The Dell SecureWorks Counter Threat Unit™ (CTU) research team analyzed a malware sample on April 9, 2014 that takes advantage of recent news reports focusing on the "Heartbleed" vulnerability. The filename used by the attacker, shown in Figure 1, literally translates to "Heartbleed vulnerability testing tool.exe," but CTU researchers are referring to it as the HelloBridge backdoor trojan. On April 9, the VirusTotal analysis service showed low detection for this malware, with only 3 of 51 antivirus (AV) vendors detecting it as malicious. As of April 17, 27 of 51 AV vendors detected it as malicious.
![]()
Figure 1. HelloBridge trojan filename translates to Heartbleed vulnerability testing tool.exe. (Source: Dell SecureWorks)
Upon execution, HelloBridge drops an executable named msbridge.exe (MD5: 0cea856a31e5ab054100158216a9b7c0) into the %Temp% directory on a victim's system and adds the following registry key to auto-run and maintain persistence:
- NTUSERSoftwareMicrosoftWindowsCurrentVersionRun
- Value=msbridge
- Data=%TEMP% msbridge.exe
As shown in Figure 2, HelloBridge also connects to hard-coded IP address 122.10.62.137.
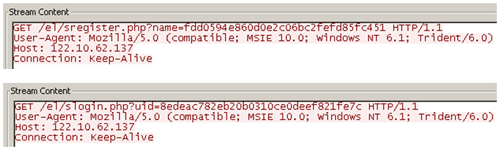
Figure 2. HelloBridge trojan connecting to 122.10.62.137. (Source: Dell SecureWorks)
U researchers identified nine additional HelloBridge samples that were hard-coded to connect to this IP address. Most of these samples were uploaded in Japan and Taiwan, suggesting that the trojan was used predominantly in Southeast Asia (see Figure 3). All of the samples also had recent compilation timestamps, indicating that it is a recent attack vector being used by adversaries. A quick analysis suggests that the malware can execute commands, download additional files, and exfiltrate data based on commands sent from a command and control (C2) server.
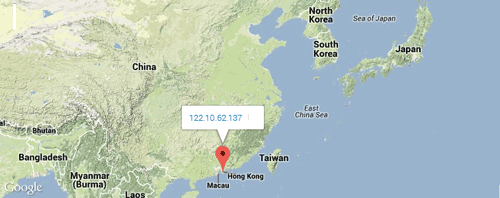
Figure 3. Location of samples connecting to 122.10.62.137. (Source: Dell SecureWorks)
To mitigate exposure to this threat, CTU researchers recommend that organizations use available controls to restrict access using the indicator in Table 1. The IP address listed in the indicators table may contain malicious content, so consider the risks before opening it in a browser.
| Indicator | Type | Context |
|---|---|---|
| 122.10.62.137 | IP address | Hard-coded IP address in the HelloBridge trojan |
| %TEMP%msbridge.exe | File path | Backdoor file path on an infected system |
| 0cea856a31e5ab054100158216a9b7c0 | MD5 hash | Cryptographic hash of the backdoor trojan dropped on an infected system |
Table1. Indicators for HelloBridge.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.

