Summary
The Dell SecureWorks Counter Threat Unit™ (CTU) research team has become aware of an ongoing spam campaign abusing various .gov web properties to lure recipients to a home business scam. As part of the campaign, victims receive nonsensical emails with a link to one of several URL shorteners. The attackers use 1.usa.gov short links in many of the emails, though other shortening services and websites have been used in the same way.
Analysis
The 1.usa.gov short URL service is run by the U.S. government, in partnership with bitly.com. When users submit a long URL to bitly that resides on a .gov or .mil top-level domain (TLD), they are given short links that use the 1.usa.gov domain rather than the bitly domain. This distinction is intended to make it "even easier for people to know when a short URL will direct them to a trustworthy official U.S. government site" [1]. However, malicious actors can abuse URL shorteners in combination with other attack techniques to direct users to malicious websites.
Many of the email messages involved in the ongoing spam campaign include links to 1.usa.gov short URLs. Evidence suggests that each short link is used in only a small number of messages before a new short link is created. This step limits the effectiveness of blacklisting or disabling any particular link.
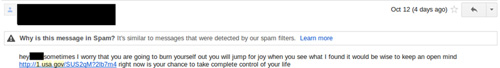
Figure 1. Sample spam message. (Source: Dell SecureWorks)
The short links expand to long links, which abuse open redirects on a number of .gov properties. CTU research indicates that the attackers are not targeting .gov sites specifically, but rather are looking for servers that expose a vulnerable version of DotNetNuke’s LinkClick.aspx. By exploiting an open-redirect vulnerability in this .aspx file, the attacker can direct traffic to a non-.gov site under his control, while exposing only a 1.usa.gov short link in the initial message.
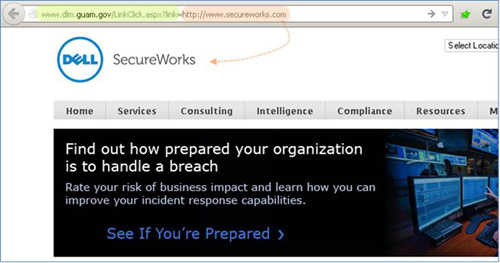
Figure 2. Example of open redirect use. (Source: Dell SecureWorks)
Figure 3 shows the domains hosting open redirects that have been abused as of the time of this publication.
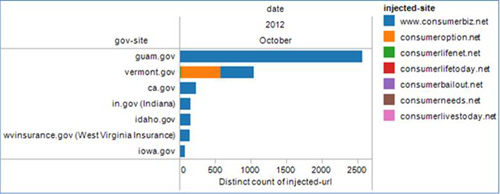
Figure 3. Number of injected sites abusing each .gov redirector. (Source: Dell SecureWorks)
Because 1.usa.gov provides real-time and historical logs of its click data [2], CTU researchers were able to effectively monitor the number of clicks, as well as the HTTP referer and victim User-Agent. The data suggests that email spam is the primary method for distributing the short links.
Overall use of open redirects on .gov websites has significantly increased since October 1, 2012, with destinations in the .net TLD accounting for the vast majority of instances (see Figure 4).
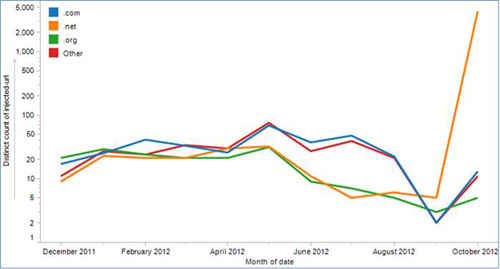
Figure 4. Usage of open redirects by TLD of landing page. (Source: Dell SecureWorks)
After victims are redirected through both the 1.usa.gov short link and the vulnerable .gov site, they are directed to one of the domains used in the scam. The following domains are being used at the time of this publication:
- consumerbailout.net
- consumerlifetoday.net
- consumeroption.net
- consumerbiz.net
- consumerlifenet.net
- consumerneeds.net
- workforprofit.net
All of these domains resolve to a small number of IPs:
- 178.208.138.229 is registered to comcor.ru, located in Moscow, Russia
- 70.39.147.119 is registered to InMotion Hosting Inc, located in the U.S.
The malicious websites are designed to look like a CNBC news article (see Figure 5). Much of the page content is from legitimate CNBC.com servers.
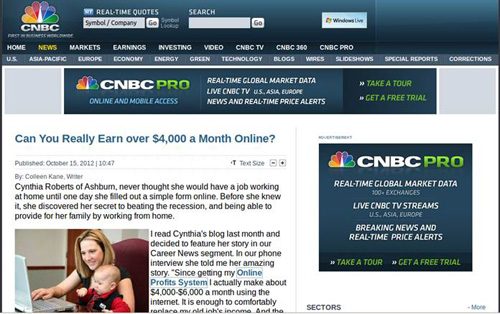
Figure 5. Fake CNBC news article. (Dell SecureWorks)
Several links on the website direct to another scam website, www.cash-online-forever.com. This website is hosted on 80.82.69.180, registered to Ecatel LTD in Amsterdam, Netherlands.

Figure 6. Cash-online-forever.com scam site. (Dell SecureWorks)
Despite the relatively unsophisticated lure, the click-through rate for the 1.usa.gov short links has been significant (see Figure 7).
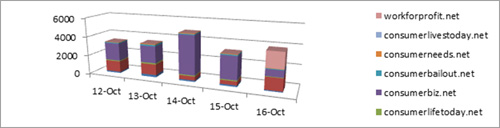
Figure 7. Number of clicks to top landing domains between October 12 and October 16, 2012. (Source: Dell SecureWorks)
While it seems the perpetrators are not targeting .gov sites specifically and are not using the government as a lure, the ability to generate short .gov links that lead users to malicious domains is concerning. If combined with a government-focused message, such as the common tax season phishing emails [3], this spam could lure even savvy users. Using open .gov redirects in phishing scams has precedent [4], and the availability of 1.usa.gov short links can be leveraged to make less suspicious URLs.
Conclusion
Users should exercise caution when dealing with unsolicited emails, especially if they include short links. To preview the 1.usa.gov short link page and see information such as the long URL, users can copy and paste the short link into the address bar of a browser window and append the "+" character. For example, http://1.usa.gov/xxxx becomes http://1.usa.gov/xxxx+. If the short link contains a "?", this character and anything following it must be removed before appending the "+". The long URL can then be inspected for any signs of redirection.
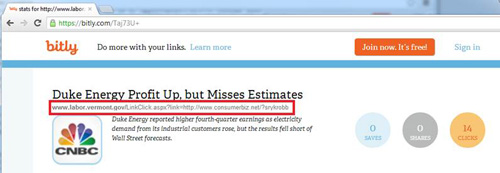
Figure 8. Preview of malicious short link. (Source: Dell SecureWorks)
Despite the best intentions, 1.usa.gov short links seem to be ineffective at ensuring the ultimate destinations of the URLs are trustworthy government websites.
References
[1] Go.USA.gov team. "Introducing 1.USA.gov URLs." March 9, 2011. http://go.usa.gov/node/15
[2] "1.USA.gov Data." October 12, 2012. http://www.usa.gov/About/developer-resources/1usagov.shtml
[3] Dell SecureWorks Counter Threat Unit research team. "Tax Season Presents Opportunities for Scammers." February 3, 2008. https://www.secureworks.com/blog/research-21001
[4] Miller, Rich. "Phishers Exploit Open Redirect on U.S. Government Site." December 1, 2005. http://news.netcraft.com/archives/2005/12/01/phishers_exploit_open_redirect_on_us_government_site.html
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

