- Author: Dell SecureWorks Counter Threat Unit(TM) Threat Intelligence
- Date: 30 May 2013
Background
Point-of-sale (POS) systems are critical components in any retail environment. Having evolved beyond simple cash registers, a modern POS system is tied to a business's payment processing, inventory, and customer relationship management (CRM) functions. Innovations in POS software development have also made it easier for small and mid-sized businesses to deploy feature-rich POS tools in their retail environments. To support these increased requirements, POS system developers are using common development environments such as Microsoft Windows. There are estimates that as many as 76% of POS systems are running some version of Microsoft Windows.
POS systems have also been a popular target for criminals due to their role in processing financial transactions. Small businesses that do not have dedicated information security resources to help secure their retail environments are at increased risk. These businesses may lack robust protection mechanisms to ensure the security of their POS devices. In addition, small businesses typically have limited resources and rely on the computers hosting the POS system to provide other functions, including email and web browsing. Businesses that handle payment card data have to conform to Payment Card Industry (PCI) regulations to ensure the security of card holder data. However, the obligation to safeguard customer data extends beyond regulatory compliance, as merchants responsible for card data theft can be subject to fines, culpability for financial losses, loss of customer confidence, and negative impact to their brand.
Reasons
Dell SecureWorks Counter Threat Unit(TM) (CTU) researchers cite multiple factors that have contributed to the rise in interest in malware used to target POS systems.
Increased POS vendor diversity
POS systems have become readily available to small and mid-sized businesses to deploy without relying on a third-party integrator or value-added reseller (VAR) that specializes in implementing POS solutions for retail environments. This accessibility provides an increased landscape of POS devices using commercially available operating systems such as Microsoft Windows, which are already viable platforms for malware. In addition, these POS devices may be set up in insecure environments that are not PCI compliant or are at increased risk even if compliance is met.
Increased demand for prepaid cards
Credit cards have historically been popular targets for criminals. In particular, cards that rely on static authentication and do not use the Europay, MasterCard, and Visa (EMV) standard for authenticating transactions have been prized for their ability to be counterfeited. Criminals then use these cards to purchase goods online or to withdraw cash from ATM systems.
A prepaid debit card functions just like a normal debit card but is loaded with cash instead of being tied to a bank account. Prepaid debit cards can be either non-reloadable or reloadable. A non-reloadable card has a defined value (e.g., $50) that is activated at purchase. Once the funds are depleted, the card is no longer useful. A reloadable prepaid card can continue to have funds added to it. Most reloadable prepaid cards can be funded via direct deposit and can have cash withdrawn from ATMs.
CTU researchers have observed an increased focus in online banking fraud and account takeover targeting high-value bank accounts belonging to businesses, non-profit organizations, and local governments. Criminals use malware such as Gameover Zeus, Bugat, and Citadel to take over the accounts and then send money out of the account through payments via the Automated Clearing House (ACH) network or through wire transfers to other bank accounts. Because reloadable prepaid cards can be funded with direct deposits, the criminals can send money from a victimized account to fund numerous counterfeited prepaid cards. These cards can then be converted to cash via ATM withdrawal or the purchase of gift cards, goods, and services. This process provides criminals with more options for cashing out a victimized account.
Criminal market demand
The criminal underground operates very much like a legitimate economy. There are demands for goods and services that allow opportunities for vendors to provide products to meet that demand. The increased demand for stolen prepaid credit cards has likely contributed to the increased demand for malware targeting POS systems.
Malware
Much of the current wave of malware targeting POS systems uses the same basic stealing components that criminals have used in the past. The malware attempts to steal the Track 1 or Track 2 formatted data that is stored on a credit card's magnetic stripe. Criminals can then re-encode the track data onto counterfeit cards. Malware that targets track data leverages the need for this data to be stored in the memory of a running program in a decrypted state for transaction authorization to occur.
Dexter
The Dexter Trojan horse was disclosed publicly by Seculert in December 2012. Dexter attempts to scan the memory of other processes looking for Track 1 or Track 2 formatted data. Dexter uses HTTP to communicate with a command and control (C2) server to exfiltrate stolen card data and to receive updates. Dexter includes an administration panel for browsing infected computers, similar to the control panels found with banking trojans (see Figure 1).
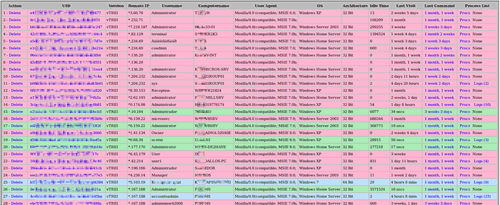
Figure 1. Dexter trojan admin panel. (Source: Seculert)
Dell SecureWorks has not observed any events triggering countermeasures for the Dexter trojan within its customer base.
vSkimmer
vSkimmer was disclosed by McAfee in March 2013. In addition to information about the malware, McAfee included details from a message on a web forum used by criminals to advertise goods and services. vSkimmer also searches program memory for track data; however, it only looks for data matching Track 2 format. Figure 2 shows the regular expression used to search for Track 2 formatted data.

Figure 2. vSkimmer regular expression for matching Track 2 formatted data. (Source: Dell SecureWorks)
In addition to using HTTP to exfiltrate stolen data to a C2 server, vSkimmer can be configured to copy data to a specific USB device if it is unable to connect to the Internet. vSkimmer dumps its stolen data to a log file on a USB drive with a certain volume name. Based on a version of the vSkimmer builder tool obtained by the CTU research team, the volume name and name of the log file can be configured by the tool used to configure and build customized versions of the malware. This option provides the attacker with an alternate mechanism for offloading stolen data from a POS device that is not allowed to communicate directly to the Internet.

Figure 3. vSkimmer trojan builder. (Source: Dell SecureWorks)
Dell SecureWorks has not observed any events triggering countermeasures for the vSkimmer trojan within its customer base.
BlackPOS
BlackPOS, which is allegedly sold under the name "Dump Memory Grabber by Ree," was disclosed publicly by the Russian-based security firm Group-IB in late March 2013. The tool was being advertised on a popular web forum for cybercriminal goods and services. BlackPOS scans the memory of running processes for stored Track 1 and Track 2 formatted data. If found, data is stored in an output file called output.txt and is uploaded to a server using FTP.
Dell SecureWorks has not observed any events triggering countermeasures for the BlackPOS trojan within its customer base.
Alina
The Alina trojan was discovered by the CTU research team in March 2013. As with the previous three POS-targeting malware, Alina searches running processes for credit card track data.
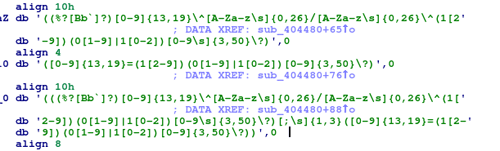
Figure 4. Alina trojan regular expressions for Track 1 and Track 2 data. (Source: Dell SecureWorks)
Alina uses HTTP to upload information about the infected computer and stolen card data to its C2 server. Alina can also download and run updates.
Shortly after its discovery, the CTU research team implemented countermeasures to detect Alina trojan activity. Infections were detected in three customer networks over a one week period. No activity has been detected since March 2013.
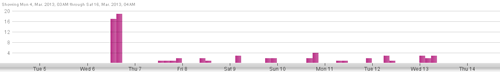
Figure 5. Alina trojan IDS activity. (Source: Dell SecureWorks)
Citadel
The Citadel trojan is a well-known crimeware kit that is used to target online banking and credit card data for the purpose of committing fraud. In addition to its ability to spy on a user's web browsing activity, Citadel has several other features that make it valuable to an attacker for identifying and compromising potential POS devices.
System reconnaissance
Citadel can be configured to run certain commands specified in a configuration file each time it starts. As shown in Figure 6, Citadel can be configured to gather information about the infected host and the network.
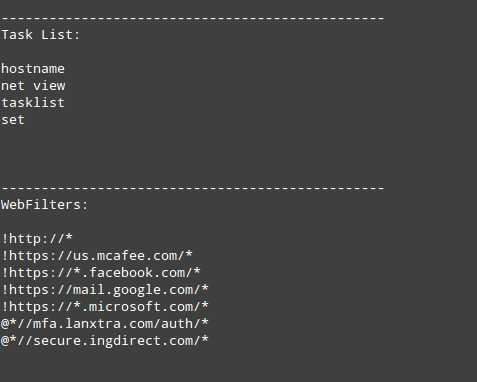
Figure 6. Sample Citadel task list. (Source: Dell SecureWorks)
Software reconnaissance
The Citadel trojan can also collect information about software installed on the infected computer. A botnet operator can use this information to gather information about the purpose of the infected computer and possibly information about other computers on the network.
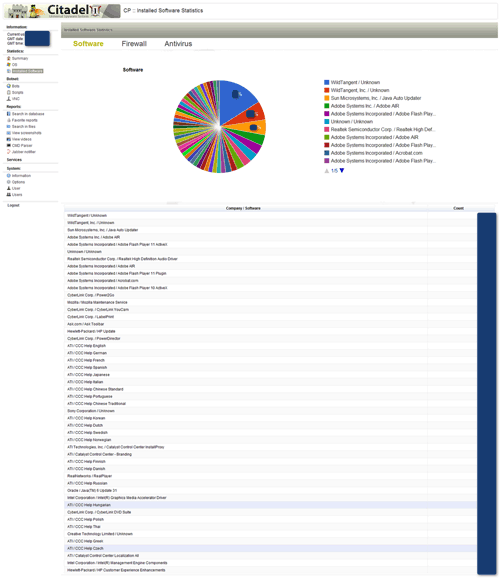
Figure 7. Citadel installed software statistics. (Source: Malware Don't Need Coffee)
Download and execute programs
Citadel allows a botnet operator to send a command to infected computers to download a program from a URL and run it on an infected computer. This instruction is referred to as a "user_execute" command. It can be sent to the entire botnet, to a single infected computer, or only to computers located within a specific country.
Keystroke logging
Citadel can be configured to log all keystrokes entered within targeted processes for a specified time period. This action can provide an attacker with sensitive information such as account credentials for POS software users and account data that is manually entered.
Screenshots and video capture
Citadel can be configured to take screenshots when a user navigates to a specific URL or even to record video of the user's actions. This ability allows attackers to collect intelligence on how a web application works. The attackers can then use this intelligence to craft their attack tools to leverage that specific platform.
Citadel campaigns
The CTU research team is aware of two Citadel botnets that have been specifically targeting POS devices.
e-trust botnet
The CTU research team refers to this Citadel botnet as the "e-trust" botnet due to its use of the "e-trust" string in several C2 domain names. In addition, the string "pos" has also been used several times in domain names.
Figure 8 shows a portion of the configuration data that was stored in a Citadel sample. This configuration data includes URLs for the sample to request additional configuration data and a botnet name that is specified by the botnet controller. The botnet name is used for attackers who want to set up multiple botnet partitions under a single C2 infrastructure. Multiple partitions are often used when criminal groups with multiple affiliates are using the same infrastructure, or when a single group that operates multiple campaigns is targeting different types of information or geographic regions.
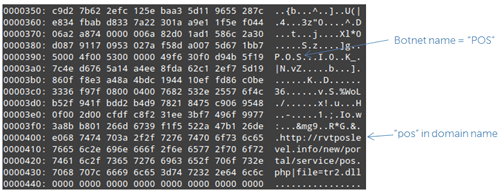
Figure 8. e-trust Citadel sample configuration data. (Source: Dell SecureWorks)
The e-trust botnet is believed to use multiple mechanisms to target track data on POS devices:
- Target web-based virtual POS applications that submit raw track data in HTTP transactions. Even if these web transactions are performed between internal systems, Citadel can intercept the data.
- Use the user_execute feature to install specialized memory parsing malware.
Keylogger botnet
CTU researchers have observed a second Citadel botnet targeting POS devices. This botnet uses Citadel's keystroke logging capability to target processes that are associated with POS software and remote access and administration tools. CTU researchers suspect the Citadel Keylogger botnet has targeted the following applications:
- *store*
- *pos*
- *term*
- *sales*
- *morris*
- *merchant*
- *mira*
- *gotomy*
- *pcany*
- *aloha*
- *backoffice*
- *moneris*
- *logmein*
- *g2view*
- *shop*
- *restaurant*
- *bar*
- *coffee*
- *caffe*
- *cafe*
- *backoffice*
Because track data cannot be intercepted via keystroke logging, the attackers may be trying to obtain user credentials to the POS software or credit card numbers that have been manually entered. The latter scenario possibly targets businesses that process credit card payments over the phone. In addition, this botnet has been configured to monitor for traffic belonging to a web-based virtual POS application run by Moneris. In this instance, the attacker may be trying to acquire merchant credentials for the system and card data. An attacker could use this information to create false transactions with the compromised credentials and then later initiate a refund to a counterfeit card.
Citadel / Alina connection
The CTU research team uses its Threat Intelligence Management System (TIMS) to correlate activity across multiple data sets, including customer telemetry and threat data from malware analysis systems. After discovering the Alina trojan, CTU researchers searched their malware repository to locate older versions of the malware and process them through CTU analysis systems to extract indicator data. Analysis of these older samples revealed an IP address (84.22.106.94) that was used by Alina for C2. This same IP address had also triggered IDS countermeasures that were consistent with Zeus or Citadel activity among Dell SecureWorks customers. Furthermore, this IP address was linked to specific domain names known to have been used by earlier instances of the Citadel Keylogger botnet. This connection indicates that the attackers behind the Keylogger botnet were possibly using Citadel to distribute the Alina trojan to systems to steal track data.
Recommendations
Organizations processing card transactions are required to meet the security requirements specified by the Payment Card Industry Data Security Standards (PCI DSS) to protect card data at the point of sale. These standards provide a solid framework for merchants to protect cardholder data. Compliance to the standards represents an organization's security posture at a specific point in time. Unfortunately, security controls occasionally fail. The following recommendations, executed as part of an overall PCI compliance strategy, will help limit the vulnerability of POS devices to malware and mitigate data loss from any successful infections.
Implement network egress policies
In PCI DSS v2.0, Requirement 1 states, "Install and maintain a firewall configuration to protect cardholder data." This requirement defines the standard of having a segmented network where payment systems live in networks with tighter access controls. In particular, POS devices that use IP-based networks for communications should have network controls that prevent them from communicating with untrusted networks. Communications to all hosts should be denied by default unless otherwise required for business purposes. This setting will help prevent malware that may get installed on a POS device from using network protocols to exfiltrate stolen card data. However, this setting will not stop attacks where data exfiltration is performed through physical means or via the network through other approved systems.
Use network intrusion detection
According to Requirement 11 of PCI DSS v2.0, "Regularly test security systems and processes." Network intrusion detection systems (IDS) can identify suspicious traffic that may indicate compromise of POS devices or systems that process card data. These signatures may look for network traffic specific to certain malware families, or they may look for patterns of data that may indicate data theft, such as a credit card number or raw track data.
Apply application whitelisting
Application whitelisting is the process of establishing policy and controls to allow only a certain set of approved applications to run on a computer. Applications can be restricted through capabilities provided by the operating system. Examples for Microsoft Windows include AppLocker for Windows 7 and Windows Server 2008 R2 and Software Restriction Policies for older versions of Windows. Application whitelisting can also be accomplished with specialized third-party tools. Application whitelisting implementations have a reputation of being difficult to maintain in standard corporate environments due to the large numbers of applications and updates that need to be supported. However, POS devices are ideal platforms for application whitelisting, as they are special-purpose computing devices that only need to run a small set of applications.
Application whitelisting is not specifically mentioned in the PCI DSS 2.0 specification. However, Requirement 5 specifies to "Use and regularly update anti-virus software or programs." Application whitelisting solutions may be an option for primary or compensating controls to satisfy this requirement.
Restrict use of POS devices
Because many POS devices run versions of the Windows operating system, these devices could turn into multi-use devices. In particular, resource-cramped small businesses may have a POS device that is also used to read email and surf the web. These additional activities place the computer at greater risk of malware infection. Retail environments should ensure that POS devices cannot browse the Internet. Small business should invest in a dedicated computer or tablet to provide web browsing and email capabilities.
Use point-to-point encryption devices
Point-to-point encryption (P2PE) solutions provide the capability to accept payments on a device that encrypts the data on the device (e.g., card swipe terminal) for transmission to a third-party for processing. The card authentication data never resides on the POS device, so it cannot be stolen. From a retail perspective, this configuration shifts many of the security requirements to protect customer card data to the third-party processor. However, merchants are still accountable for PCI DSS compliance, as they need to physically handle payment cards and ensure the integrity of the physical P2PE devices. This type of solution can be attractive to smaller merchants with few storefronts and cashiers.
Investigate next-generation payment technologies
Popular in Europe, next-generation payment technologies such as EMV standards-based payment cards (also known as Chip and PIN) and Near Field Communications (NFC)-based payment devices are beginning to emerge in the United States. These technologies reduce the need for static authentication data, such as track data, for transaction authorization. It is much more difficult for criminals to counterfeit legitimate payment cards for fraud purposes. Technologies like Chip and PIN do not eliminate the possibility of fraud, but they reduce the risk faced by merchants.
Review for threat indicators
Organizations should search their environments for the threat indicators in Table 1. These threat indicators may indicate the presence of malware targeting POS devices.
| Indicator | Type | Context |
|---|---|---|
| d72bce2ccd44eb96f3e76a420ea5c246 | MD5 file hash | Citadel executable |
| b12d775df2c6af43180bc115b57efe0d | MD5 file hash | Citadel executable |
| b9f4294601adbb613ab089e536ad04f6 | MD5 file hash | Citadel executable |
| ea8cbc2b839cea72bae436313291d42c | MD5 file hash | Citadel executable |
| c8e5728b05c3ac46212c33535b65f183 | MD5 file hash | Citadel executable |
| 82ec7b37a138d99cd68d9dcf64a29117 | MD5 file hash | Citadel executable |
| ea8cbc2b839cea72bae436313291d42c | MD5 file hash | Citadel executable |
| 88d7eddf873383f7d2d5b9ecb5a74187 | MD5 file hash | Citadel executable |
| ultimaresources . com | Domain name | Citadel C2 server |
| ultimaresource . com | Domain name | Citadel C2 server |
| e-trustwildlevel . com | Domain name | Citadel C2 server |
| wildresource . info | Domain name | Citadel C2 server |
| newposlevel . us | Domain name | Citadel C2 server |
| e-trustposlevel . us | Domain name | Citadel C2 server |
| trustposlevel . com | Domain name | Citadel C2 server |
| white-teeth2012 . org | Domain name | Citadel C2 server |
| airtravelers . org | Domain name | Citadel C2 server |
| lovelypictures . org | Domain name | Citadel C2 server |
| sport-models . org | Domain name | Citadel C2 server |
| hotels2013 . org | Domain name | Citadel C2 server |
| printing-offices . com | Domain name | Citadel C2 server |
| voip-offices . in . ua | Domain name | Citadel C2 server |
| real-life2013 . in . ua | Domain name | Citadel C2 server |
| computershop2013 . org | Domain name | Citadel C2 server |
| paristours2013 . org | Domain name | Citadel C2 server |
| yamaha-motor2013 . com | Domain name | Citadel C2 server |
| reallife-stories . com | Domain name | Citadel C2 server |
| real-life-tips . com | Domain name | Citadel C2 server |
| 213.57.77.220 | IP address | Citadel C2 server |
| 91.243.115.83 | IP address | Citadel C2 server |
| 91.243.115.86 | IP address | Citadel C2 server |
| 166.78.144.80 | IP address | Citadel C2 server |
| 46.165.200.115 | IP address | Citadel C2 server |
| 62.109.25.228 | IP address | Citadel C2 server |
| 64.13.192.163 | IP address | Citadel C2 server |
| 68.68.28.103 | IP address | Citadel C2 server |
| 85.17.122.230 | IP address | Citadel C2 server |
| 2fd2073dcc197e0b5da425d663a6c5cd | MD5 file hash | Alina executable |
| 8b82d07d41bec878fb10f7ae616226f4 | MD5 file hash | Alina executable |
| 99a307128daa407147d1c69d2824d703 | MD5 file hash | Alina executable |
| 37493eb319d126d0ab8f5a55da85563d | MD5 file hash | Alina executable |
| 1efeb85c8ec2c07dc0517ccca7e8d743 | MD5 file hash | Alina executable |
| 2c2cfa4a685bb56a1cbb5979f13e6ab2 | MD5 file hash | Alina executable |
| 2139e613dc20df19daa6d90a0ff05591 | MD5 file hash | Alina executable |
| 0de9765c9c40c2c2f372bf92e0ce7b68 | MD5 file hash | Alina executable |
| 8e9e0a0fcd8df9da2980a260cd309a1e | MD5 file hash | Alina executable |
| 208.98.63.226 | IP address | Alina C2 server |
| 0ca4f93a848cf01348336a8c6ff22daf | MD5 file hash | BlackPOS executable |
| f45dcb05203909c6093f8dee0f223069 | MD5 file hash | BlackPOS executable |
| 05e9e87f102ea12bce0563f91783dc3 | MD5 file hash | BlackPOS executable |
| 109.234.159.254 | IP address | BlackPOS data exfiltration server |
| 31.170.164.227 | IP address | BlackPOS data exfiltration server |
| ftp . onelove . 16mb . com | Domain name | BlackPOS data exfiltration server |
| 03fe4ec93b5ea4f00ac693cbec92c0dc | MD5 file hash | vSkimmer executable |
| b93001b162f63902d0c42e2494dfcd25 | MD5 file hash | vSkimmer executable |
| 65577db601ca9be40ad91fc25fa08937 | MD5 file hash | vSkimmer executable |
| c42f45197ace43beed3e2d21faa4f3cc | MD5 file hash | vSkimmer executable |
| dae375687c520e06cb159887a37141bf | MD5 file hash | vSkimmer executable |
| www . posterminalworld . la | Domain name | vSkimmer C2 server |
| www . adssa-org . 1gb . ru | Domain name | vSkimmer C2 server |
| cepperofthelight . p .ht | Domain name | vSkimmer C2 server |
| www . mellat . info | Domain name | vSkimmer C2 server |
| btodata . net | Domain name | vSkimmer C2 server |
| 5.9.175.150 | IP address | vSkimmer C2 server |
| 81.177.174.13 | IP address | vSkimmer C2 server |
| 31.170.164.60 | IP address | vSkimmer C2 server |
| 31.31.196.44 | IP address | vSkimmer C2 server |
| 70feec581cd97454a74a0d7c1d3183d1 | MD5 file hash | Dexter executable |
| f84599376e35dbe1b33945b64e1ec6ab | MD5 file hash | Dexter executable |
| ed783ccea631bde958ac64185ca6e6b6 | MD5 file hash | Dexter executable |
| 2d48e927cdf97413523e315ed00c90ab | MD5 file hash | Dexter executable |
| 11e2540739d7fbea1ab8f9aa7a107648 . com | Domain name | Dexter C2 server |
| 67b3dba8bc6778101892eb77249db32e . com | Domain name | Dexter C2 server |
| 7186343a80c6fa32811804d23765cda4 . com | Domain name | Dexter C2 server |
| 815ad1c058df1b7ba9c0998e2aa8a7b4 . com | Domain name | Dexter C2 server |
| e7bc2d0fceee1bdfd691a80c783173b4 . com | Domain name | Dexter C2 server |
| e7dce8e4671f8f03a040d08bb08ec07a . com | Domain name | Dexter C2 server |
| fabcaa97871555b68aa095335975e613 . com | Domain name | Dexter C2 server |
| 67b3dba8bc6778101892eb77249db32e . com | Domain name | Dexter C2 server |
| 173.255.196.136 | IP address | Dexter C2 server |
| 50.116.41.199 | IP address | Dexter C2 server |
| 193.107.19.165 | IP address | Dexter C2 server |
Table 1. Threat indicators for malware targeting POS devices.
Conclusion
Cybercrime continues to evolve in response to technical and legal actions. Criminals are now leveraging payment mechanisms such as prepaid cards to make their schemes more efficient. This approach also allows more criminals to use magnetic string based authentication systems to conduct tried-and-true attacks against POS systems. CTU researchers believe that POS devices will continue to be an attractive target, with criminals developing new malware and repurposing existing malware to steal card data. Organizations that process card data need to continue to monitor the threat landscape and adapt their controls to protect card data beyond PCI requirements.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
