Secureworks® Counter Threat Unit™ (CTU) researchers are monitoring activity conducted by the INC Ransom group, which CTU™ researchers track as GOLD IONIC. The threat group, which emerged in August 2023, uses the common double extortion method: they exfiltrate data before encrypting systems and then threaten public exposure as leverage in ransom negotiations with victims.
Victimology
- GOLD IONIC named 72 victims on its Tor leak site from August 2023 through March 2024. As of this publication, seven victims have been published in April.
- Most of these victims are based in the U.S., but the group has expanded its global reach.
- The victims represent a wide range of sectors, but the most common are industrial, healthcare, and education organizations.
GOLD IONIC appears to operate as a closed group rather than using affiliates in a ransomware-as-a-service model. Figure 1 shows the monthly breakdown of victims posted to the leak site. The numbers indicate a fairly steady and consistent pattern, with the outliers possibly being due to batched releases.
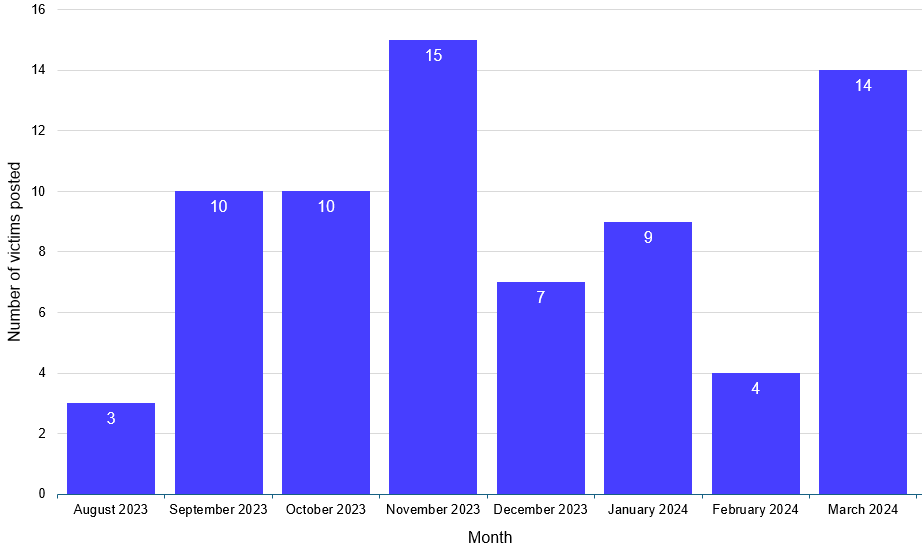
Figure 1. Number of victims posted to GOLD IONIC's leak site from August 2023 through March 2024. (Source: Secureworks)
One common theme across financially motivated threat groups is the indiscriminate and opportunistic nature of their attacks. As a result, victims represent a broad range of geographies and sectors. However, CTU analysis of GOLD IONIC's victimology revealed that most of the impacted organizations are based in the U.S., with the UK trailing by a significant margin (see Figure 2). The impact to Western organizations and lack of victims from Commonwealth of Independent States (CIS) countries suggests that this group operates out of Russia or one of the CIS countries.
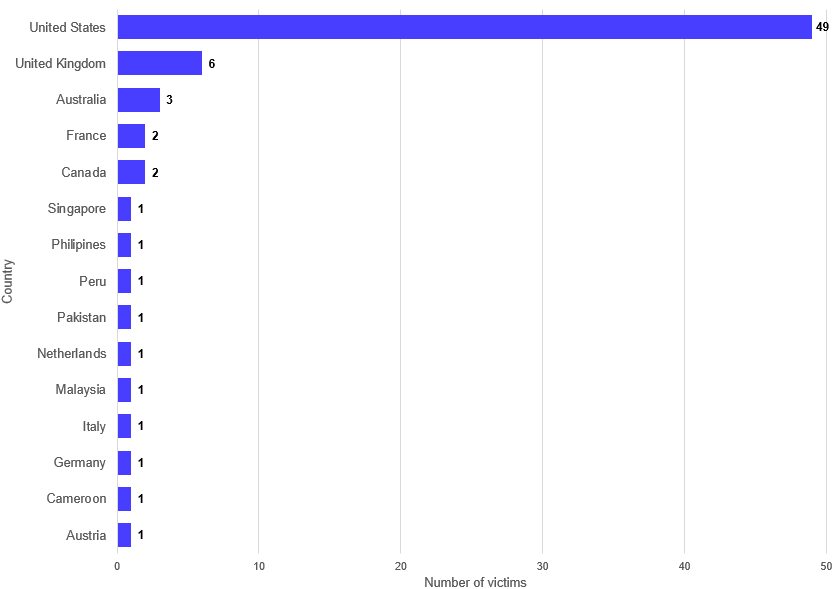
Figure 2. Geographic locations of victims posted to GOLD IONIC's leak site. (Source: Secureworks)
There is no obvious trend to the impacted sectors. Like many ransomware groups, industrial, healthcare, and education organizations feature most prominently in their victim list (see Figure 3). The proportion of educational establishments is more than double than the overall percentage (5%) across all ransomware groups between August 2023 and March 2024. However, the small sample size of GOLD IONIC victims makes it difficult to draw any meaningful conclusions.
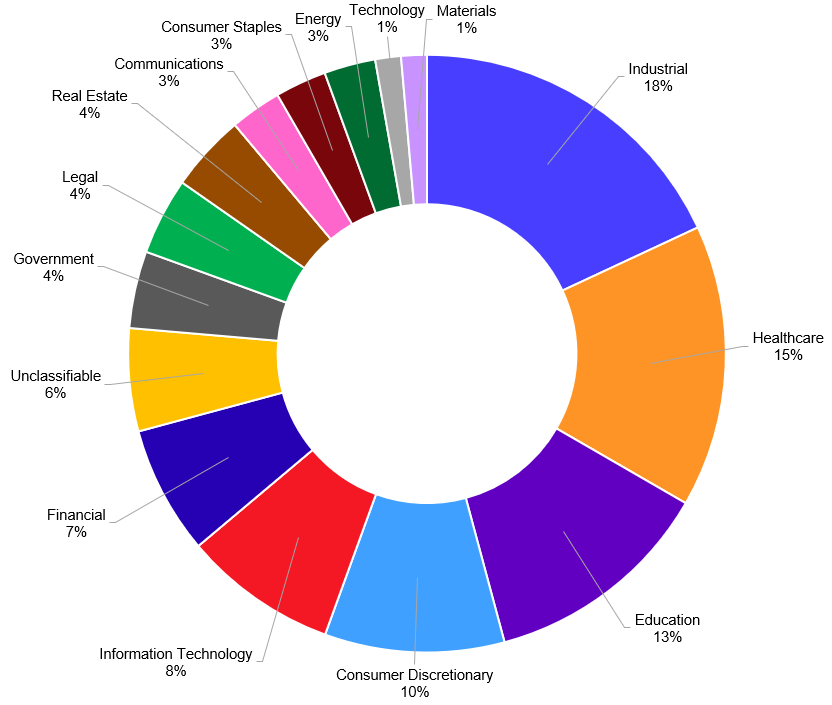
Figure 3. Breakdown of sectors for victims posted to the GOLD IONIC leak site. (Source: Secureworks)
Operations
Secureworks incident response engagements featuring GOLD IONIC indicate that the group consistently deploys INC ransomware. In one of these incidents, exploitation of the "Citrix Bleed" vulnerability (CVE-2023-4966) may have provided initial access. Affiliates of the GOLD MYSTIC threat group's LockBit ransomware-as-a-service (RaaS) operation have historically favored this initial access vector for data theft and extortion.
After gaining access to the network, the attacker dropped an executable (p443x64.exe) that installed a Meterpreter shell. They then used the AdFind command-line Active Directory query tool to enumerate the environment, WinRAR to archive files and folders, and the Megasync cloud hosting solution to exfiltrate more than 70 GB of data. After exfiltrating the data, the threat actor copied the INC ransomware executable to over 500 other systems and then ran it remotely via PsExec. The executed binary encrypted files, added a .inc file extension to the encrypted files, and dropped the INC ransom note (INC-README.txt) (see Figure 4). The filename of the ransomware binary is unique to each victim and contains the organization's name.
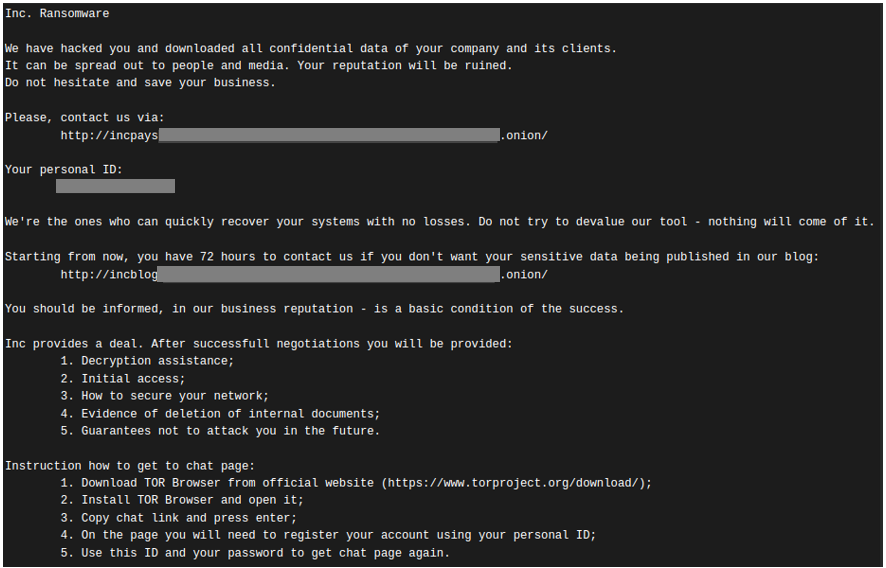
Figure 4. INC ransom note from Secureworks incident response engagement. (Source: Secureworks)
The INC ransom note includes a Tor .onion address along with a personal ID, and it instructs the victim to contact the threat actor within 72 hours or sensitive data will be published to the leak site. The structure and design of the INC Ransom leak site are similar to the LockBit leak site (see Figure 5), but there are no other indications that the groups are related.
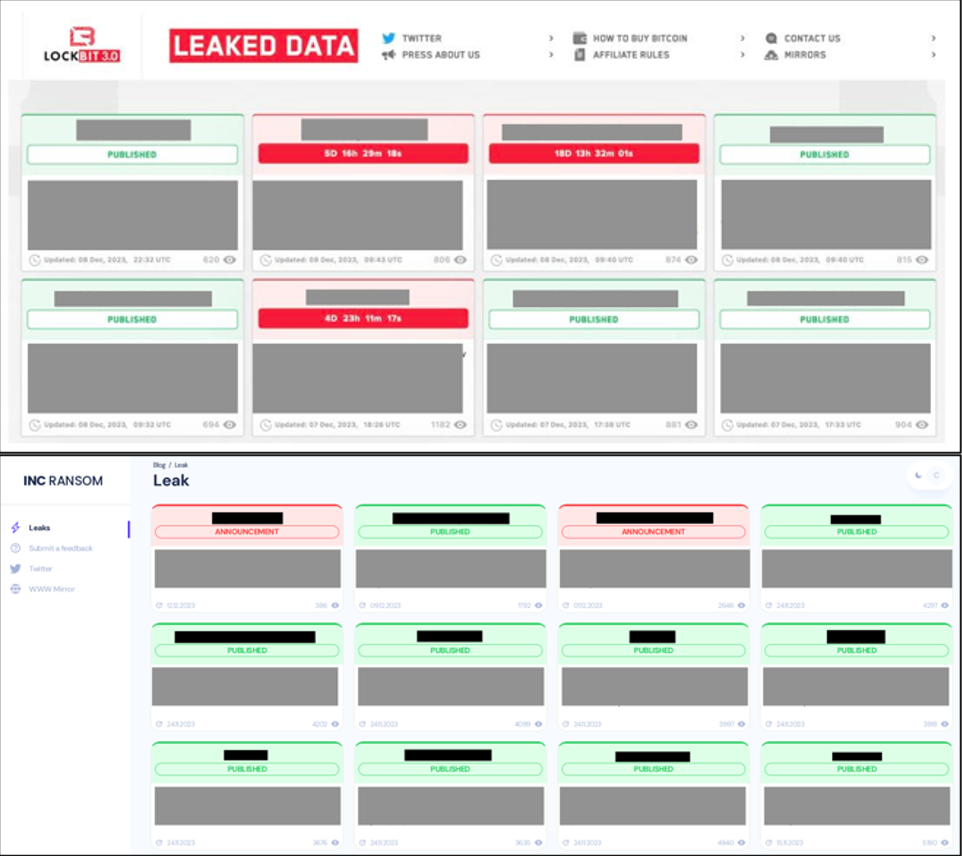
Figure 5. Comparison of the LockBit (top) and INC Ransom (bottom) leak sites. (Source: Secureworks)
The INC Ransom leak site lists some victims of other ransomware attacks. Secureworks incident responders determined that the executed files and the ransom note filename format (RECOVER-<seven random letters>-FILES.txt) in one compromised environment aligned with the ALPHV ransomware managed by GOLD BLAZER. The timing of the data theft aligned with law enforcement action that rendered GOLD BLAZER's Tor-based infrastructure unreachable. During this period of inactivity, other ransomware groups such as GOLD MYSTIC attempted to recruit ALPHV affiliates and offered to allow these affiliates to use the LockBit leak site to post data and conduct negotiations. These circumstances could explain why a victim of an ALPHV ransomware attack was posted to the INC Ransom leak site; the post was not necessarily the result of GOLD IONIC operating an affiliate model.
Ransomware affiliates are financially motivated and may operate in their own best interest rather than remaining loyal to a particular threat group or ransomware family. For example, CTU researchers observed a warning on Donut Leaks' leak site about an affiliate who had allegedly stolen data from them and posted it on other leak sites with modified contact information to collect the ransom (see Figure 6). The post specifically mentions INC ransomware, although the connection is unclear. Some affiliates have reportedly deployed up to seven different ransomware families. The dynamic relationship between affiliates and operators could be another explanation for the cross posting of the stolen data on other leak sites. However, there is little evidence to suggest that different affiliates work for GOLD IONIC.
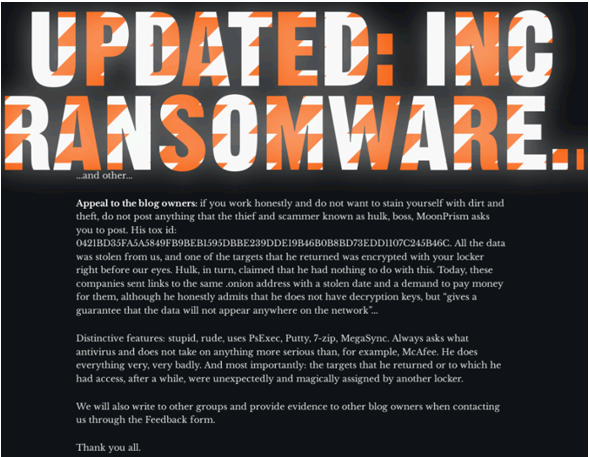
Figure 6. Donut Leaks warning about affiliates posting stolen data to other leak sites. (Source: Secureworks)
Conclusion
GOLD IONIC is yet another emerging ransomware group quickly amassing victims, and its tactics, techniques, and procedures (TTPs) are similar to many other groups. CTU researchers advise organizations to follow guidance provided by the U.S. Cybersecurity & Infrastructure Security Agency (CISA) and the UK National Cyber Security Centre (NCSC) to mitigate the risk of ransomware attacks. Organizations should also implement and test incident response plans so they can react quickly if an attack occurs.
Detecting and mitigating malicious activity before ransomware is deployed can limit the impact of the attack. Learn more about the ransomware threat:
- 2023 State of the Threat: A Year in Review
- Ransomware Evolution
- Phases of a Post-Intrusion Ransomware Attack
If you need urgent assistance with an incident, contact the Secureworks Incident Response team.
Secureworks has been acquired by Sophos. To view all new blogs, including those on threat intelligence from the Counter Threat Unit, visit: https://news.sophos.com/en-us/.
