Dell SecureWorks Counter Threat Unit™ (CTU) analysts previously observed the use of Unicode characters within the Windows Registry to obscure the presence of malware on a system. Similar techniques can be used within the file system. CTU analysts examined a system infected with the Win32/Vercuser.B worm, which was obscured, in part, through the use of a Unicode character.
While performing Targeted Threat Hunting services for an enterprise, CTU analysts detected the Poison Ivy remote access trojan (RAT) running within the memory of a system. A review of additional data provided no indications of other artifacts known to be associated with Poison Ivy infections previously observed by the CTU research team, such as network traffic for command and control (C2) communications, related file paths, Windows services, and the use of NTFS alternate data streams (ADSs).
CTU analysts received an acquired image of the compromised system.
An initial inspection of the image using AccessData FTK Imager version 3.1.0.1504 revealed two folders named “Program Files” (see Figure 1).

Figure 1. Partial file system tree view in FTK Imager. (Source: Dell SecureWorks)
According to data available via FTK Imager, attributes of the folder highlighted in Figure 1 were set to “hidden” and “system.” Figure 2 is the Windows Explorer view of the folders for the C: volume after CTU analysts used FTK Imager to mount the image as a read-only volume. The attribute settings were clearly meant to hide the additional Program Files folder from view while the system was running.
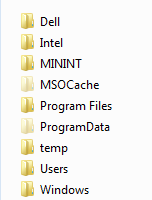
Figure 2. Root folders viewed in Windows Explorer. (Source: Dell SecureWorks)
CTU analysts extracted the master file table (MFT) from the image and parsed it with a custom Perl script, which displayed the names from the $FILE_NAME attributes of each record in hex dump format, prior to converting the names from their Unicode format.
The output of this parser revealed that the Program Files folder highlighted in Figure 1 had the “A0 00” character between the two words rather than a typical space (i.e., “20 00”).
CTU analysts manually examined the system user’s NTUSER.DAT Registry hive, verified values listed in the VirusRadar documentation, and examined the contents of the user’s Run key in the MiTeC Windows Registry Recovery (WRR) viewer (see Figure 3).
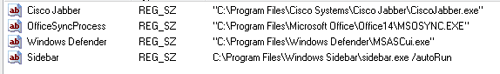
Figure 3. User’s Run key values viewed in MiTeC WRR. (Source: Dell SecureWorks)
CTU analysts also opened the user’s NTUSER.DAT hive in TZWorks yaru64.exe (version 1.17) (see Figure 4).
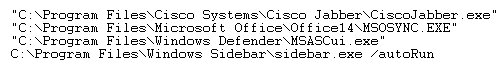
Figure 4. User’s Run key value data viewed in TZWorks yaru. (Source: Dell SecureWorks)
Figure 5 illustrates the contents of the user’s Run key when viewed in the Windows Registry Editor (RegEdit.exe).
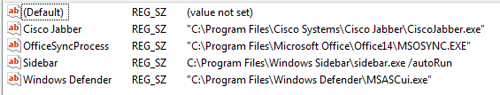
Figure 5. User’s Run key values and data viewed in RegEdit. (Source: Dell SecureWorks)
After running the user_run.pl RegRipper plugin against the NTUSER.DAT hive for the user, CTU analysts observed the following entry within the Run key:
Windows Defender: "C:Program FilesWindows DefenderMSASCui.exe"  
It is clear that the Unicode character and the attribute settings for the folder were used to hide the malware on the system. Not only would the folder remain hidden from view on a system with default configuration settings, but following the path in the user’s Run key would lead to the legitimate Microsoft Windows Defender executable, as that application was installed on the system. Threat actors took advantage of how graphical user interface (GUI) applications native to Windows systems, as well as applications popular with digital forensic analysts, display the “A0 00” character. As a result, they were able to hide the Vercuser worm, which infected the system with Poison Ivy.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

