Summary
SecureWorks' research team has been alerted to another piece of ransomware in the wild, called Trojan.Arhiveus.
Analysis
Unlike ransomware we have seen in the past, Arhiveus does not actually encrypt files, it simply concatenates them into a file called EncryptedFiles.als along with a name and length header for each file. Another new development in the ransomware arena is the fact that Arhiveus does not ask the user to deposit money into an E-Gold or another money transfer service, but instead attempts to force the victim into buying pharmaceuticals from a Russian website for $75 or more a bottle, depending on the drug. Presumably, the trojan author is an affiliate of the "Pharma Shop" website, and will get a cut of each sale which originated with his/her affiliate ID.
Since Pharma Shop is presumably already operating outside of U.S. jurisdiction and is also apparently involved in spam as well as dispensing controlled substances without a prescription, it makes it unlikely that the owner of the website would cooperate with efforts to obtain the identity of the affiliate spreading the trojan.
Even worse, the trojan author suggests that the victim can even make money off of the scheme, by reselling the drugs, in effect coercing them to become an international prescription drug trafficker.
File Details
Filename: 00xstemp.exe
Filesize: 49,152 bytes
MD5: 5394073fde0e9631e3c42232e6e46c58
SHA1: 3ca424a3dbfd1b886ec7049dc90abc724196068a
Packer: none
Compiler: Visual Basic 6.0
Compile Date: Sat Apr 29 07:40:17 2006
CME Number: none assigned
Identifying Strings:
- myarhive
- E:\troys\myarhive2\myarhive.vbp
- LS-Soft
When run, Arhiveus searches the user's "My Documents" folder for files which it will copy into EncryptedFiles.als, and then delete. A file called Demo.als is also created in the same directory, along with a file named INSTRUCTIONS HOW TO GET YOUR FILES BACK.txt:
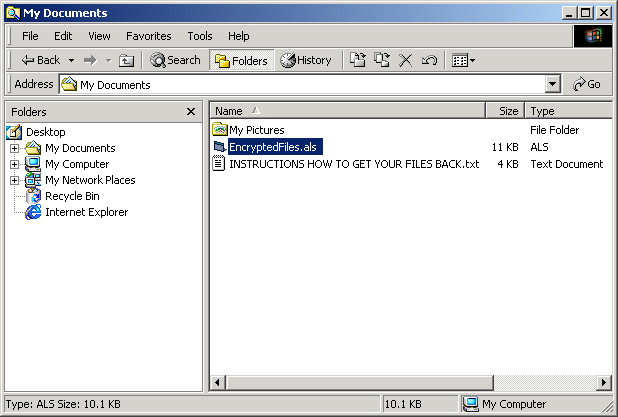
The following content can be found within:
INSTRUCTIONS HOW TO GET YOUR FILES BACKREAD CAREFULLY. IF YOU DO NOT UNDERSTAND - READ AGAIN.This is the automated report generated by auto archiving software. Your computer caught our software while browsing illegal pornpages, all your documents, text files, databases in the folderMy Documents was archived with long password. You can not guess the password for your archived files - passwordlength is more than 30 symbols that makes all password recoveryprograms fail to bruteforce it (guess password by trying allpossible combinations). Do not try to search for a program that encrypted your information - itsimply does not exist in your hard disk anymore. Reporting to police about a case will not help you, they do not know thepassword. Reporting somewhere about our email account will not helpyou to restore files. Moreover, you and other people will lose contactwith us, and consequently, all the encrypted information.WE DO NOT ASK YOU FOR ANY MONEY! We only want to do business with you.You can even EARN extra money with us.If you really care about the documents and information in encrypted file,you should follow the instructions below.This is your only way to get your files back and save your time. ------------------------------How to get your information back.1. Follow any link belowhttp://[blocked]HealthServices.info/ ?833F866fe62adAd883cc38bcd6b0Tdaahttp://[blocked]Products.info/ ?82Fdf3abfb7Abc9385ed1c26afT6bb6ehttp://[blocked]HealthWorld.info/ ?12aba12eF79ef8A4bf7f9bd49Tfc6690and enter our online pharmacy. Our online pharmacy is the world leader inFDA approved medications. 2. Choose any product you like and buy it.3. Send an email with your order id to our email address restoring@[blocked].net or restoringfiles@[blocked].comThe password will be sent to your email address as soon as we verify yourorder id (usually 3-4 hours or shorter) and you will get your informationin encrypted file back. All the emails with invalid order ids will be ignored.------------------------------ We do not ask you for any money! We guarantee that you will receive the productyou buy! You can use it by yourself or even sell and earn extra money becauseall the products in our online pharmacy are discounted!We guarantee that you will receive the password for encrypted file as soon as you buyany product in our online pharmacy.We guarantee that you will be able to restore all the encrypted information and we canprove it. Doubleclick on the file Demo.als and enter the following password:kw9fjwfielaifuw1u3fw3brue2180w3hfse2The encrypted information will be restored in several seconds.The file EncryptedFiles.als is encrypted with another password which you will receivein the email from us.We guarantee that you will never be asked to buy anything in our online pharmacy again.We do not want to do you any harm, we do not ask you for money, we only want to do business with you. ##########################################################################Remember you are just three steps away from your files##########################################################################
The message appears to have been partially cribbed from the message left behind by the Cryzip ransomware first seen in March 2006, however Arhiveus does not appear to be related to Cryzip from a code standpoint.
Arhiveus creates a file association for files with the extension ".ALS" to be opened by itself. When the ALS file is double-clicked, Arhiveus opens a decryption dialog box where it extracts the concatenated files if given the correct password, as shown in the following sequence:
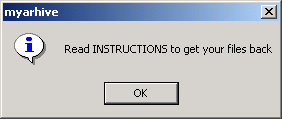
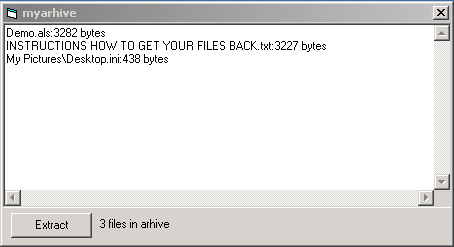
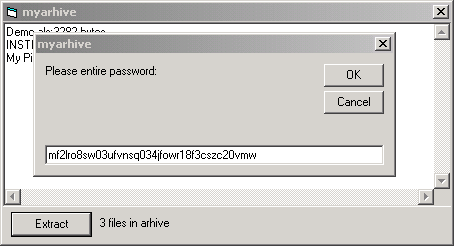
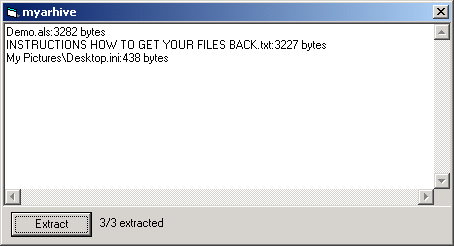
The extraction password is present in the binary in plain text, so with even beginner-level reverse-engineering, the password can be obtained from the Arhiveus executable. The ransom note claims that the executable has been deleted, but in fact, the author is forced to leave the executable on the system as it is required in order to open the .ALS files and check the password. The password in the executable we analyzed is:mf2lro8sw03ufvnsq034jfowr18f3cszc20vmw
Conclusion
The infection vector is unknown at this time, however it could easily be as claimed in the text of the ransom note, "caught while browsing porn", perhaps by malicious websites or in exploits posted to Usenet groups. Infection reports are not widespread at this time. Most users will not have to worry about this threat, however this does appear to be more evidence that a trend of this type of malware is beginning, and malware authors may continue to experiment with the business model of ransomware. But once again, simply having and using proper backup software would mitigate the risk here.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
