In this post I will go over the latest botnet making the headlines. The "Finjan botnet" appears to be large and strikes fear into many. As an average computer user, should you be afraid of the botnet, or should you be scared of being compromised by a Trojan? How bad can one piece of malware be?
I would like to give credit to FireEye for trying to track down the Finjan Botnet that Finjan first reported on. Reading through the Finjan and FireEye write-ups, one is able to reconstruct the trail and also discover the path taken. We can see two major types of Trojans that play a part in this. We have the VBInject Trojan and the AutoIt Trojan.
There are two servers on the same network to which VBInject phones home: x.x.62.2 and x.x.21.186. The server at x.x.21.186 is no longer responsive and appears down at this time. The server at x.x.62.2 is still up and DNS still responds with that IP address for the domain name used in these attacks. If you actually try to browse to that domain though, you will not arrive at this server. As you can see from reading the FireEye article, the Trojan phones home to /ldr/loadlist.php. It downloads more malware from /ldr/dl/. One of the Trojans it downloads is AutoIt.
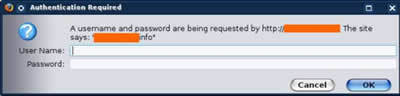
At the time of this post, if you navigate to /ldr/dl/ you are presented with a directory structure where the Trojans had been kept but now they are gone. If you navigate to the /ldr/ directory you are presented with a login screen. It says "A username and password are being requested by http://.x.x.62.2. The site says: Fun House-10001" Is this a login page to control a botnet?
Now AutoIt looks to phone home to one server with different domain names. I have found at least five different .info domains associated with one particular IP address in the 124.217.x.x range. If you look at /proxy.cfg off of one of those domains it pops up proxy information that says to have everything open and to use the OpenDNS name servers for DNS resolution. When attempting to do a fake phone home I was presented with the below response which is the same response that FireEye got back, however the domains have changed from one ten-letter nonsensical .com domain name to another.
Here is the fake phone home that FireEye posted.
GET /0/x.php?hid=531e237606675012bef96b4bef939b8d&mhid=bd1de70c62b17015b639adb2d30f0f0b&version=7&name=Codec_v.1004.1.exe&os=WIN_XP&_=262604330120091
User-Agent: AutoIt v3
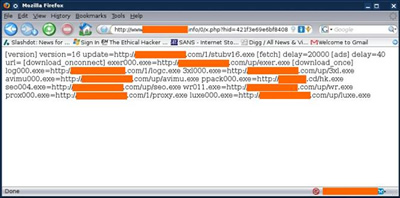
Notice that the user agent is listed as AutoIt. This is the AutoIt Trojan phoning home and the response is to download around 15 pieces of malware. FireEye posted the details of all of the malware in their blog post. Also I found an interesting script where AutoIt sends email through a Gmail account at http://pastie.org/pastes/385624/.
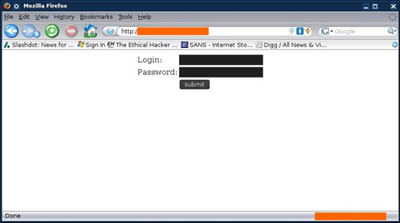
From my investigations into the various malware that use these domains I saw that anIP address in the 124.217.x.x range also pops up. This IP might serve the same function as the one in the 124.217.x.x range but I have not seen any domains for it. Both the ten-letter nonsensical .com domain names resolve to an IP address in the 94.75.x.x range. By using Google and one of the.com domain names in a search I found the whole directory listing for this malware server. When going to /_private/ it asks for a login page. A username and password are being requested by http://xxxxxxxxxx.com. The site says: "xxxxxxxxxx.info" The .info domain name also resolves to the same 94.75.x.x IP address.
Other notes in regards to the Finjan article. The Trojan that is partially redacted from their write-up is ZCHMIB.EXE and can be seen phoning home "66.90.x.x/bots /control.php?action=getMessage&version=test|16". An interesting thing about this Trojan is that it uses a site called Decaptcha to bypass captcha's for sites. The site also has a /bot/captcha/ directory to bypass Gmail captcha so it can send spam.
The other file that was partially redacted on the Finjan site looks to be SENEKA[random].DLL. This might be associated with the TDSS/Seneka rootkit. It performs a phone home to a server in the Ukraine "GET /seneka/engine/ld.php?affid=303350&action=2". This might be the server that Finjan was talking about in regard to the botnet. The IP addresses related to this are both on the same 78.26.x.x network.
The 78.26.x.x IP addresses are no longer in use. The IP addresses resolved to a domain name that now resolves to an IP address in the 94.75.x.x range which is already associated with yet another domain name. The original domain comes to a login page but new domain name does not. At this time there is no "0-day" binary that has been identified by Finjan or anyone else to be the botnet.
As you can see by following the trail, gone are the days where you have just one Trojan infection. When you have an infection it usually comes from what is known as a Trojan dropper or downloader that will then download many more Trojans that each serves a purpose. From the Finjan article, the botnet masters used their dropper to open up a botnet. From this botnet they were able to specify what Trojans to download for whatever purpose they wanted. Trojans now come in many flavors.
You have spamming Trojans, ransomware, keyloggers, ones that steal your personal data, and many more. The end goal is monetary gain. When you become infected today, it is best to just do a complete reformat of your machine instead of trying to recover it, because you really don't know how many infections you have. I have read plenty of articles where someone cleans their machine and they think everything is fine only to find more malware days to weeks later.
There is not any perfect AV tool; there is no perfect solution for any one problem. Your best defense is to practice what is called defense in depth and to only go to known websites. Don't open mail from people you don't know and be careful opening attachments from people that you do know. Update your OS and software regularly, including AV. Just having AV does not mean that you are protected; you also have to keep it updated.
- FireEye Blog : http://blog.fireeye.com/research/2009/04/botnetweb-part-ii.html
- Finjan article : http://www.finjan.com/MCRCblog.aspx?EntryId=2237
- Prevx shows ZCHMIB.EXE : http://www.prevx.com/filenames/1521641268775071064-X1/ZCHMIB.EXE.html
- ThreatExpert shows TDSS/Seneka activity : http://www.threatexpert.com/report.aspx?md5=5a1a6f4e83900e86c3e7dc62554318ac
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

