Summary
In early February 2015, Dell SecureWorks Counter Threat Unit™ (CTU™) researchers investigated a new file-encrypting ransomware family named TeslaCrypt, which was distributed by the popular Angler browser exploit kit. After encrypting popular file types with the AES-256 encryption algorithm, TeslaCrypt holds the files for a ransom of $250 to $1000. The malware uses the Tor anonymity network for command and control (C2) and does not require network connectivity to encrypt files, which complicates detection, prevention, and remediation.
History
Although ransomware that locks files until victims pay to restore them has existed for many years, it became more prevalent after the Gameover Zeus botnet operators introduced the once widespread but now-defunct CryptoLocker malware in early February 2015. An early TeslaCrypt sample was uploaded to the VirusTotal analysis service on November 11, 2014, but TeslaCrypt was not widely distributed until early March 2015. The TeslaCrypt operators mimicked CryptoLocker in the warning screen shown to victims (see Figure 1).
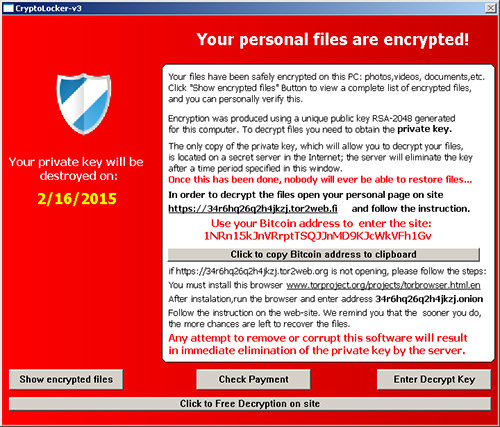
Figure 1. TeslaCrypt "splash screen" displayed to a victim. (Source: Dell SecureWorks)
CTU researchers are unaware of additional malware families associated with the TeslaCrypt threat actors. The group's infrastructure shows involvement in additional fraudulent activity, including theft of financial data and other credentials. TeslaCrypt does not contain credential theft or data exfiltration capabilities.
In late April 2015, the ransom payment servers began referring to TeslaCrypt as "Alpha Crypt" and "AlphaTool," which may signal that the malware is being rebranded. On April 27, 2015, Cisco Talos researchers created a decryption tool that allows many victims to recover files.
Malware distribution vector
As of this publication, TeslaCrypt has been exclusively distributed by the Angler and Nuclear browser exploit kits. Angler is a prolific exploit kit that has garnered notoriety for two reasons:
- It uses a memory-resident, file-less mechanism called Bedep that minimizes the observable footprint of an infection. Bedep can download additional malware payloads and initiate advertising click-fraud activity.
- It exploited several Adobe Flash Player zero-day vulnerabilities in early 2015. Exploit kits distributing commodity-style malware rarely exploit zero-day vulnerabilities.
Nuclear has distributed ransomware families such as CryptoWall and Troldesh. Both Angler and Nuclear exploit patched vulnerabilities in popular web technologies such as Internet Explorer, Adobe Flash, Adobe Reader, Microsoft Silverlight, and Oracle Java. The Contagio exploit kit table lists the vulnerabilities exploited by Angler, Nuclear, and many other exploit kits.
Infection process
The exploit kit downloads and executes TeslaCrypt on a system, and TeslaCrypt immediately copies itself into %AppData% using a random string of seven lowercase alphabetical characters (e.g., smshdff.exe). The original copy executes this new copy and then terminates. Software Restriction Policies can prevent execution within %AppData% and neutralize the malware.
At start time, the malware deletes any volume shadow copies on the system:
%WinDir%\system32\vssadmin delete shadows /all
It then creates a mutex to prevent more than one TeslaCrypt infection from occurring on the same system. CTU researchers have observed several different mutex values, including "System1230123" and "dslhufdks3".
To ensure persistence across reboots, the malware adds a Run key to the registry:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "<random string>":"<full path to copied malware in %AppData%>"
An identical key is also added to the HKCU hive in the victim's profile.
In every directory in which it encrypts files, TeslaCrypt creates a "HELP_RESTORE_FILES.txt" file that contains ransom payment details. Many hundreds or thousands of these files can be found on compromised systems. A ransom message (see Figure 2) is saved as "HeLP_ReSTORe_FILeS.bmp" on the desktop and becomes the desktop's background image. Some older versions used the filenames "HELP_TO_SAVE_YOUR_FILES" and "HELP_TO_DECRYPT_YOUR_FILES".
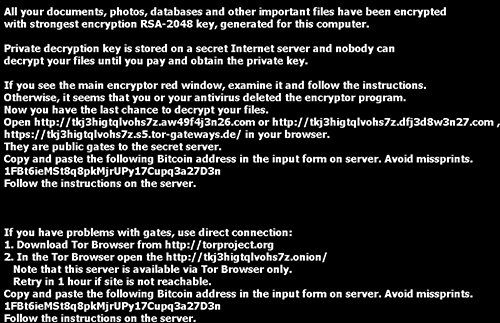
Figure 2. Ransom message set as desktop background by TeslaCrypt. (Source: Dell SecureWorks)
Finally, TeslaCrypt creates a desktop Windows shortcut link named "CryptoLocker", which points to the malware executable within %AppData%.
Encryption
TeslaCrypt uses the Advanced Encryption Standard (AES) algorithm to encrypt files, but the malware misrepresents its file encryption in two ways:
- It renames encrypted files with an "ecc" extension, which suggests use of an Elliptic Curve Cryptographic (ECC) algorithm. The malware uses the algorithm when generating Bitcoin addresses, but not to encrypt files.
- Splash screen messages and files left on compromised systems claim to use the RSA-2048 encryption algorithm.
TeslaCrypt targets a broad range of common file extensions (see Appendix A) that would be on any system used for general-purpose computing. It ignores music and video file formats such as MP3s and MP4s, as well as many file extensions associated with common business-class applications. It targets file formats from productivity suites such as Open Office and Microsoft Office, as well as formats associated with video games (e.g., media and "save" files) and creative applications (e.g., Adobe Photoshop).
The encryption process begins with the malware using the GetLogicalDriveStrings() API function to enumerate storage on the system's lettered drives (e.g., C:\). The GetDriveType() API call then selectively targets DRIVE_FIXED drives (e.g., hard disks, solid-state drives (SSDs)) and DRIVE_REMOTE drives (e.g., mapped network shares). TeslaCrypt does not attack removable (e.g., USB) storage or scan connected networks for open shares.
The malware recursively scans the drives for files with targeted extensions, and then opens, reads, and encrypts each file. The encrypted data is written into the original file, which reduces the likelihood that forensic tools can recover the original data. As shown in Figure 3, the encrypted file data is prepended with a 20-byte header composed of a 16-byte initialization vector (IV) and a four-byte value representing the original file size. The addition of this header, along with padding introduced by the encryption process, can slightly increase the size of encrypted files (typically by 1% or less). The new filename is identical to the original, including any extensions, but includes an appended "ecc" extension (e.g., document.pdf becomes document.pdf.ecc).
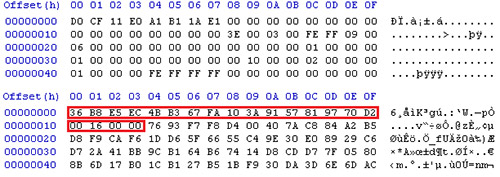
Figure 3. Unencrypted Excel file (top) versus encrypted version with header. (Source: Dell SecureWorks)
A list of encrypted files is stored in %AppData%\log.html. TeslaCrypt also stores metadata about the infection in a small (<1 KB) %AppData%\key.dat binary file (see Figure 4).
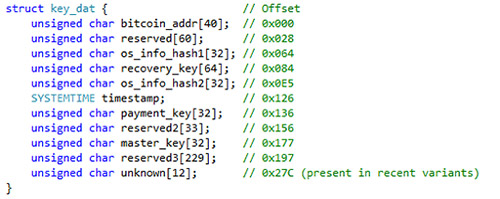
Figure 4. Organization of the key.dat files stored in %AppData%. (Source: Dell SecureWorks)
Command and control traffic
Like malware families such as the Chanitor downloader, TeslaCrypt hosts its command and control (C2) infrastructure on the Tor anonymity network. The TeslaCrypt C2 servers and ransom payment server reside within the Tor network as hidden services. Compromised systems communicate with these servers in two ways:
- Through publicly-available web-to-Tor gateways such as Tor2web.org, tor2web.fi, and blutmagie.de.
- Through proxy servers located on attacker-controlled assets (e.g., dpckd2ftmf7lelsa . aenf387awmx28 . com). These attacker-controlled domains are often hosted on legitimate infrastructure operated by third-parties such as CloudFlare.
Communication between a compromised system and the C2 infrastructure is often SSL-encrypted. Early TeslaCrypt versions included a backup communication mechanism that connected directly to 50 . 7 . 138 . 132, located in Amsterdam, Netherlands.
After the initial infection, the malware determines the system's public IP address via the legitimate ipinfo.io service (see Figure 5).
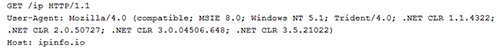
Figure 5. TeslaCrypt determining the compromised system's public IP address. (Source: Dell SecureWorks)
TeslaCrypt then phones home to a C2 server with an HTTP GET request (see Figure 6).
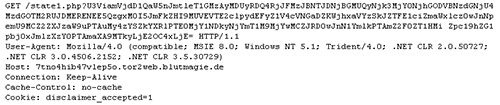
Figure 6. TeslaCrypt notifying its C2 server of a new infection. (Source: Dell SecureWorks)
A C2 server PHP component receives a single Base64-encoded parameter from the compromised system that decodes to the following string:
Subject=Ping&key=F302052D48F2E32A52C60F1D269726468F85A77F65837F936EBC0DD4A 9C813B9&addr=1EDU16rZrtArgUxqSFh6JZ8qiV3JBYLQ5r&files=0&size=0&version=0.3.3a &date=1426549266&OS=2600&ID=0&subid=0&gate=G2&is_admin=1&is_64=0&ip=192.168.1.1
The decoded string contains multiple parameters. A live C2 server acknowledges commands by returning an HTTP 200 OK response that contains "---!!!Done!!!---".
- Subject — represents the command verb of the request; may be one of three options:
- Ping — signals a new infection to the C2 server
- Crypted — sent when the victim's file system has been fully encrypted
- Payment — sent if the victim attempts to pay using the displayed dialog window
- key — modified version of the encryption key used to destroy files
- addr — unique Bitcoin address generated on the victim's system to send ransom payments
- files — total number of encrypted files
- size — total size, in megabytes, of encrypted files
- version — TeslaCrypt malware version (The first version analyzed by CTU researchers was 0.2.5, and the latest version as of this publication was 0.3.6a.)
- date — local time when the command was sent, in Unix epoch time format
- OS — build number of the operating system
- ID — identification number
- subid — secondary identification number; may be combined with ID to implement an affiliate program
- gate — indicates which web-to-Tor gateway transmitted the request
- is_admin — Boolean value indicating if the victim's account has Administrator privileges
- is_64 — Boolean value indicating if the compromised system is a 64-bit architecture
Unlike ransomware families such as CryptoLocker and CryptoWall, preventing TeslaCrypt from communicating with its C2 server does not prevent encryption. TeslaCrypt does not send beacons to its C2 server after sending the 'Ping' and 'Crypted' messages.
Payment
TeslaCrypt demands ransoms between $250 and $1000. Most ransom demands observed by CTU researchers have been 1.5 bitcoin (BTC), with an increase to 2.5 BTC after several days of non-payment. The malware operators seem to encourage payment through the Bitcoin network but also accept prepaid cards. North American victims are given the option to pay $1000 with PayPal My Cash cards, and European victims can pay €600 with PaySafeCard or uCash (see Figure 7).
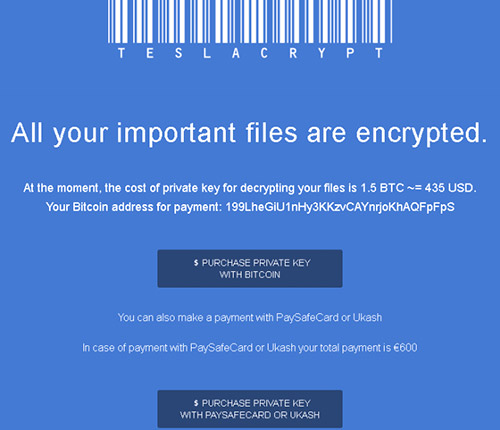
Figure 7. European ransom demand of 1.5 BTC or €600 by prepaid card. (Source: Dell SecureWorks)
Threat indicators
The threat indicators in Table 1 can be used to detect activity related to TeslaCrypt. The IP addresses and domains may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| 50.7.138.132 | IP address | TeslaCrypt C2 server |
| 46.4.20.40 | IP address | TeslaCrypt C2 server |
| 178.63.9.48 | IP address | TeslaCrypt C2 server |
| 94.242.216.5 | IP address | TeslaCrypt C2 server |
| 94.242.216.63 | IP address | TeslaCrypt C2 server |
| sshowmethemoney.com | Domain name | TeslaCrypt malicious proxy |
| jjeyd2u37an30.com | Domain name | TeslaCrypt malicious proxy |
| 63ghdye17.com | Domain name | TeslaCrypt malicious proxy |
| 42k2bu15.com | Domain name | TeslaCrypt malicious proxy |
| 42k2b14.net | Domain name | TeslaCrypt malicious proxy |
| 42kjb11.net | Domain name | TeslaCrypt malicious proxy |
| 2kjb9.net | Domain name | TeslaCrypt malicious proxy |
| 2kjb8.net | Domain name | TeslaCrypt malicious proxy |
| 2kjb7.net | Domain name | TeslaCrypt malicious proxy |
| 7hwr34n18.com | Domain name | TeslaCrypt malicious proxy |
| wh47f2as19.com | Domain name | TeslaCrypt malicious proxy |
| 63ghdye17.com | Domain name | TeslaCrypt malicious proxy |
| aw49f4j3n26.com | Domain name | TeslaCrypt malicious proxy |
| 79fhdm16.com | Domain name | TeslaCrypt malicious proxy |
| dfj3d8w3n27.com | Domain name | TeslaCrypt malicious proxy |
| 4lpwzo5ptsv6a2y5.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server (from November 2014) |
| 34r6hq26q2h4jkzj.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server |
| qcuikaiye577q3p2.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server |
| 7tno4hib47vlep5o.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server |
| 3kxwjihmkgibht2s.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server |
| epmhyca5ol6plmx3.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server |
| tkj3higtqlvohs7z.onion | Tor hidden service | TeslaCrypt C2 and ransom payment server |
| a9ed5ec475f4f746d77576a7c48f15ac | MD5 hash | 2014 TeslaCrypt sample |
| ff213401244ba42ae7bc629115dcee702895e3b90dbc 4fc1fbee03b7f71e8ebd | SHA256 hash | 2014 TeslaCrypt sample |
| 209a288c68207d57e0ce6e60ebf60729 | MD5 hash | 2015 TeslaCrypt sample #1 |
| 3372c1edab46837f1e973164fa2d726c5c5e17bcb888 828ccd7c4dfcc234a370 | SHA256 hash | 2015 TeslaCrypt sample #1 |
| 318eca04390a9ce009e09762c8150311 | MD5 hash | 2015 TeslaCrypt sample #2 |
| 1287ff572592401e16831c274648a399aada9d4d774 4d53c40c0d978bbb329d0 | SHA256 hash | 2015 TeslaCrypt sample #2 |
| 7616872b3a200264a8d476db29be2313 | MD5 hash | 2015 TeslaCrypt sample #3 |
| 18bd1ff24cf637c9ce36cd4e995b217a616063167355 497803cca6b58eab9020 | SHA256 hash | 2015 TeslaCrypt sample #3 |
| 8afa5dd088871bbd0d63c461413cb5a1 | MD5 hash | 2015 TeslaCrypt sample #4 |
| 1ee6da8ca0649ca3508d176164acdc14615ffd99eb2cb 48c50c247f0eac264b4 | SHA256 hash | 2015 TeslaCrypt sample #4 |
| b14dedb35189ff2761da7763a95c6893 | MD5 hash | 2015 TeslaCrypt sample #5 |
| f29be2a61e39742ed657545ff56f7b96cff58d50bf2cb fe8f7d4bdb7447b1e4f | SHA256 hash | 2015 TeslaCrypt sample #5 |
| 388fc7a1de13ec2345c18893be62d965 | MD5 hash | 2015 TeslaCrypt sample #6 |
| 8f1640e5b52122815510264321fab4b2c023015a2720 de1de787667e49fe3384 | SHA256 hash | 2015 TeslaCrypt sample #6 |
Table 1. Threat indicators for the TeslaCrypt ransomware.
Conclusion
File-encrypting ransomware continues to be a growing trend in malicious software. TeslaCrypt joins CryptoWall, CTB-Locker, and TorrentLocker as the top active ransomware threats. Although the Cisco Talos decryption tool allows many victims to recover files, the following actions may mitigate exposure to or damage from TeslaCrypt:
- Block executable files and compressed archives containing executable files before they reach a user's inbox.
- Keep operating systems, browsers, and browser plugins fully updated to prevent compromises resulting from exposure to exploit kits.
- Reevaluate permissions on shared network drives to prevent unprivileged users from modifying files.
- Implement Software Restriction Policies to prevent programs like TeslaCrypt from executing in common directories such as %AppData%.
Appendix A — Targeted file extensions
| .7z | .map | .m2 | .rb | .jpg |
| .rar | .wmo | .mcmeta | .png | .cdr |
| .m4a | .itm | .vfs0 | .jpeg | .indd |
| .wma | .sb | .mpqge | .txt | .ai |
| .avi | .fos | .kdb | .p7c | .eps |
| .wmv | .mcgame | .db0 | .p7b | |
| .csv | .vdf | .DayZProfile | .p12 | .pdd |
| .d3dbsp | .ztmp | .rofl | .pfx | .psd |
| .sc2save | .sis | .hkx | .pem | .dbfv |
| .sie | .sid | .bar | .crt | .mdf |
| .sum | .ncf | .upk | .cer | .wb2 |
| .ibank | .menu | .das | .der | .rtf |
| .t13 | .layout | .iwi | .x3f | .wpd |
| .t12 | .dmp | .litemod | .srw | .dxg |
| .qdf | .blob | .asset | .pef | .xf |
| .gdb | .esm | .forge | .ptx | .dwg |
| .tax | .001 | .ltx | .r3d | .pst |
| .pkpass | .vtf | .bsa | .rw2 | .accdb |
| .bc6 | .dazip | .apk | .rwl | .mdb |
| .bc7 | .fpk | .re4 | .raw | .pptm |
| .bkp | .mlx | .sav | .raf | .pptx |
| .qic | .kf | .lbf | .orf | .ppt |
| .bkf | .iwd | .slm | .nrw | .xlk |
| .sidn | .vpk | .bik | .mrwref | .xlsb |
| .sidd | .tor | .epk | .mef | .xlsm |
| .mddata | .psk | .rgss3a | .erf | .xlsx |
| .itl | .rim | .pak | .kdc | .xls |
| .itdb | .w3x | .big | .dcr | .wps |
| .icxs | .fsh | .unity3d | .cr2 | .docm |
| .hvpl | .ntl | .wotreplay | .crw | .docx |
| .hplg | .arch00 | .xxx | .bay | .doc |
| .hkdb | .lvl | .desc | .sr2 | .odb |
| .mdbackup | .snx | .py | .srf | .odc |
| .syncdb | .cfr | .m3u | .arw | .odm |
| .gho | .ff | .flv | .3fr | .odp |
| .cas | .vpp_pc | .js | .dng | .ods |
| .svg | .lrf | .css | .jpe | .odt |
Table 2. File extensions targeted by TeslaCrypt.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
