Overview
Dell SecureWorks Counter Threat Unit(TM) (CTU) researchers analyzed an ongoing spam campaign that uses the "UPS delivery notification tracking number" lure to infect unsuspecting users. While UPS-related spam emails are common, this particular campaign has been observed since October 2013 and uses exploit-laden documents to deliver its payload. The initial delivered payload is the Liftoh downloader trojan, which in turn downloads additional malware as a secondary payload onto the victim's system.
Analysis
Figure 1 shows the spam email containing a link to a malicious "Rich Text Format" (RTF) file. The malicious RTF is attached to the email, disguised as a .doc file.
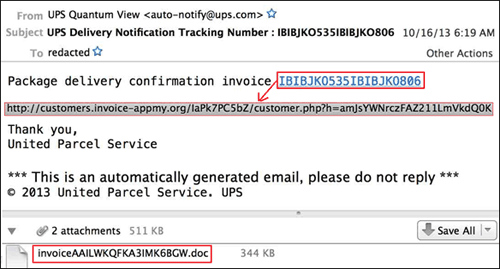
Figure 1. Spam email containing link and attachments for malicious RTF file. (Source: Dell SecureWorks)
Figure 2 shows an example header from the spam email with spoofed sender information.
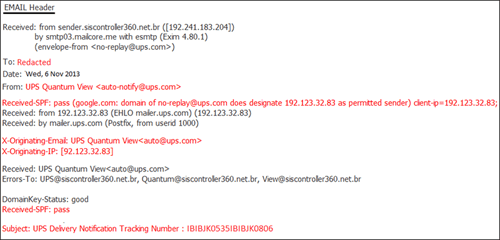
Figure 2. Email header with spoofed sender information. (Source: Dell SecureWorks)
The spoofed sender is <auto-notify @ ups . com> or <auto @ ups . com>, but the headers reveal some of the actual senders (see Table 1). Some of the hosts listed in Table 1 may have appeared in DNS blacklisting lists such as SpamhausDBL, PSBL, SURBL, and SORBS, and some hosts are offline as of this publication. These hosts might have been compromised and used for SMTP relays, or could be part of a “use-and-throw” attacker-owned spam infrastructure.
| Domain name | IP address | ASN | ISP | Location |
| mail . enviosuperfast . info | 184.82.214.54 | AS21788 | Network Operations Center |
Scranton, Pennsylvania, United States |
| mail1 . sinalturbo . com . br | 189.85.19.140 | AS11835 | Ipe Informatica Ltda | Matinhos, Parana, Brazil |
| mail1 . ideasinnovation . info | 46.165.219.112 | AS16265 | LeaseWeb B.V. | Germany |
| mail1 . studioinfinity . info | 46.165.219.89 | AS16265 | LeaseWeb B.V. | Germany |
| mail1 . infosoftwebmarketing . net | 177.10.190.154 | AS52929 | Elias Peixoto Nacle Estefan - ALBERGUE IDC |
Brazil |
| mail2 . infosoftwebmarketing . net | 177.10.190.155 | AS52929 | Elias Peixoto Nacle Estefan - ALBERGUE IDC |
Brazil |
| mail2 . topbrasil100 . net | 177.10.190.3 | AS52929 | Elias Peixoto Nacle Estefan - ALBERGUE IDC |
Brazil |
| mail1 . sarl-bjt . fr | 88.173.220.169 | AS12322 | Free SAS | Paris, Ile-de- France, France |
| dns . sarl-bjt . fr | 78.229.183.241 | AS12322 | Free SAS | Paris, Ile-de- France, France |
| mail . planete . sn | 188.165.255.149 | AS16276 | OVH Systems | France |
| mail . alphamix . info | 177.137.18.72 | AS28271 | DataCorpore Servi | Brazil |
| t5 . com . br | 201.33.22.202 | AS28271 | DataCorpore Servi | Brazil |
| sender . siscontroller360 . net . br | 192.241.183.204 | AS62567 | Digital Ocean, Inc. | New York, New York, United States |
| mail11 . superlojas . biz | 192.157.233.99 | AS18978 | Enzu Inc | Henderson, Nevada, United States |
| ip1 . www . 653 . webpainel . org | 198.24.186.122 | AS19437 | Secured Servers LLC | Tempe, Arizona, United States |
| 192.123.32.83 | Unknown | Kraft Foods Group | Winnetka, Illinois, United States |
Table 1. Senders of spam email.
CTU researchers observed the following domains in spam recipient email addresses:
- gicom . nl
- mvdloo . nl
- cneweb . de
- yahoo . fr
- helimail . de
- online . fr
- tq3 . co. uk
- excel . co. jp
- smegroup . co . uk
- fujielectric . co . jp
- st-pauls . hereford . sch . uk
The RTF file contains exploits for patched vulnerabilities CVE-2012-0158 (MSCOMCTL.OCX RCE vulnerability) and CVE-2010-3333 (RTF stack buffer overflow vulnerability). Opening the RTF file drops and launches an empty document file in the user's %TEMP% folder with filename "cv.doc". Successful execution of the exploit code drops the Liftoh downloader malware onto the victim's system. This malware was observed spreading via Skype and other instant messenger applications in May 2013. Liftoh also downloaded the Phopifas worm as a secondary payload.
Liftoh is initially dropped into and executed from the user's %TEMP% folder with filenames such as "CD.tmp" or "Winword.exe". The legitimate "Winword.exe" file belongs to the Microsoft Office Word application and resides in the Program Files directory. The malware then copies itself to the %CommonAppData% and %AppData% folders with a random filename such as "afdaafdebcfsacfsfdsf.exe".
The path name and file location are determined by the following environment variables:
- %Temp% refers to the user's Temp folder and by default is "C:\Documents and Settings\<Current User>\Local Settings\Temp" for Windows 2000/XP and "C:\Users\<Current User>\AppData\Local\Temp" for Windows Vista, Windows 7, and Windows 8.
- %CommonAppData% refers to the Application Data folder for the All Users Profile. By default, the location of this folder is "C:\Documents and Settings\All Users\Application Data" for Windows 2000/XP and "C:\ProgramData\" for Windows Vista, Windows 7, and Windows 8.
- %AppData% refers to the current user's Application Data folder. By default, the location of this folder is "C:\Documents and Settings\<Current User>\Application Data" for Windows 2000/XP and "C:\Users\<Current User>\AppData\Roaming" for Windows Vista, Windows 7, and Windows 8.
Liftoh injects malicious code into a legitimate system process such as "explorer.exe" and then adds its path to the system's Run registry key to maintain persistence. The Run registry key is HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
The Liftoh downloader initially sends information about the infected system, including the GUID, to its command and control (C2) server. The communication is encrypted with the C2 hostname, in a process similar to that used by the Shylock trojan. The C2 server uses the infected system's GUID to encrypt commands and malware payloads.
Figure 3 shows initial network communication (HTTP POST request) observed from an infected system by the most recent variant of Liftoh downloader as of this publication. The text highlighted in purple is the POST request, and the text highlighted in red is the host or C2 domain.
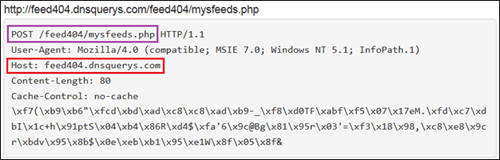
Figure 3. Initial network activity associated with the most recent variant of Liftoh downloader. (Source: Dell SecureWorks)
Figure 4 shows initial network communication (HTTP POST request) observed from an infected system by a previous variant of Liftoh downloader that was observed in May 2013. The text highlighted in purple is the POST request, and the text highlighted in red is the host or C2 domain.
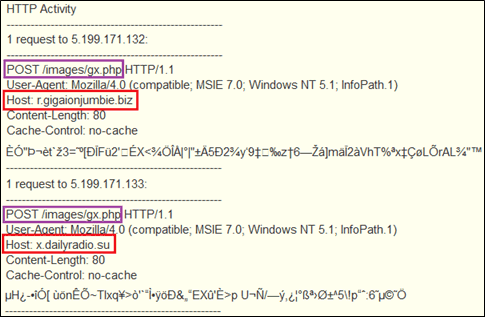
Figure 4. Initial network activity associated with a previous variant of Liftoh downloader. (Source: Dell SecureWorks)
Liftoh downloads and executes additional malware from hard-coded URLs. CTU researchers have observed Liftoh downloading Bitcoin miner and a variant of Zeus/Zbot (version 2.1.1.2). In the past, Phopifas worm was downloaded as a secondary payload from the Hotfile file sharing website. Figure 5 shows a sample of network activity (HTTP GET request) for a previous variant of the Liftoh downloader downloading the secondary payload. The text highlighted in purple shows the GET request, and the text highlighted in red shows the host or C2 domain.
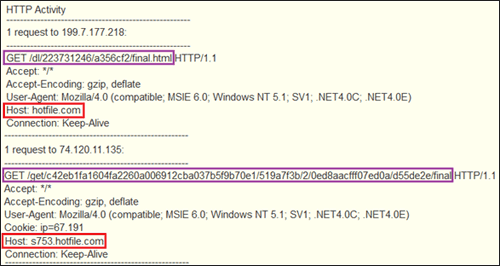
Figure 5. Secondary payload (Phopifas worm) download network activity. (Source: Dell SecureWorks)
Figure 6 shows where the threat actor embedded distinguishing strings within the data section of one of the malware's binary payloads (MD5: e2ee9453132f90c2e9b8a0bccb2f605d).
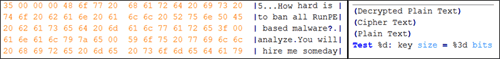
Figure 6. Additional strings embedded by the threat actor within the data section of the malware's binary payload. (Source: Dell SecureWorks)
Telemetry
Telemetry from Dell SecureWorks event monitoring shows organizations in the following market verticals have been affected by Liftoh:
- Banking
- Manufacturing
- Healthcare
- Legal
- Credit unions
- Retail
- Technology providers
Figure 7 shows a timeline of the Liftoh downloader activity based on Dell SecureWorks telemetry. The majority of events were for the most recent variant of the Liftoh downloader beginning in November 2013.
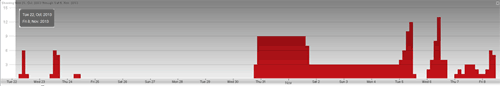
Figure 7. Timeline of activity associated with Dell SecureWorks iSensor countermeasures for the Liftoh downloader between October 22 and November 8, 2013. (Source: Dell SecureWorks)
Conclusion
The threat actors seem to be delivering Liftoh downloader via different mechanisms. In May 2013, the threat actors used spammed links to Skype users and other instant messenger applications. In October 2013, a spam email campaign used exploit-laden RTF documents. It is very likely that the threat actors will switch to other delivery mechanisms in the future that use social engineering techniques to maximize infection yields. It is also likely that the threat actors may leverage the Liftoh downloader to deliver a variety of other malware as secondary payloads.
Dell SecureWorks recommends that organizations protect themselves against malicious campaigns by deploying a defense-in-depth strategy that includes the following components:
- Ensure that your Microsoft Office applications are current and up to date with security updates.
- Ensure that your browser application software is up to date with all available security updates to prevent exploitation of known browser vulnerabilities that deliver "drive-by" downloads.
- Ensure that your version of the Windows operating system has all available security updates.
- Schedule and maintain routine patching cycles, especially on servers that host public services and are accessible through the firewall, such as HTTP, FTP, email, and DNS services.
- Leverage features in Microsoft Office applications to improve overall security, such as disabling ActiveX, disabling macros, and blocking external content.
- Install and tune spam filters on your email server to block suspicious and malicious email content. For example, flag or block email containing file attachments that are commonly used to spread threats, such as .exe, .pif, .scr, .vbs, .hlp, and .bat files. Deploy advanced malware protection devices inline with incoming email streams containing malicious file attachments as well as subsequent file downloads.
- Ensure that appropriate policies are in place to restrict programs and users of a computer to only use the lowest level of privileges necessary to complete a task. Users should not operate with Administrative privileges.
- Disable AutoPlay on network and removable drives to prevent the automatic launching of executable files.
- Apply post-infection controls such as firewall policies, web proxies, file downloads over HTTPS, and associated log monitoring to identify anomalies. If an infection is detected, immediately isolate compromised computers to prevent threats from spreading. If needed, perform a forensic analysis on the infected system to identify the attack vector and identify potential data exfiltration. CTU researchers highly recommend restoring infected systems to a clean state using trusted media.
- Train users not to click links or open attachments in unexpected emails. Also, train users not to execute software that has been downloaded from the Internet until it has been scanned for malware with an antivirus application.
Threat indicators
The threat indicators in Table 2 can be used to detect activity related to this campaign. The domains and IP addresses listed in the indicators table may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| feed404.dnsquerys.org | Domain name | C2 and data exfiltration server Resolves to 158.255.2.60 HTTP POST request for /feed404/myfeeds.php |
| feed404.dnsquerys.com | Domain name | C2 and data exfiltration server Resolves to 158.255.2.60 HTTP POST request for /feed404/myfeeds.php |
| feeds.nsupdatedns.com | Domain name | C2 and data exfiltration server Resolves to 158.255.2.60 HTTP POST request for /feed404/myfeeds.php |
| feeds404.dnsmicrosf.com | Domain name | C2 and data exfiltration server Resolves to 158.255.2.60 HTTP POST request for /feed404/myfeeds.php |
| 404.mysyncdns.com | Domain name | C2 and data exfiltration server Resolved to 146.0.79.146 on October 21, 2013 Resolved to 118.67.250.91 on October 22, 2013 HTTP POST request for /feed404/feed.php |
| 404.dnsmicrosf.com | Domain name | C2 and data exfiltration server HTTP POST request for /feed404/feed.php |
| feed.queryzdnsz.org | Domain name | C2 and data exfiltration server Resolved to 118.67.250.91 HTTP POST request for /feedswebz/feed/mysfeedys.php HTTP GET request for /feedswebz/html/ServerBWS.exe |
| r.gigaionjumbie.biz | Domain name | C2 and data exfiltration server Resolved to 5.199.171.131 in May 2013 Resolved to 5.199.171.132 in May 2013 Resolved to 5.199.171.133 in May 2013 HTTP POST request for /images/gx.php |
| x.dailyradio.su | Domain name | C2 and data exfiltration server Resolved to 5.199.171.131 in May 2013 Resolved to 5.199.171.132 in May 2013 Resolved to 5.199.171.133 in May 2013 HTTP POST request for /images/gx.php |
| customers.invoice-appmy.org | Domain name | Hosts download for malicious RTF document Resolves to 118.67.250.91 HTTP GET request for /IaPk7PC5bZ/PYTWNBZBEF.php HTTP GET request for /IaPk7PC5bZ/customer.php |
| customer.invoice-appmy.com | Domain name | Hosts download for malicious RTF document Resolves to 118.67.250.91 HTTP GET request for /IaPk7PC5bZ/PYTWNBZBEF.php HTTP GET request for /IaPk7PC5bZ/customer.php |
| customer.appmys-ups.org | Domain name | Hosts download for malicious RTF document Resolves to 118.67.250.91 HTTP GET request for /B4VByTbwk4/PYTWNBZBEF.php HTTP GET request for /B4VByTbwk4/customer.php |
| customer.appmys-ups.com | Domain name | Hosts download for malicious RTF document Resolves to 118.67.250.91 HTTP GET request for /B4VByTbwk4/PYTWNBZBEF.php HTTP GET request for /B4VByTbwk4/customer.php |
| static.invoice-appmy.com | Domain name | Hosts download for malicious RTF document Resolves to 118.67.250.91 HTTP GET request for /Om7T4PaFJ9/PYTWNBZBEF.php HTTP GET request for /Om7T4PaFJ9/customer.php |
| luxlibertins.com | Domain name | Hosts download of malicious RTF document Resolves to 213.186.33.87 HTTP GET request for /statement.doc |
| 158.255.2.60 | IP address | Associated IP address of C2 and data exfiltration server ASN: AS49335 Navitel Rusconnect Ltd ISP: Mir Telematiki Ltd Country: Russian Federation |
| 146.0.79.146 | IP address | Associated IP address of C2 and data exfiltration server ASN: 57043; HOSTKEY-AS HOSTKEY B.V. Country: Netherlands |
| 118.67.250.91 | IP address | Associated IP address of C2 and data exfiltration server ASN: AS17447; NET4-IN Net4India Ltd Country: India |
| 5.199.171.131 | IP address | Associated IP address of C2 and data exfiltration server ASN: AS16125; UAB Duomenu Centras Country: Cyprus / Lithuania |
| 5.199.171.132 | IP address | Associated IP address of C2 and data exfiltration server ASN: AS16125; UAB Duomenu Centras Country: Cyprus / Lithuania |
| 5.199.171.133 | IP address | Associated IP address of C2 and data exfiltration server ASN: AS16125; UAB Duomenu Centras Country: Cyprus / Lithuania |
| ad0ef249b1524f4293e6c76a9d2ac10d | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| e335af83d768498505957df217a1c46c1a0ee6cbdf 884d7a11166831dbd5e825 |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| 7500198c94051785a68addc5f264a10f | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 71e8c525d8399c2285dc2c06b09a6779078c782f 52682000c2633f4ffc6773fa |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| ae83982f1ac50b4b08d7e509bc9cfc45 | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 072b71c0ec67ff541b1fda21c4df5cc74ea3ef32254 6916214860529a9a2254a |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| 8244c515873ecc466ebf3be970477c04 | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 53c45ce4b80ade517afc6b2969d054063893418d ab41f5832df3a41b625f1e64 |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| 625eb0ba883eece4edb7b09602d7da78 | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 7ae68e2ea93115a786e902ab98f104e22ef38d9f91 36d6155e45653bd1ed4e6b |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| a0b05cf03031edcdd4e4dd1e8f786255 | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 2c06345b8ad01ea872cee37c71deab1aada22836e 9f2788919480264ef9dc218 |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| b20d0254faedc6608d640290aeb20b4a | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 6c654921074a82ff6f4a6309b5dfa94587efcb81cd 3d8559eac3488102f51d0a |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| 153a5282bcee2b9a3d0a13da13b79718 | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| 5538bf5442e76ff47f2713f0d82064083262193c5c de660dbcbce7e873dd8532 |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| 7c2fd4abfe8640f8db0d18dbecaf8bb4 | MD5 hash | Malicious document containing exploit for CVE-2012-0158 |
| ccf7fed174dc9864c810d1c53b1ba7dfedede41cc9 fd2ec82d85ec865ca67db8 |
SHA256 hash | Malicious document containing exploit for CVE-2012-0158 |
| 62e25cc76291a3f348324172ff306ba0 | MD5 hash | Malicious binary (Liftoh downloader) |
| 83f4b9560085c1f8eee3c43235c74c9152289ffe8c ae141f80f1fba9e26d8281 |
SHA256 hash | Malicious binary (Liftoh downloader) |
| a4746ecbb7dc5a9856a15ba80cc2cc3d | MD5 hash | Malicious binary (Liftoh downloader) |
| 8a4a8ffad419e2a39a20b2c491f59d54b9ba014dcf 7671552bd34fec90649300 |
SHA256 hash | Malicious binary (Liftoh downloader) |
| d8362a96f0f2920a82d8f41ec342a679 | MD5 hash | Malicious binary (Liftoh downloader) |
| 43bdb0fa301d758c0b72b69258fc09a1d9cec57c6 dcd032bea915705de0e13d3 |
SHA256 hash | Malicious binary (Liftoh downloader) |
| 61b384950ca6586b35898b2223d36f37 | MD5 hash | Malicious binary (Bitcoin miner (BitWall), secondary payload) |
| dfbd4ce72503b9558a4ba872c0d5d6ffa62727f5d7 74284c17b8a15c8f5e807c |
SHA256 hash | Malicious binary (Bitcoin miner (BitWall), secondary payload) |
| 18a429ffa3441df8edb200f92806f720 | MD5 hash | Malicious binary (Phopifas worm (Dorkbot, Skypii), secondary payload) |
| d4ca04308caf0e2496b008376d3b124e73a463ed 27e4defe0d5c46664b08c79a |
SHA256 hash | Malicious binary (Phopifas worm (Dorkbot, Skypii), secondary payload) |
| e2ee9453132f90c2e9b8a0bccb2f605d | MD5 hash | Malicious binary (Zeus/Zbot variant, secondary payload) |
| b4e57e2ac90a7758c09f0a975f3382673ddcdcec1 b39e68eef8dac17158c0136 |
SHA256 hash | Malicious binary (Zeus/Zbot variant, secondary payload) |
| f6b201fb248a0fcd31b0488449776a9f | MD5 hash | Malicious binary (Zeus/Zbot variant, secondary payload) |
| aae885295762461c4aabe1fc826b0dcc93762b9c 96ef4c93122751c321261028 |
SHA256 hash | Malicious binary (Zeus/Zbot variant, secondary payload) |
| e5e1ee559dcad00b6f3da78c68249120 | MD5 hash | Malicious binary (Zeus/Zbot variant, secondary payload) |
| 889589844d0f6a79dfff7de99e165d7ba796b26c9f d4c8e059db36d509d6b549 |
SHA256 hash | Malicious binary (Zeus/Zbot variant, secondary payload) |
| 015e60d0ddff09d7df66d926d3793cc8 | MD5 hash | Malicious self-extracting RAR archive executable |
| 2695e33e671c4eee1e55ad534d9b33445a56b8ffe ff50b7c63fa12f266de1088 |
SHA256 hash | Malicious self-extracting RAR archive executable |
| 718532b47f2ae3006df2268ba3d1f5b9 | MD5 hash | Malicious self-extracting RAR archive executable |
| e65e8ba751fa23414c045bad5333af3f7cfe453599 bea7cdd15403c36a132fd6 |
SHA256 hash | Malicious self-extracting RAR archive executable |
| invoiceBQW8OYJDDGXIPN8H63.doc | Filename | Malicious RTF file containing exploit |
| invoiceAAILWKQFKA3IMK6BGW.doc | Filename | Malicious RTF file containing exploit |
| invoiceU6GCMXGLL2O0N7QYDZ.doc | Filename | Malicious RTF file containing exploit |
| invoiceCM0V9ORWJF23KX8PAP.PDF.exe | Filename | Malicious self-extracting RAR archive executable |
| fotos_facebook-20052013-png.exe | Filename | Malicious binary |
| adcbfbcebcfsacfsfdsf.exe | Filename | Malicious binary |
| afdaafdebcfsacfsfdsf.exe | Filename | Malicious binary |
| cabcbfdbeffbfcsacfsfdsf.exe | Filename | Malicious binary |
| ccbaddaabdfsacfsfdsf.exe | Filename | Malicious binary |
| dbcdfbfbbebsacfsfdsf.exe | Filename | Malicious binary |
| dfbbffbabeadfbsacfsfdsf.exe | Filename | Malicious binary |
| fbaaddacacsacfsfdsf.exe | Filename | Malicious binary |
| -1_cc_fabbc6a1-c573-4ea0-9ca1- 50004b35a440sacfsfdsf |
Mutex | Runtime Mutex created by malware |
| -3__fabbc6a1-c573-4ea0-9ca1- 50004b35a440sacfsfdsf |
Mutex | Runtime Mutex created by malware |
Table 2. Indicators related to Liftoh downloader spam campaign.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
