Endpoint security software hardens your endpoints and attempts to detect hacker access at the endpoints.
But this only gets you so far. What's the next step in endpoint protection, to holistically defend against all endpoint threats?
Most CISOs acknowledge the reality that the advanced threat actor will evade endpoint security controls. So how do you know when an advanced threat actor is present, which systems have been compromised, how they got in, and how to get them out? Does your software do this? Where will it fail, and where will the next step begin?
Traditional Endpoint Security Software Protection
Endpoint security software addresses the risk of various endpoints (laptops, PCs, servers, mobile devices, etc.) connected to an enterprise network. Endpoint security software is installed on each endpoint as well as on a central server or management console. Often a policy-based approach is used where devices are required to meet security standards before given network access. It can even go so far as to take limited control of an endpoint device that does not comply with policy, such as removing local administrative rights or restricting internet browsing. Margaret Rouse gives a succinct explanation in her TechTarget definition for endpoint security management. Endpoint security software may also provide application white listing, VPN network access control, signature based anti-malware or anti-virus, memory inspection, encryption, vulnerability shielding, command and control blocking, and others.
Endpoint detection software often looks for known malware and tools used by hackers and adversaries. But some adversaries are not using malware. Or they are using zero-day malware that's previously been unseen. More advanced endpoint protection products use behavior based detection.
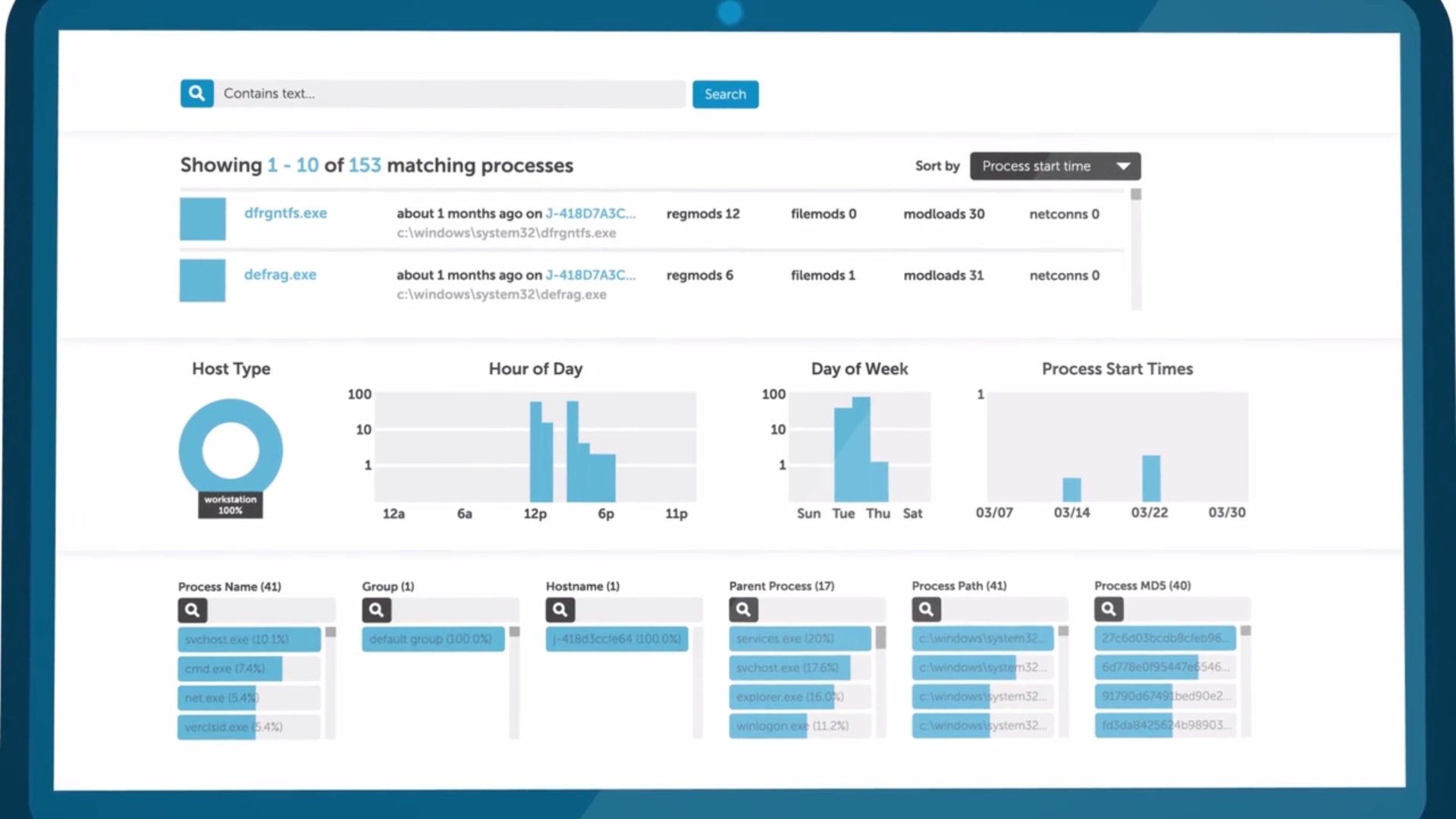
Signature Based Protection vs. Behavior Based Protection
Most consumers are familiar with anti-malware or anti-virus software. This is signature-based detection. A database is kept of known tradecraft and threat actor tools. These known tools leave a signature. Anti-malware software looks for that list of known signatures and alerts the user when a "virus" is detected. The goal of anti-malware is to detect and prevent the adversary from gaining access to the device. This has long been the approach of the security service industry.
The industry's definition of defeat is different from the adversary's definition of winning. A lot of people in the security service industry consider a defeat when the hacker has malware on the endpoint or control of the machine. But in fact, the adversaries don't care whether they have malware on the box, they don't care if there's any malware in play, or how they get access to the environment. All they are really after is data.
Behavior based endpoint protection looks for suspicious activity. It looks for files where they don't belong and users or scripts accessing files they don't usually use. Behavior based endpoint detection protects against more advance adversaries.
There are a lot of steps in the time between when the adversary compromises a host and gets the data out.
They must:
- Orient themselves
- Find credentials they need
- Look around the environment to find where the data lives
- Collect data
- Get data out of the environment
These steps can take days, weeks or months – depending on the size and complexity of your network environment.
What's missing from Endpoint Security Software?
More advanced endpoint technologies, like SecureWorks Red Cloak™ use both behavior and malware signature detection. Even if your traditional malware detection fails, Red Cloak can observe threat actor behavior and detect them in time before they accomplish their goal of getting your data out of the environment.
Endpoint protection products like Red Cloak should include:
- Sensors at each endpoint – monitor registries, file systems, process tables, network connections
- Interface – providing telemetry and logs
- Analyst staff – investigate how threat entered network, if it spread, what data was breached
- Severity of threat – who is behind it, their objective, what tradecraft they commonly use
- Next steps to eradicate threat
Beyond behavior based detection, the ideal endpoint security is not simply endpoint security software, host intrusion detection or any other device protection on the market, but rather a 24x7 managed security service (MSS).
This managed service should be capable of:
- Monitoring endpoints for signs of advanced threat actor activity
- Scanning for specific indicators of compromise as conditions change
- Keeping threat intelligence data up to date
- Analyzing endpoint forensics data
- Alerting you with specific recommendations on how to proceed should an endpoint compromise be indicated
Threat intelligence is a critical piece of endpoint security that can make or break your solution. It gives you the earliest possible warning that your endpoints may be hosting an advanced adversary. A fully managed security service heightens your security situational awareness by warning you when endpoints may have been compromised. And, accessing extensive intelligence on threat actors and tradecraft, accelerates incident response efforts. An MSS with excellent intelligence and Red Cloak endpoint security software can pinpoint exactly which systems are compromised, how they were compromised, and how you can repair them.

To be an effective endpoint security solution, a fully managed security service must:
- Monitor the state of your endpoints (Windows servers, laptops, desktops) for threat indicators
- Investigate events to determine severity, accuracy and context
- Quickly escalate critical events that suggest endpoint compromise
How to Identify the Best Endpoint Security Solutions
Intelligence Experience
That's the best way to know if one endpoint security provider has better ability than another. How long have they been observing advanced threat actor behavior? Do they have researcher experienced in hunting engagements? Do they have global experience?
Resolution
Is the endpoint service using many levels of detection, or just a few? Is it looking for adversary behavior across all the steps between compromising the endpoint and getting the data out? Is it utilizing sensor across endpoints as well as the entire network? And, most importantly, will it record all this so that forensic analysts can quickly see how an adversary got in and where they went?
Actionable Guidance
Many endpoint security providers offer detection along with next steps. But this is again where experience comes into play. Cybersecurity analysts are in high demand. Endpoint security software companies are hiring new employees as quickly as possible so they can provide live staff to give actionable steps. But do you want your recommendations coming from a novice or a seasoned expert?
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

