Botnet operators often use malicious software to perform click fraud, which involves silently clicking online advertisements for financial gain.
Click fraud impacts end users by consuming computing resources and bandwidth, and affects online advertisers who pay for a service they do not receive. It also allows threat actors to download and install additional malicious software.
Dell SecureWorks Counter Threat Unit™ (CTU) researchers, in collaboration with researchers from Palo Alto Networks’ Unit 42, analyzed variants of the Ramdo (also called Redyms) click-fraud malware. Palo Alto Networks has also published a blog post about the joint findings. Documented by Microsoft in 2014, Ramdo continues to evolve to evade host-based and network-based detection. Its capabilities include traffic encryption and novel virtualization detection.
Distribution
Threat actors primarily use exploit kits to distribute Ramdo. Dell SecureWorks CTU researchers observed Ramdo variants installed by the Angler, RIG, Blackhole, and Magnitude exploit kits.
The malware is also distributed through spam messages that convince victims to install fake versions of Adobe Flash Player. The spam messages direct users to a URL that downloads a Ramdo variant. The malware advertised in these spam messages typically has the filename “flashplayer20_ga_install.exe”.
Figure 1 shows the number of Ramdo files submitted to the Palo Alto Networks AutoFocus platform between September 2013 and February 2016. More frequent submissions occurred between February and May 2014, and between May and September 2015.
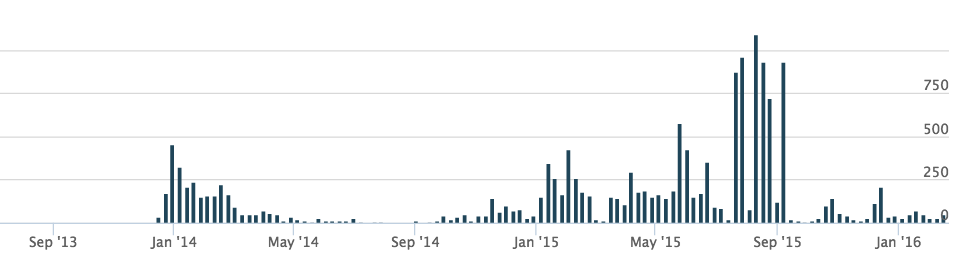
Figure 1. Ramdo malware samples submitted to Palo Alto Networks’ AutoFocus platform. (Source: Palo Alto Networks)
Dell SecureWorks iSensors detected similar trends on client networks (see Figure 2). The increased activity around January 2014 and Spring 2015 correlates with spikes observed by Palo Alto Networks. These results indicate that Ramdo is actively maintained and distributed by its operators.
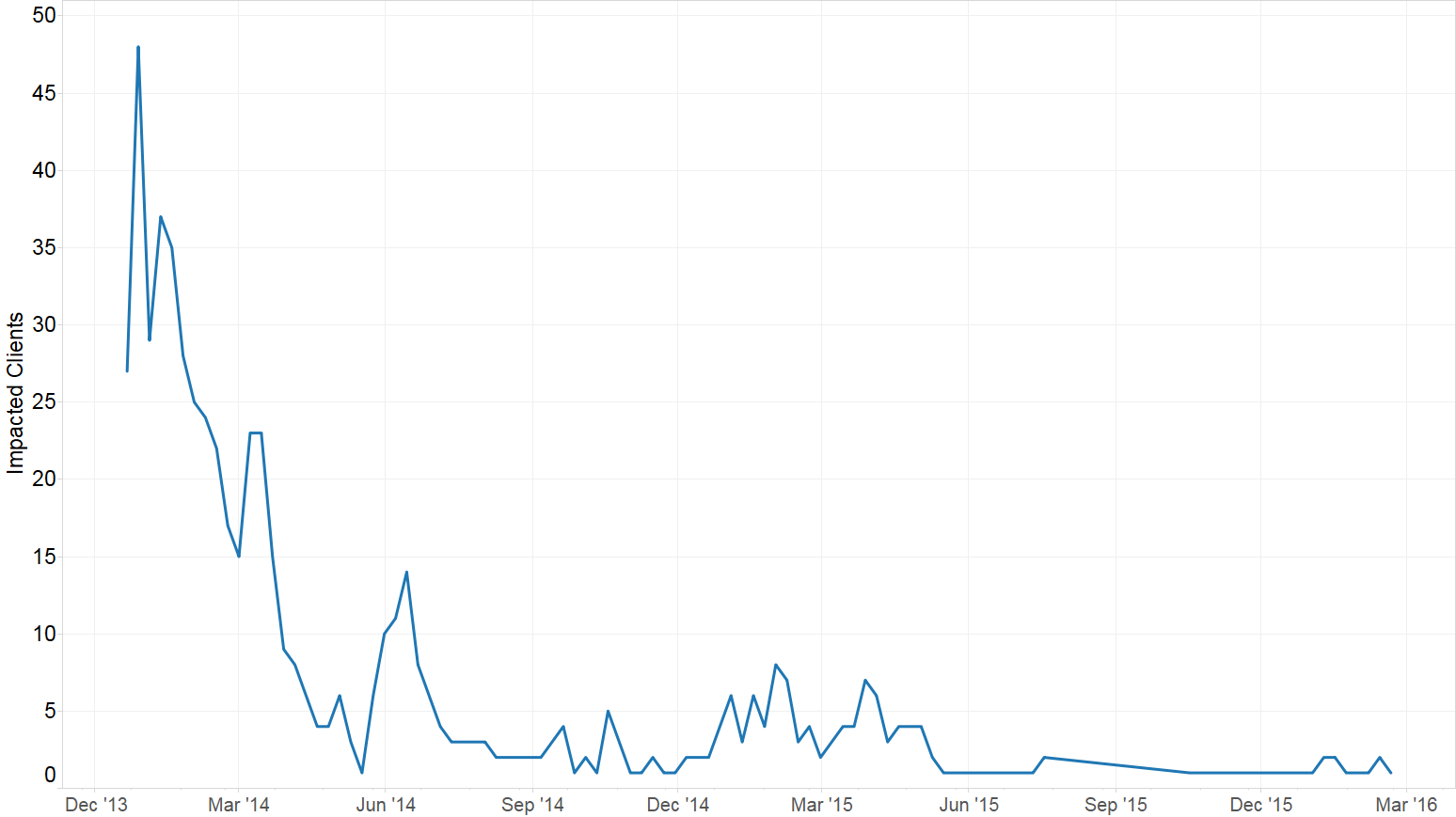
Figure 2. Ramdo activity affecting Dell SecureWorks iSensor clients.
Operation
After Ramdo is executed on a system, it tries to identify if the system is using virtualization or if it is executing in a sandbox environment, which may indicate that it is being analyzed by a security researcher. If the malware does not find evidence of these platforms, it copies itself to %APPDATA%\Microsoft\bstack.dll. Ramdo also adds a registry entry to load and execute the bstack.dll file when an infected system is started.
The malware then creates a new, legitimate, Windows process based on what programs are already running on the system, and injects malicious DLL code into the process. The injected code contacts the malware’s command and control (C2) infrastructure and downloads an archive containing a copy of the Chrome Extended Framework. Without the victim’s knowledge, the malware uses this self-contained browser to navigate to advertisements via a fake search portal (see Figure 3). When Ramdo clicks the “search” button (without entering a search term), the portal displays a link to a sponsored advertisement. By clicking the link from the search portal, the malware manipulates website analytics so advertisers believe the link was followed by a user searching for specific results rather than by an automated tool. Passive DNS information reveals that some of the search portals have been active since at least 2011.
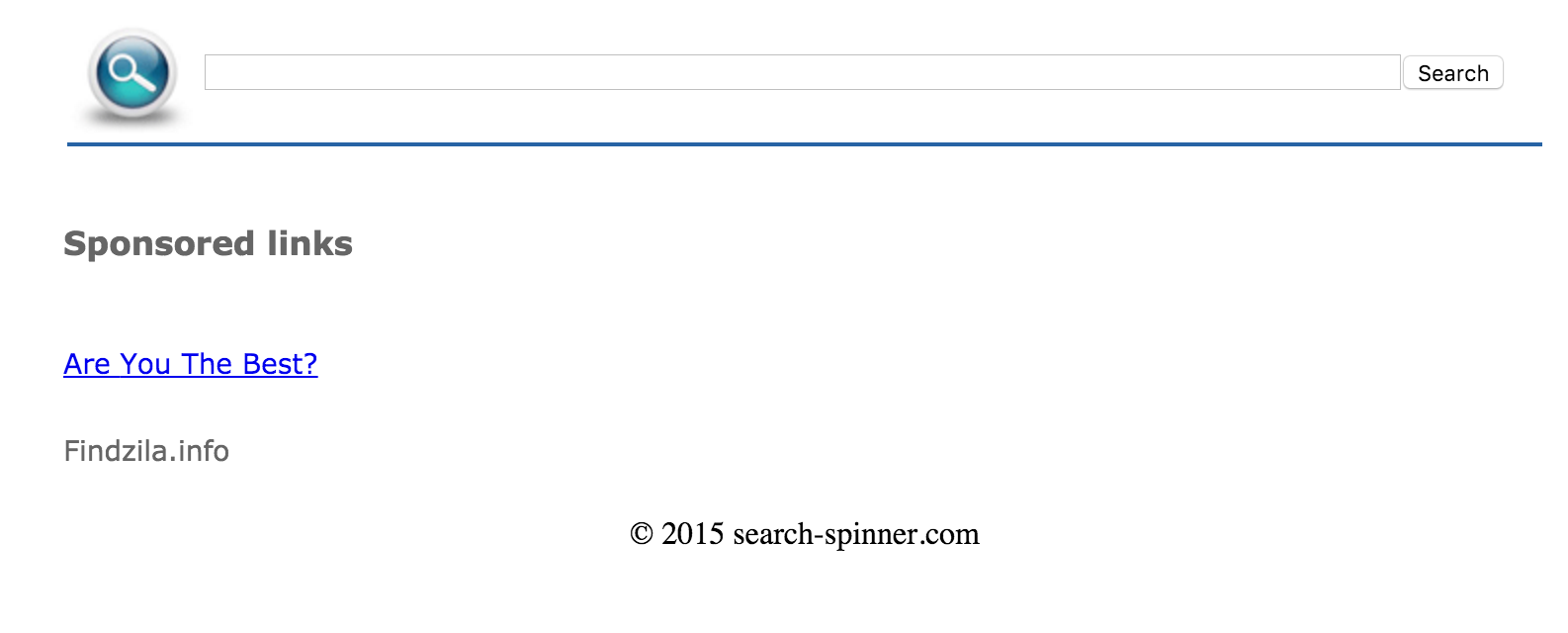
Figure 3. Fake search portal. (Source: Dell SecureWorks)
Virtualization Detection
The Ramdo malware family is evolving to evade virtualized environments. It uses the “cpuid” instruction to detect if the processor configuration is running in hypervisor mode (see Figure 4). If so, the malware assumes it is running in a virtualized environment and sets the EAX value to 1, directing the cpuid instruction to return the processor information and feature bits. The malware checks the 31st bit returned in ECX, which is set to 0 if the processor is running on hardware and 1 if running on a hypervisor.
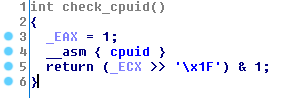
Figure 4. Use of cpuid to detect hypervisor mode. (Source: Dell SecureWorks)
Ramdo sets a flag in its memory if it detects that it is executing inside a virtualized environment. This flag is sometimes used to compute the seed that is used in the dynamic generation algorithm (DGA) for C2 domain names and is communicated to the malware’s C2 server.
Sandbox Detection
Ramdo also tries to identify if it is executing in a sandbox environment. Ramdo enumerates the names of the hard drives attached to the infected system. If a device contains one of the following substrings, the malware concludes that it is executing in a virtualized environment:
- VMWARE
- VBOX
- VIRTUAL
If one of the following three substrings is in the executable’s file path, then the malware concludes that it is executing in a virtualized environment:
- \sand-box\
- \cwsandbox\
- \sandbox\
If the malware determines that it is executing inside a virtualized environment, it enters an infinite loop and does not reveal its full behavior.
Network Communications
Ramdo variants released after June 2015 use the HTTPS protocol to communicate with their C2 servers. Rather than using hard-coded C2 server addresses, the malware generates domain names using a DGA with hard-coded constants. Except for some variations in the constants, the algorithm has not changed much since 2013. These characteristics make the malware harder to detect and block from a network defense perspective.
Geographic Distribution
Sinkholing Ramdo C2 domain names reveals the geographic distribution of infected systems. Figure 5 maps the distribution of unique IP addresses that contacted sinkholed domains. The United States, Germany, Australia, and Japan had the most infections.
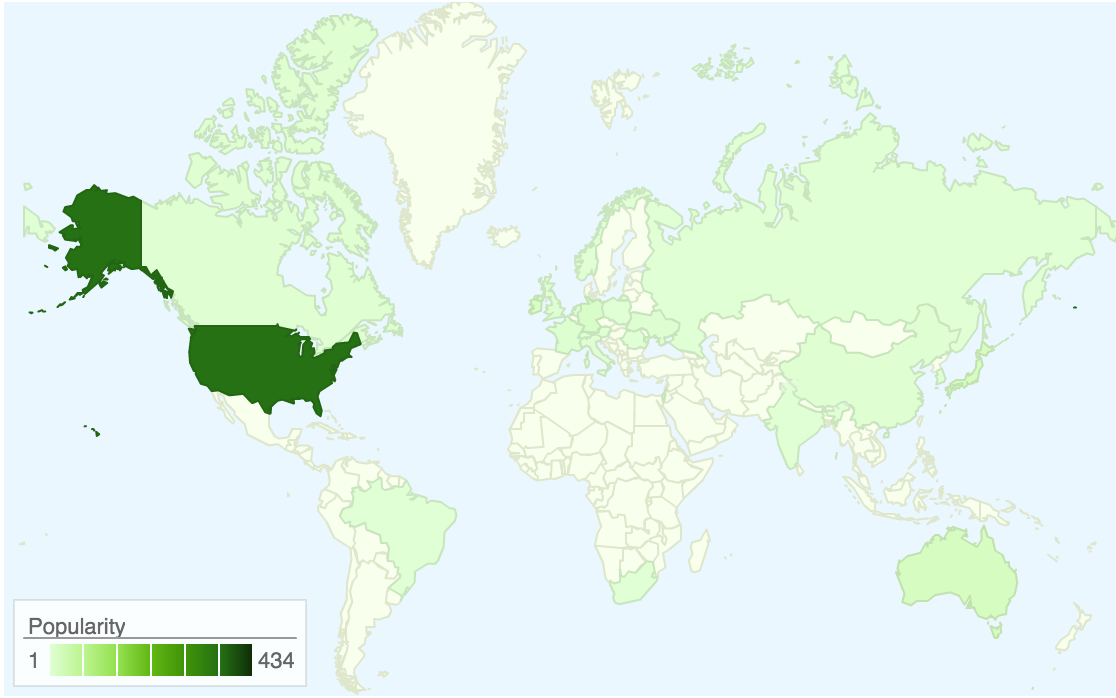
Figure 5. Map of IP addresses that contacted sinkholed Ramdo domains. The darker the color, the higher the number of infections. (Source: Dell SecureWorks)
The sinkholes received more than 70,000 connections in seven days. Many of these requests were performed by automated tools, likely associated with security researcher activities. After filtering the data, Dell SecureWorks CTU researchers determined that approximately a thousand unique IP addresses contacted the infrastructure, 434 of which were from the United States.
Conclusion
Defrauding advertisement services to generate revenue is a popular monetization scheme for botnet operators. Ramdo is one of many malware families that are actively deployed and maintained to perform click fraud. This malware can also download and install additional malware. Dell SecureWorks CTU researchers recommend that organizations keep operating systems and browsers up to date, and use an updated anti-malware solution.
Dell SecureWorks CTU analysis indicates that the Ramdo malware operators are actively deploying new features to avoid both network detection and analysis environments. The collaboration between the Dell SecureWorks CTU research team and Palo Alto Networks allowed researchers from both organizations to compare observations, confirm trends, and discuss how to analyze this threat and study its global distribution.
Threat Indicators
The threat indicators in Table 1 can be used to detect activity related to Ramdo.
|
Indicator |
Type |
Context |
|
b2022f7ef5936c3ee76d39b16ffd4b421576937ca4687bfb210b4035fc28c371 |
SHA256 hash |
Ramdo malware sample |
|
b534d55f384f4a2f9f8762ccd360a7c5d3fbd9ba15b1671e4a3629ef69a4472b |
SHA256 hash |
Ramdo malware sample |
Table 1. Threat indicators for Ramdo. (Source: Dell SecureWorks)
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

