- Author: Joe Stewart, Dell SecureWorks Counter Threat Unit™ Threat Intelligence
- Date: 23 July 2012
Summary
Since February 2011, members of the Dell SecureWorks Counter Threat Unit(TM) (CTU) have been engaged in a project to uncover and track as many elements as possible of the so-called "Advanced Persistent Threats" (APT), the term commonly used to refer to cyber-espionage activity carried out against governments, activists, and industry. "Elements" can be anything that provides a point of information — malware, command and control (C2) domains, hostnames, IP addresses, actors, exploits, targets, tools, tactics, and so on. Even though this project is not (and probably never will be) complete, CTU researchers have learned a great deal about the scope and scale of the threat so far, and the insights have been disturbing.
Learn more about what is an advanced persistent threat. Discover who these threat actors are and how they operate.
The scale of cyber-espionage
As a result of this project, the CTU research team is tracking numerous digital elements involved in cyber-espionage activity:
- More than 200 unique families of custom malware used in cyber-espionage campaigns
- More than 1,100 domain names registered by cyber-espionage actors for use in hosting malware C2s or spearphishing
- Nearly 20,000 subdomains of the 1,100 domains (plus a significant number of dynamic DNS domains) are used for malware C2 resolution
This quantity of elements rivals many large conventional cybercrime operations. However, unlike the largest cybercrime networks that can contain millions of infected computers in a single botnet, cyber-espionage encompasses tens of thousands of infected computers spread across hundreds of botnets, each of which may only control a few to a few hundred computers at a time. Therefore, each time an "APT botnet" is discovered, it tends to look like a fairly small-scale operation. But this illusion belies the fact that for every APT botnet that is discovered and publicized, hundreds more continue to lie undetected on thousands of networks.
There is a seeming disparity in the way different security researchers speak about the cyber-espionage problem. On one hand, many claim that APT is an over-hyped, unsophisticated threat. Yet at the same time, researchers who are on the other side of the issue declare it to be a state of national emergency, with the potential to bring down the economy of countries. The researchers in the former camp claim that APT warnings from the latter-mentioned researchers are self-serving and can be dismissed as FUD (fear, uncertainty and doubt) designed to line the pockets of companies whose bottom lines depend on promoting services targeting cyber-espionage threat.
It is challenging to truly convey the scope of the problem even when using illustrations. Figure 1 is a graph of connections between all known APT malware families the CTU research team is tracking and the DNS names and domains connected to them. To see the entire graph, it has to be zoomed out to a point where it is impossible to see any detail.

Figure 1. Connections between known APT malware families, DNS names, and domains. (Source: Dell SecureWorks)
The graph in Figure 1 represents only the portion of the APT universe CTU researchers have confirmed through obtained and analyzed malware samples. Zooming in on a tiny section of the graph shows quite a bit of data represented within the blotches (see Figure 2).

Figure 2. Zooming in on the details of the APT malware groups and their connections. (Source: Dell SecureWorks)
Despite the immense scale of the entire graph, it only represents a fraction of the actual cyber-espionage picture. CTU researchers are tracking many thousands of other DNS names with no accompanying malware samples. The absence of samples is most likely because the malware has not yet been discovered by the victim and has not yet been sent to antivirus vendors.
Update on HTran and information sharing
Another stumbling block against a unified message and an approach to defending against cyber-espionage is the different opinions on what information should be shared. For instance, in 2011 the CTU research team published a report detailing a tool called "HTran," used by Chinese cyber-espionage actors to hide their C2 locations by bouncing traffic through a third-party computer in another country. When this disclosure was covered in the news, security researchers both privately and publicly suggested that revealing this information would cause certain parties to lose visibility into attacks where the HTran tool was being used. At publication time, the use of this tool has not ceased or even slowed. To date, the CTU research team has detected hundreds of hidden C2s using the technique that was publicly disclosed. The disclosure has hopefully allowed private organizations that were not previously privy to this knowledge to discover latent cyber-espionage activity on their networks. Over-classification of cyber-threat indicators is a common problem, and one that Dell SecureWorks hopes to solve by increased sharing among private network defenders.
The scope of cyber-espionage
Tracking malware and C2s is only one part of the picture. Truly understanding the mission and scope of the cyber-espionage actors requires insight into who the targets are. One way this is accomplished is by "sinkholing," which involves taking over a domain or IP address used by the hackers and decoding the inbound traffic to identify the victims. In February 2012, the CTU research team shared details of a sinkhole operation that uncovered hundreds of cyber-espionage victims in Southeast Asia. CTU researchers have continued this work by sinkholing a number of other domains that have revealed even more victims.
One of these sinkholing efforts led to the discovery of widespread attacks targeting Japan. While this fact has been revealed in bits and pieces in news stories, it is always useful to know exactly what kinds of organizations are being impacted. One campaign involved a strain of malware that was also used in the RSA breach disclosed in 2011. In this case, the malware targeted a number of Japanese government ministries, universities, municipal governments, trade organizations, news media outlets, think tanks and manufacturers of industrial machinery.
A second cyber-espionage campaign uncovered by the CTU research team's sinkholing efforts involves a lesser-known piece of malware called "Elirks," which uses a stealthy tactic to avoid detection by network administrators. Elirks uses the microblogging service Plurk to act as a first-stage C2. Hackers set up phony Plurk accounts and use them to post encoded messages containing the real C2 URL. This behavior allows the malware to look innocuous in network traffic because it simply appears to be regularly visiting a friendly site. However, when the hackers are ready to exfiltrate data or further penetrate a network, they can redirect the malware to connect to C2 servers where they can interactively log in and control the victim's computer.
Figure 3 shows a network capture of an example Elirks HTTP request.
|
GET /zxzxy HTTP/1.1 |
The Plurk account may contain one or more short messages prefixed with the text "got Available serial Number" (see Figure 4).
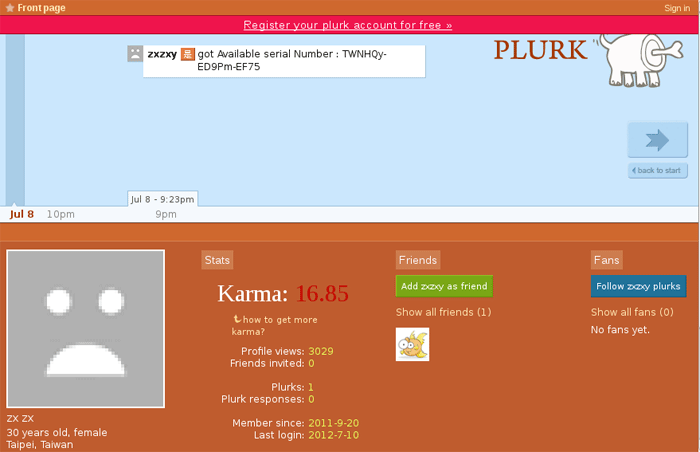
Figure 4. Plurk account containing messages from the Elirks malware.
The code at the end of the message is the IP address and port of the real C2 server, encrypted with a modified Tiny Encryption Algorithm (TEA) and Base-64-encoded using a modified alphabet.
.text:00401C21 |
push |
esi |
| .text:00401C22 | jz | short loc_401C57 |
| .text:00401C24 | cmp | eax, 8 |
| .text:00401C27 | jg | short loc_401C6E |
| .text:00401C29 | lea | eax, [esp+14h+var_C] |
| .text:00401C2D | push | 0Ch |
| .text:00401C2F | push | eax |
| .text:00401C30 | mov | ecx, 8 |
| .text:00401C35 | mov | eax, edi |
| .text:00401C37 | call | modifiedBase64Decode |
| .text:00401C3C | mov | esi, eax |
| .text:00401C3E | add | esp, 8 |
| .text:00401C41 | test | esi, esi |
| .text:00401C43 | jz | short loc_401C6E |
| .text:00401C45 | push | esi |
| .text:00401C46 | push | edi |
| .text:00401C47 | push | edi |
| .text:00401C48 | mov | eax, offset teaKey |
| .text:00401C4D | call | modifiedTeaDecrypt |
| .text:00401C52 |
add |
esp, 0Ch |
The Perl script in Figure 6 can be used to decrypt these encoded C2 strings.
#!/usr/bin/perl
# Elirks C2 decoder
# By Joe Stewart <[email protected]>
use Socket;
use strict;
my $encoded = $ARGV[0];
die "Usage: $0 <encoded Elirks C2 string>\n" unless $encoded;
my $teakey = "\xde\x3e\xfd\x9e\x2c\x5c\x18\xad\x55\x59\x6f\x04\x65\x5c\x06\x8d";
$encoded =~ s/-//g;
my $decoded = DecodeBase64Modified($encoded);
my ($ip,$port) = DecryptTeaModified($decoded,$teakey);
print "$ip:$port\n";
sub DecodeBase64Modified {
# adapted from pure perl base64 decode by zentara
my $d = shift;
$d =~ tr!a-z\@0-9*A-Z!!cd;
$d =~ s/-+$//;
$d =~ tr!a-z\@0-9*A-Z! -_!; my $r = '';
while( $d =~ /(.{1,60})/gs ){
my $len = chr(32 + length($1)*3/4);
$r .= unpack("u", $len . $1 );
}
$r;
}
sub DecryptTeaModified {
my ($a, $k) = @_;
my @key;
my ($de0, $de1) = tea_decode(
unpack("L", $a), unpack("x4 L", $a),
unpack("L", $k), unpack("x4 L", $k),
unpack("x8 L", $k), unpack("x12 L", $k));
return (inet_ntoa(pack("L", $de0)), $de1 & 0xffff);
}
sub tea_decode {
# From Crypt::Tea by Peter J. Billam
my ($v0,$v1, $k0,$k1,$k2,$k3) = @_;
use integer;
my $sum = 0; my $n = 32;
$sum = 0x9e3779b9 << 5 ;
while ($n-- > 0) {
$v1 -= (($v0<<4)+$k2) ^ ($v0+$sum) ^ ((0x07FFFFFF & ($v0>>5))+$k3) ;
$v1 &= 0xFFFFFFFF;
$v0 -= (($v1<<4)+$k0) ^ ($v1+$sum) ^ ((0x07FFFFFF & ($v1>>5))+$k1) ;
$v0 &= 0xFFFFFFFF;
$sum -= 0x9e3779b9 ;
}
return ($v0, $v1);
}
|
From the example in Figure 4, the Elirks backdoor would decode "TWNHQy-ED9Pm-EF75" as "175.45.22.233:80" and would attempt to communicate with that server via HTTP. By searching for the prefix string used by Elirks as well as sandboxing Elirks samples, CTU researchers were able to locate several Plurk accounts being used to feed C2 data to Elirks backdoors (see Figure 7).
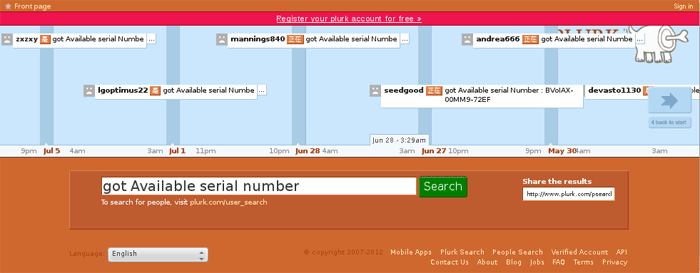
Figure 7. Multiple Plurk accounts used for Elirks C2 data.
Figure 8. Other Plurk accounts used for Elirks C2 data.
Several of the accounts the CTU research team examined appeared to have been purged, but the accounts listed in Figure 9 are still live and serving up Elirks messages at the time of this publication.
|
andrea666 |
Guncannon_Century is the oldest and most active of these accounts — it appears this account was the primary for testing the Elirks malware. CTU researchers decoded the messages on these accounts, and Figure 10 lists the IP addresses posted over the past two years.
|
0.0.0.0:2 |
Sometimes the Plurk C2 update method is used only as a backup if the hard-coded C2 domains are unavailable. By scouring different sandboxes and the CTU research team's malware repository, CTU researchers collected a list of the domains and subdomains used by Elirks variants as well. Zooming in on the APT malware/DNS relationship graph, Figure 11 shows that Elirks is tied to several other cyber-espionage trojans the CTU research team is tracking.
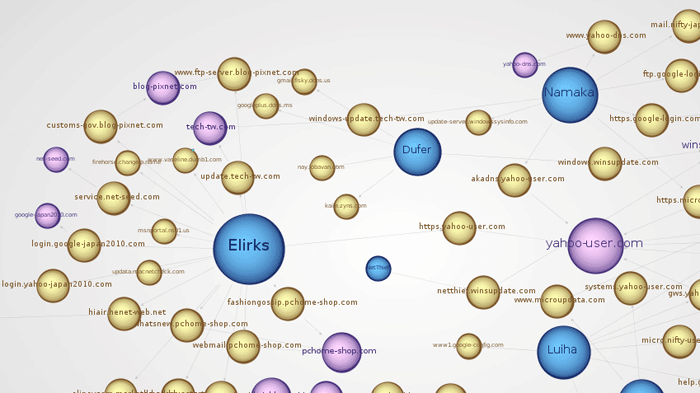
Figure 11. Cyber-espionage trojans linked to the Elirks backdoor malware. (Source: Dell SecureWorks)
By sinkholing several of the Elirks domains after they had expired, CTU researchers observed confirmed Elirks backdoor connections to the sinkhole from dozens of infected systems. Most of these computers are located in Taiwan, with several belonging to government ministries. While this number of infections may seem small, these domains had been abandoned by their owner at least three months before they were able to be re-registered and sinkholed. During this time, infected systems may have been detected, cleaned, or possibly deactivated, meaning the botnets were likely much larger at one time. However, the fact that these systems are still infected after a long time interval and are able to communicate using the Elirks protocol over HTTP means that the defenses of the impacted organizations are clearly not adequate.
For malware researchers wanting to further investigate Elirks, Figure 12 contains a representative list of MD5 hashes of Elirks samples.
|
026f3bda49dad69e5812778228711399 |
6b30f9433456ff84c50ecacd3f05d294 |
Addressing the problem of cyber-espionage
Cyber-espionage does not directly impact every organization on the Internet. Organizations whose intellectual property is not valued by hackers involved in cyber-espionage will likely never see an intrusion into their networks seeking to exfiltrate that information. For those organizations, warnings about cyber-espionage can seem overblown and unnecessary. However, CTU researchers are seeing increasing overlap in the way that cyber-espionage actors and cybercriminals operate. Spearphishing has become a favorite tactic of fraudsters seeking to gain access to an organization's bank account, and web exploits are being adopted by cyber-espionage actors when their target is able to successfully defend against malicious attachments in email. While most organizations may not have intellectual property of high interest to foreign spies working on behalf of competitors or governments, they all have bank accounts. The techniques for defending a network are the same in both cases, and organizations should understand how cyber-espionage attacks work and why they are almost always successful unless appropriate defenses are in place.
The CTU research team has repeatedly advised organizations about the need for segregating critical data on networks and deploying layered, intelligence-driven defenses. However, technology is only a tool, and it must be constantly evaluated and monitored for success by someone with the knowledge and creativity that allows them to stay ahead of the game. Succinctly put, organizations need to have people on or supplementing their team who are as good as or better than the hackers.
The threat indicators the CTU research team is collecting around cyber-espionage attacks are available as an intelligence feed to Dell SecureWorks customers. This data can be used to feed different types of security devices that can employ blacklists of hosts by domain or IP. Additionally, the Dell SecureWorks iSensor intrusion prevention platform has more than 1,000 signatures specifically designed to detect and block cyber-espionage exploits and malware.
A glimpse of the future?
Cyber-espionage by government-backed actors is only the beginning. As it becomes known that more governments are involved in cyber-espionage and cyber-sabotage, this knowledge has the effect of legitimizing this type of activity for private organizations. CTU researchers have uncovered a sizable cyber-espionage operation carried out by a private computer security company in an Asian country (not China) against a foreign military, presumably on behalf of the government of the country where that company resides. Outsourcing of offensive hacking to contractors is to be expected, given that the market demand for such skills often precludes governments from possessing such talent for very long. However, CTU researchers have discovered that the scope of that company's operations also extends to using backdoors and spearphishing to spy on companies in the U.S and Europe, and even journalists native to the same country. Ironically, this same company offers ethical hacking courses as part of its services.
Even though they may never face prosecution, companies that are found to engage in this kind of activity will likely have a difficult time maintaining trusted relationships with ethical security companies and security researchers who disavow such actions against civilian targets. This disconnect will make it harder for these companies to legally obtain real-time cyber threat intelligence, ultimately damaging both their reputation and their ability to defend their clients' networks from attack.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
