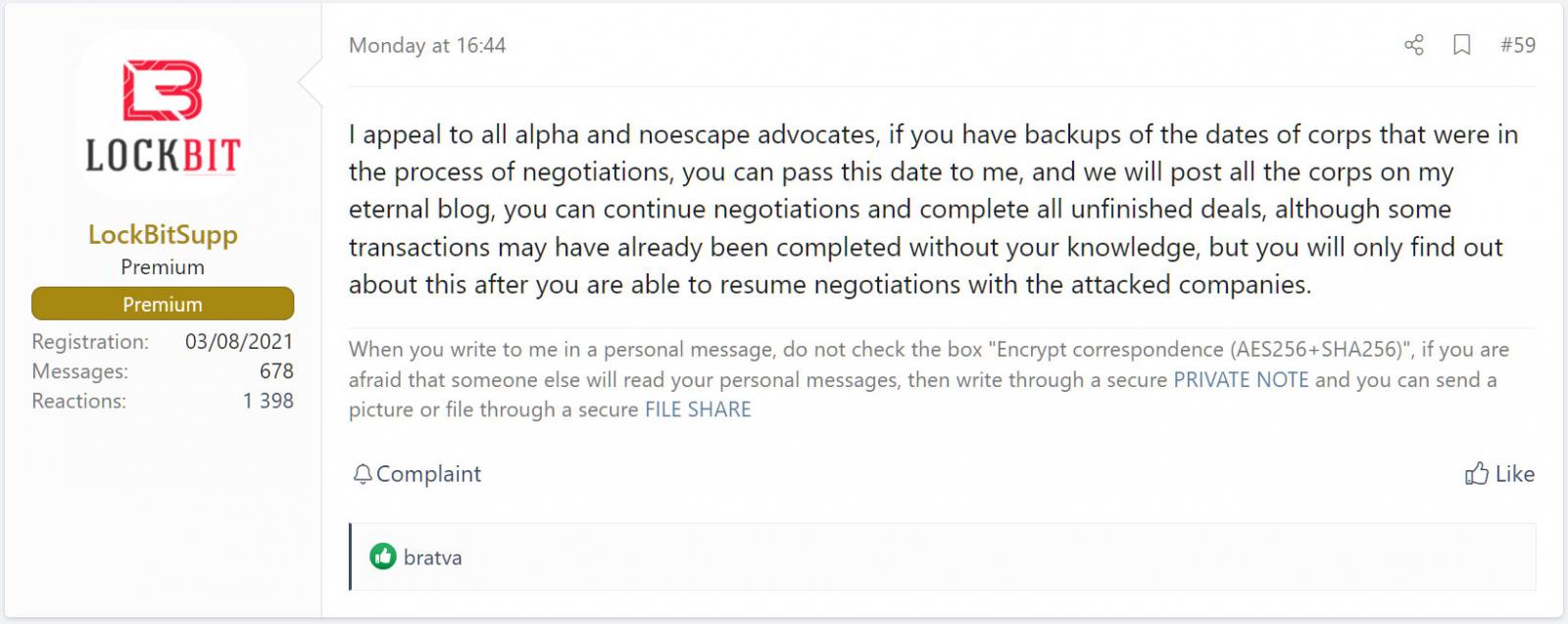
Figure 8. LockBitSupp offer to ALPHV and NoEscape affiliates. (Source: Secureworks)
Fickle affiliates
Affiliates do not need much encouragement to flit between RaaS operations. Monetizing their "work" takes priority over loyalty to a particular scheme.
In mid-2021, just after the launch of LockBit 2.0, Secureworks incident responders investigated Incident C, which involved the deployment of the ransomware via a Gootloader infection. Artifacts associated with the deployment suggested that a former affiliate of the REvil RaaS was responsible.
The infection started when a user searched for a specific document online. Search engine optimization (SEO) poisoning directed the user to a URL on a compromised WordPress site that hosted a ZIP file containing a malicious JavaScript file. Executing the JavaScript initially downloaded PowerShell scripts from three remote locations. When run, the PowerShell scripts started an infection chain that resulted in the execution of Cobalt Strike Beacon.
The threat actor conducted network discovery using Advanced IP Scanner before moving laterally in the network via RDP. A version of Free Files Sync was installed, but there was no evidence of its use and no data exfiltration activity was observed. A week later, the threat actor deployed LockBit ransomware and printed hundreds of copies of the ransomware on networked printers using a technique known as print bombing.
By investigating the supporting infrastructure, CTU researchers identified links to an intrusion from earlier that year that involved the deployment of REvil ransomware. This connection suggested that a REvil RaaS affiliate switched to LockBit after the former operation shuttered on July 13, 2021.
Incident H in late-2022 involved the compromise of a WMware Horizon instance and the deployment of LockBit 3.0 ransomware. The deployment was fairly limited in scope and had low impact on the victim's operations. However, just 12 hours after the LockBit deployment, ALPHV ransomware was detonated in the environment. The absence of data prevented a conclusive assessment on attribution. While it is possible that a different threat actor was responsible for the ALPHV deployment, it was more likely the same affiliate given the time frame. Furthermore, the victim was named on the LockBit leak site but not the ALPHV site.
In an engagement (Incident T) in late 2023, Secureworks incident responders observed a LockBit ransom note delivered to a network shortly after data was exfiltrated. There was no evidence of ransomware deployment. Approximately two weeks later, the organization received a ransom demand from the Hunters International ransomware group. There was no evidence to suggest that two different groups were involved. Given that there was no deployment of ransomware, the purpose of two threats of data release is unclear, particularly as the victim was not named on either leak site. However, CTU researchers are aware of at least one other victim that was named on both the LockBit and Hunters International leak sites.
In September 2023, the U.S. Federal Bureau of Investigation reported that they had observed affiliates deploying two or more variants of ransomware in their intrusions. LockBit was listed as one of the variants, although neither ALPHV nor Hunters International were mentioned. The FBI indicated that the dual deployments "resulted in a combination of data encryption, exfiltration, and financial losses from ransom payments," but it is not clear whether they are more successful as a tactic than single-variant encryption.
Copycats
The LockBit brand is powerful. As a result, it is exploited by other cybercriminals seeking to monetize the threat it poses. CTU researchers have observed two forms of copycatting. One is arguably more serious than the other and involves a threat actor deploying ransomware in an environment, purporting to be LockBit, and hoping that referencing a prolific and well-known ransomware scheme will be enough to convince victims to pay. The other threatens malicious activity under the LockBit name but does not actually involve ransomware-related activity such as data encryption or theft.
In Incident K at the end of 2022, a threat actor deployed LockBit 3.0 ransomware in a victim's environment. The deployment was unsophisticated and the impact was limited, as the attacker navigated to individual hosts to deploy the ransomware rather than using a mechanism to distribute it automatically network-wide. A desktop splash screen appeared on each encrypted host referencing LockBit Black (another name for LockBit 3.0) as the ransomware, but the text file ransom note that was generated did not (see Figure 9).
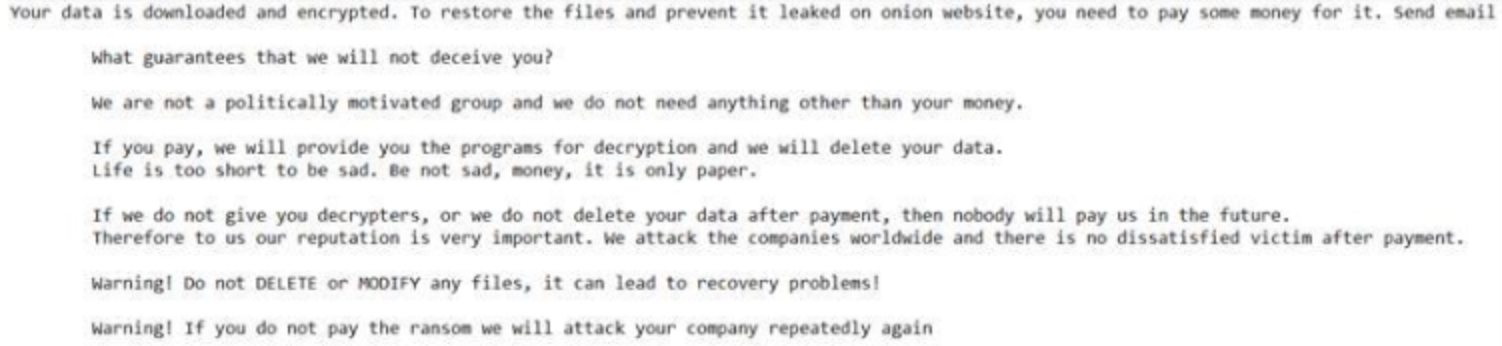
Figure 9. LockBit copycat ransom note. (Source: Secureworks)
Importantly, the ransom note also did not contain the usual links to the .onion portals through which victims communicate with LockBit affiliates to negotiate payment in return for the decryption key. In this case, the victim was instructed to send an email. This is unusual and suggests that the threat actor was a copycat using the LockBit ransomware and name to pressure the victim to pay. The LockBit 3.0 builder was leaked a few months earlier, apparently by a disgruntled developer, which enabled any attacker to use it.
Some groups go even further to masquerade as LockBit, building convincing-looking support infrastructure to pressure victims into payment (see Figure 10). The great lengths that groups go to mimic LockBit is a testament to the power of the brand that GOLD MYSTIC has cultivated through high-profile and prolific attacks.
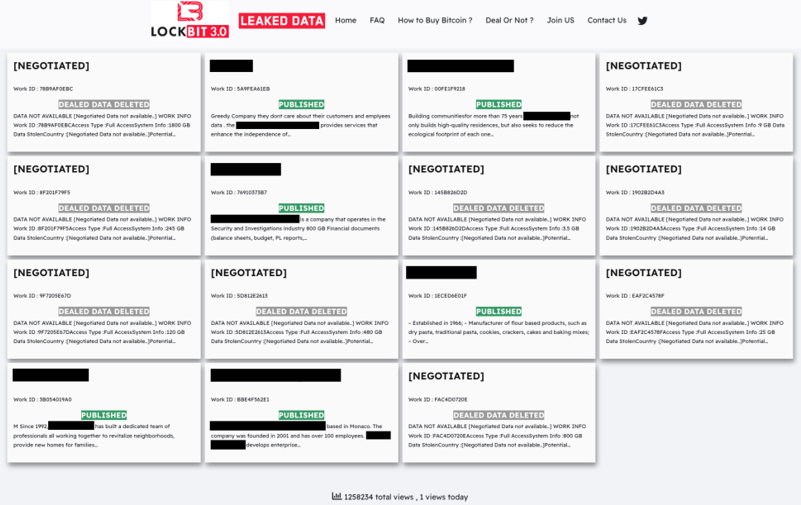
Figure 10. Copycat site hosted at lockbitblog . info as of January 31, 2024. (Source: Secureworks)
CTU researchers first observed threat actors using the second copycat approach in October 2022. The simple scam involved an email allegedly from the "LockBit hacker group" that demanded 25 bitcoins (worth approximately $515,000 USD at the time) to prevent a ransom attack and the release of stolen data (see Figure 11). After the deadline passed without payment, no ransomware was deployed and no data was published online. It is likely that this email template was used to target multiple organizations worldwide.
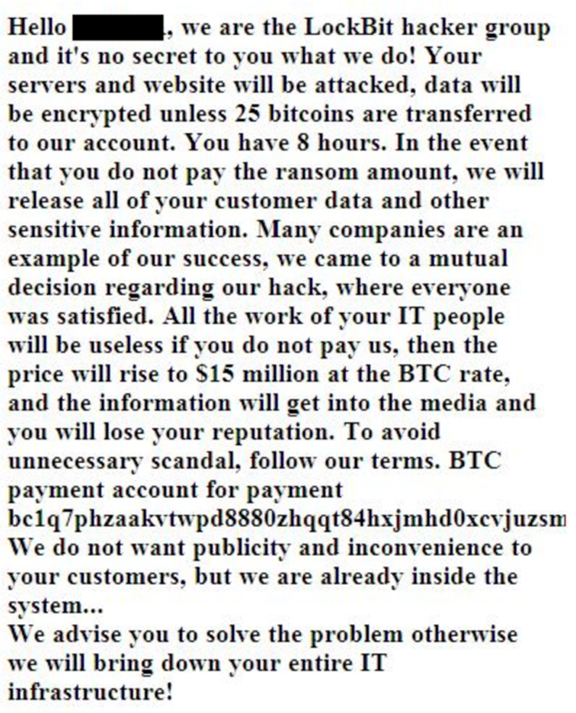
Figure 11. Contents of extortion email purporting to be from the LockBit operators. (Source: Secureworks)
Impersonating infamous threat groups in email to encourage payment is not new. The GOLD FLANDERS threat group invoked the North Korean Lazarus Group and Russian Fancy Bear threat group names to add weight to their threats of distributed denial of service (DDoS) attacks in 2021. However, the October 2022 incident was the first time CTU researchers observed the use of a ransomware group name.
Recommendations
For the most part, LockBit's affiliates use the same TTPs as other groups engaged in ransomware. Detecting precursor activity is crucial to defending against the threat.
During LockBit engagements, Secureworks incident responders have provided detailed recommendations for victims of ransomware or data theft. Guidance focuses on preventing initial access, detecting post-compromise activity, and implementing changes to assess root cause and successfully remediate attacks.
Preventing initial access
- Implement a patch management program. Ensuring that services and applications are running the most up-to-date versions is critical in defending against hostile vulnerability scanning and exploitation. Identifying end-of-life services and replacing or removing them is also crucial. Regular vulnerability scanning against the perimeter is important for identifying such services.
- Limit access to services or devices from external resources. Only make services accessible from the internet if absolutely necessary.
- Block downloads from untrusted sources. Allow-listing sources or using a software management tool prevents the download and installation of unauthorized applications.
- Implement a robust access policy. Enforce strong MFA across all internet-facing services. Remove old or legacy accounts that might not have been involved in the MFA rollout. Use a password manager, preferably saved locally, to store passwords. Saving passwords in a browser significantly increases the risk of exposing corporate credentials, as browsers are specifically targeted by malware like infostealers.
- Educate users on the current trends in phishing, social engineering, and other malware delivery techniques. For example, IT support staff in particular should be aware of social engineering involving bogus user password resets and SIM-swapping.
- Regularly test security frameworks through penetration testing or table-top exercises (TTX).
Detecting post-compromise activity
- Deploy an EDR solution. Having sight of activity on endpoints and receiving timely alerts are crucial for identifying activity that is the precursor to ransomware. Even a small window of opportunity can be enough to take action and prevent devasting impact. Ensure that the EDR rollout is robust and does not overlook devices that might be used to stage activity. For example, Secureworks incident responders have observed LockBit affiliates exploiting a networked training device and a proof-of-concept server that were not enrolled in EDR solutions.
- Harden VMware ESXi hosts. VMware ESXi hypervisors are high-value assets targeted by multiple ransomware groups, including LockBit affiliates. The use of EDR agents, if compatible, and native logging exported to a SIEM, can provide warnings of threat actor activity. VMware publishes hardening guides for many of its product suites, which should be closely followed.
- Restrict application or tool usage to specific users and/or hosts. Regular users should not be able to execute certain code (e.g., PowerShell) on their systems if there is no business requirement to do so.
- Create application allow-lists for users dictated by business need. Restrict software that can be accessed by users to limit the use of illegitimate and potentially dangerous software.
Remediation
- Create reliable backups. Having data properly backed up is essential to quickly recovering from ransomware attacks and often removes the perceived need to negotiate payment in return for a decryption key. Ransomware groups are known to target backups (e.g., LockBit ransomware attempts to delete shadow copies on execution), so ensure the backups are air-gapped or isolated from production environments.
- Centralize event logging and ensure the correct information is collected. Logs are critical to identifying the root cause and full extent of an intrusion. Without them, it is not always possible to identify and remediate all access vectors, which could allow a threat actor to re-enter the environment.
- Engage incident response as early as possible after suspecting a compromise. Thoroughly investigate activity before re-imaging devices to ensure forensic analysis is possible and allow for identification of the root cause and full remediation of an intrusion.
Conclusion
There are two almost-distinct elements to the LockBit operation. First is the ransomware itself, which has moved through a number of iterations to improve its capability while facilitating use by lower-skilled affiliates. Second, and perhaps more importantly, is the brand. Posts by the LockBitSupp underground persona, which is likely operated by the leader of GOLD MYSTIC, indicate that the ransomware operators recognize that creating an ecosystem is more important than the ransomware itself. They offer to give LockBit affiliates the means to monetize any access they can achieve, even if it is with another ransomware variant or through data theft-only operations. Giving affiliates the control over negotiations and payment handling has allowed LockBit operations to scale considerably above any other scheme.
Although LockBit was the most prominent RaaS scheme, it is unlikely that its demise will translate into the disappearance of all affiliates. Just as LockBit operators have attempted to attract affiliates from the defunct REvil and NoEscape operations and near-defunct schemes like ALPHV, LockBit affiliates will likely not be homeless for long. Further creative efforts to curtail the activities of ransomware groups will be needed to have a broad and lasting impact.
References
Abrams, Lawrence. "LockBit ransomware builder leaked online by 'angry developer‘." Bleeping Computer. September 21, 2022. https://www.bleepingcomputer.com/news/security/lockbit-ransomware-builder-leaked-online-by-angry-developer/
Abrams, Lawrence. "LockBit ransomware now poaching BlackCat, NoEscape affiliates." Bleeping Computer. December 13, 2023. https://www.bleepingcomputer.com/news/security/lockbit-ransomware-now-poaching-blackcat-noescape-affiliates/
Abrams, Lawrence. "Ransomware gang apologizes, gives SickKids hospital free decryptor." Bleeping Computer. January 1, 2023. https://www.bleepingcomputer.com/news/security/ransomware-gang-apologizes-gives-sickkids-hospital-free-decryptor/
AzAl Security (@azalsecurity)."NoEscape exit scam." X. December 10, 2023. https://twitter.com/azalsecurity/status/1734030086183993664
Bernardo, Jett Paulo, et al. "LockBit Resurfaces With Version 2.0 Ransomware Detections in Chile, Italy, Taiwan, UK." Trend Micro. August 16, 2021. https://www.trendmicro.com/en_us/research/21/h/lockbit-resurfaces-with-version-2-0-ransomware-detections-in-chi.html
Dela Cruz, Junestherry. "Analysis and Impact of LockBit Ransomware's First Linux and VMware ESXi Variant." Trend Micro. January 24, 2022. https://www.trendmicro.com/en_us/research/22/a/analysis-and-Impact-of-lockbit-ransomwares-first-linux-and-vmware-esxi-variant.html
DiMaggio, Jon. "Ransomware Diaries: Volume 1." Analyst1. January 16, 2023. https://analyst1.com/ransomware-diaries-volume-1/
DiMaggio, Jon. "Ransomware Diaries: Volume 3 - LockBit's Secrets." Analyst1. August 13, 2023. https://analyst1.com/ransomware-diaries-volume-3-lockbits-secrets/
Europol. “Law enforcement disrupt world’s biggest ransomware operation.” February 20, 2024. https://www.europol.europa.eu/node/5666
Secureworks. "Law Enforcement Takes Action Against ALPHV/BlackCat Ransomware." December 19, 2023. https://www.secureworks.com/blog/law-enforcement-takes-action-against-alphv-blackcat-ransomware
Tunney, Catharine. "Intelligence agency says ransomware group with Russian ties poses 'an enduring threat' to Canada." CBC News. February 2, 2023. https://www.cbc.ca/news/politics/cse-lockbit-threat-1.6734996
UK National Crime Agency. “International investigation disrupts the world’s most harmful cyber crime group.” February 20, 2024. https://nationalcrimeagency.gov.uk/news/nca-leads-international-investigation-targeting-worlds-most-harmful-ransomware-group
U.S. Department of Justice. “U.S. and U.K. Disrupt LockBit Ransomware Variant.” February 20, 2024. https://www.justice.gov/opa/pr/us-and-uk-disrupt-lockbit-ransomware-variant
U.S. Federal Bureau of Investigation (FBI). "Two or More Ransomware Variants Impacting the Same Victims and Data Destruction Trends." September 27, 2023. https://www.ic3.gov/Media/News/2023/230928.pdf
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
