On December 19, 2023, the U.S. Department of Justice (DOJ) announced a technical operation against the operators of the ALPHV (also known as BlackCat) ransomware. The operation involved cooperation from multiple international law enforcement agencies. Secureworks® Counter Threat Unit™ (CTU) researchers attribute ALPHV to the GOLD BLAZER threat group, which has been active since late 2021. The announcement follows public speculation that law enforcement had acted against the group after GOLD BLAZER's Tor-based infrastructure went offline between 0600 and 0700 UTC on December 7.
At approximately 1300 UTC on December 11, the main ALPHV leak site resumed operation and redirected visitors to a newly created Tor (.onion) address. At the time, the new address hosted no victim data but demonstrated that GOLD BLAZER still controlled the private encryption key necessary to operate the Tor service. At approximately 1230 UTC on December 19, the Tor infrastructure originally controlled by GOLD BLAZER began displaying the seizure notice shown in Figure 1. Several ancillary websites operated by GOLD BLAZER that had remained down since December 7 also resumed operation and displayed the seizure notice.

Figure 1. Domain seizure notice appearing on several GOLD BLAZER websites on December 19, 2023. (Source: Secureworks)
Several hours after the U.S. Federal Bureau of Investigation (FBI) posted this notice, GOLD BLAZER responded with its own notice on the original main leak site (see Figure 2). Both GOLD BLAZER and the FBI possess the private keys necessary to host the hidden service on the Tor network. The Tor network directs clients to the service that most recently announced itself, creating competition for which entity's site is displayed.
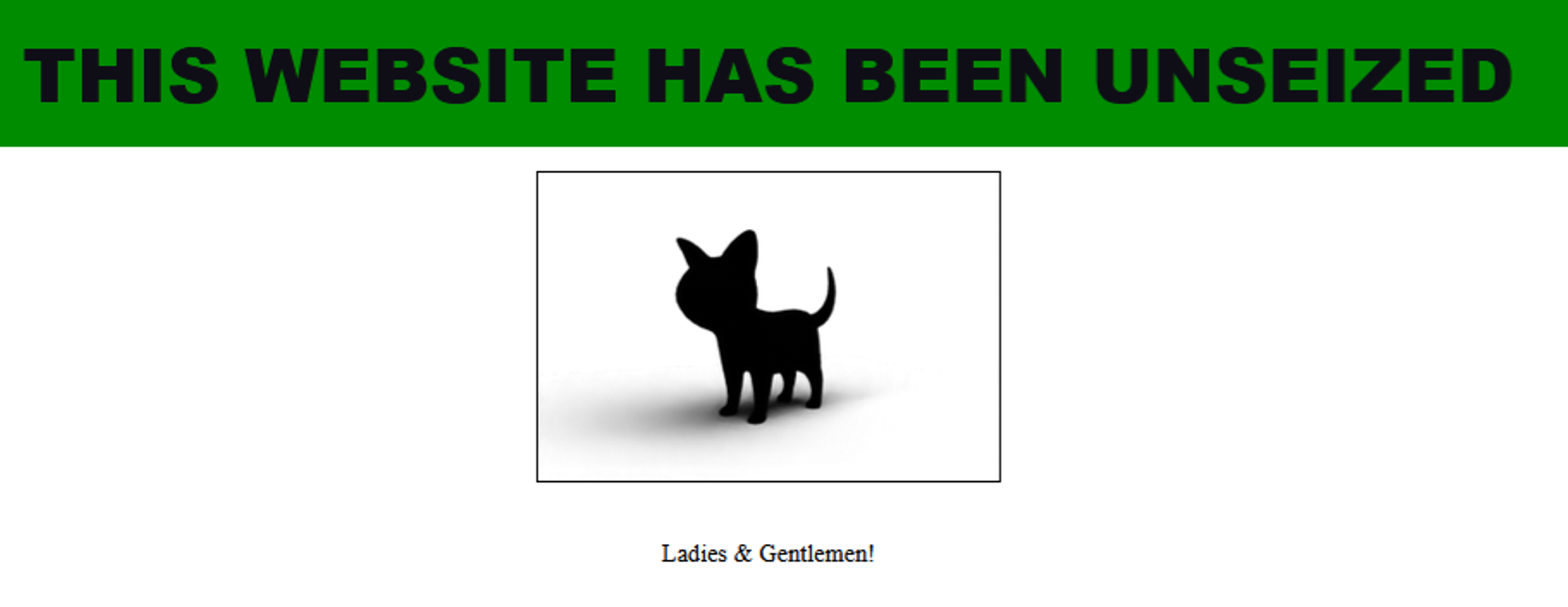
Figure 2. GOLD BLAZER response posted to main leak site on December 19. (Source: Secureworks)
This notice was accompanied by a link to GOLD BLAZER's new blog site and a Russian-language announcement that acknowledged the FBI's action and threatened retribution. Figure 3 shows a machine-translated copy of this message.
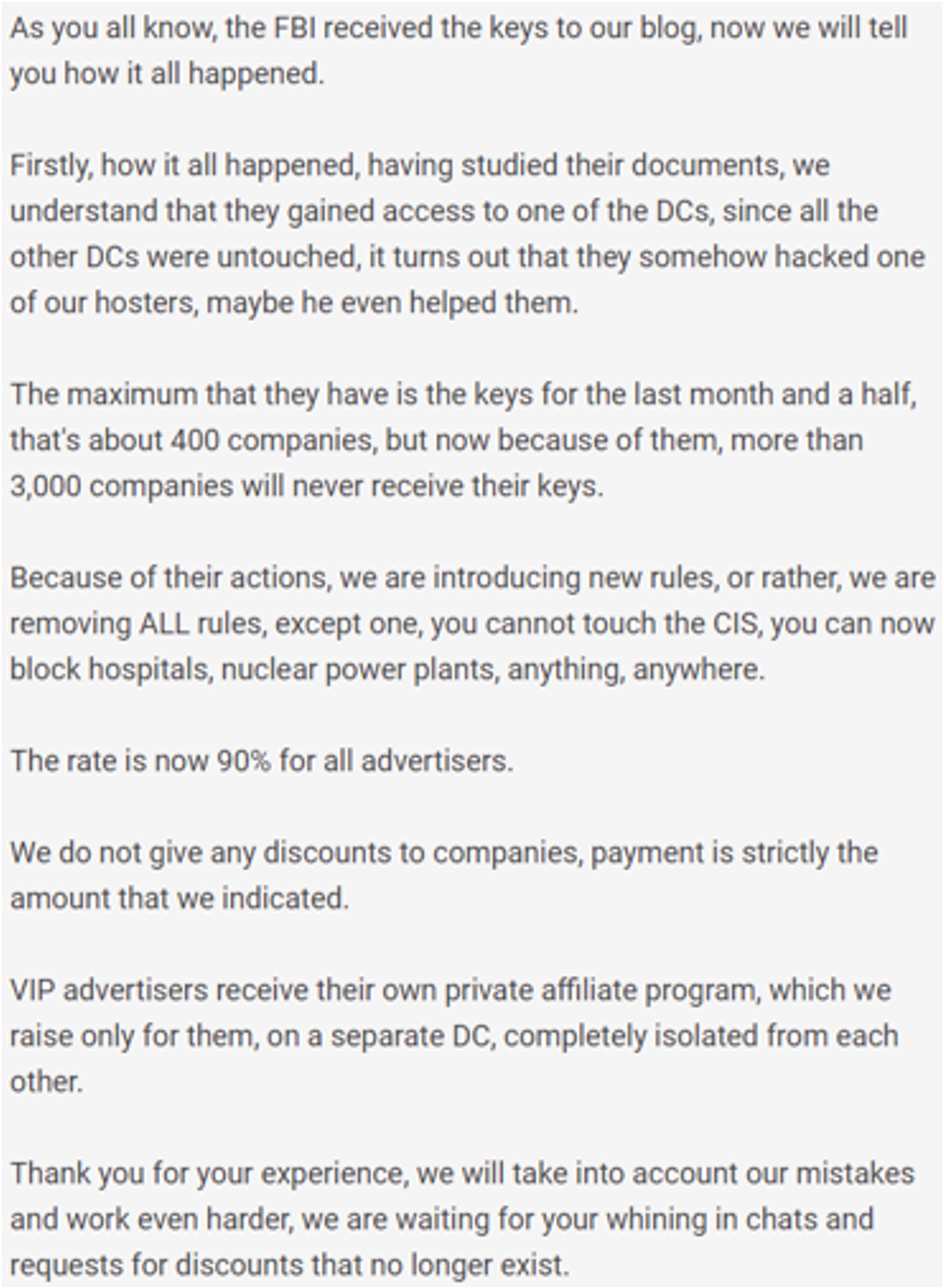
Figure 3. Machine translation of GOLD BLAZER's message responding to FBI takedown. (Source: Secureworks)
GOLD BLAZER made its last update to the main leak site on December 6 (see Figure 4). On December 13, the group published the first victim to its new leak site. As of December 19, five victims were posted to the new site, demonstrating the group retained some operational capacity.
Figure 4. Screenshot of ALPHV leak site several hours before the December 7 takedown. (Source: Secureworks)
In the twelve days following the takedown, CTU™ researchers observed multiple ransomware-as-a-service (RaaS) operators offer to publish stolen data on behalf of ALPHV affiliates. CTU researchers observed one compromise involving ALPHV deployment that occurred shortly before the takedown. Due to the leak site's unavailability, the affiliate engaged with another threat actor to post the stolen data to the INC ransomware leak site.
From November 2021 through November 2023, GOLD BLAZER published nearly 700 unique victims to its leak site (see Figure 5). The overwhelming majority of victims were in the United States, Canada, Australia, and western Europe. The inclusion of victims in Asia and South America displayed affiliates' willingness to broaden their targeting. There were no victims from Russia or its near-abroad neighbors, which is typical of most ransomware operations. While most ALPHV victims are small and medium-sized organizations, the group claimed responsibility for a September 2023 cyberattack on MGM Resorts.
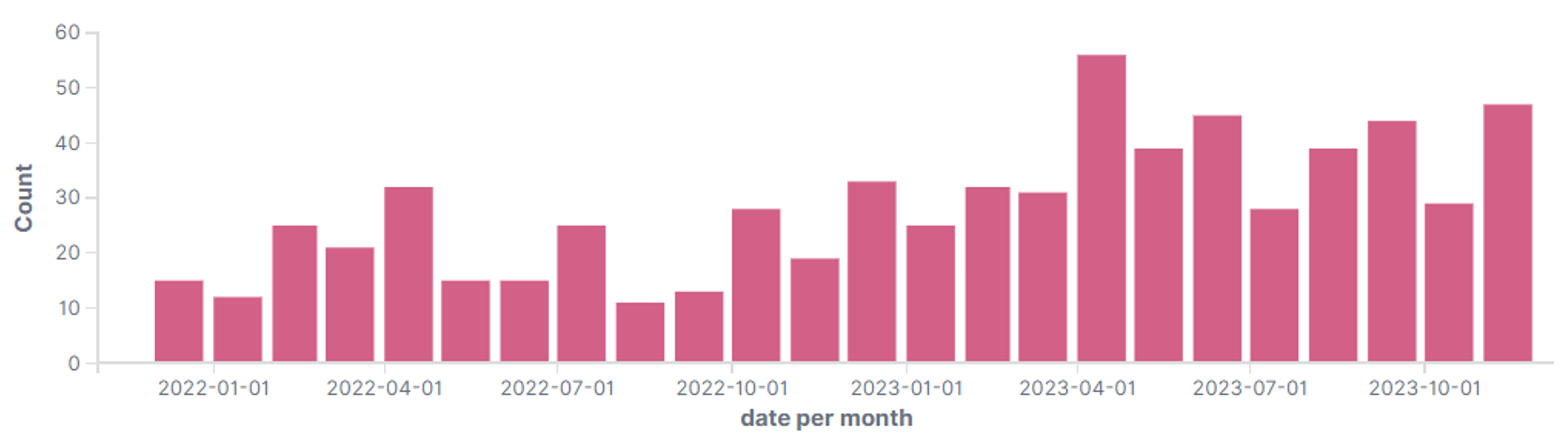
Figure 5. Victims posted to ALPHV leak site each month from November 2021 through November 2023. (Source: Secureworks)
Since early 2022, Secureworks incident responders have investigated at least 15 incidents involving ALPHV deployment or an intrusion by a threat actor known to distribute ALPHV, making it more prevalent than LockBit, Hive, Clop, and Black Basta. ALPHV affiliates typically compromise targeted networks, frequently by exploiting vulnerabilities in internet-facing services, and then exfiltrate sensitive data before deploying ALPHV to critical systems. The threat actors then publish victims' data to the leak site if they do not receive the ransom.
In an unsealed search warrant, the FBI claims to have obtained 946 encryption keys used to host ALPHV infrastructure on the Tor network. According to the U.S. DOJ announcement, ALPHV has affected “over 1,000” victims, and the FBI is making a decryption tool available to “over 500 affected victims.” Distributing the decryption tool aligns with the U.S. DOJ's efforts to “prioritize victim safety and security.” It also imposes a large cost to GOLD BLAZER and demonstrates that cybercriminals are not beyond the reach of the law. CTU researchers advise past ALPHV victims to contact law enforcement about the possibility of decrypting lost data.
Learn more about the ransomware threat and law enforcement operations in the 2023 State of the Threat report. If you need urgent assistance with an incident, contact the Secureworks Incident Response team.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
