- Author: Joe Stewart
- Date: 18 October 2006
Understanding the purpose of malware simply by searching anti-virus writeups can sometimes be a daunting task. Often, we see trojans which have painfully little information about their functionality other than "backdoor", or "keylogger", or "proxy". In many cases, widely varying trojans are given similar, non-descriptive names like "Trojan.Agent.abc", further adding to the murky view we have of just what modern malware is up to.
Sometimes, when we shine a light on a particular piece of malware, we find some interesting things that would otherwise go unnoticed. One such piece of malware is the trojan sometimes called "Troj/SpamThru", among other names.
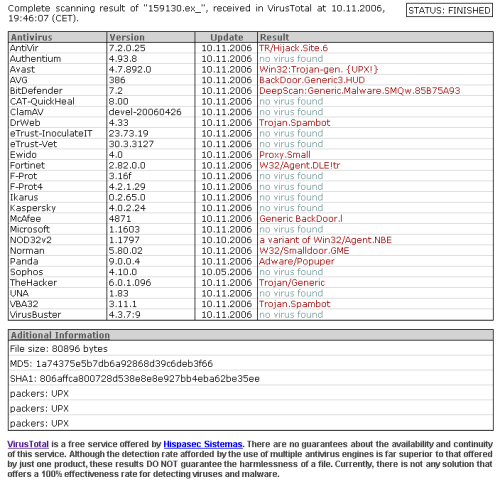
Note that the current incarnation is not called SpamThru by any vendor who detects it in the above scan result from VirusTotal, however, by correlating behavior with previous writeups, it is apparent that it is the same trojan. Given that SpamThru is the most descriptive and unique name assigned to it, we have chosen to call it that in this writeup as well. Overall, detection by AV vendors is sparse, but that's to be expected given that SpamThru is a money-making operation, and the author takes great care to make sure that detection by the major vendors is avoided by frequently updating the code.
Although many trojans and viruses are turning to rootkits to hide their activities on a system, SpamThru uses little more than a few registry keys to keep its hold on the system. It uses the classic HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run key in order to launch at startup, but also tries to start from HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SharedTaskSchedulerand SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad just in case the Run key is removed.
The registry keys are named based on the trojan's control server port, so you might see any of the following at this time:
| Run Registry Key Name | SharedTaskScheduler/ShellServiceObjectDelayLoad Registry Key Name/CLSID | |
|---|---|---|
| Explorer 2222 | DCOM Server 2222 | {2C1CD3D7-86AC-4068-93BC-A02304BB2222} |
| Explorer 2225 | DCOM Server 2225 | {2C1CD3D7-86AC-4068-93BC-A02304BB2225} |
| Explorer 2234 | DCOM Server 2234 | {2C1CD3D7-86AC-4068-93BC-A02304BB2234} |
| Explorer 2235 | DCOM Server 2235 | {2C1CD3D7-86AC-4068-93BC-A02304BB2235} |
| Explorer 2236 | DCOM Server 2236 | {2C1CD3D7-86AC-4068-93BC-A02304BB2236} |
| Explorer 2237 | DCOM Server 2237 | {2C1CD3D7-86AC-4068-93BC-A02304BB2237} |
| Explorer 2238 | DCOM Server 2238 | {2C1CD3D7-86AC-4068-93BC-A02304BB2238} |
| Explorer 2239 | DCOM Server 2239 | {2C1CD3D7-86AC-4068-93BC-A02304BB2239} |
| Explorer 2240 | DCOM Server 2240 | {2C1CD3D7-86AC-4068-93BC-A02304BB2240} |
| Explorer 2241 | DCOM Server 2241 | {2C1CD3D7-86AC-4068-93BC-A02304BB2241} |
| Explorer 2242 | DCOM Server 2242 | {2C1CD3D7-86AC-4068-93BC-A02304BB2242} |
| Explorer 2243 | DCOM Server 2243 | {2C1CD3D7-86AC-4068-93BC-A02304BB2243} |
Basically SpamThru is designed to send spam from an infected computer. This type of operation is now years old, however, SpamThru has some new twists.
Peer-to-Peer Communication
SpamThru uses a custom P2P protocol in order to share information with other peers including the IP addresses and ports and software version of the control server, template servers, and all the peers they each know about. Control is still maintained by a central server, but in case the control server is shut down, the spammer can update the rest of the peers with the location of a new control server, as long as he/she controls at least one peer.
The network generally consists of one control server (running multiple peer-nets on different ports), several template servers, and around 500 peers per port. There appears to be a limit to how many peers each port can effectively control, as the overhead in sharing information between hosts is fairly large. The estimated number of infected hosts connected to the one control server we looked at was between one and two thousand across all open ports (however this is only counting IP addresses, which can skew the actual numbers due to on dynamic IPs and NAT.)
The protocol is binary-based and the initial packets usually begin with a header:
01 = protocol version?68 73 35 70 00 = magic (hs5p\x00)
The header is followed by a one-byte command code, and any arguments to the command. The command codes we've seen are:
| Command Code | Type | Direction |
|---|---|---|
| 00 | Peer login/information exchange | to control, to/from peers |
| 01 | Request update | to control |
| 03 | Request file (usually empty) | to control |
| 04 | Request spam template | to template server |
| 05 | Report on results of spam run | to template server |
| 07 | Request AV DLL | to control |
| 08 | Report AV scan status (usually not used) | to control |
So far, the network appears to use 208.66.195.67 (bn.i-ru.net) as the sole control server, and the template servers seen are 208.66.193.26, 208.66.193.29, 216.255.178.170, 216.255.178.178, 216.255.182.202.
Anti-Virus Scanning
Like many viruses and trojans, SpamThru attempts to prevent installed anti-virus software from downloading updates by adding entries into the %sysdir%\drivers\etc\hosts file pointing the AV update sites to the localhost address. In the past, we've also seen malware which tries to uproot other competing malware on an infected system by killing its processes, removing its registry keys, or setting up mutexes which fool the other malware into thinking it is already running and then exiting at start.
SpamThru takes the game to a new level, actually using an antivirus engine against potential rivals. At startup, SpamThru requests and loads a DLL from the control server. This DLL in turn downloads a pirated copy of Kaspersky AntiVirus for WinGate from the control server into a concealed directory on the infected system. It patches the license signature check in-memory in the Kaspersky DLL in order to avoid having Kaspersky refuse to run due to an invalid or expired license. Ten minutes after the download of the DLL, it begins to scan the system for malware, skipping files which it detects are part of its own installation. Any other malware found on the system is then set up to be deleted by Windows at the next reboot.
Template-based spam
Inside of acting as a proxy for spam senders, each SpamThru client is its own spam engine, downloading a template containing the spam, random phrases to use as hash-busters, random "from" names, and a list of several hundred email addresses to send to.
Encryption
The spam templates are encrypted with AES (Rijndael) encryption. Also, an AES-based challenge-response authentication method is used to prevent third-parties from being able to download the templates from the template server.
GIF randomization
GIF files in the spam template are modified with each spam sent, to change the width and height, and a section of random pixels is appended to the bottom, in order to defeat anti-spam solutions which might try and reject mail based on a static image.
 |
 |
| Original GIF from spam template | Resulting GIF sent in spam |
In this case, the GIF comprises most of the message, with the remainder being hash-busters that are mostly invisible to the client. Below is what an email sent by the SpamThru trojan would look like to an Outlook user (assuming it wasn't caught in the junk email folder):
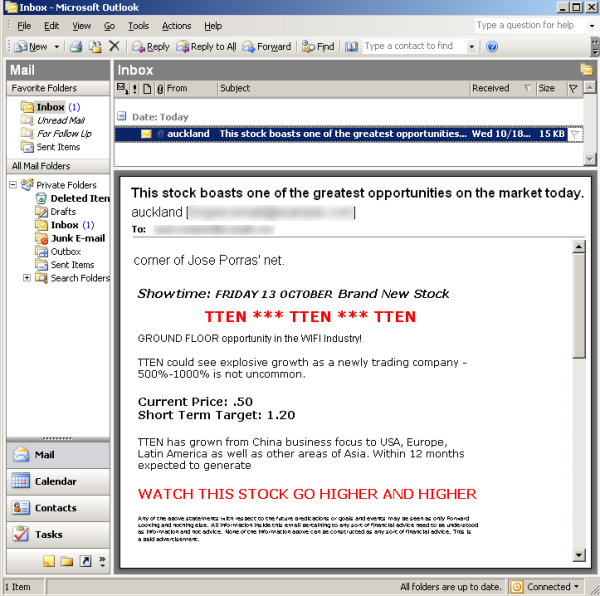
Although we've seen automated spam networks set up by malware before (Sober, Bobax, Bagle, etc) this is one of the more sophisticated efforts. The complexity and scope of the project rivals some commercial software. Clearly the spammers have made quite an investment in infrastructure in order to maintain their level of income.
Detecting infections of SpamThru on your networks can be done using the Snort IDS and the following signatures:
alert tcp any any -> any any (msg:"SpamThru trojan peer exchange"; flow:established,to_server; content:"|01|hs5p|0000|"; depth:7; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000553; rev:1;)
alert tcp any 25 -> any any (msg:"SpamThru trojan SMTP test successful"; flow:established,to_client; dsize:6; content:"XSMTPX"; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000554; rev:1;)
alert tcp any any -> any any (msg:"SpamThru trojan update request"; flow:established,to_server; content:"|01|hs5p|0001|"; depth:7; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000555; rev:1;)
alert tcp any any -> any any (msg:"SpamThru trojan AV DLL request"; flow:established,to_server; content:"|01|hs5p|0007|"; depth:7; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000556; rev:1;)
alert tcp any any -> any any (msg:"SpamThru trojan spam template request"; flow:established,to_server; content:"|01|hs5p|0004|"; depth:7; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000557; rev:1;)
alert tcp any any -> any any (msg:"SpamThru trojan spam run report"; flow:established,to_server; content:"|01|hs5p|0005|"; depth:7; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000558; rev:1;)
alert tcp any any -> any any (msg:"SpamThru trojan AV scan report"; flow:established,to_server; content:"|01|hs5p|0008|"; depth:7; classtype:trojan-activity; reference:url,www.secureworks.com/research/spamthru; sid:1000559; rev:1;)
Update: Additional analysis of SpamThru is now available.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
