What is the Difference Between IDS and IPS?
An intrusion detection system (IDS) is a device or software application that monitors and analyzes information within your network to identify possible vulnerabilities, security breaches or malicious activity.
An intrusion prevention system (IPS) is a device or software application that acts as a critical layer of defense that requires vigilant monitoring to protect your network from harmful traffic such as a cyber-threat that has passed through or bypassed your firewall.
Do you need an IDS, IPS or both?
Invest in an intrusion detection system or intrusion prevention system (IDS/IPS) that is separate from the firewall. An IDS/IPS behind the firewall can catch thousands of threats daily that get past the firewall and can also catch threats that are trying to leave the network. A security specialist must proactively update the IDS/IPS with threats and policies and must ensure it is being monitored 24/7. Depending upon how often an organization is targeted, IDS/IPS devices that are not tuned properly can generate false-negative responses to true threats or can generate thousands or millions of false-positive alerts each day, making it difficult to identify true threats and take timely action. The device must continually be tuned (sometimes daily or more) and be updated to provide the latest defenses and ensure that you are being alerted to the right activities. If your security devices continually send false alerts, your staff will likely ignore them as well as those that actually are true-positive alerts. Many companies have been breached because their security teams ignored an alert that should not have been.
An IDS/IPS also lets you store information for analysis and reporting at a later date. The company that codes and builds your IDS/IPS should be different than the one that codes and builds your firewall, and the two should be physically separate to ensure that they both aren’t blind to the same vulnerabilities and exploits. Even if you have an appliance that is a mixture of a firewall and an IDS/IPS, you still need a separate layer of IPS/IDS protection behind your firewall to have a defense-in-depth strategy. You should place a network IDS/IPS at all possible points of entry to your network, a host IDS/IPS on your most valuable servers to prevent intrusion and a wireless IPS to prevent attacks that use your wireless Internet connection.
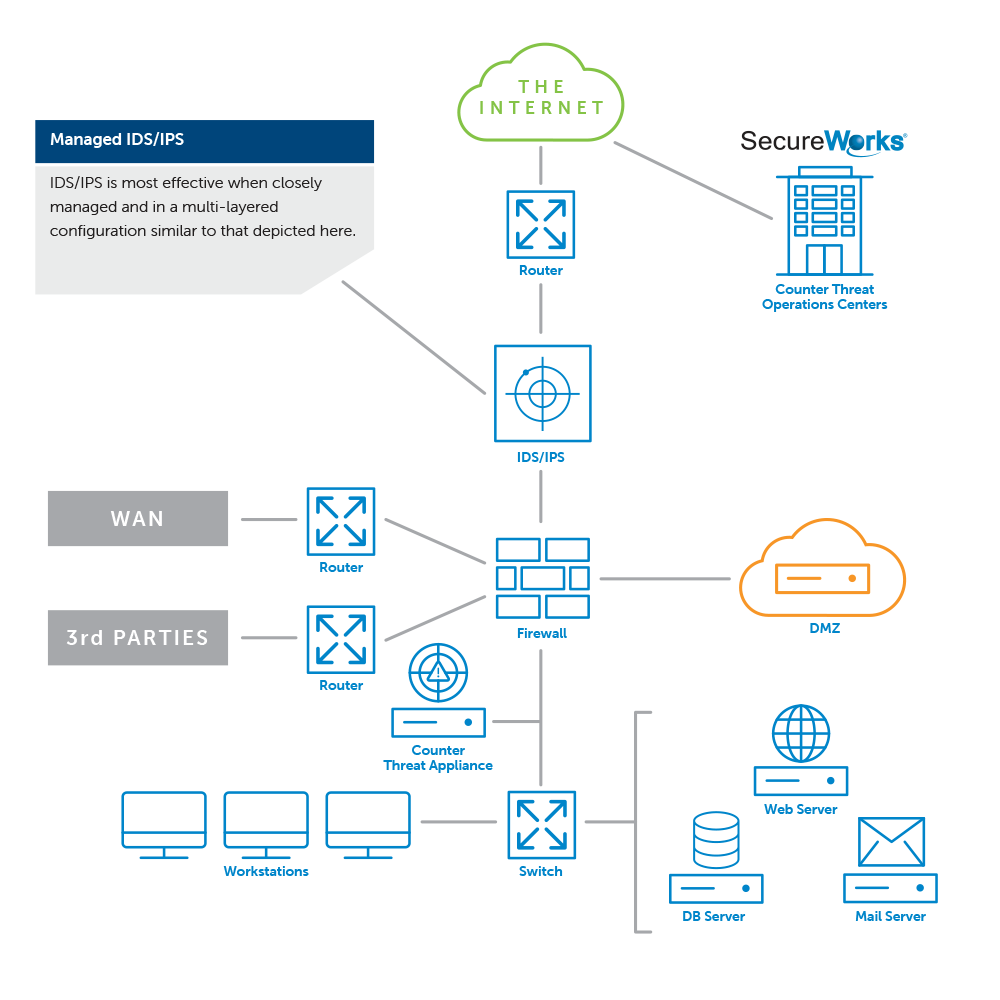
Layered Protection to Prevent Information Security Compromise
With continuous emergence of new threats and company resources under constant pressure, it can be difficult to balance all of the strategic and operational tasks required for an effective information security program. Network intrusion detection system and intrusion prevention system (IDS/IPS) devices can provide a highly effective layer of security designed to protect critical assets from cyber threats. Organizations can detect attempts by attackers to compromise systems, applications and data by deploying Network Intrusion Detection Systems; however, keeping the devices tuned and up-to-date so they are effective is a challenge for many organizations.
IDS/IPS Management Problems for Organizations
Managing IDS and IPS devices requires a specialized skill set because the devices are only effective if they are well tuned to the current threats and the network in which they are deployed. Intrusion Detection System devices can generate thousands of alerts each day and are especially prone to false positives, making it difficult to identify true threats and take timely action to protect assets.
Managed Network Intrusion Detection and Prevention Benefits:
Improve IDS/IPS Effectiveness
Expert signature tuning and device management ensures you will get the maximum value out of your devices.
Identify and Respond to Threats Faster
Your IDS/IPS provider should hold the SANS GIAC Certified Intrusion Analyst (GCIA) certification, so they can monitor intrusion detection system and intrusion prevention system alerts in real time. Events can then be correlated across all available information sources, including other IDS and IPS devices, firewall logs, network devices, host and application logs, vulnerability scan results, and asset information.
Bolster Security with Advanced Research and Global Security Intelligence
Your IDS/IPS vendor should have extensive visibility into billions of events per day that enables their security analysts to identify and investigate emerging threats, and develop countermeasures for organizations. Your IDS/IPS security provider should deliver an advanced level of protection by correlating this intelligence in real time with IDS events seen across their customer base.
Retain the Level of Control Required by Your Enterprise
Your MSSP should offer flexible support in the most complex environments, allowing our experts to tailor services to each customer's individual needs. Appliances can be managed in a traditional managed services model, where customer personnel have limited or no administrative privileges for their IDS/IPS devices.
Choose a provider that can also support co-management, where the customer retains ownership and administrative rights to their IDS/IPS appliances to the extent that is preferred. With this approach, our experts alleviate the management, maintenance and monitoring burdens without the customer being locked out of their infrastructure.
Obtain Comprehensive Visibility into the Security Activity on Your Network
Your IDS/IPS security provider should have the most advanced web-based portal for managed security services. The intuitive and appealing interface furnishes you with clear views into the state of your organization's security posture, supported by real-time, enterprise-wide reporting: Convey the state of your organizations' security with executive level reports and dashboards; drill down into security activity and events using operational reporting tools; prove regulatory compliance to auditors quickly and effectively.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

