With technology rapidly advancing, many organizations have upgraded or are considering upgrading to a Voice over Internet Protocol (VoIP) phone system rather than a legacy phone system.
When considering network security, please keep in mind your phone system, or Private Branch Exchange (PBX), is also a possible point of compromise. Transitioning to VoIP technology has its advantages, but like with any new technology, understanding how to secure the system can help mitigate risks of compromise.
Network-Based Vs. Session-Based Authentication
Legacy PBXs such as PRI, CAS, and Analog are examples of phone systems that utilize network-based authentication. Network-based authentication relies on physically being a part of the network as a means of authenticating. This can make it challenging for threat actors to compromise remotely. For example, plugging in your fax machine allows it to make outbound calls. This is almost the same as being punched down directly on the punch-down block.
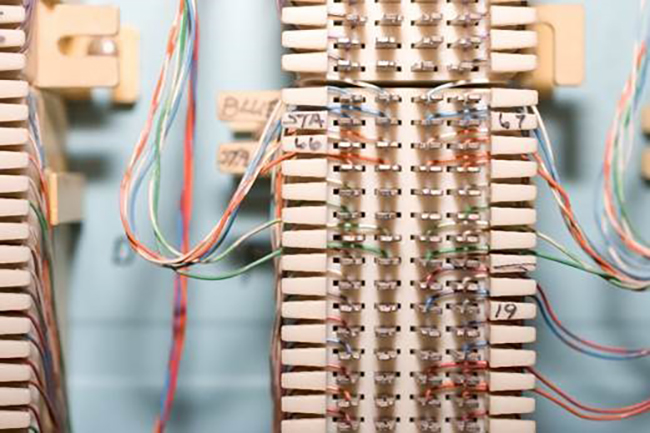
CAPTION: The punch-down block refers to the 66 block or 110 block where you "punch" down your phone system's twisted pairs to connect to the ISP provided lines. Image Source: Punch Block
(source: iStockPhoto)
One side is connected via the ISP, and the other side is connected to your local voice lines. These are connected in the middle of the block via a jumper to complete the circuit. Any call made from this point would be routed through your voice provider's backbone and sent out to the Public Switched Telephone Network (PSTN) for completion of the call. In most cases, the threat actor would need physical access to accomplish this. It should be noted that some legacy phone systems do have a VoIP backing for remote phones, a Graphical User Interface (GUI) for administration of features such as voicemail, or other features that utilize an IP on your network for access. These may be considered a hybrid PBX.
VoIP phone systems utilize session-based authentication. This may come as no surprise, as VoIP is traveling across your IP network via User Datagram Protocol (UDP). This presents additional opportunities for cybercriminals. There are several types of VoIP PBX, but the focus here will be Session Initiation Protocol (SIP). Among other things, SIP provides the signaling, and it controls the multimedia for your communication session. The signaling is the creation and tear down of every phone call. In this case, the multimedia is the two-way audio for your phone call. Since the network is no longer the point of authentication and SIP is session-based, SIP can authenticate every session. VoIP phone systems authenticate with registration attempts to a SIP trunk and VoIP handsets authenticate with registration attempts to the PBX.
Simply put, A SIP trunk is a logical point that provides logical lines for your phone system to make calls. Unlike receiving a physical line per phone call as you would in legacy voice, concurrent phone call capacity is limited by this trunk. Registration is the process of authenticating before calls can be made. The PBX initiates the authentication process by sending a REGISTER over port 5060 UDP – the default port and protocol for SIP traffic – to the registrar provided by your VoIP provider. Additionally, SIP uses HTTP messaging such as 401 unauthorized and 200 OK. If the REGISTER does not contain the user name and password, the registrar responds with a 401 unauthorized. This is referred to as nonce authentication, and it is also the response if the user name and/or password are incorrect. The PBX responds by sending the REGISTER again, but this time the REGISTER contains the requested authentication. If the user name and password are correct for either the original request or in the register response to the nonce, the SIP trunk responds with a 200 OK and holds the registration information provided for the time frame specified in the REGISTER. Handsets and soft phones undergo a similar process, except it's handset to PBX instead of PBX to SIP trunk. At this point, the handset or PBX is considered authenticated for the registration period, and it will be able to process calls during that time.
Network Voice Security – What to Consider
Telephony fraud is a viable avenue of revenue for cybercriminals. Premium-rate telephone numbers are easy to obtain, and the cost is paid by the initiator. An example of these would be psychic hotlines, phone lottery hotlines, or video game hint hotlines. A compromised phone system placing calls to such numbers "owned" by a threat actor is a fast way to generate money, leaving the victim with the bill. For a subtler approach, they may forward all of the lines in the phone system during off-hours to several of these previously set up toll numbers. Registering a phone to an open extension and setting up an auto-dialer to call these numbers repeatedly is trivial. Better yet, they can use foreign numbers to get international premium rates involved. Additionally, a man-in-the-middle attack that records sensitive information in a phone call could prove to be devastating to your business. While this is merely a basic overview, hardening your voice network's security can possibly stop fraud and save your company money.
This brings up several points to consider when evaluating a network's voice security. The SIP trunk is not located on your network, so 5060 UDP needs to be allowed inbound and outbound. The multimedia will also need to be allowed. Depending on several factors such as the multimedia specified, this will require a range of around 10,000 UDP ports to be allowed inbound and outbound. Additionally, remote phones will need to be able to reach the PBX to authenticate. The PBX will have packets routed to it both internally and externally for features as well.
Consider implementing these basic recommendations to assist in mitigating possible attacks against your voice network:
Research & Training
- Implement a telephony security training regime as a part of your network security training program.
- Refer to the manufacturer and owner's manual for best practices and advanced hardening for the specific PBX deployment.
- Discuss cybersecurity options with your ISP, network admin, and voice admin.
- Ensure your provider limits registration attempts to your registrar network range. If your provider utilizes a Session Border Controller (SBC), ensure you are registering to it properly.
- Discuss the use of an SBC (Session Border Controller) and/or MVG (Media Voice Gateway) with your ISP, network admin, and voice admin. If an MVG is in use, ensure it is hardened as they can have the ability to make calls.
- If your environment merits it, consider a managed security services provider.
- Peruse VoIP security vulnerabilities both general and specific to your environment.
Configuration & Setup
- Authenticate as many sessions as possible. SIP can be configured to authenticate every session.
- Use authentication codes on the phone system as well as through your provider. These are codes that can be enabled and required for any outbound call to toll numbers.
- Delete or disable any extensions not in use.
- Require passwords that follow strong security guidelines for all authentication. Do not leave any features, extensions, or other authentication areas open.
- Disable call forwarding on extensions that are not utilizing this feature.
- Utilize allow and/or deny rules by network/host for each individual extension. Write these rules to where the PBX only honors registration attempts from IP's you've pre-defined on each extension.
- Limit 5060 UDP traffic and related multimedia traffic at the perimeter of your network to your ISP's provided range(s). Consider the use of an ACL at your perimeter that allows outbound traffic and evaluates inbound return traffic based on the outbound traffic for these sessions. This is commonly referred to as a reflexive ACL.
- Remote phones can be a challenge. Most phone systems have a configurable ACL option on each extension. Configure these to only accept registration attempts from pre-determined networks and hosts. Implement this functionality where applicable, even for your internal extensions.
Administration
- Regularly update all software with the latest security patches.
- Consider physical security for your phone system. Keep entries locked and limit access.
- Periodically review enabled call forwarding to ensure it is accurate.
- If eavesdropping on telephone conversation(s) is a concern, consider using encrypted multimedia where applicable.
- Consider normal network security vulnerabilities and attacks. These communications are done over your data network and are no exception.
References:
http://www.rfc-base.org/txt/rfc-3261.txt
http://www.rfc-base.org/txt/rfc-3665.txt
https://www.sans.org/reading-room/whitepapers/voip/voip-security-vulnerabilities-2036
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

