- Author: Brett Stone-Gross, Dell SecureWorks Counter Threat Unit(TM) Threat Intelligence
- Date: 23 July 2012
The Dell SecureWorks Counter Threat Unit(TM) (CTU) research team continues to monitor the latest advancements to the ZeuS banking Trojan horse malware family. One of the most significant developments since the leak of the ZeuS source code in May 2011 has been the introduction of a private peer-to-peer (P2P) version, first identified in October 2011, which removes the centralized command and control (C2) infrastructure previously required to push configuration files, updates, and collect information harvested from infected computers. Over the past year, CTU researchers have tracked the tools, techniques, and modus operandi of the attackers behind the P2P version of ZeuS, and have gained a comprehensive view into the thriving underground economy.
Background
The underground economy provides a marketplace for cybercriminals to buy and sell their products and services. Nearly everything has a price: stolen credit cards, spam services, and do-it-yourself (DIY) botnet kits. Arguably the most popular DIY botnet kit is the ZeuS banking trojan, which first appeared in 2006. In May 2011, the source code of ZeuS was leaked, which spawned two new botnet kits known as ICE IX and Citadel. Both of these kits are sold through underground forums and provide customers with bug fixes to the original ZeuS codebase and with new features such as sandbox detection and video recording. In addition to these commercial botnet kits based on ZeuS, there have also been variants of ZeuS that have not been marketed and offered for sale in the public domain. These variants include Murofet/Licat, which introduced a domain generation algorithm (DGA) in October 2010 to make takedown efforts more difficult, and P2P ZeuS, which is also known as Gameover ZeuS because of an early version that contained HTTP POST requests to the C2 server that contained the keyword gameover. P2P ZeuS is a significant improvement from all other versions of ZeuS, because it replaces the centralized C2 server, a single point of failure targeted by researchers and law enforcement, with a robust P2P network. This is a particularly important modification in light of Microsoft's execution of legal action in March 2012 through a civil lawsuit dubbed Operation b71. The lawsuit resulted in a court order to seize 147 domains and a number of servers used for ZeuS, ICE IX, and SpyEye botnets. However, the action had no effect on the P2P version of ZeuS because of its network architecture. In the P2P model of ZeuS, each infected client maintains a list of other infected clients. These peers act a massive proxy network between the P2P ZeuS botnet operators and the infected hosts. The peers are used to propagate binary updates, to distribute configuration files, and to send stolen data to the controllers.
In this threat analysis, the CTU research team analyzes the lifecycle of P2P ZeuS. Specifically, CTU researchers analyze the P2P ZeuS crew's distribution mechanisms used to spread their malware, the P2P infrastructure that replaces the centralized C2 server, the recruitment of unsuspecting individuals (i.e., money mules) to wire stolen funds, and the use of distributed denial of service (DDoS) attacks to create a diversion when withdrawing large sums of money from victims' accounts. All in all, the P2P ZeuS crew makes significant use of commercial tools and services offered by many other well-known criminal operations.
Malware distribution via the Cutwail spam botnet
There are a variety of techniques to spread malware, most of which rely on aspects of social engineering and software vulnerabilities. The crew behind P2P ZeuS use Cutwail, one of the largest and most notorious spam botnets, to send massive amounts of email that impersonate well-known online retailers, cellular phone companies, social networking sites, and financial institutions. These lures typically come in the form of an invoice, an order confirmation, or a warning about an unpaid bill (usually with a large balance due to increase the likelihood that a victim will click the link). The links in the email have been replaced with those of compromised sites that redirect victims to an exploit kit.
Cybercriminals can rent access to Cutwail's spam-as-a-service infrastructure to design and execute a spam campaign. The Cutwail botnet relies upon hundreds of thousands of compromised systems to send spam on its behalf and uses templates to generate a large number of variations to the email message to evade spam filters. For example, the spam bot engine may use a macro within the body of the email to add a random number of spaces or to add a random dollar amount to a fake invoice, as shown in Figure 1. The body of the email contains links that appear to go to www.[removed]cards . com. However, the URLs actually lead to websites that were hacked to redirect victims to an exploit kit. In example shown in Figure 1, one of the URLs was replaced with hxxp: //gsp[removed] . org/BgwiyFa9/index.html.
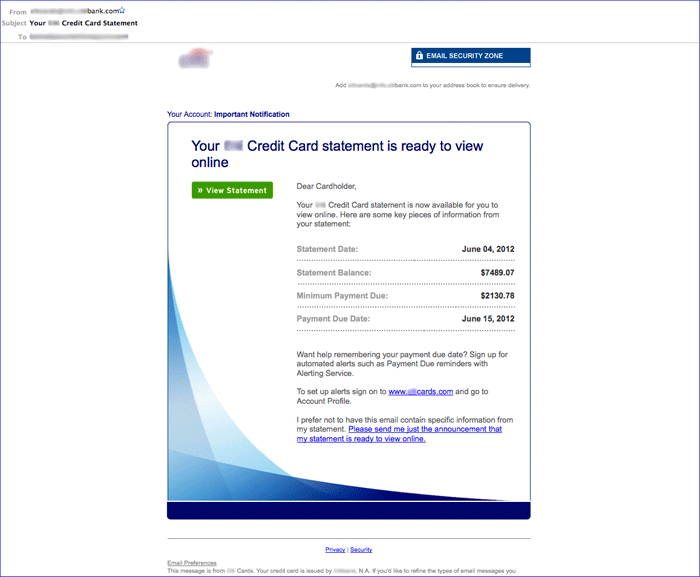
Figure 1. Example of a spam email lure sent by Cutwail. The URLs link to compromised websites redirecting to an exploit kit. (Source: Dell SecureWorks)
Blackhole exploit kit
When a victim clicks a URL in the spam email, a compromised website is loaded that displays a fake loading page. The purpose of this page is to distract the victim and retrieve redirection code to a commercial exploit kit known as Blackhole that targets vulnerabilities in web browsers and plugins such as Adobe Reader, Flash, and Java. The redirection code is obtained through JavaScript included from three different compromised sites as shown in Figure 2.
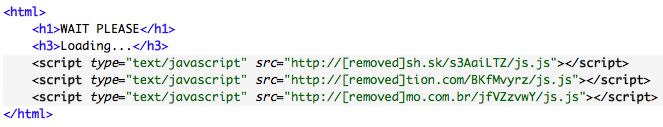
Figure 2. Blackhole fake loading page hosted on a compromised server.
In many cases, the Blackhole exploit code is loaded directly from a malicious server. However, the P2P ZeuS crew has recently been using additional compromised servers to proxy the traffic between the exploit server and the victim. For example, the JavaScript code in Figure 3 redirects the victim through an nginx server that is installed on the compromised server at 209.59.xxx.xx. The nginx web server is popular among cybercriminals because of its reverse proxy functionalities. The nginx proxy relays the requests to the Blackhole exploit kit's backend infrastructure. The query string parameter 's' is used to identify a specific exploit campaign (also known as a thread).
![]()
Figure 3. JavaScript code that redirects victim through an nginx server.
At this stage, the victim's web browser retrieves the exploits through obfuscated JavaScript code that downloads malicious Java applets and PDF files. If any of the exploits are successful in compromising the victim's system, then the shellcode silently downloads and executes the malware payload. Similar to other exploit kits, the request for the malware payload contains a numeric value that reports which vulnerability was exploited, enabling the attackers to collect statistics and improve their techniques. Figures 4 and 5 show examples of Blackhole statistics pages containing detailed information about the infection rate and the visitors (e.g., operating system and web browser versions, geography, and optionally the referring website).
The use of the Cutwail spam botnet to propagate malware is not unique to P2P ZeuS. The CTU research team has observed several malware families that are propagated using similar techniques, including the Bugat/Feodo/Cridex and Mebroot/Torpig banking trojans.
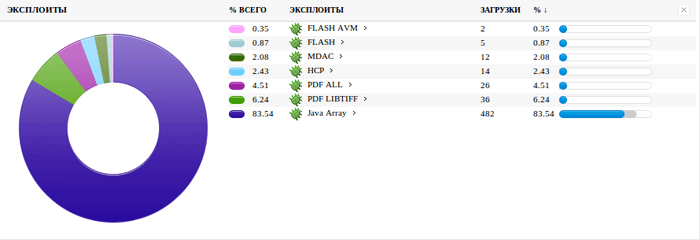
Figure 4. Example of a Blackhole kit statistics page showing the success rate of exploits from July 2012.(Source: Dell SecureWorks)
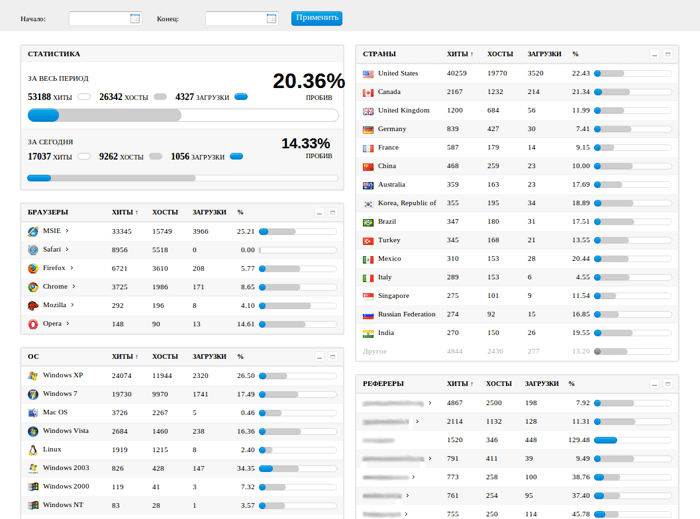
Figure 5. Example of the main statistics page from a Blackhole kit from July 2012. (Source: Dell SecureWorks)
Pony loader
The malware payload delivered by the Blackhole exploit kit does not normally drop P2P ZeuS directly. Rather, a downloader (or loader) called Pony has been observed retrieving the P2P ZeuS binary from additional compromised websites (e.g., hxxp: //definitived[removed] . co . za/VCPoN7xh.exe). The Pony loader typically attempts to download the P2P ZeuS binaries from three hard-coded compromised web servers, which vary among samples.
The Pony loader comes bundled as a kit that contains a builder for the malware binary and a PHP-based web interface front end to configure and manage the distribution of malware. In addition to downloading and executing the P2P ZeuS malware, Pony also mines a victim's system for HTTP/HTTPS, FTP/SFTP, and email credentials from dozens of programs. Figure 6 is a screenshot of some of the programs targeted by the Pony loader.
The Pony loader reports the extracted credentials to the Pony C2 server through an encrypted HTTP POST request, which itself is proxied through a compromised server running nginx (e.g., http:// etsiunj[removed] . fr:81/pony/gate.php). Each binary usually contains a primary and secondary C2 URL. The botnet operators can access the stolen credentials through the web portal provided by the Pony loader.
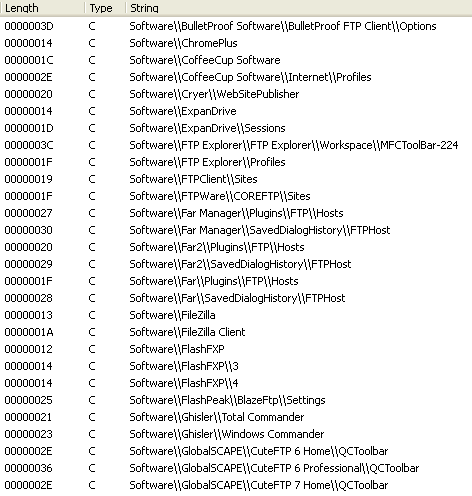
Figure 6. Partial list of the program strings targeted in the Pony loader malware.(Source: Dell SecureWorks)
Figure 7 displays the administrator's login page to the Pony loader web portal. The FTP credentials exfiltrated by Pony are particularly valuable because they can be used to seed (modify and add content to) the hacked websites hosting the P2P ZeuS binaries and the compromised redirector websites accessed from the spam emails.
Figure 7. Example of a Pony loader admin login page.(Source: Dell SecureWorks)
Another important advantage that the Pony loader provides to the P2P ZeuS crew is its ability to evade antivirus detection. A Pony sample uploaded by the CTU research team to VirusTotal on July 13, 2012 (MD5: 3006922e7c4ea1d64dbb3f0061fd4663) showed only 2 out of 41 detections, and both detections were generic signatures.
The ZeuS trojan
The ZeuS malware family provides an attacker with a diverse set of features to capture information from a victim through keystroke logging, form grabbing, and credential scraping. Moreover, ZeuS provides the ability to modify the HTML of a target website, as well as to inject additional form fields to dupe a victim into entering sensitive information, a process known as web injects. Web injects are usually more difficult for a victim to identify than a classic phishing attack, because the expected URL is displayed in the web browser and works even with encrypted HTTPS sessions. Web injects display forms that request information, including credit card numbers, social security numbers, mother's maiden name, ATM PINs, and date of birth. In addition, web injects can be used to bypass two-factor authentication security features by prompting the victim for the required information. The web injects are defined in the ZeuS configuration files and can be updated dynamically.
The P2P version of ZeuS is very similar to its predecessors except for its network communications. The CTU research team has observed that the P2P ZeuS crew operating the botnet primarily target financial institutions, such as banks, credit unions, and payment providers. In addition to the financial sector, CTU researchers have spotted web injects targeted at department stores, social networking sites, and webmail services. Figure 8 shows a web inject that is currently being used by the P2P ZeuS crew. When a victim's infected web browser visits the targeted URL, the web page displays a popup in the foreground. This HTML form is not part of the website. The form is inserted by the ZeuS malware according to the definition provided in the ZeuS configuration file. When the victim selects the "Verify" button, the information is encrypted using RC4 and is sent to a proxy node in the P2P network.
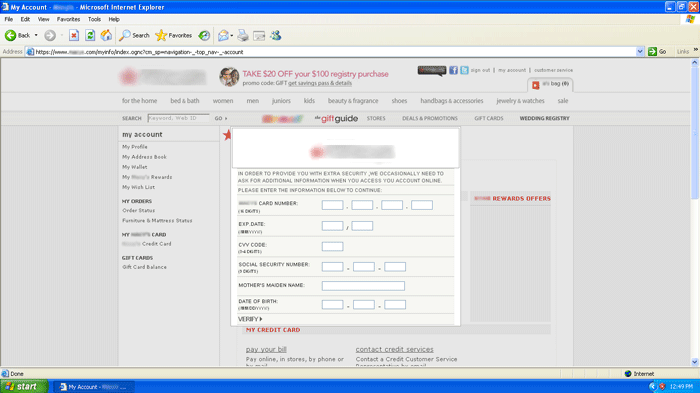
Figure 8. ZeuS P2P web injects targeting a department store's website. (Source: Dell SecureWorks)
Recent samples of the P2P ZeuS malware analyzed by CTU researchers have very poor antivirus coverage. A sample (MD5: 2464355c63e0e31c9f013b79becc0a85) submitted to VirusTotal on July 15, 2012 shows the same low detection rate as the Pony loader, with 2 out of 41 detections, again with only generic signature matches.
The ZeuS P2P network
After the P2P ZeuS malware executes, it immediately contacts a series of peers hard-coded into the program to request configuration files, binary updates, and peer lists. If the hard-coded peers in the ZeuS binaries cannot be reached, P2P ZeuS falls back to a DGA seeded by the current date. The DGA produces 1,000 pseudorandom domains per day. The domain names are between 32 and 48 characters in length appended with one of six top-level domains (com, net, org, biz, info, and ru). These backup domains provide a fresh list of active peers in the network. Each peer entry is stored as a tuple of a Bot ID, IPv4 address, port, IPv6 address, and port. The ZeuS P2P network supports both IPv4 and IPv6 addresses. Although CTU researchers have not yet observed active peers with IPv6 addresses, that scenario may change over time as more ISPs and commodity hardware support IPv6.
The ZeuS P2P network relies on a protocol that is loosely based on the Kademlia P2P protocol. Neighboring peers are calculated by a simple XOR distance comparison. Communication between peers occurs over TCP and UDP ports between 10,000 and 30,000, which are chosen randomly when the malware is installed. Control messages such as binary/configuration version requests and peer list requests occur over UDP. Larger data exchanges, including the configuration files, binary updates, and drop zone submissions, occur over TCP ports. The P2P ZeuS crew digitally signs the configurations and binaries to prevent attackers from pushing arbitrary versions of these files. In addition, some of the P2P control messages, such as those that set the HTTP proxy nodes, are signed to prevent poisoning.
Botnet node enumeration
Estimating the size of centralized botnets is difficult without obtaining access to the C2 server. In contrast, most P2P networks are open by design; therefore, it's possible for an outsider to enumerate the nodes in a P2P network by using a technique known as crawling. The method involves emulating a node in the network that queries a set of peers for their neighbors, and is illustrated at a high level in Figure 9.
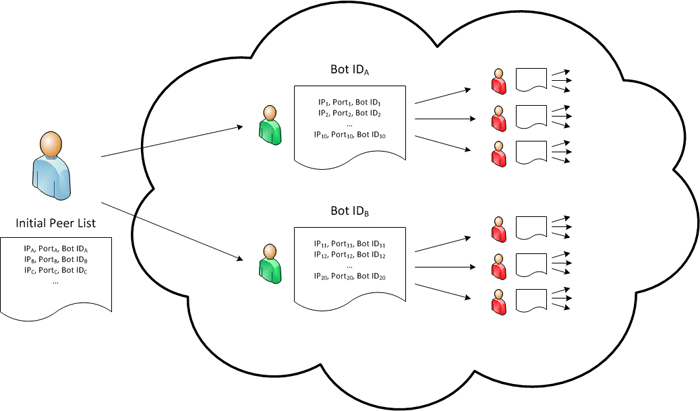
Figure 9. The process of crawling the ZeuS P2P network. (Source: Dell SecureWorks)
The process starts by querying an initial list of active peers (shown in green) for their neighbors. During a P2P ZeuS peer list request, neighboring peers provide a list of up to 10 peers to the requesting node, although each node is capable of storing a total of 150 peer entries at a time. The non-duplicate records from each peer list (shown in red) are then added to a queue, and the process is repeated recursively until the entire network is enumerated.
CTU researchers developed a custom client to perform these operations. This client has been crawling the P2P ZeuS botnet since April 25, 2012 to estimate the number of infections. There are challenges to quantifying a P2P botnet's size. The challenges stem from whether a bot contains a unique identifier (e.g., peers in some P2P botnets such as ZeroAccess are only identified by IP address) and whether fake peers are being injected into the network (e.g., by other researchers). In the case of P2P Zeus, each node generates a unique 20-byte SHA-1 hash that is used as a Bot ID and is included in the header of every packet. The CTU research team identified two groups of researchers that were poisoning the network by injecting fake peers. Fortunately, these bogus entries were easy to filter out when counting the total number of botnet nodes.
Overall, CTU researchers identified 678,205 unique Bot IDs and 1,570,871 unique IP addresses advertised in peer lists. Not all of these peers were reachable, suggesting they are behind a firewall, proxy, or NAT, or they were offline. The P2P ZeuS crawler developed by the CTU research team was able to connect to 99,572 Bot IDs (14.7%) and 354,017 unique IP addresses (22.5%). More than 97% of all IP addresses were associated with only one Bot ID, indicating that many of the infected systems contained multiple IP addresses due to DHCP churn. The graph in Figure 10 shows the cumulative number of active Bot IDs and the total Bot IDs and IPs observed from April 25, 2012 to July 11, 2012.
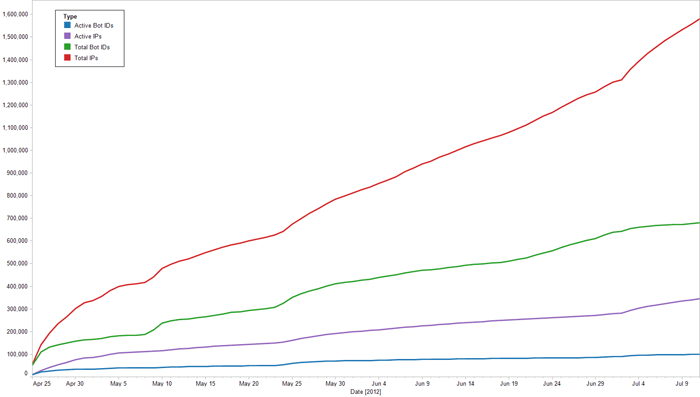
Figure 10. ZeuS P2P crawler statistics aggregated per day. (Source: Dell SecureWorks)
Although the peer list exchanges in the ZeuS P2P network contain only 10 entries each (in comparison, peer exchanges in the Waledac/Kelihos P2P network contained up to 250 entries), Figure 11 shows that the ZeuS P2P network is still highly connected. The graph represents 23,196 nodes (infected systems) shown as blue dots, and the green lines indicate a connection (peer list entry) between two nodes.
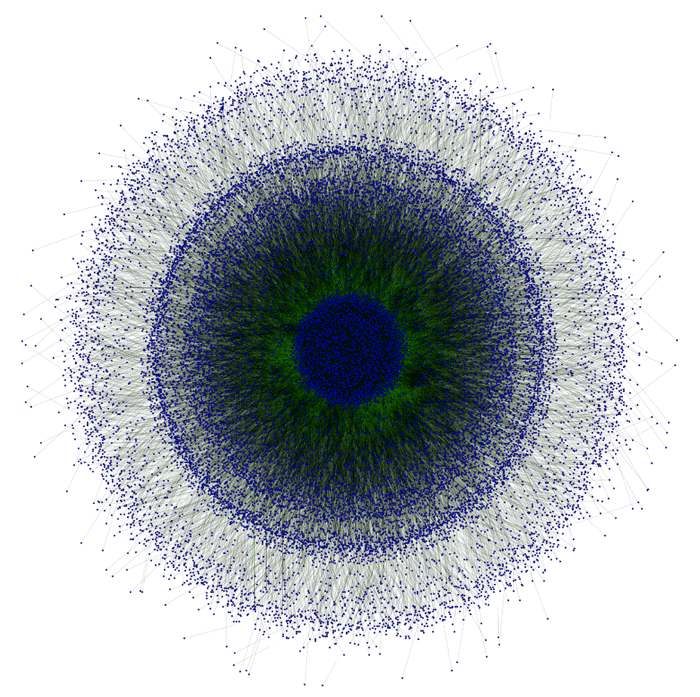
Figure 11. ZeuS P2P network connectivity graph between 23,196 nodes. The blue dots indicate the nodes (systems infected with P2P ZeuS) and the green lines indicate the edges between nodes. (Source: Dell SecureWorks)
Geographic distribution
The results of crawling the P2P ZeuS botnet show infections in 226 countries. The geographic distribution closely follows the regions targeted in the P2P ZeuS configuration files. Table 1 lists the countries with the most infections. Overall, the United States accounts for the most infections, likely due to the P2P ZeuS crew's targeted spam campaigns used to propagate the P2P ZeuS malware. Germany and Italy ranked second and third respectively in the number of infections, but each had less than one-third as many infections as the United States. The unique number of IP addresses per country is shown for completeness. The discrepancy between the number of Bot IDs and IP addresses is due to the infected hosts receiving new IP addresses via DHCP from their Internet service providers (ISPs).
| Rank | Country | Unique Bot IDs | Unique IPs |
| 1 | United States | 150,201 (22.1%) | 458,882 (29.2%) |
| 2 | Germany | 48,853 (7.2%) | 73,951 (4.7%) |
| 3 | Italy | 34,361 (5.1%) | 145,290 (9.2%) |
| 4 | Canada | 27,150 (4.0%) | 40,482 (2.6%) |
| 5 | Brazil | 24,997 (3.7%) | 120,497 (7.7%) |
| 6 | Mexico | 24,143 (3.6%) | 119,658 (7.6%) |
| 7 | India | 23,811 (3.5%) | 141,412 (9.0%) |
| 8 | Indonesia | 19.146 (2.8%) | 113,196 (7.2%) |
| 9 | Iran | 18,948 (2.8%) | 69,617 (4.4%) |
| 10 | Turkey | 16,935 (2.5%) | 104,391 (6.6%) |
Table 1. Breakdown of P2P ZeuS infections by top 10 countries. (Source: Dell SecureWorks)
Figure 12 shows P2P ZeuS infections around the globe affecting nearly every market sector, including 14 of the top 20 Fortune 500 companies, universities, hospitals, financial institutions, defense contractors, and nearly all levels of government (local, state, and federal agencies, law enforcement, and the armed services).
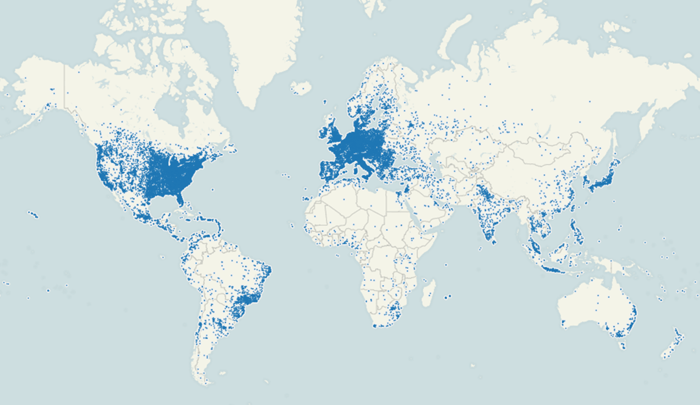
Figure 12. Geographic distribution of nodes in the ZeuS P2P network by Bot ID. (Source: Dell SecureWorks)
Money mule recruitment
The ultimate goal of the group running P2P ZeuS is to profit from the information gathered from the botnet. The P2P ZeuS crew primarily monetizes the botnet through large Automated Clearing House (ACH) transactions and wire transfers. To siphon funds from compromised accounts at financial institutions, the crew behind P2P ZeuS must find accomplices to accept fraudulent ACH transfers. These accomplices are known as money mules and usually need to be within the same area or country as the victim to complete the transaction and reduce the risk of detection. Operators of botnets such as P2P ZeuS often resort to spam services because they can target mules from specific regions. In other words, if the botmasters have compromised an account at a German financial institution, they can spam recruitment offerings within Germany by targeting the .de global top-level domain (gTLD). The CTU research team has observed numerous money mule recruitment spam campaigns delivered by Cutwail bots that target specific regions (e.g., United States, United Kingdom, Germany, Italy, Spain, France, Netherlands, and Sweden). Unfortunately, it's difficult to correlate the mule recruitment with the specific botnet aiming to cash out funds from a victim account, but CTU researchers believe that some of these Cutwail spam campaigns are likely sent on behalf of the P2P ZeuS crew. Figures 13-15 show examples of three different Cutwail mule recruitment spam campaigns in English, German, and Italian.
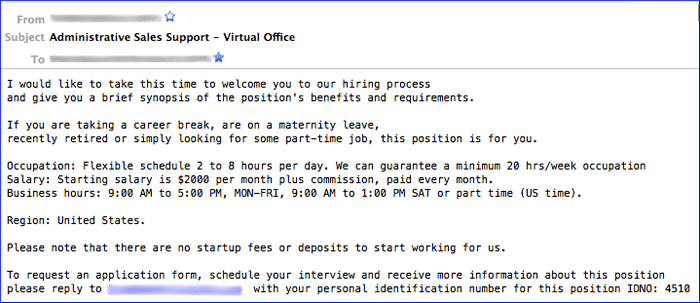
Figure 13. Example of money mule recruitment spam sent by the Cutwail spam botnet targeting Americans.
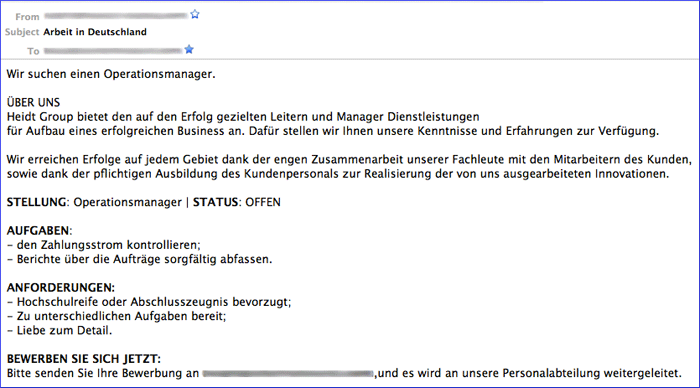
Figure 14. Example of money mule recruitment spam sent by the Cutwail spam botnet targeting Germans.
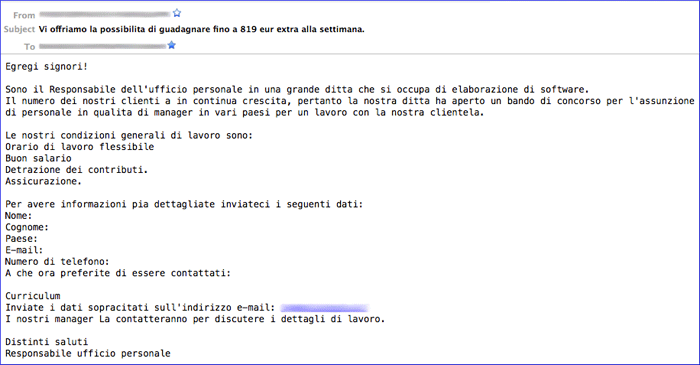
Figure 15. Example of money mule recruitment spam sent by the Cutwail spam botnet targeting Italians.
The email address domains that the recipient is asked to respond to in the mule spam are usually registered within a few days of the spam campaign and only contain a DNS mail (MX) server record. Most of the mule domains spammed through Cutwail have been registered through the registrar BIZCN.
The mule recruitment scams usually advertise a work from home job with positions such as administrative assistant, operations manager, or financial administrator. Once hired, the mule provides personal bank account information to the cybercriminals. The mule's job is simple: accept the fraudulent transfer and wire the money to the cybercriminals' account, minus a commission for performing the task.
DDoS attacks via Dirt Jumper
Starting around November 2011, the crew operating the P2P ZeuS botnet began using DDoS attacks in conjunction with high-value ACH transfers or wire transfers to create a diversion and to prevent victims from being able to log into their accounts. The DDoS attacks were launched with the help of a commercial DDoS botnet kit called Dirt Jumper, which is the successor to the RussKill DDoS botnet. The CTU research team has observed 85 active Dirt Jumper C2 servers since February 2012.
The Dirt Jumper kit is sold through underground forums with prices ranging from $200 to $1200, although many recent versions of the kit have been leaked online. Dirt Jumper features a variety of attack types targeted at HTTP/HTTPS and FTP servers, including various flooding techniques (TCP SYN and HTTP GET/POST requests) to saturate the target server's bandwidth and resources. The HTTP flood requests rotate the Referer and User-Agent strings to make filtering more difficult. The kit comes with a builder to customize the Dirt Jumper binary and a web interface to configure and manage a DDoS attack. Figure 16 shows an example of the web control panel for Dirt Jumper.
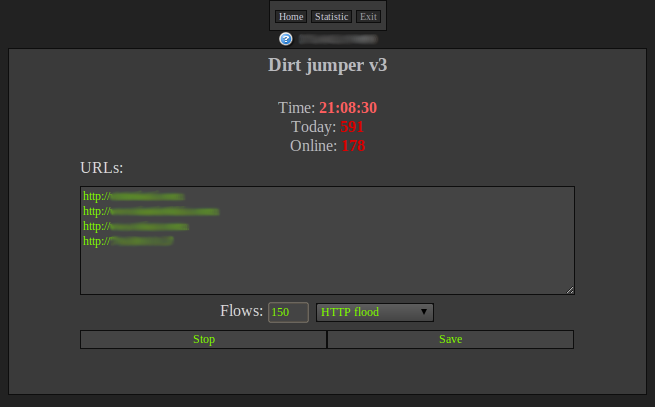
Figure 16. The Dirt Jumper (version 3) web interface control panel. (Source: Dell SecureWorks)
In the past, the P2P ZeuS crew started with a short-lived DDoS attack (around 15-30 minutes) to determine if they could disrupt the financial institution's website. Now, the DDoS attacks start immediately after the transfer takes place. The duration of the attacks also varies with the type of fraud. For example, DDoS attacks for a fraudulent wire transfer generally last for a few hours, while attacks during an ACH transfer can last for a few days. Since March 2012, CTU researchers have observed more than 40 financial institutions targeted by the P2P ZeuS crew. Most of the affected financial institutions have been small to medium-sized, although a few large financial institutions have also been targeted.
Conclusion
The P2P variant of ZeuS represents a technical evolution away from the centralized botnet model. As a result, the infrastructure makes disruption (especially through legal action) and attacker attribution more difficult. On the other hand, there are a number of disadvantages in a P2P network. The decentralized nature of the P2P ZeuS botnet allows researchers to enumerate the infected botnet population by recursively crawling each node's peer list. It is also possible to poison peer lists by injecting fake peer nodes into the P2P network, which has enabled researchers to sinkhole and neutralize P2P botnets (e.g., Storm, Waledac, and Kelihos). The P2P ZeuS crew receives considerable support from the products and services offered by the underground community, who collectively fulfill vital functions to plan and execute a large successful cybercriminal operation. Moreover, the large number of compromised personal computers and web servers provide a robust and low cost infrastructure for a variety of malicious activities.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
