One of a threat actor's first objectives after initially entering a target network environment is to gain the necessary privileges to access hosts containing the desired information.
Threat actors commonly use a credential theft tool that exploits weaknesses in Windows to obtain the credentials of users that recently accessed a system. Depending on the configuration of the system, these stolen credentials may be in the form of plaintext passwords, password hashes, or Kerberos tokens. Typically, threat actors continue to use the credential theft tool on accessible hosts until they can access domain controllers and steal the credentials of every user in the domain. Endpoint detection and response technologies like Red Cloak can detect the use of credential theft tools so network defenders can stop intruders before they gain full access.
Case study
During an incident response engagement, Dell SecureWorks Counter Threat Unit™ (CTU) researchers observed that threat actors gained access to an environment through a compromised externally facing webserver. After stealing credentials from the web server, the threat actors re-entered the environment through the corporate VPN and began using a combination of Remote Desktop Protocol (RDP) and PsExec to remotely control systems.
Over the course of three days, the threat actors connected to and dumped credentials from a total of 10 systems using the process shown in Figure 1.
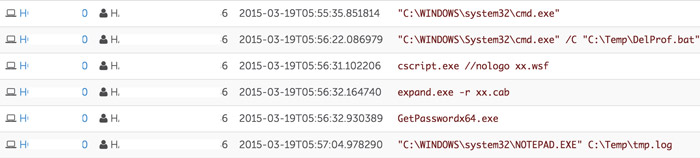
Figure 1. Threat actors dumping credentials. (Source: Dell SecureWorks)
After connecting to a targeted system via RDP, the threat actors copied and executed the credential theft tool on the system using a custom tool. The tool, which the CTU research team named Expandito, encodes a binary file as text and produces a batch file that an adversary can copy, paste, and run on target systems by taking advantage of the shared clipboard.
The credential theft tool of choice for the threat actors was GetPassword, a program based on mimikatz that dumped plaintext passwords from WDigest. By acquiring the passwords in plaintext, the threat actors could immediately use the stolen credentials to connect to other systems via RDP, as they did not have to brute-force hashes.
After three days and lateral movement to 25 different systems, the threat actors managed to gain administrative access to a domain controller. On the domain controller, they used the GSecDump tool to dump the credentials of every user on the domain. Figure 2 shows the threat actors copying tools to the system using Expandito, and then using PsExec (process.exe) to run GSecDump (resuly.exe). The threat actors then exfiltrated the resulting credentials for future use.
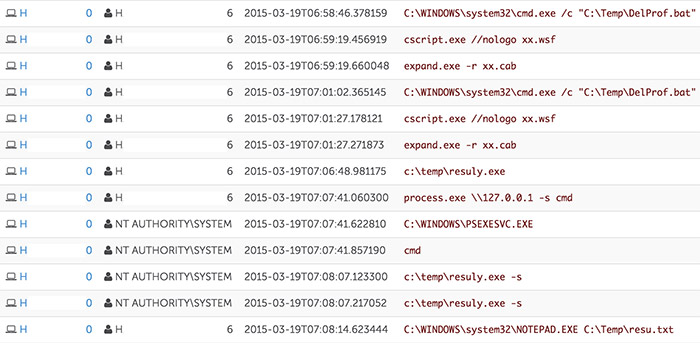
Figure 2. Using GSecDump to dump credentials from domain controller. (Source: Dell SecureWorks)
Before the threat actors could use the newly obtained credentials, the network administrators took remediation actions and evicted the threat actors from the environment. In addition to removing the web shells, patching the exploited vulnerability, and resetting the credentials of every user on the domain, the network administrators set a group policy to disable the WDigest authentication method domain-wide.
The threat actors were not deterred, and after waiting more than a week re-entered the environment by exploiting a different web server. Similar to the previous intrusion, the threat actors attempted to dump credentials using the GetPassword tool. However, since WDigest had been disabled, this tool no longer functioned as expected. As shown in Figure 3, the threat actors repeatedly ran the GetPassword tool (Macfeee.exe) without success.
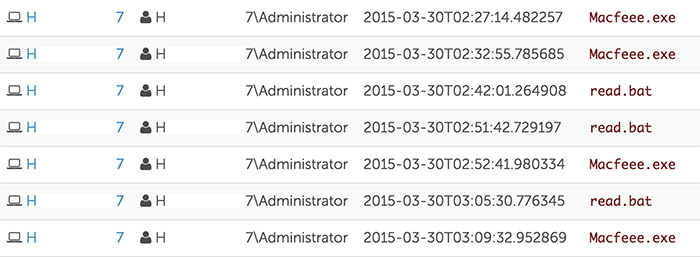
Figure 3. Attempts to use GetPassword. (Source: Dell SecureWorks)
Approximately two hours later, the threat actors resorted to using the SysInternals tool ProcDump to dump the memory of the lsass.exe process to perform an offline attack against the credentials. Figure 4 shows the execution of ProcDump (Macfeee.exe) and the preparation of the memory dump for exfiltration.
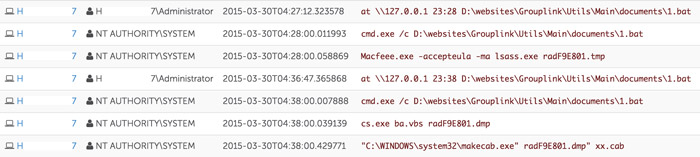
Figure 4. Use of SysInternals ProcDump and packaging for exfiltration. (Source: Dell SecureWorks)
Due to the delay imposed on both collecting and using these credentials, the threat actors were only able to dump credentials on one other host before being evicted from the network. Additionally, because the threat actors used their backup access vector, returning a third time (as expected of a persistent actor) would require an alternative means of entry.
A lack of two-factor authentication on the target's Citrix applications allowed the threat actors to again re-enter the environment by brute-forcing the credentials of a user who had simply incremented the number at the end of their password by one for each reset. Figure 5 shows the threat actors using PsExec to gain a system-level shell and (after some difficulty) using mimikatz to dump credentials from the system.
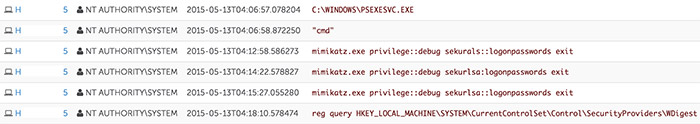
Figure 5. Use of mimikatz and PsExec to dump WDigest registry value. (Source: Dell SecureWorks)
Because WDigest was disabled, the threat actors could not recover plaintext passwords using mimikatz and even queried the value of the WDigest registry value to confirm the obstacle. The lack of plaintext passwords limited the threat actors' speed moving laterally through the environment and resulted in their eviction a few hours later.
Conclusion
This case study illustrates how persistent threat actors can escalate their credential theft tactics to overcome roadblocks imposed by network defenders. Despite the multiple re-entries into the environment, the intrusions were always quickly contained. While it is possible to limit the impact of credential theft, it is not possible to prevent it entirely. For this reason, organizations should implement a detection and response capability to evict intruders from the environment early in the intrusion, well before they can achieve objectives such as data exfiltration.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.