Overview
The Dell SecureWorks Threat Report for 2012 analyzes the conditions in 2012 that create threat scenarios and discusses notable trends in software vulnerabilities, global-scale threats, distributed denial of service (DDoS) attacks, Advanced Persistent Threats, and mobile threats.
The findings in this report are based on the ongoing security research conducted by the Dell SecureWorks Counter Threat Unit™ (CTU) research team, broad threat visibility as a Managed Security Services Provider, and Security Risk Consulting incident response experiences. Key findings for calendar year 2012 include:
- The scope of potential threat scenarios remains intrinsically broad.
- Expansion in threat exposure continues to trend heavily toward web services software and end-user devices as primary attack vectors.
- Attack techniques and technology used for global-scale malware deployment continue to mature in terms of scope, resiliency, and effectiveness.
- DDoS attacks continue to be executed for many purposes with notable focus on political and financial motivations.
- There is increased awareness of advanced persistent threats across industry verticals, and threat actors are using targeted attack techniques to exploit commodity and new threat scenarios to penetrate and achieve persistence in target networks.
- Attack technology for mobile platforms is rapidly evolving, with focus on many of the same threat scenarios leveraged against more traditional computing platforms.
- Architecting for security in the face of advancements in threat persistence, and implementing practices to defend against insider threat, continue to present challenges to many organizations.
Threat landscape
The composition of the Internet ecosystem is complex in terms of how connected technology and resources are designed, built, deployed, used, and maintained. Many of the today's threats are a result of people leveraging systemic threat scenarios that are intrinsically built into the fabric of the global Internet. These conditions exist for positive reasons by design, but the potential for misuse is always present. Table 1 demonstrates how certain threat scenarios persist year-to-year and decade-to-decade.
|
Condition |
Threat Scenario |
|---|---|
|
Software can do amazing things, but engineering defect-free software the first time is challenging. |
Software vulnerabilities, exploits, misconfigurations, etc. |
|
People can use the vast array of connected technologies for amazing things but often make complex security decisions with incomplete or misunderstood information. |
Social engineering, malicious email attachments, malicious links, phishing, spearphishing, etc. |
|
Common computing platforms create rich software ecosystems, but not all software is desirable. |
Spyware, malware, potentially unwanted programs (PUPs), etc. |
|
Networked resources are available in all shapes, sizes, and budgets, but networked resources are shared, limited, and consumable. |
Denial of service attacks, particularly DDoS attacks. |
|
Assets can be networked and leveraged to create great value for many stakeholders, but deployed assets represent and have value. |
Motivation to break laws, execute attacks, etc. |
|
A connected world brings people together, but everyone's security posture is affected by the rest of the world's security posture. |
Distributed attack systems, botnets, regionalization / globalization of attacks, relative anonymity, lack of harmonized laws across borders, etc. |
|
Information exchange and commerce is globally empowered, but interdependencies can be attacked. |
Supply chain attacks, leveraging trust relationships, etc. |
Table 1. Internet threat scenarios. (Source: Dell SecureWorks)
For these classes of threat scenarios, attack tradecraft has matured over the years based on threat actors' ability to develop technology that leverages basic and intrinsic threat scenarios. The attack technology is nearly as old as the reasons that allow the techniques to exist. These types of threats are commonly referred to as "commodity" threats — classes of threat that cause security to be a process rather than an achievement and that generally lack complete solutions short of the raw consequence of law enforcement. In a sense, commodity threats are the elements of risk any Internet-connected organization must be prepared to persistently defend against using a combination of layered defenses, good policies and practices, knowledge of current threat information, and the ability to effectively respond to events.
Software vulnerabilities
Security weaknesses and exposures in Internet-deployed software and systems continue to represent a significant global threat surface. Attackers continue to leverage old and new software vulnerabilities in pursuit their objectives.
In 2012, the CTU research team documented 7,696 new software vulnerabilities — a 6% increase over the total number of software vulnerabilities documented for 2011 (see Figure 1).
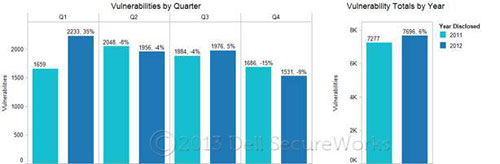
Figure 1. Vulnerability totals by quarter and year. (Source: Dell SecureWorks)
Table 2 shows the percentage of change in specific areas that echo larger industry software development and system deployment trends such as mobile and cloud computing.
|
Area |
Change from 2011 to 2012 |
|---|---|
|
Content management systems (CMS) |
+50% |
|
Mobile operating systems |
+28% |
|
Virtualization and cloud technologies |
+74% |
Table 2. Percentage change in reported vulnerabilities between 2011 and 2012. (Source: Dell SecureWorks)
The distribution of severity levels (high, medium, and low), as scored by the Common Vulnerability Scoring System (CVSS), illustrates that the majority of vulnerabilities discovered in 2012 were rated low to medium in severity (see Figure 2). The riskiest issues encompass the smallest percentage (less than 1%). In cases where a vulnerability has only partial CVSS information (approximately 2% of the total vulnerabilities), the available information has been used to project the vulnerability's worst-case severity level.
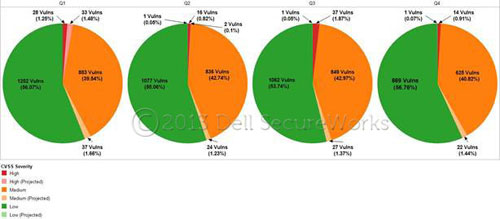
Figure 2. Temporal CVSS-based severity ratings by quarter for 2012. (Source: Dell SecureWorks)
Figure 3 shows that web application vulnerabilities, including cross-site scripting and SQL injection, top the list of classes of vulnerabilities documented in 2012 per Common Weakness Enumeration (CWE) categorization.
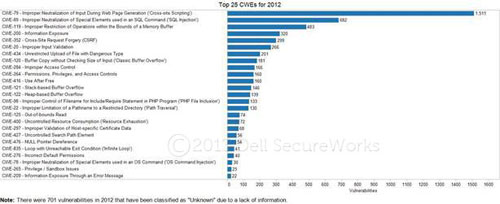
Figure 3. Top 25 common weaknesses for vulnerabilities documented in 2012. (Source: Dell SecureWorks)
As shown in Figures 4 and 5, most vulnerabilities discovered in 2012 were disclosed with official fixes available for remediation. The last two quarters of 2012 showed a rising trend in the percentage of officially remediated vulnerabilities. This trend is also visible when comparing 2011 and 2012 in Figure 5.
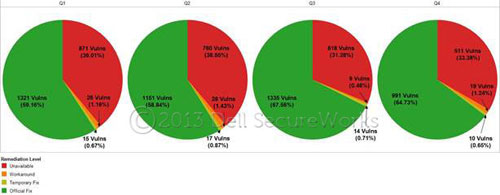
Figure 4. Remediation levels by quarter for 2012. (Source: Dell SecureWorks)

Figure 5. Remediation level trend for 2011 through 2012. (Source: Dell SecureWorks)
This trend is likely to continue, even as the universe of produced software expands, based on an ecosystem of responsible disclosure practiced by vulnerability researchers, software producers improving their software development lifecycles (SDLC) to address security issues, and improved response by product security teams to vulnerabilities reported in software products.
Based on the steady growth of new web application vulnerabilities, and an ever broader deployment of business-critical web applications, it is tremendously important for organizations to direct investment toward secure SDLC, product security, and layered protection strategies when producing, deploying, and maintaining critical web applications.
Notable threats
During 2012, CTU researchers continued to observe large-scale global deployment of malware via specific targeting of end-user systems. Email and web browsing continued to be primary threat vectors exploited by threat actors using maturing classes of attack technology. The diagram in Figure 6 represents a partial view of the complex relationship among attack technologies used to deploy malware and leverage compromised systems.
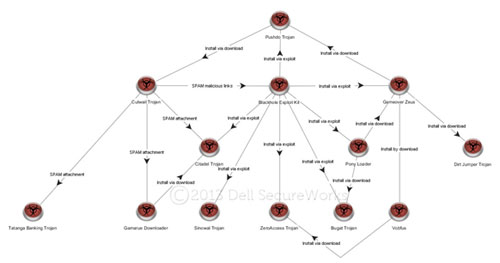
Figure 6. Relationships between attack technologies and malware. (Source: Dell SecureWorks)
The backbone for global malware deployment in this attack system is a large botnet formed and maintained using the Cutwail trojan. The Cutwail botnet, one of the largest and most notorious spam botnets, is used to send massive amounts of email that impersonates well-known online retailers, cellular phone companies, social networking sites, and financial institutions. Cybercriminals can rent access to Cutwail's spam-as-a-service infrastructure to design and execute a spam campaign. The Cutwail botnet relies upon hundreds of thousands of compromised systems to send spam on its behalf and uses templates to generate a large number of variations to the email message to evade spam filters.
Spam email delivered through the Cutwail botnet is typically designed to deploy malware either by attaching a malicious file to an email message, or by using links which, if followed, instruct a web browser to load malicious content supplied by an exploit kit. These two techniques represent direct attacks via email and web browsing as primary threat vectors, and they provide threat actors with a diverse and automated means of widely deploying malware.
An exploit kit is a packaged collection of exploits wrapped in a toolkit to enable the efficient and large-scale execution of attacks leveraging known software vulnerabilities. Most exploit kits target the attack surface created by end-user web browsers and software a website can invoke through an end-user web browser. The Blackhole exploit kit is among the most commonly observed, though there are many variations in use that accomplish the same end goal of deploying malware on end-user systems via exploitation of unpatched web browsing software.
As illustrated in Figure 7, the Pushdo Trojan horse plays an important role in maintaining the Cutwail botnet. Threat actors continually deploy additional Cutwail trojans to join the global Cutwail botnet to ensure the botnet's survival despite remediation efforts. Pushdo is commonly deployed using the Cutwail botnet in combination with the Blackhole exploit kit, forming a self-sustaining loop designed to maintain and expand the breadth of the Cutwail botnet.
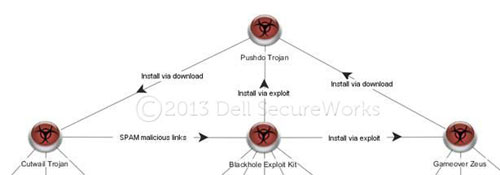
Figure 7. Malware interrelationships in the Cutwail botnet ecosystem. (Source: Dell SecureWorks)
The CTU research team has also observed the Pushdo trojan being installed via direct download by other malware families such as Gameover Zeus. The use of both a web exploitation threat vector and installation via downloader to deploy the Pushdo trojan highlights the trend of threat actors actively building multi-path diversity and resiliency into the techniques and technologies used to sustain large malware deployment infrastructures.
As an example of the continued effectiveness of large-scale malware distribution, consider the global distribution of just one malware family linked to the deployment infrastructure described above. The ZeroAccess trojan uses a custom peer-to-peer (P2) protocol for command and control (C2).
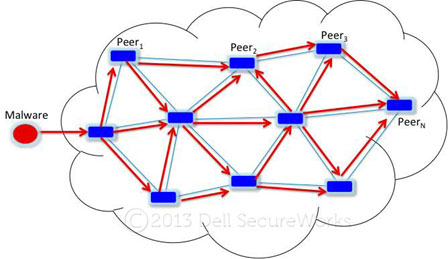
Figure 8. High-level diagram of the distribution of malware through a P2P botnet. The rectangles in blue represent peers that propagate malware to their neighboring peers. (Source: Dell SecureWorks)
The purpose of the ZeroAccess trojan is to download and install additional malware components as part of a pay-per-install affiliate program. Said another way, ZeroAccess is used to deploy even more malware. Figure 9 shows the global scope of systems known to be compromised and running at least one version of the ZeroAccess trojan. Known infected systems are colored with light blue dots.
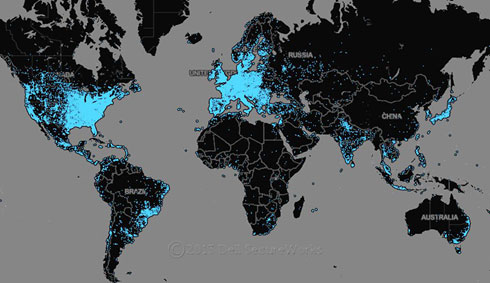
Figure 9. Map of ZeroAccess v2 infections. (Source: Dell SecureWorks)
Although large-scale commodity threats are caused by a relatively small number of people, remediation becomes a global issue. Many organizations sustain their own defensive posture relative to common threat scenarios. It is also tremendously important to work together as a community; one organization that avoids direct compromise by a commodity threat remains exposed to risk created by those that are not so well defended. Likewise, the threat scenarios exploited by the people and technology behind commodity threats represent the same threat scenarios and techniques that are likely to work during a targeted attack. Complex attack systems exist and quite readily achieve global impact using many of the same commodity threat scenarios leveraged by targeted threat actors.
DDoS trends
The CTU research team continues to observe growth and active development within the underground economy, both in offering DDoS as a service as well as creating DDoS kits usable by threat actors with any skill level. Dirt Jumper is the DDoS malware family most often encountered by CTU researchers, and it went through several iterations throughout 2012. While Dirt Jumper can still be found by its original name, the most recent version has been named Pandora. A number of other DDoS kits surfaced, such as YZF, DiWar, and ArmageddoN. Some of these kits turned out to be a rebranded version of Dirt Jumper. Others, such as BlackEnergy and Optima, remained in active use as well.
The concept for these malware families is simple:
- HTTP-based C2 botnet
- Sole focus: DDoS
- Operates as a multi-threaded process
- Starts a new thread to execute each task
- Can attack by domain or IP address
- HTTP, HTTPS, and FTP assets
- Can target other assets by IP address and port
Controlling a DDoS botnet or acquiring DDoS as a service from a criminal group continues to be simple and relatively inexpensive. Observed DDoS C2 infrastructure remains distributed globally, with higher concentrations in Ukraine, United States, and Russia.
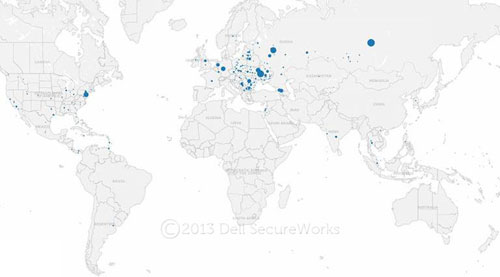
Figure 10. Geographic breakdown of known DDoS C2 infrastructure. (Source: Dell SecureWorks)
DDoS used as cover fire for parallel attacks
Working with organizations affected by Dirt Jumper DDoS attacks revealed a threat scenario in which the threat actor first performed a short-lived "test" DDoS attack to determine if the actor's botnet could make the targeted site unusable. If the test was successful, then the threat actor performed another DDoS attack in the near future, but this time the DDoS attack occurred shortly after an unauthorized wire or Automated Clearing House (ACH) transfer out of a compromised account. DDoS attack patterns revealed that short-lived attacks were an indicator of an unauthorized wire transfer, while longer attacks, which could last hours to days, were indicators of a fraudulent ACH transfer. The fraud attempts were nontrivial and were usually in the six-figure range, with some attempts in the millions of dollars. Transfers were being made to banks located in Russia, Cyprus, and China.
Eventually the "test" DDoS attack was phased out. Visibility on these attacks proved to be quite useful — in some cases, the DDoS attack was the initial notice that high-dollar fraud was occurring. Some of the fraud attempts and losses are staggering, with total dollar values of attempted fraud ranging from $180,000 to $2.1 million.
DNS amplification to generate DDoS attack payload
Attackers use DNS amplification attacks to magnify the amount of bandwidth they can send a victim. The attacks are possible due to poorly-configured software and devices. To create a successful DNS amplification attack, a threat actor needs two things: a list of open recursive DNS resolvers and a system for spoofing packets. Open recursive DNS resolvers respond to any IP address on the Internet that queries them, instead of only being available to trusted systems. Neither of these two resources is difficult to acquire.
Throughout 2012, the CTU research team witnessed multiple DNS amplification attacks on the Internet. While targets varied, the sizes of the attacks were staggering: there were reported bandwidth totals of 30Gbps, 50Gbps, and 65Gbps.
DNS amplification attacks are a defensible class of problem, in that network and system administrators can take a variety of steps to combat this issue. Network ingress filtering as described in BCP38 prevents spoofed packets from leaving a network (BCP84 should be reviewed for multihomed networks). Either disabling recursion or only permitting queries from specific Classless Inter-Domain Routing (CIDR) blocks prevents unauthorized parties from abusing DNS servers. DNS Response Rate Limiting (DNS RRL) is another feature that can limit the effectiveness of an attack on an authoritative name server.
Operation Ababil
A multitude of high-profile DDoS attacks began targeting the United States financial sector in September 2012. The group Izz ad-Din al-Qassam Cyber Fighters (QCF) took credit for this effort, named "Operation Ababil." According to QCF, the attacks were in retaliation for a YouTube video insulting the prophet Muhammad and would continue until the video is removed.
- Attacks lasted more than 4 months
- Target: HTTP, HTTPS, IP, DNS server resources
- GET/POST requests, bandwidth consumption attacks
Careful examination of top-talking attacking IP addresses revealed that all were compromised web servers. During the remediation process, CTU researchers identified a common set of malicious PHP files that were placed on the websites through the exploitation of multiple content management systems (CMS). Joomla was the most exploited CMS, followed closely by WordPress. Based on CTU analysis, the Bluestork template within Joomla is the most exploited vulnerability in this botnet.
As of January 2013, the CTU research team was aware of at least 34,714 malicious URLs related to Operation Ababil. This number is based on the unique count of malicious URLs observed across time and includes URLs with filenames that have been renamed. These malicious URLs reside on 20,862 unique domain names. Of those compromised domains, there are 15,163 unique IP addresses spread across 149 different countries.
These compromised web servers generated attack traffic in the tens of Gbps in size and tens of millions of packets per second (pps).
Use of compromised websites as DDoS botnets
The use of websites as botnets presents a significant challenge and risk to the Internet community. The large numbers of web servers provides a huge potential attack surface and a high cost of remediation. Typical web servers run a wide variety of software, most of which is not automatically patched for known vulnerabilities. Web servers typically operate continuously, eliminating botnet agent downtime for an attacker. Web servers are also typically well-connected with access to high levels of availability and bandwidth, and they typically do not run endpoint security controls such as antivirus software. They generate volumes of traffic and log files, which make detecting anomalous behavior challenging.
Advanced Persistent Threat
Advanced Persistent Threat (APT) continues to emerge as a prominent concern in today's threat landscape. APT attacks represent a growing threat to an organization's intellectual property, financial assets, and reputation. Targeting of critical infrastructure and government suppliers can threaten a victim country's national mission. The defensive tools, procedures, and other controls commonly put in place to handle commodity security threat scenarios are an important layer of defense against APT-style threat actors. However, there are differences based on the targeted nature of the attacks. The threat actors behind the intrusion focus on a specific target and customize and adapt their tactics, techniques, and procedures (TTP) to predict and circumvent security controls and standard incident response practices. Consistently applied, and adaptable, defense and response practices are critical.
Achieving and maintaining persistence in a target organization's network is a key element of APT-style attack campaigns. Many different malware families have been observed in use as a part of APT attack campaigns aimed at persistence. Understanding, defending against, and responding to persistence is a key layer in a robust defensive posture against APT attacks.
The illustrations in Figures 11 through 14 show observed APT malware family activity by quarter during 2012. Most of the malware types represented in the charts are trojans aimed at achieving and maintaining persistence within a compromised network. The icon (insect) size represents the number of unique organizations affected, while the shading of the icon represents the magnitude of observed telemetry indicating use of the particular malware family.
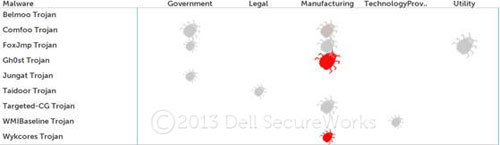
Figure 11. APT malware activity for 1Q2012. (Source: Dell SecureWorks)
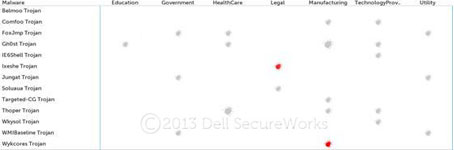
Figure 12. APT malware activity for 2Q2012. (Source: Dell SecureWorks)

Figure 13. APT malware activity for 3Q2012. (Source: Dell SecureWorks)

Figure 14. APT malware activity for 4Q2012. Source: Dell SecureWorks)
The variety of APT threats encountered within a single vertical can indicate different attack campaigns executed by multiple threat actors.
Specific APT threat actors often deploy multiple families of malware during a single attack campaign to increase their chances of remaining persistent in the target environment. The actors vary the malware families used at different access points into the same victim organization. This approach is a key persistence strategy. If indicators from one family of malware are detected, the victim may block related communications or begin eradicating the malware from all systems exhibiting those indicators. Diversifying the malware allows the actors continued access to operate even if one or more malware families are detected. The actors can then continue lateral movement to spread to a new set of systems using more families of malware. This persistence tactic is one of the reasons affected organizations may find it difficult to eradicate APT threats.
CTU researchers have observed and are tracking common Internet infrastructure being shared between multiple malware families. These shared network indicators demonstrate that multiple malware families are often used by the same threat actor groups to maintain persistence within a single attack campaign.
The graph in Figure 15 demonstrates the interconnectivity between observed APT malware families based on their use of common domains across multiple malware families. The nodes of the graph represent domains, and the connections between nodes represent relationships based on malware families leveraging the domains. Tightly clustered groupings are singular malware families leveraging many domain names. Linkage between clusters represents infrastructure shared between malware families.

Figure 15. The relationships between malware families and common domain name usage. (Source: Dell SecureWorks)
Drilling down into connectivity between a single malware family and other malware families further shows the interconnected use of shared domains between malware families. The graph in Figure 16 represents domain infrastructure observed used by the Comfoo trojan, along with linkages to the following nine malware families that use at least one common domain:
- Fakemsn trojan
- Gh0st trojan
- Conime trojan
- Glofun trojan
- Mindjob trojan
- Poison Ivy trojan
- Protux trojan
- Vinself trojan
- Wolyx trojan
The nodes on the graph in Figure 16 represent domains, and the blue links between nodes represent relationships between domains based on the observed malware family. The dark cluster of nodes near the top of the graph consists of domains used by the Comfoo trojan. The red clusters of nodes toward the bottom of the graph represent domains used by the other nine malware families. The horizontal bar near the center of the graph represents 12 domains that are linked to both the Comfoo trojan and the other nine malware families.
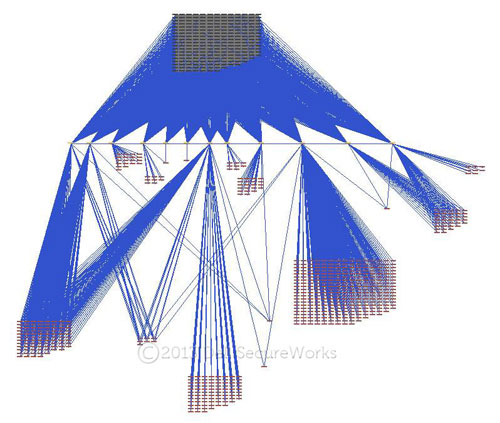
Figure 16. Domain name interrelationships between Comfoo trojan and nine other malware families. (Source: Dell SecureWorks)
The Comfoo trojan is relatively prolific in terms of its interconnectivity to domain infrastructure used by other malware families. The FoxJmp trojan, in contrast, shares common domain utilization with only two other malware families, denoted by the red nodes in Figure 17. Yet, analysis reveals more than two variations in the clustering of domains because the FoxJmp trojan is actively evolving, and multiple variations were observed in 2012.
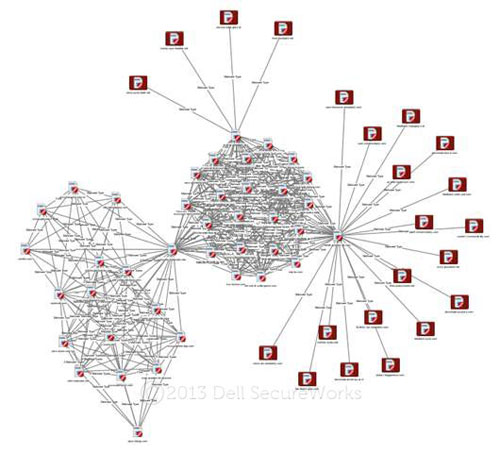
Figure 17. Evolution of the FoxJmp trojan's use of domains with other malware families. (Source: Dell SecureWorks)
The FoxJmp trojan is an example of one malware family used in the persistence stage of an APT attack campaign. It is notable for its prevalence across multiple verticals in each quarter of 2012, and it highlights the evolution of a single APT malware family even on a per-attack campaign basis.
FoxJmp samples analyzed by the CTU research team include the following attributes:
- Designed to run persistently, without detection, on a compromised system. The goal of the malware is to help an actor gain and expand a beachhead into a target network using compromised systems.
- Used as a platform to retrieve and run additional malicious programs on a compromised system.
- Uses C2 techniques where instructions are embedded in files, such as JPEG files, and retrieved via Hypertext Transfer Protocol (HTTP) requests. See Figure 18.
- Can be instructed to sleep for arbitrary period of time after receiving an instruction, keeping subsequent retrieval of additional malware "low and slow" in terms of overall observable network security events.
- Obfuscates and embeds additional retrieved malware in decoy files retrieved via an HTTP request.

Figure 18. An example HTTP request by FoxJmp to retrieve an image file with instructions. The highlighted field contains the encoded computer name of the compromised system and the malware's installation ID. (Source: Dell SecureWorks)
Analysis of FoxJmp variants discovered throughout 2012 revealed an evolution of the malware. Features were changed to add or remove functionality based on the needs of a particular attack campaign. In one observed variant, the persistence mechanism was replaced with a self-destruct capability. Coupled with the addition of an interactive channel to execute arbitrary commands in a shell on the compromised system, this variant's C2 design included a way for the actor to directly interact with the malware in a highly customized manner during a specific APT attack campaign.
Notable APT campaigns
In early 2012, CTU researchers released a report titled "The Sin Digoo Affair." This report presented activity related to the Enfal, RegSubDat, and Murcy malware families and their role in a multi-year espionage-by-malware operation affecting governments and industry around the world.
In late February and early March 2012, threat actors circulated emails to members of the International Tibet Network, a global coalition of Tibet-related non-governmental organizations. This targeted phishing campaign exhibited characteristics common in APT operations. The emails were delivered with the subject line "10 March 2012." The message body contained information about the Tibetan National Uprising and 24 Tibetans who self-immolated in protest against the actions of the Chinese government. These emails also included several attachments, including a Microsoft Word document that attempted to exploit CVE-2010-3333 (Microsoft Office RTF stack buffer overflow vulnerability) to install the Comfoo Trojan horse on victim systems.
CTU researchers observed another APT-related malware distribution campaign in March 2012. This campaign used emails to deliver malicious documents such as "Iran's Oil and Nuclear Situation.doc." These documents attempted to leverage a vulnerability in Adobe Flash (CVE-2012-0754) to install the Mswab trojan. Mswab is a backdoor Trojan horse that provides remote access and the ability to steal intellectual property as part of an APT.
The Dell SecureWorks Threat Analysis "Chasing APT," released in July 2012, examines the size of the threat based on CTU research since February 2011. At the time of the report's release, CTU researchers had identified 200 unique malware families. These families are malware samples that share a common code base and only vary based on different C2 servers or in basic functionality. From these families, the CTU research team identified more than 1,100 domain names, with close to 22,000 subdomains used by APT threat actors for malware C2 servers or spearphishing. Figure 19 illustrates a small region of these associations.
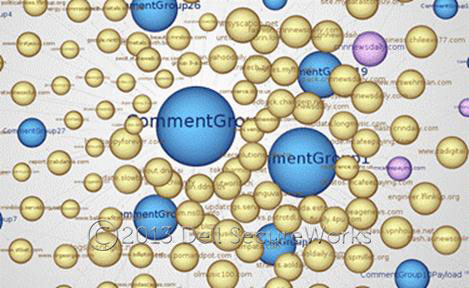
Figure 19. Zooming in on the details of the APT malware groups and their connections. (Source: Dell SecureWorks)
Prior to the "Chasing APT" report, many of the hypotheses about the scope of the issue were based on statistical calculations and predictions of threat actors' intent. This report revealed the scope of activity through looking at the historical CTU data, as well as data received through partnerships in the security community and through in-house tracking efforts.
The follow-up report to the "The Sin-Digoo Affair" titled "The Mirage Campaign," published in early September 2012, tracks the same actors behind the Enfal and RegSubDat malware families to the Mirage malware family.
At the end of 2012, CTU researchers began tracking a series targeted threat campaigns that embedded malicious code in legitimate websites. In some cases, zero-day exploits were used avoid detection.
The first of these campaigns was the "VOHO" or Elderwood campaign, which infected websites related to activism, national defense, financial services, and local state government. Analysis by CTU researchers and other security groups revealed up to eight different zero-day exploits for Microsoft Internet Explorer and Adobe Flash Player (CVE-2010-0249, CVE-2011-0609, CVE-2011-0611, CVE-2011-2110, CVE-2012-0779, CVE-2012-1875, CVE-2012-1889, and CVE-2012-1535) used in the attacks. The exploits embedded in these sites were used to drop a variant of the Gh0st remote access trojan onto the compromised systems.
In late December 2012, CTU researchers investigated a "watering hole" campaign that leveraged the Council for Foreign Relations (CFR) website. Watering hole campaigns target sites likely to be visited by individuals of interest to the threat actor. News about the CFR attack was disclosed on December 27. The CFR website was compromised to include a malicious script that exploited an undisclosed Internet Explorer vulnerability (CVE-2012-4792) against returning visitors and installed a backdoor on vulnerable systems. Within two days of the public disclosure, the vulnerability was weaponized with a working exploit released to the public.
The use of "watering hole" attacks has become a new and popular vector for exploiting specific targets in a regimented and organized manner. Based on the frequency of these attacks, CTU researchers are confident that this type of attack will become common in the future.
Mobile device threats
As mobile networked computing devices become more common, attackers are actively developing and maturing technology and techniques to leverage threat scenarios associated with mobile devices.
In 2012, mobile malware development and deployment primarily focused on the Android mobile platform. The trend toward targeting Android is not likely to change based on public market share data; threat actors have traditionally targeted malware development and use on the most broadly deployed platforms. The raw count of unique Android malware samples is growing exponentially each month.
Mobile malware continues to increase in complexity and is maturing quickly. For example:
- The Opfake malware family now uses types of polymorphism.
- FakeRegSMS employs steganographic techniques.
- RootSmart contains privilege escalation ("rooting") exploits.
- FakeToken malware steals sensitive information under the guise of a single-use authentication generator targeting popular banks.
The rapid evolution of mobile malware is following a similar, though accelerated, progression as that observed in traditional PC-based malware over the past decades.
Malicious actors are beginning to use variations on existing attacks that have historically been successful on traditional computers. Hybrid attacks are emerging that combine traditional computer and mobile threats. While the majority of Android malware is still found in unofficial third-party markets, attackers are increasingly leveraging drive-by downloads, luring victims to malicious sites using in-app advertising links, social networking profile pages, and email campaigns. Similarly, recent malware uses Twitter for C2 communication. Perhaps most concerning is the high percentage of mobile malware families that use rooting (also known as jailbreaking) privilege escalation exploits. These exploits effectively grant more administrative access to malware than granted to a typical user or device management software.
Approximately two-thirds of Android malware observed by CTU researchers has been grafted into existing legitimate applications (also called "repackaging"), and most malware is distributed via alternative marketplaces. After publishing a malicious application to an alternative marketplace, an attacker still faces the problem of convincing people to download the application. People are less likely to download an unpopular or new, unrated application. Social engineering is used to alter application ratings.
For example, the SimpleTemai malware, discovered during the third quarter of 2012, uses social engineering by artificially inflating the popularity of certain applications. Once installed on a victim's device, the malware downloads, rates, and uninstalls applications from alternative marketplaces. Unlike other malware, SimpleTemai does not directly harm the victim by stealing information or cause a financial burden. For people with limited bandwidth plans, this malware may exhaust the monthly data plan allocation, causing a victim to pay for additional increments of bandwidth. If the execution of SimpleTemai is interrupted, for example by turning the device off, then the device may have unexpected and undesirable applications installed. SimpleTemai has been observed on the Internet in Chinese alternative markets and has been repackaged into existing applications.
Some mobile malware families monetize infected devices using Premium SMS, usually by sending a short code via SMS to request premium pay content. On systems that require confirmation (such as in the U.S.) the malware may also intercept the verification SMS and automatically send the proper confirmation message. In a slight variation of this attack, malware known as MMarketPay attempts to purchase mobile applications or videos from a particular marketplace. The market, run by China Mobile, confirms all paid app downloads via SMS message. MMarketPay intercepts this confirmation SMS, and if required will upload a CAPTCHA to a secondary server for analysis. MMarketPay automates the process of downloading paid content from the market, circumventing verification controls.
New system architectures and software distribution models introduce new avenues for attack. A new type of attack observed in 2012 is an application update attack. Android can permit installed applications to automatically update if the updated application requests the same permissions and is cryptographically signed by the same key as the incumbent application. In application update attacks, a user first downloads a malware-free application that was created by an attacker. Later, the original application is automatically updated to one that contains malicious content.
The ubiquity of mobile devices and the regularity with which they move between networks challenge conventional security boundaries. A new threat in the second quarter of 2012, named NotCompatible after one of the C2 domains, acts as a proxy that gives the attacker access to networks accessible by the mobile device. As shown in Figure 20, this Android malware poses as a security update and is downloaded directly from the Internet. Once executed, the malware behaves as a botnet client, initiating contact with C2 servers and executing attacker commands. The connectProxy command permits the attacker to make TCP connections through the device, including connections to any local or restricted hosts accessible by the device.
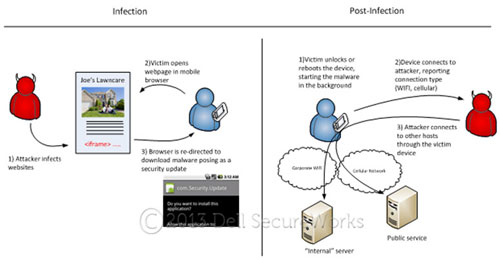
Figure 20. Android "NotCompatible" malware permits attackers to connect to network resources through an infected mobile device. (Source: Dell SecureWorks)
Telemetry data from the fourth quarter of 2012 shows that at least one NotCompatible campaign is reaching a global victim pool, as shown in Figure 21. This particular NotCompatible network was used to send email spam.
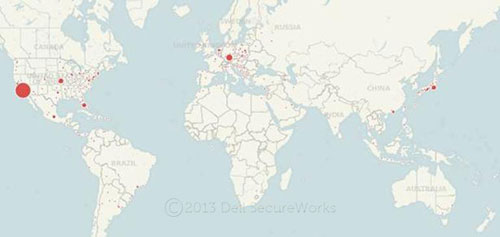
Figure 21. Worldwide Android NotCompatible infections. (Source: Dell SecureWorks)
The SpamSoldier malware, discovered in the fourth quarter of 2012, propagates primarily via SMS. In this attack, a victim receives a text message to download a popular game (Figure 22), likely from an unrecognized number. SpamSoldier installs and hides itself, and then automatically installs the game expected by the victim. The malware retrieves lists of messages and target numbers from a remote server and sends the message to each telephone number via SMS. The first indicator of the effects of this malware may be the SMS log as part of the victim's monthly bill.
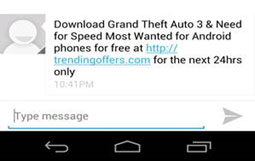
Figure 22. Android SpamSoldier spam text message. (Source: Dell SecureWorks)
While Android persists as the primary target for malware, exploits targeting Apple iOS are still being developed and used. These exploits are commonly found on jailbreaking websites and are used by individuals who wish to gain elevated administrative access on an iOS device. Often, a willing user downloads an application-level exploit (such a browser or PDF-based exploit) followed by a root privilege escalation exploit. Determining the security posture of a device after this process may require extensive analysis of the exploits; therefore, the resulting security posture is often unknown. While particular device and version support varies, public exploits are readily available for all iOS phone and tablet devices.
Common financial sector botnet software now has mobile-oriented components. Both Zitmo (Zeus in the mobile) and Spitmo (SpyEye in the mobile) have been used for nearly two years to steal SMS messages used for out-of-band transaction authentication mechanisms. In 2012, malware such as Tatanga and Carberp have embraced mobile devices.
During 2012, these financial sector attacks predominately targeted European countries such as Germany, the Netherlands, Italy, Portugal, and Spain, where banks tend to use SMS for transaction verification. However, Carberp variants have been observed targeting Russian banks. Carberp C2 servers were primarily observed in Poland and Russia.
The mobile space continues to evolve rapidly, both in malware maturity and in security controls. Most malware continues to target the Android platform. Most malware is found in unofficial, third-party markets. Use of marketplaces that do not have published and practiced malware identification and remediation practices result in additional risk.
Applying relevant security updates for mobile device software remains a best practice. Security-conscious users may want to use applications, particularly web browser applications, that differ from built-in applications. Using external applications allows security updates to be applied more frequently than periodic operating system updates. In general, the practice of controlling threat exposure by limiting and updating installed applications is as valid on mobile devices as it is for traditional computing devices.
Conclusions — Insights from incident response
Defending against a full range of threat scenarios requires a persistent, layered approach to security as a system of process. History and experience suggest even the best security implementations are likely to, at some point, experience attacks, accidents, or failures that violate security policies and trigger incident response processes. Security incidents represent opportunities to learn and improve.
The following observations are based on experiences helping organizations respond to security incidents via the Dell SecureWorks Security Risk Consulting practice.
- 80% of the Dell SecureWorks incident response engagements in 2012 resulted from activity initiated by external actors. The remaining 20% of engagements resulted from insider threat activity.
- The top three targeted verticals were Manufacturing (17%), Financial (16%), and Industry Service Providers (15%).
Figures 23 through 25 highlight primary asset targeting, attack vectors, and affected attributes observed across incident response engagements.
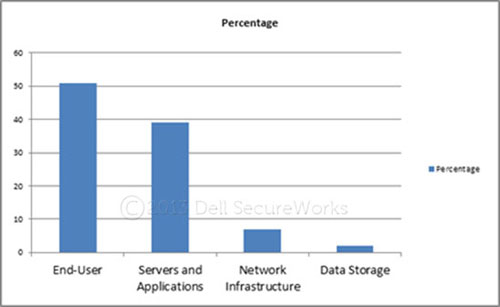
Figure 23. Assets targeted by threat actors in 2012. (Source: Dell SecureWorks)
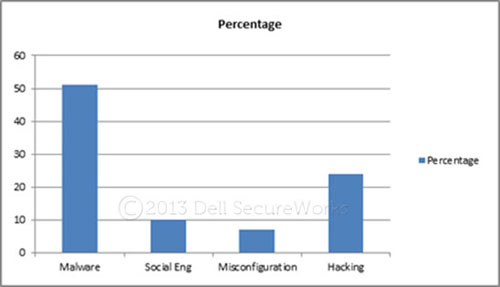
Figure 24. Attack vectors used in 2012 incident response engagements. (Source: Dell SecureWorks)
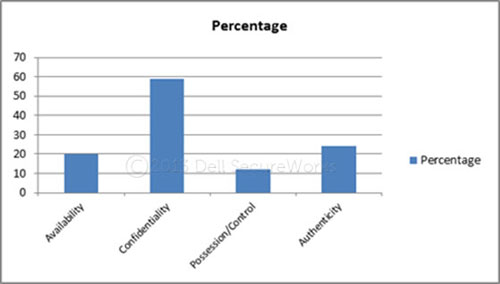
Figure 25. Affected attributes for 2012. (Source: Dell SecureWorks)
At a high level, Dell SecureWorks’ incident response experiences in 2012 underscore several key conditions and trends:
- End-user / application targeting — End users and end-user applications continue to be primary targets for threat actors behind both commodity and APT attacks. Social engineering and reconnaissance of targeted organizations is prevalent and advancing, making phishing and spearphishing campaigns more convincing.
- Data exfiltration — External-facing web and application servers still provide significant risk to organizations. They pose the most risk to legal exposure with the possible compromise of Personal Identification Information (PII) and Payment Card Industry (PCI) data.
- Architecture — Many organizations still struggle with legacy IT architectures that are poorly designed for defense, have poor segmentation of critical systems, and use very little (if any) data classification that offers additional layers of protection for critical intellectual property. Administrator privileges are often not properly managed or controlled, which allows threat actors to easily attain administrator or domain administrator access.
- Insider threat — Organizations take very little or no proactive measures to monitor insider threat activity or to reduce the risk of insider activity. Nearly all of the incident response engagements that involved an insider threat were investigations where a terminated employee was suspected to have used elevated privileges to sabotage the network or to remove intellectual property. In only one case did an organization discover the activity through a data loss prevention (DLP) solution. As security policy is formulated and becomes practice, there is a continued disconnect between IT / IT Security departments and Human Resources (HR) departments in many organizations. Managers who supervise employees with privileged access should consider restricting that access when poor performance or employee misconduct is observed. The basic practice of terminating access, especially privileged access, before an employee leaves an organization would have mitigated most of the insider threat incidents.
Recommendations
Organizations can adopt key practices to improve their ability to defend, detect, and respond. The recommendations are grouped into three broad categories based on perceived difficulty of implementation: low complexity, medium complexity, and high complexity. While this is not a comprehensive list of security measures and controls, these actions would have significantly minimized the incidents observed by the Dell SecureWorks Security Risk Consulting team in 2012.
Low complexity (Can be implemented by management controls or IT staff):
- Implement a strict policy on elevated privileges based on risk. Ensure users with elevated privileges only log in as an administrator when doing administrator-level tasks. Limit and properly train users with domain-level administrator access, and ensure they execute their duties in a secure, monitored, and audited manner.
- Conduct aggressive user training and certification to raise the level of awareness about threat actors targeting the organization. Tie user access and privileges to performance and compliance with training programs. For example, restrict Internet access for non-compliant users.
- Limit DNS traffic in the network configuration to guard against both inbound and outbound DNS UDP traffic, minimizing the risks of a DDoS attack.
- Ensure critical network infrastructure elements (e.g., DNS, domain controllers, routers) are on non-routable IP space and are configured to reduce arbitrary discovery by authorized parties (i.e., do not respond to simple network scans).
- Work with business owners to properly classify data in risk categories (i.e., high, medium, and low).
- Ensure only application servers and data storage that must be accessed from outside of the networks are connected to the Internet. Ideally, place servers that require these connections in a DMZ (perimeter network).
- Coordinate communication between the HR and IT Security staff to share advance notice of pending termination of employment. Managers of employees with elevated privileges should be cognizant of the risk their employees pose to the enterprise and take appropriate actions to restrict access when warranted by employee poor performance or misconduct.
- Establish an incident response plan that is compliant with the organization's recognized standards (e.g., PCI/PFI, NIST, HIPAA). Routinely rehearse the plan to validate procedures and the team's proficiency.
Medium complexity (Can be implemented by IT staff with support from security professionals):
- Route all web traffic through proxy servers located in a DMZ.
- Implement two-factor authentication, especially for remote access through a virtual private network (VPN).
- Implement an alternate token for administrator access.
- Ensure desktop environments are configured to an enterprise-wide security standard, risk is reduced through a secure configuration, and patching of OS and application software is timely.
- Tier and map access controls to the data classification program so users only have access to data they need to do their jobs. Determine data access as part of the HR onboarding process.
- Ensure IT and security staff are involved in merger and acquisition processes, and develop a plan for integrating the newly acquired IT infrastructure into the parent organization security plan.
- Aggressively patch and conduct vulnerability scans of external-facing data and application servers, prioritizing servers with critical data such as PCI and PII.
- Strip high-risk email attachments (e.g., EXE, RAR, SCR) from all inbound mail.
- Implement a security checklist for the software development lifecycle (SDLC) internal to the organization. Ensure application development considers security and the risk accepted during the SDLC is transparent so security staff can reduce the residual risk.
High complexity (requires a security professional and possible outside consulting services):
- Ensure IT architecture is designed with security in mind. Establish aggregation points where firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and deep package inspection (DPI) are in line and able to filter and inspect all inbound and outbound traffic.
- Consider subscribing to signatures and indicators provided by a Managed Security Service Provider (MSSP) to ensure network defense appliances (e.g., firewalls, IPS, IDS) are tuned with threat indicators gathered through activity observed across a multitude of networks.
- Consider implementing enhanced, in-line filtering of email and web traffic where executable code is discovered with both signature-based indicators and in-line sandbox discovery. Ensure SSL traffic is decrypted at the boundary and inspected for threat activity.
- Optimize event logging to ensure capture of all relevant security events that could be elevated to security incidents. Conduct some type of analytics on these event logs based on a reputable set of threat indicators to look for threat activity that may be avoiding signature-based defense appliances.
- Subscribe to a DDoS protection provider if critical business operations rely on connectivity with customers from the Internet. Rehearse and stress test DDoS recovery plans and ensure they can be implemented in close coordination between the IT and security staff.
- Implement a DLP solution that is integrated with a digital rights management (DRM) solution to detect activity and prevent improper sharing of critical intellectual property.
- Where required for scale, implement an electronic governance, risk management, and compliance system (eGRC) to monitor security controls and compliance to policy and procedures.
- Conduct regular penetration testing and red-teaming of security controls by an outside party to assess effectiveness.
- Conduct brand and executive intelligence surveillance of the organization to help identify threat actors, quantify their risk to the organization, and assess vulnerabilities to these threat actors' capabilities.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
