Recently, programmer Ruben Unteregger released the source code for a Trojan that allows an attacker to listen in on a victim's Skype conversations [1]. For approximately seven years, Unteregger has worked as a software engineer for ERA IT Solutions AG where he developed the trojan. Skype traffic is encrypted using a 256-bit AES block cipher [2], the kind approved by the US Government to protect "TOP SECRET" information.
The Megapanzer trojan variant was released as free software by Unteregger under theGNU General Public License (GPL). The trojan works by injecting a thread into the Skype process and hooking several API calls. While Unteregger's trojan does not break Skype's encryption, this method allows an attacker to bypass it as PCM audio data is captured after being decrypted and converted to MP3 digital audio files. The MP3 recordings of the Skype call may then be uploaded to an attacker-controlled server [3].
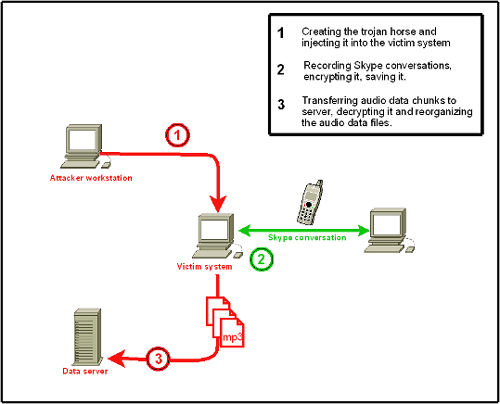
Fig. 1: Skype Trojan Overview [1]
Governments around the world worry about the use of Skype for nefarious purposes, as the service may be used to place calls that cannot be traced or monitored using contemporary lawful interception techniques. The NSA has reportedly offered billions of dollars to anyone who can "offer reliable eavesdropping on Skype IM and voice traffic" [4]. Even though no backdoors or weaknesses in Skype's encryption scheme have been disclosed, this trojan demonstrates that an attacker doesn't need to exploit a flaw in Skype to eavesdrop on Skype communications. This is essentially a variation on the Man-in-the-Browser (MitB) techniques used by malware to steal information and commit financial fraud.
It seems novel that a programmer would release a trojan as free and open source software, however Unteregger stated in an interview that he wanted the code to be available to anyone who wanted to learn or add additional functionality [5]. In addition, since the code is published, it will be detected and blocked by most AV products. The trojan is currently detected by AV as Trojan.Peskyspy.
Fig. 2: Skype Trojan Source Snippet
After becoming infected, the trojan will attempt to disable the following firewalls (if they are present):
- Outpost firewall
- McAfee firewall
- ZoneAlarm firewall
- BitDefender firewall
- F-Secure firewall
- Kerio firewall
- AVG firewall
- Webroot firewall
A backdoor will be created, allowing an attacker to communicate with the victim's machine. Once connected, an attacker may upload captured MP3 files, update the trojan, or remove the trojan from the machine. The released trojan does not contain a mechanism to spread itself, and has not been weaponized. The CTU believes that we may see variations of this trojan in the future and as always recommend keeping gateway and host AV signatures up to date and the use of a defense in depth approach to security.
References:
- http://www.megapanzer.com/source-code/
- https://support.skype.com/faq/FA145/What-type-of-encryption-is-used
- http://blogs.zdnet.com/security/?p=4133
- http://www.theregister.co.uk/2009/02/12/nsa_offers_billions_for_skype_pwnage/
- http://www.megapanzer.com/2009/08/25/interview-on-gulli-com-about-the-skype-trojan-and-trojans-in-general-english/
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

