After the initial entry into a targeted network environment, threat actors commonly run credential theft tools to acquire the usernames and passwords they need to access other more sensitive hosts. Executing credential theft tools requires administrative privileges, which a threat actor may not immediately have on the host they initially accessed. By using a privilege escalation exploit, threat actors can turn their unprivileged access into SYSTEM-level privileges that provide complete control over the host.
Privilege escalation exploits are typically not rated critical, so organizations may skip software patches that address these vulnerabilities for fear of disrupting business operation. Even if addressing privilege escalation vulnerabilities is a priority, applying patches in corporate environments can sometimes take days, weeks, or even months. These realities, combined with the number of publicly available exploits, means threat actors do not need to exploit zero-day privilege escalation vulnerabilities to steal credentials and move laterally inside an environment. In the following case studies,SecureWorks Counter Threat Unit™ (CTU) researchers used the Advanced Endpoint Threat Detection Red Cloak, an endpoint security technology, to detect threat actor behavior that would otherwise have likely gone unnoticed.
Case study 1
During a targeted threat response engagement, CTU researchers observed a threat actor re-enter an environment, evaluate a Windows Server 2008 patch level, and deploy an appropriate privilege escalation exploit within three minutes. In the next 15 minutes, the threat actor had installed multiple back doors across the environment and obtained the credentials of hundreds of users.
The threat actor achieved privilege escalation by first running the built-in Windows command line tool systeminfo, which lists the security patches installed on the host. It revealed that the latest security patches, released just 10 hours earlier, had not been installed. The threat actor then proceeded to upload and execute a tool named reaa.exe that exploited CVE-2015-1701 to gain SYSTEM-level privileges on the host.
CVE-2015-1701, a vulnerability in Windows kernel-mode drivers that allows local users to gain privileges via a crafted application, was patched as part of MS15-051. As shown in Figure 1, the described activity occurred around 03:00 UTC on May 13, 2015, approximately ten hours after Microsoft released MS15-051 and a researcher published proof-of-concept code demonstrating how this vulnerability could be exploited.

Figure 1. Threat actor exploiting CVE-2015-1701 using a tool named reaa.exe to escalate privileges. Sensitive data has been redacted. (Source: Dell SecureWorks)
Case study 2
During another engagement, CTU researchers observed a threat actor escalate from an unprivileged user to SYSTEM-level privileges on a compromised Citrix server. The threat actor, who entered the environment through a single-factor remote access solution, ran the whoami Windows command line tool to display the name, group, and privilege information of the logged-on user. The threat actor then proceeded to run the help.exe privilege escalation tool with the parameter “cmd” (no quotes) to create a command shell with SYSTEM-level privileges (see Figure 2). These elevated privileges were then used to dump credentials, allowing the threat actor to move laterally to other hosts in the environment.
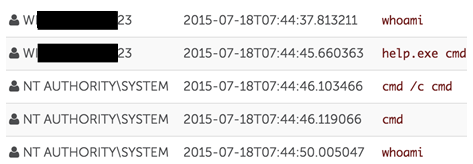
Figure 2. Threat actor exploiting CVE-2015-2387 using help.exe to escalate privileges. Sensitive data has been redacted. (Source: Dell SecureWorks)
The help.exe tool exploits CVE-2015-2387, a vulnerability in a Windows font driver, to gain SYSTEM-level privileges. This vulnerability was addressed in MS15-077, released on July 14, 2015. Public exploit code for this vulnerability became available as part of the Hacking Team leaks on July 5, 2015, leaving a gap of approximately 10 days between public disclosure and when the patch became available. The help.exe binary was compiled on July 8, 2015, indicating that threat actors quickly leveraged this public disclosure to exploit the vulnerability before a patch was available.
Conclusion
After obtaining SYSTEM-level privileges, the threat actors moved laterally to other hosts to dump credentials. Because Red Cloak was installed on all of these hosts, it recorded and immediately detected the entire intrusion, allowing administrators to evict the threat actors from the environment before they could achieve their objective.
These case studies illustrate how quickly threat actors can exploit a published or leaked vulnerability, even without zero-day exploitation. Preventative measures like software patch management are critical, but just as important are detection and response capabilities for situations where prevention is not feasible or timely enough.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

