Last week I attended the RSA Conference, the largest information security conference in the world. Alan Turing was the conference mascot and the question "what would Turing do?" was frequently asked.
Turing was a brilliant computer scientist, considered the father of modern computing, capable of seeing the math in everything and envisioned an age when machines would be as intelligent as humans. He devised what is known as the Turing test, used to gauge the capabilities of artificial intelligence. We've all taken Turing tests, they're used to guarantee that a human is on the other end of an application or communication stream. For example when you register for a Gmail account you see an image that is obfuscated in a way that only humans can decipher, this is called a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart). Therefore if the text in the image is read correctly entered there must be a human on the other screen reading it. This is an example of a Turing test.
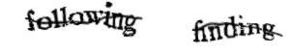
For more information http://en.wikipedia.org/wiki/Captcha
The theme of the keynote presenters seemed to be a call for information-centric security. I think this is appropriate considering they were presenting at a conference hosted by a company that was founded by (and named after) cryptographers who invented the most widely used asymmetric encryption algorithm (RSA) today. Cryptography has always served the purpose of two of the three premises of the information security triad, confidentiality and integrity (the third being availability which, it could be argued, cryptography inhibits). The need to protect information should not obviate the need to continue to protect the infrastructure. We are dependent on the infrastructure for the storage and transit of information and need to protect it.
Compared to last year there appeared to be fewer Network Admission/Access Control (NAC) vendors, fewer Data Loss Prevention (DLP) vendors and fewer Network Behavior Analysis (NBA) vendors. The newest technology based on an old idea is application whitelisting. Application whitelisting changes the logic used by many endpoint security solutions which today allow everything and deny the known bad. Instead application whitelisting denies everything and allows the known good. In an age where more malware is created than legitimate software it makes sense to invert the logic.
Turing was a brilliant computer scientist, considered the father of modern computing, capable of seeing the math in everything and envisioned an age when machines would be as intelligent as humans. He devised what is known as the Turing test, used to gauge the capabilities of artificial intelligence. We've all taken Turing tests, they're used to guarantee that a human is on the other end of an application or communication stream. For example when you register for a Gmail account you see an image that is obfuscated in a way that only humans can decipher, this is called a CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart). Therefore if the text in the image is read correctly entered there must be a human on the other screen reading it. This is an example of a Turing test.
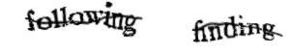
For more information http://en.wikipedia.org/wiki/Captcha
The theme of the keynote presenters seemed to be a call for information-centric security. I think this is appropriate considering they were presenting at a conference hosted by a company that was founded by (and named after) cryptographers who invented the most widely used asymmetric encryption algorithm (RSA) today. Cryptography has always served the purpose of two of the three premises of the information security triad, confidentiality and integrity (the third being availability which, it could be argued, cryptography inhibits). The need to protect information should not obviate the need to continue to protect the infrastructure. We are dependent on the infrastructure for the storage and transit of information and need to protect it.
Compared to last year there appeared to be fewer Network Admission/Access Control (NAC) vendors, fewer Data Loss Prevention (DLP) vendors and fewer Network Behavior Analysis (NBA) vendors. The newest technology based on an old idea is application whitelisting. Application whitelisting changes the logic used by many endpoint security solutions which today allow everything and deny the known bad. Instead application whitelisting denies everything and allows the known good. In an age where more malware is created than legitimate software it makes sense to invert the logic.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

