The SecureWorks CTU™ is closely monitoring a 0-day vulnerability in multiple Microsoft Windows operating system releases. The vulnerability lies in how Windows handles hcp:// URLs, used to access help documents. An attacker may create a malicious hcp:// URL and distribute it to victims via an HTML web page, e-mail message, document, or a variety of other attack vectors. Successful exploitation of this vulnerability may allow an attacker to execute arbitrary commands, which may result in total system compromise. This vulnerability is an excellent example of a blended threat: leveraging several vulnerabilities of a lesser severity to accomplish an attack of greater severity.
The original discloser reports that Windows XP and Windows Server 2003 using Internet Explorer 8, Mozilla Firefox, and Google Chrome are affected. Microsoft has reported that Windows Vista, Windows 7, Windows Server 2008, and Windows Server 2008 R2 are not vulnerable to this attack. Microsoft has released Microsoft Security Advisory 2219475 discussing the details of this vulnerability.
When invoked using an hcp:// URL, Windows Help Center uses a whitelist to only allow certain help documents and parameters. An error in the MPC::HTML::UrlUnescapeW() function bypasses this whitelist, permitting access to any help documents on a system. Combined with a known DOM-based (Document Object Model) cross-site scripting (XSS) vulnerability in sysinfomain.htm, hcp:// links may be created that launch arbitrary commands when visited on a vulnerable computer, although a warning dialog box displays to the victim before the command can launch.
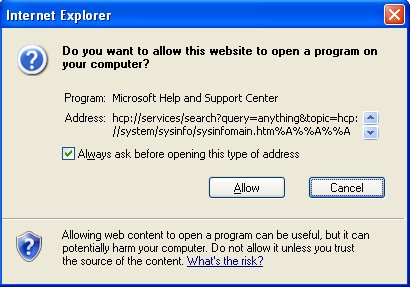
Figure 1. Warning dialog to allow command execution.

Figure 2. Successful execution of calc.exe.
The warning dialog may be suppressed when the exploit is placed in an IFRAME in an .ASX file containing an HtmlView element. This approach is advantageous to a potential adversary, because viewing a malicious web page or e-mail may be all that is required to successfully exploit the vulnerability. Other methods of suppressing the warning dialog box may also exist. Proof of concept code is available at the following site:
http://seclists.org/fulldisclosure/2010/Jun/205
An unofficial hotfix has been released by the original discloser; however this patch may be bypassed as it does not properly correct the underlying vulnerability. At this time, there is no official patch available. Disabling the HCP protocol handler is the recommended mitigation, but doing so will impact some legitimate Windows Help Center functionality. This mitigation may also be pushed to multiple clients using Group Policy.
Before modifying the registry, the CTU recommends you export a copy of the HCP registry hive so it may be restored later if needed.
- Click Start, and then click Run.
- Type regedit, and then click OK.
- Expand HKEY_CLASSES_ROOT, and then highlight the HCP key.
- Right-click the HCP key, and then click Export.
- Export the registry hive to a local file.
- Right-click the HCP key, and then click Delete.
References:
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

