Speed is key in threat mitigation and incident response. In fact, average dwell times between initial access and ransomware payload delivery have dropped significantly to a median of just 24 hours. The longer a security breach goes undetected or unresolved, the greater the potential impact. Quick investigations help identify and contain security threats before they can spread within an organization. To speed up investigations, security analysts should take the following three approaches.
1. Gather additional evidence
To speed up an investigation, security analysts should gather documentation related to the investigation in one place. Additional context helps in understanding the scope and impact of a security incident as well as identifying the underlying cause to prevent future occurrences. To respond appropriately to a security incident, an analyst needs to understand the who, what, when, where, and how of the event. Important context elements include:
- Entities —Data that played a role in the incident, including usernames, hostnames, IP addresses, and files.
- Alerts — Notifications that are issued when a security system detects an unusual or potentially harmful activity that could indicate a threat.
- Events — Any observable occurrence in a system or network that has implications for the security posture of that environment.
- Agents — Devices affected by the alerts or events in the investigation.
- Searches — Search queries linked to the investigation.
- Attachments — File attachments related to the investigation.
- History — Audit log history for the investigation.
Contextual data helps in prioritizing which incidents require immediate attention and which can be deferred, ensuring that resources are allocated efficiently. Gathering additional evidence can also help distinguish between false positives and true security incidents, keeping the security team's efforts focused on genuine threats. Overall, this leads to more effective and efficient detection, analysis, response, and prevention of future threats.
2. Visualize the scope of the investigation
Analysts should map out the various investigation alerts, events, and actions based on the time each activity took place, so they can visualize the scope of the investigation. Graphs, charts, and diagrams can reveal patterns and correlations that might not be obvious from raw data. This can help in identifying the root cause, the extent of the compromise, and the methods used by the attackers.
Entity graphs, for example, are excellent for displaying complex relationships and interactions between different entities, such as users, IP addresses, devices, applications, and files. This can help analysts understand how different components are connected and how an attacker may have moved through the network. Entity graphs provide context around each entity, showing not just isolated events but how they relate to the broader environment. This context is crucial for determining the significance of each event within the scope of the investigation.
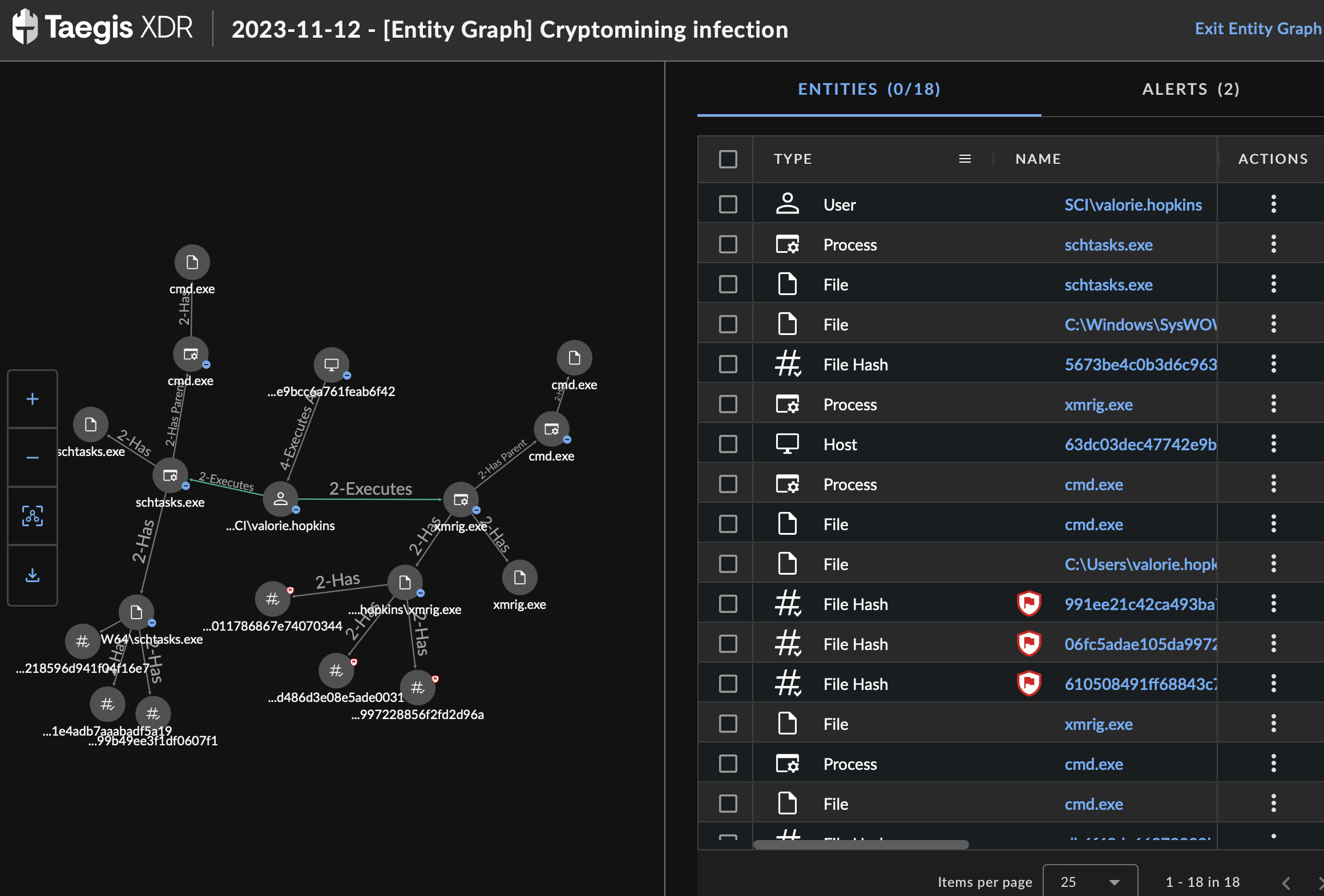
With the help of an entity graph, an analyst can:
- Visualize how entities that are part of the investigation are connected. The visual graph displays entity relationships, providing connections across different data sources.
- Gain additional insights about the entity, such as its properties, related alerts, related entities, and threat intelligence, if available.
- Understand the alerts and events that are part of that relationship.
Many entity graph tools allow analysts to interact with the data, such as zooming in on specific details, filtering out noise, or highlighting critical paths of an attack. This interactivity can lead to a more thorough and efficient investigation. By visualizing the entities and their interactions, analysts can more accurately assess the scope of an incident and its potential impact, which is essential for effective and fast response and remediation efforts.
3. Automate repetitive tasks
SecOps teams need to work efficiently despite the size and scale of the task at hand. To achieve this, security analysts need to automate time-consuming and repetitive manual work. Automation can significantly speed up security investigations by streamlining processes and allowing security professionals to focus on more complex and critical activities. Automated systems can use machine learning and other analytical techniques to identify patterns and anomalies that might indicate a security incident. This can be much faster than manual analysis, especially when dealing with large volumes of data. Automation may also help analysts gather and record the key findings of an investigation, automatically create and append alerts to investigations, and leverage automatic enrichment and response workflows.
Organizations should look for an open security platform that integrates with a wide range of security products across multiple point solutions, and support playbook creation, enrichment, automation, and response capabilities out of the box. Automated workflows can initiate responses to common types of security incidents, such as isolating infected systems, blocking malicious IP addresses, or revoking compromised user credentials. By automating manual tasks, organizations can reduce the time it takes to detect, investigate, and respond to security incidents, thereby minimizing the potential damage and improving overall security posture.
Accelerate Investigations with XDR
Cyber attackers are constantly evolving their tactics. Rapid investigations can help organizations stay ahead of attackers by quickly understanding and responding to new threats. Speeding up security investigations is crucial for limiting the damage caused by security incidents, maintaining stakeholder trust, and enabling the organization to quickly recover and learn from the events. Extended Detection and Response (XDR) is an advanced security solution that can significantly accelerate security investigations by providing a more comprehensive and efficient approach to threat detection and response. XDR provides rich contextual information about threats and reduces the time security analysts spend on manual tasks with automation.
Secureworks® Taegis™ XDR is a security platform designed to improve an organization's ability to detect, investigate, and respond to cybersecurity threats. The platform provides a single view of relevant security context and an entity graph for security analysts to visualize complex data and relationships during an investigation, which can lead to more effective detection, analysis, and response to security incidents. With a growing library of over 200 automated playbooks and integration connectors available out of the box, Taegis helps organizations scale their security operations by automating the most common and repetitive tasks — freeing your team to focus on mission-critical activities to protect your business. To learn more, request a demo of Taegis today.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
