During various incident response engagements, Dell SecureWorks Counter Threat Unit (CTU) researchers observed threat actors employing tactics to identify user accounts on target systems within the compromised environment. The adversaries may have been gathering information relevant to their objectives, such as data about administrative accounts, targeted individuals, or business units, or may have been identifying accounts they could compromise to avoid anomaly detection focused on suspicious account activity.
A new profile is created each time a new user interactively accesses a system, which could raise a red flag with incident responders. To blend in and avoid detection within the victim’s network, skilled threat actors leverage credentials of users who previously accessed targeted computer systems.
Case Study 1 – LogParser
While investigating one intrusion, CTU researchers discovered that threat actors had used compromised credentials to log into a large technology company’s network via Citrix, a popular remote network access tool. The adversaries were able to escape the Citrix sandbox and move laterally through the network to the company’s Microsoft Exchange server. From there, the threat actors extracted, archived, and exfiltrated email from a variety of victims, including key executives of the organization, employees of a company subsidiary, and incident response personnel.
The threat actors then copied the Security event log from a specific system in the victim’s network. CTU researchers later detected that the adversaries executed Microsoft’s LogParser tool, which had been previously installed on a domain controller within the network (see Figure 1). The LogParser tool is used legitimately by system administrators to query and parse data stores like Windows event logs.
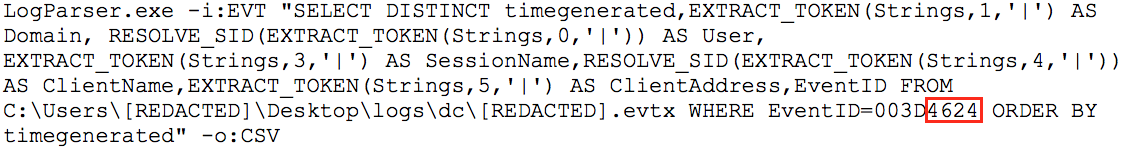
Figure SEQ Figure \* ARABIC 1 LogParser command. (Source: Dell SecureWorks)
Figure 1 illustrates the threat actors collecting Security event log information, specifically for Event ID 4624, which is created when an account successfully logs on to a system running Windows Vista or subsequent Windows operating system. CTU researchers assess with medium confidence that the threat actors were attempting to identify privileged accounts they could use to access systems belonging to high-value employees.
Case Study 2 – Domain Logon Script
During another engagement at a professional services company, CTU researchers discovered that threat actors had gained initial access into the organization by moving from a compromised host in the perimeter network (DMZ) to the company’s corporate network via a computer with connections to both networks. The adversaries’ ultimate goal was to steal sensitive personally identifiable information (PII) by deploying keylogging and screen capture tools to specific systems within the company.
CTU researchers also discovered that the threat actors added a logon script named delprof.vbs to the scripts directory on a domain controller (see Figure 2). The script collects the username and host name from each logon session, and writes the output to the file named delprof.dll on the specified target system. CTU researchers assess with medium confidence that the threat actors were attempting to collect information that would enable them to access target systems using unsuspicious accounts to avoid anomaly-based detection.
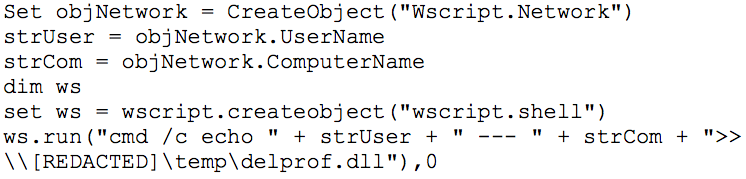
Figure 2. Delprof.vbs contents. (Source: Dell SecureWorks)
Conclusion
These case studies do not reflect all possible tactics to link users to systems, but they represent tactics observed in the field by CTU researchers. Organizations should audit domain login scripts for additions or modifications to existing code. As network defenders improve their ability to detect adversaries who live off the land by compromising and using employee credentials, the adversaries are evolving their tactics to blend in with legitimate activity in the target’s IT environment. Threat actors are also becoming more skilled at taking advantage of native capability within compromised environments to more stealthily achieve their objectives.
[1] CTU researchers have adopted the U.S. Office of the Director of National Intelligence grading system, in which medium confidence "generally means that the information is credibly sourced and plausible but not of sufficient quality or corroborated sufficiently to warrant a higher level of confidence."
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

