- Author:Dell SecureWorks Counter Threat Unit(TM) Threat Intelligence
- Date: 13 December 2013
Production use of software in a networked environment is typically surrounded by security processes to mitigate newly discovered security vulnerabilities. Software patch management is one of the fundamental security processes that organizations employ to mitigate risk and ensure system compliance. Software vendors usually update software to fix discovered vulnerabilities and release new software versions or patches to existing software versions. When a software vendor discontinues updates for security-related issues, newly discovered vulnerabilities become persistent threats in an organization's attack surface. When a software application is widely deployed, the attack surface becomes a significant risk.
Overview
Microsoft has announced that extended support for the Windows XP operating system is scheduled to end on April 8, 2014. According to Microsoft, end of support means an end to the following features:
- Security updates
- Non-security hotfixes
- Free or paid assisted support options
- Online technical content updates
Analysis
The Microsoft Windows XP operating system is one of the most widely deployed operating systems on globally networked systems. By some estimates, the Microsoft Windows XP operating system still has a one-third share of the desktop operating system market.
Continuing to use Windows XP beyond the end-of-support date presents security and business risks to organizations. Any newly found software vulnerabilities in Windows XP will essentially be perpetual zero-day vulnerabilities because vendor updates will not be released. In situations where Windows XP is used in a regulated application subject to audit and compliance review, business risk will include exposure to a control failure based on an inability to maintain patch levels for known software vulnerabilities.
There are two general approaches to mitigate the risk posed by the Windows XP end-of-support date. Both approaches involve implementation cost to an organization.
- Migrate Windows XP systems to supported operating systems to meet ongoing security control requirements.
- May require migration of dependent applications
- May require staff re-training
- Enables continued use of software patching processes to remediate newly discovered vulnerabilities
- Implement and maintain compensating controls around existing Windows XP systems until migration to a supported operating system.
- May defer migration and re-training costs, but will likely not eliminate these costs
- May require compensating control implementation and documentation for each newly discovered vulnerability
- May not completely remediate exposures created by newly disclosed vulnerabilities, forcing unaddressable compliance issues
- Introduces risk of compliance failure
The Dell SecureWorks Counter Threat Unit(TM) (CTU) research team endorses a timely migration strategy approach and cannot recommend a compensating control approach.
The CTU research team tracks software vulnerabilities across many vendors and products using the Common Platform Enumeration (CPE) standard. As of November 30, 2013, CTU researchers continue to document newly discovered vulnerabilities in one or more versions of Windows XP (see Figure 1). As of this publication, CTU researchers have cataloged more than 760 vulnerabilities linked to Windows XP.
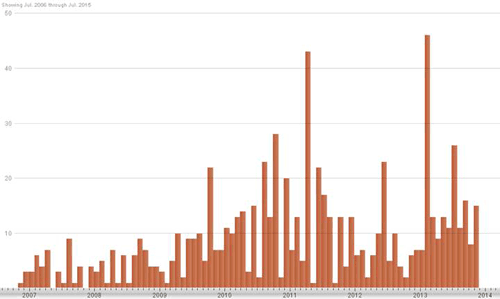
Figure 1. Vulnerabilities impacting Windows XP cataloged by CTU researchers per month. (Source: Dell SecureWorks)
As shown in Figure 2, many of the 175 vulnerabilities cataloged in 2013 have been rated as "high severity" based on Common Vulnerability Scoring System (CVSS) scoring standards followed by the NIST National Vulnerability Database. A high-severity vulnerability has a CVSS base score between 7.0 and 10.0.
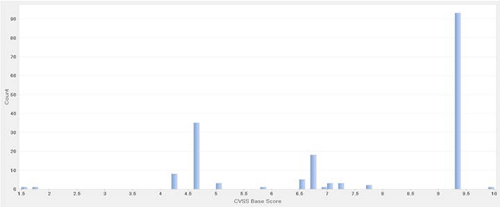
Figure 2. CVSS base scores for Windows XP vulnerabilities cataloged in 2013. (Source: Dell SecureWorks)
CTU researchers expect continued discovery and disclosure of new software vulnerabilities linked to Windows XP well beyond the end-of-support date. The Windows XP codebase consists of approximately 60 million lines of code. A study released in 2004, three years after the launch of Windows XP, indicated that the average defect rate in well-produced software was about 1 defect per 1,000 lines of code. The surface area for potential defects in Windows XP code is well into the tens of thousands in order of magnitude.
In addition, the CTU research team shares a speculative opinion by Microsoft and other security vendors that there are known, undisclosed zero-day vulnerabilities in Windows XP being closely guarded by potential attackers until after the end-of-support date. To a potential attacker, an exploitable vulnerability that will never be patched in 1 of 3 desktop operating systems connected to the Internet has tremendous value. Although CTU researchers do not have evidence to support the opinion, there is no evidence to discount the potential risk posed by this serious threat scenario.
Conclusion
From a patch management lifecycle perspective, it is extremely important to consider that the primary disclosure of new vulnerabilities in Windows XP will no longer originate from the authoritative software vendor. Once Microsoft discontinues extended support, there will not be a participating vendor to execute and communicate a typical responsible disclosure process for newly discovered vulnerabilities. Windows XP will be excluded from the monthly security bulletin process. Microsoft Active Protections Program (MAPP) members, such as Dell SecureWorks, will no longer have access to authoritative information about Windows XP vulnerabilities for use in crafting timely protections.
Instead, information about newly discovered Windows XP vulnerabilities will originate from non-authoritative third-party sources, will likely not be disclosed via well-monitored communication channels, and may be incomplete or inaccurate. Organizations that continue using Windows XP beyond the April 8, 2014 end of support will be relying on incomplete, non-authoritative, third-party information to make informed decisions about the use and effectiveness of compensating controls around Windows XP systems.
The CTU research team does not consider compensating controls to be an effective security approach and highly recommends that organizations migrate to a supported operating system well in advance of the April 8, 2014 end-of-support date.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
