We've done a lot of analysis on the Ozdok (aka Mega-D) trojan botnet in the past. Even now it is one of the biggest botnets of 2009, despite having its primary sponsor shut down by court order in October 2008.
Recently, with the help of Spamhaus, we were given access to files collected from yet another Ozdok/Mega-D command-and-control server. Although we have seen the controller code before, it was surprising to learn that this variant was collecting screenshots from its victims' computers, and that thousands of them were stored on the control server. Grabbing screenshots isn't new for backdoor trojans, but it's the first time we've seen this functionality in a spambot.

What can be seen in these screenshots is mostly what you'd expect: people checking up on social networking pages, looking at videos, reading their email, browsing porn sites, and a fair number running anti-spyware tools (not that they helped at all). One might ask, "why would a botnet spammer be interested in people's desktop screenshots?" It could be for a couple of different reasons.
One reason could be to search for interesting machines in order to further probe them for financial credentials or intellectual property. This theory could be supported by the fact that we found a WinVNC server binary on the controller that could be pushed to remote machines, giving the spammer full access and control over the computer desktop.
Another reason might be self-preservation: Many malware researchers utilize virtual machines like VMware in order to do analysis of malicious software. Lately we've seen a trend of malware authors switching from detecting VMs in the client code to detecting them server-side. For instance, the Pushdo trojan sends the serial number of the computer's hard drive back to the controller. VMware has a very recognizable serial number pattern, so it is trivial for the controller to be programmed to give different instructions to these bots. Other threats, like the Gimmiv worm, send the MAC address of the infected machine's Ethernet card to the controller. This also is a good way to differentiate between virtual and real machines.
So, it could be that the Ozdok spammer is trying to figure out what IP addresses might be attempting to join the botnet in order to spy on it, and is using screenshots to help make that determination. It would be a manual process, but it didn't take us very long looking through the screenshots to pick out these four images, all showing advanced auto-analysis tools being used on the Ozdok sample as it connects to its control server:
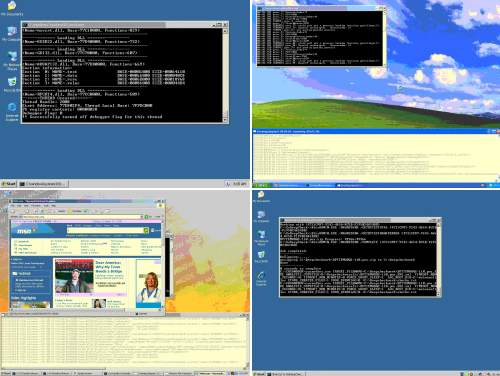
Note to researchers: If you are doing automated analysis, there's no reason to have a window displaying what you are doing. Hide your tools better, and try not to have your honeypot desktop look like a brand-new install of Windows!
Also, a note to the gentleman searching for images of nude preteen girls: You can run all the anti-spyware tools you can find, and employ the best anonymity tools in your web browser. It's not going to help you if you get infected with an advanced trojan like Ozdok/Mega-D or one of the many others that allow hackers to take screenshots of your computer desktop. Don't worry though, you probably won't need a computer in the near term, as we've notified the authorities of your name and location (which you conveniently provided in a series of screenshots).
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

