History of the PPI Business
The Pay-Per-Install business model (PPI) has existed for years. When the PPI business first started, it was used to distribute advertisements. Today it is mainly used to spread spyware and malware. PPI starts with an “affiliate” interested in building a network of infected computers or earning money. The affiliate signs up to a PPI site and receives a file from the PPI provider. The PPI-provided files were originally a variant of adware program. The affiliate “binds” the PPI-provided file with another program that they might host on their site. A binder is a program that can combine the adware provided by the PPI site with a known program. Whoever downloads the program gets the adware installed on their computer. The affiliate is paid per install of that adware that the PPI site sent them.
PPI Evolves From Pushing Adware to Spyware and Malware
The PPI business has seen significant and malicious changes over the years. It has gone from having victims unknowingly download and install adware to having them download and install spyware and malware. While some PPI sites are still distributing adware, the majority push malware and spyware to unsuspecting users. These PPI sites create an underground economy that profits from installing malware. This economy is so widespread that there is even a side business selling programs to make it more difficult for computer users to detect that they are installing something malicious.
We will first look at www.pay-per-install.org. This site hosts a forum where affiliates come together to discuss the PPI business and how to make money. This site is used for a variety of reasons:
- Lists affiliate programs organized in a way that affiliates can get an idea which PPI business is paying the most and paying reliably for installs.
- Provides a forum for affiliates to discuss how to make money the fastest and how to advertise their links to get victims to download their installs.
- Tutorials and guides to get affiliates started in the PPI business.
Methods and Tools
Many affiliates of the different PPI sites have various methods and tools they use to maximize the effectiveness of their malware-packed download. One suggested method is the use of peer-to-peer (P2P) networks. Affiliates recommend using BitTorrent or eMule, two of the most popular P2P networks. Once the affiliate signs up with the PPI site and receives the malicious file, the affiliate must choose a file to “bind” to the malicious file. Most affiliates access BitTorrent and download a legitimate program or game crack, bind the malicious file with the legitimate program that they downloaded, upload the bundled file to the torrent sites and advertise that file as the original non-modified file. The goal is to have computer users download the malicious bundled file and execute it, thinking that they are actually installing a useful program and not malware. The affiliate gets paid after the file is installed on the victim’s computer.
Seedboxes
One challenge affiliates encounter is that they must perform hundreds to thousands of installs to receive any significant income, which is why sites like www.pay-per-install.org exist to provide guidance. To address this challenge, many affiliates use a seedbox, or a private dedicated server used for the uploading and downloading of digital files. Affiliates use a seedbox to rapidly spread their malware-infected files using BitTorrent and eMule, avoiding the need to host the files on their computer. This can be a labor intensive process because once a P2P site discovers the malware in the uploaded affiliate file, that file is deleted or gets banned from the P2P network. Many affiliates take precautions to avoid this scenario by using special tools such as crypters to hide their files.
Crypters
One type of program that www.pay-per-install.org sells is called a crypter. Crypters are programs that hide malicious files from anti-virus (AV) solutions intended to protect your computer. Crypters are used to make a malicious file fully undetectable (FUD). Making files FUD is a money-making business in the world of malware. For example, the crypter on www.pay-per-install.org is called PXCrypter and is currently on version 1.1. Affiliates usually receive free upgrades when the author updates the crypter. This crypter sells for $75 and includes 1 stub; additional stubs are $25. The stub is the code that decrypts the rest of the program when it is executed. Because the stub must be available to perform the decryption, it can't be encrypted and is eventually identified by AV programs as malicious. To avoid this situation from occurring, crypters are sold with several stubs, with more available for an additional price.
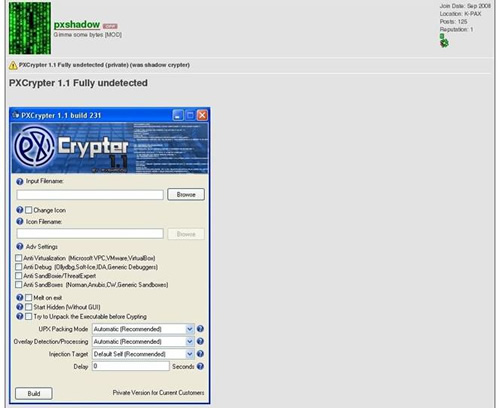
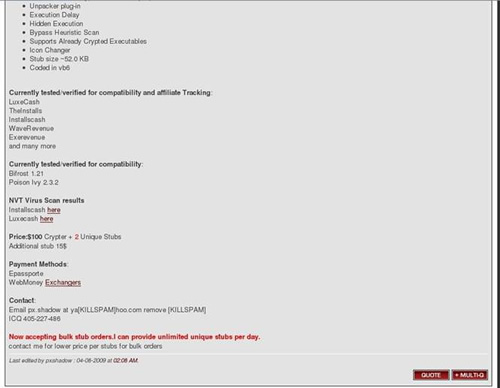
PXCrypter has been written to work with many PPI affiliate files, has many features to avoid detection by AV software and prevents a malicious file from running in a sandbox. Sandboxes are often used by security researchers to create a virtual environment where malicious programs can run and be observed without causing damage to the computer or its operating system. Sandboxing is a good way to determine malware behavior and design effective protection techniques and countermeasures.
Trojan Download Manager
Another type of tool used by affiliates is a Trojan Download Manager. A Trojan Download Manager is commonly seen in the blackhat malware communities because it allows an attacker to update any malware that has been downloaded by a victim’s computer, install additional malware, and perform any other functions that the Trojan Downloader Manager software author has designed.
The www.pay-per-install.org site has a Trojan Downloader Manager program for sale called SDdownloader or Silent Downloader. SDdownloader normally sells for $300; however, it is currently on special for $225. It is at version 3 and includes:
- One unique stub to decrypt the malware and minimize its visibility to antivirus software
- Binder software to combine the malware file with another file sought by a victim
- A web interface to track statistics for infected computers
- An interface to make the infected PC a SOCKS proxy, allowing an attacker to funnel malicious network traffic through the infected computer
- Tools to download more malware to the already infected computer
Trojan Download Managers are popular because they not only allow attackers to infect the computer, but they can also force the computer to download and install any PPI files or malware at the attacker’s command.
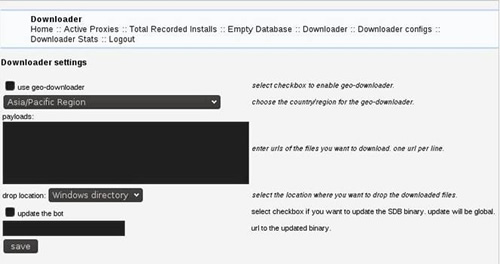
Log-in Page and Downloader Settings for SDdownloader:
Stats for SDdownloader-Infected Machines:
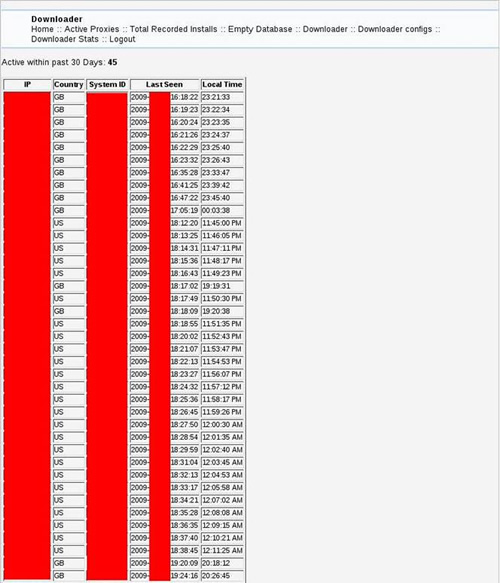
Since the initial CTU writeup of SDdownloader in June 2009, the author of this program has joined forces with another programmer to offer multiple products through their company. The products they offer include software that can pop up advertisements on infected computers, manage infected computers similar to the features in SDdownloader, a Gmail account harvester, a binder, and a low-tech version of SDdownloader. They refer to themselves as internet marketing tool developers.
Black Hat Search Engine Optimization (SEO)
A scammer who doesn't want to use P2P but wants traffic directed to their site that hosts malicious files can use black hat SEO techniques. Black hat SEO increases the volume of traffic to a web site by manipulating search engines. The user clicks the link in response to their search query and the victim’s computer visits the site, where exploits hijack vulnerable computers using a technique known as drive-by downloads. After the site compromises the victim’s computer, an attacker can successfully transfer and install as much malware as they want.
Attackers use tools such as XRumer to perform these tasks. XRumer is an auto-submitter program that posts messages to forums, guestbooks, bulletin boards and catalogs. An auto-submitter’s purpose is to announce the attacker’s site URL throughout the Internet to increase search engine rankings and display the site at or near the top of search engine results. This software also helps advertise the attacker’s site URL so more people might be willing to click on it in a guestbook or forum posting.
Doorway Pages
Another method used by attackers to increase traffic so more victims will visit their site and download malicious files is the use of a doorway or doorway pages. Doorway pages are similar to SEO, but the goal is to increase the search ranking of the doorway page instead of the attacker’s site. The doorway is simply a web page that may list many keywords in an attempt to increase the search engine ranking. This doorway page will not contain any malicious files to download, so it will not be removed from search engines or blacklisted. Instead, the doorway page contains scripts that redirect the victim’s computer to the attacker’s malicious or scamming adware page, where malware or adware may be downloaded to vulnerable computers.
The PPI sites
Pay-per-install.org references a number of PPI sites that offer to pay affiliates to install programs on victims’ computers. Most affiliates judge PPI sites by two main criteria: how much they pay and how honest they are. In PPI jargon, ‘shaving’ is the act of not counting some installations by affiliates. Some PPI sites are accused of shaving a portion of installations from the affiliates’ total. Most affiliates want to sign up to a PPI site that has a good reputation and pays on time. Affiliates can work with many different PPI sites simultaneously to maximize their income.InstallsCash
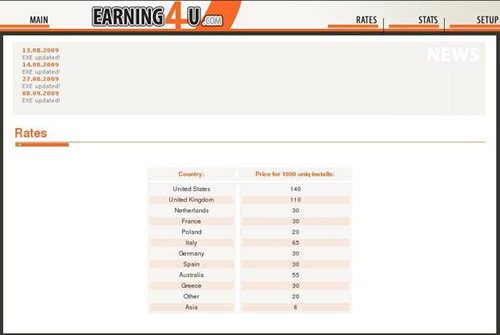
The first PPI site CTU investigated was called InstallsCash, which seems to have changed its name to Earning4u. When it was doing business as InstallsCash, this site claimed to count affiliate installations in realtime and claimed that it was not shaving its affiliate's install counts. InstallsCash only pays in increments of 1000 installs. Payments are $140 for U.S. computers, $110 for the U.K., $60 for Italy, $30 for France, and $6 for any computer in Asia (per thousand installs). Affiliates can be paid via Fethard, Webmoney, Wire, Western Union, MoneyGram, Anelik, and EPassporte. The site claims that running the InstallsCash file on a victim’s computer installs a toolbar and a dialer. A dialer enables the victim’s computer to automatically ‘phone home’ or go to a specified web site. InstallsCash claims that the dialer launches 15 to 30 minutes after the initial execution.


The file that InstallsCash pays affiliates to install on victims’ computers is the Piptea Downloader Trojan. As of May 2009, 16 out of 40 antivirus software products detect Piptea, according to Virustotal, a malware analysis website (http://www.virustotal.com/analisis/7cb2cf1ad9ed861273572f037d95c293).
Piptea — A Downloader Trojan
Downloader Trojans are used to download and install other pieces of malware. The downloader uses the Internet to contact a control server and request a file to download, usually via HTTP to avoid detection. The initial contact allows the control server to record the IP address, operating system (OS), language and other information by interrogating the infected computer’s web browser. Using this information, the control server is able to send customized malware to the victim’s computer based on OS version, language and country of origin. When CTU investigated Piptea, it ‘phoned home’ (that is, it contacted) a server in Russia at 195.2.XXX.XXX to download additional malware, which was subsequently identified by AV vendors as Virut. The infected computer will then start communicating with another Russian server at nxxx.tv (91.212.XXX.XXX) to perform two different ‘phone home’ types of traffic. Browsing the http://nxxx.tv/gda website displays a login to what is probably the C&C (Command and Control) server used by a ‘botmaster’ to manage the infected computers.
The infected computer will download another piece of malware detected as Koobface from 195.2.xxx.xxx. The infected computer performs another phone home operation to wnxxx.com/achcheck.php, downloading browser helper object (BHO) malware from a server in China at 218.93.xxx.xxx. The infected computer phones home once again to a Chinese server at 221.12.xxx.xxx so that the botmaster can now communicate with the malware (also called a ‘bot’) using a custom encrypted protocol.
When CTU downloaded and installed a new version of the InstallsCash file weeks after the initial investigation in June 2009, the list of downloaded malware had changed. Piptea was still the first infection, followed by TDSS and Rustock. The Rustock Trojan sends spam and phoned home to a server in the United States. Piptea also downloaded approximately 10 additional malware and spyware programs. The InstallsCash file download sequence seems to change based on who they are currently doing business with, which could mean InstallsCash is paid by one or more business partners. The screenshots illustrate how many computers are infected on a weekly basis from just one affiliate.
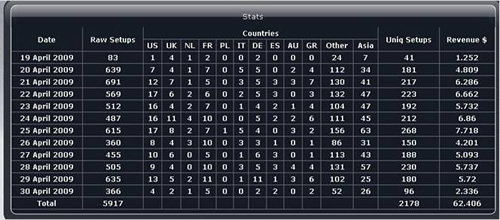
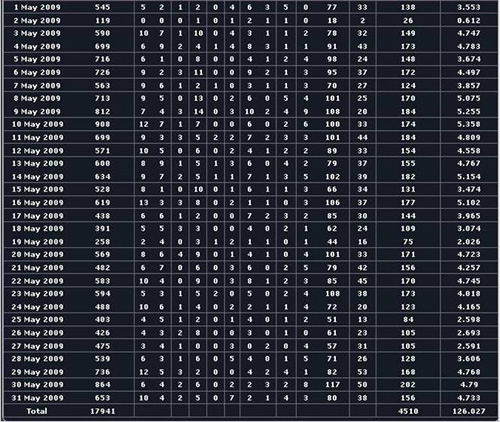
Affiliate-reported installs from InstallsCash. (Source: Pay-Per-Install.org)
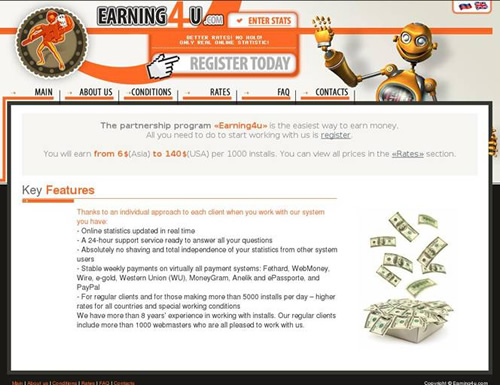
Earning4u.com (formerly InstallsCash)
The Earning4u.com site is relatively new and reportedly is a continuation of InstallsCash. InstallsCash ceased operations around the same time this site became active. Earning4u.com has the same pricing as InstallsCash, basing their affiliate compensation on per-1000 installations. Screen shots of the actual site shows a pricing breakdown similar to that of InstallsCash, which shows that some things have not changed. The site’s look and feel is different, but it has the same Russian and English language options as InstallsCash. The site has a Russian IP address and is registered to a software company in China.
The site claims to have been in business since 2001, allegedly employs a team of 20 professionals, and claims to have over 1000 registered affiliates. The site processes payments using the same payment systems as InstallsCash in addition to e-gold and PayPal. One item of interest is that they refuse to pay for installations on Russian or any CIS-based (Commonwealth of Independent States, or former Soviet Republic) computers.
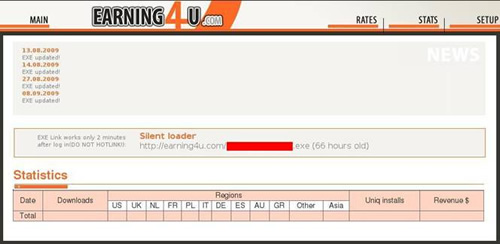
Just like InstallsCash, the “silent loader” software that can be downloaded and distributed by the affiliate will download and install a nasty malware combination. The initial executable file is the Iframecash Trojan downloader, a well-known malware product that’s been available for years. However, the PPI site owners repack this malware to avoid detection for as long as possible. The CTU observed that this Trojan downloader approached a 50% detection rate only 66 hours after its initial availability. The rapid detection rate underscores why most affiliates prefer to use crypters to avoid or delay detection.
Earning4u.com makes the same claims for the installer as the InstallsCash installer. They claim that it is not harmful and only changes the web browser’s homepage, as well as setting up a dialer to contact web sites. After the victim’s computer executes the Iframecash downloader, the program phones home to http://ae4xxx.com located in the United States. This server is registered to the same Chinese software company as Earning4u.com.
The phone home traffic to http://ae4xxx.com consists of HTTP GET requests to download multiple pieces of malware, as well as phone home traffic that lets the malware check in with the C&C server. The other malware downloaded by Iframecash consists of Rustock, Vundo, Zeus Banking Trojan, Piptea, and Rogue AV.
Ya!Bucks
The third site investigated by the CTU is called Ya!Bucks. This site is different in that it doesn't just pay for installs, but it also helps affiliates find ways to get victims to install the files. The site claims they offer 75% revenue share, software lifetime payout, bi-weekly payments, undetectable software, and 10% commission bonus on referrals. This site also has a chat window on every page so that affiliates can chat with other affiliates that use the site and ask questions.

One way Ya!Bucks offers to help affiliates spread malware is by offering a number of website links to which affiliates can direct traffic. These website links lead to pages with clever ways to trick victims into downloading malware. One such site advertises software called AdwareHelp 2009, which advertises a fraudulent antivirus solution.
Another website link attracts victims by offering pirated games for download. This website includes keywords for better SEO, so that victims might discover it from search engine results. Of course, any files downloaded from these websites will be malicious in nature.
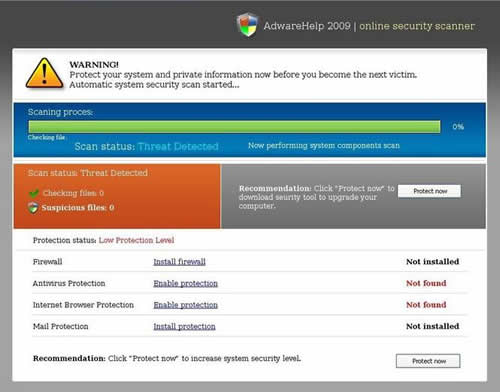
The CTU’s investigation of Ya!Bucks found that their executable file was downloaded from a China-based server at http://inxxx.cn/stubfiles/ (210.51.xxx.xxx). Most of Ya!Bucks's website is written in English and Russian. The site even mentions providing exploit code to affiliates who generate a good amount of traffic to their site. In May 2009, the file that Ya!Bucks provided to affiliates for installation on victims’ computers had a detection rate of 6/40 and is detected as Dontovo or MSAntispyware 2009 (http://www.virustotal.com/analisis/4594f1a534d8316540daab9f9717ec398831a2847cdceea16423269540349975-1243368986).
TrafCash
The fourth site the CTU investigated is called TrafCash. This site pays 6 cents per U.S. install and 5 cents per U.K. install. The server hosting this site is in Germany and is registered using privacy protection so that the site owner is not exposed. The site claims: “We install PPC advertisement module and antivirus module. You can install both of them, or only one of them. Contact support to get the antivirus module.”

TrafCash directs affiliates to http://malxxx.com/install/ to receive the installation file for victims’ computers. This web page lists approximately 500 available installation files for everyone registered to the site.
The file that TrafCash sends affiliates for installs had a detection rate of 7/39 in May 2009 and is detected as Trojan downloader Cbeplay, even though the CTU observed that the file does not exhibit the same behaviors as Cbeplay. (http://www.virustotal.com/analisis/893e44d75c13803cd4acc2d6878825fbe487448ea15e239b4b593ce2a83b7f69-1243370884).
The Cbeplay Trojan performs many actions, such as starting a program named Avast!Antivirus that masquerades as legitimate Antivirus software. Cbeplay then phones home and embeds the TrafCash affiliate ID in the phone home packet.
POST /stat.php
os=2600&ver=0.0.0.162&idx=aad5f0c0-7d77-11dc-b3a9-806d6172696f&user=XXX&ioctl=20&data=3c8b978ebdf779f52de6f22cae18270d-2.cdd7a26b823b214edac34dd1bb04dd68-2
The infected computer attempts to download the Malware Doctor and Ambler.D malware from 66.199.xxx.xxx. Malware Doctor is a bogus antivirus program that has a detection rate of 15/39 (http://www.virustotal.com/analisis/e95a0dfdf8458df7b2d4549c3cf6a51d78d454b904058a826e62656a9e380239-1243461741).
Ambler.D is the second downloaded malware product and has a detection rate of 21/40. Ambler.D attempts to phone home to malxxx.info, which has the same IP address as http://malxxx.com (http://www.virustotal.com/analisis/11c47b28065684b7dfe2c9f9652bdf76e4a8080d2d891b74a5e0db18517ec9ed-1243462477).
Conclusion
To protect your computer and your company from these types of threats, your organization needs to have strong Information Technology (IT) policies and user education in place. IT policies should not allow any kind of peer-to-peer (P2P) usage because file sharing can easily lead to the downloading of malicious files. Users should also be prohibited from installing pirated or unlicensed software, as this software often contains malware.
Use caution when using search engines to find software downloads. Only download software from reputable sites, as SEO techniques are often used to display malicious download sites in search engine rankings.
Depending on your organization’s security and business needs, consider preventing end users from installing any programs on their work computer. Users should be educated on the reasons for these policies, as well as common scams used to con them into running Trojan programs (such as tempting movies, fake codecs, fake AV programs, and spam-based Trojans).
Because many of these PPI programs install the Zeus Trojan and other similar financial and credential-stealing Trojans on victims’ computers, CTU recommends that businesses handling online banking and financial transactions adopt a strategy to isolate the workstations, used for these activities, from possible Zeus or other data-stealing Trojan infections. Operating system and antivirus software should be updated frequently. The PPI business threat is rapidly growing and attackers use more tools and methods to trick computer users into downloading malware that can result in millions of computers being compromised.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
